The annual Kaspersky Incident Response 2023 report has revealed that in 2023, more than 1/5 of cyberattacks persisted for over a month, with trusted relationships emerging as one of the main attack vectors in these prolonged cases. The report draws on the results of Kaspersky’s cyberattack investigations throughout the year, gathered when supporting organizations seeking incident response assistance or hosting expert events for their internal incident response teams.
What Kaspersky Incident Response Report 2023 Indicates?
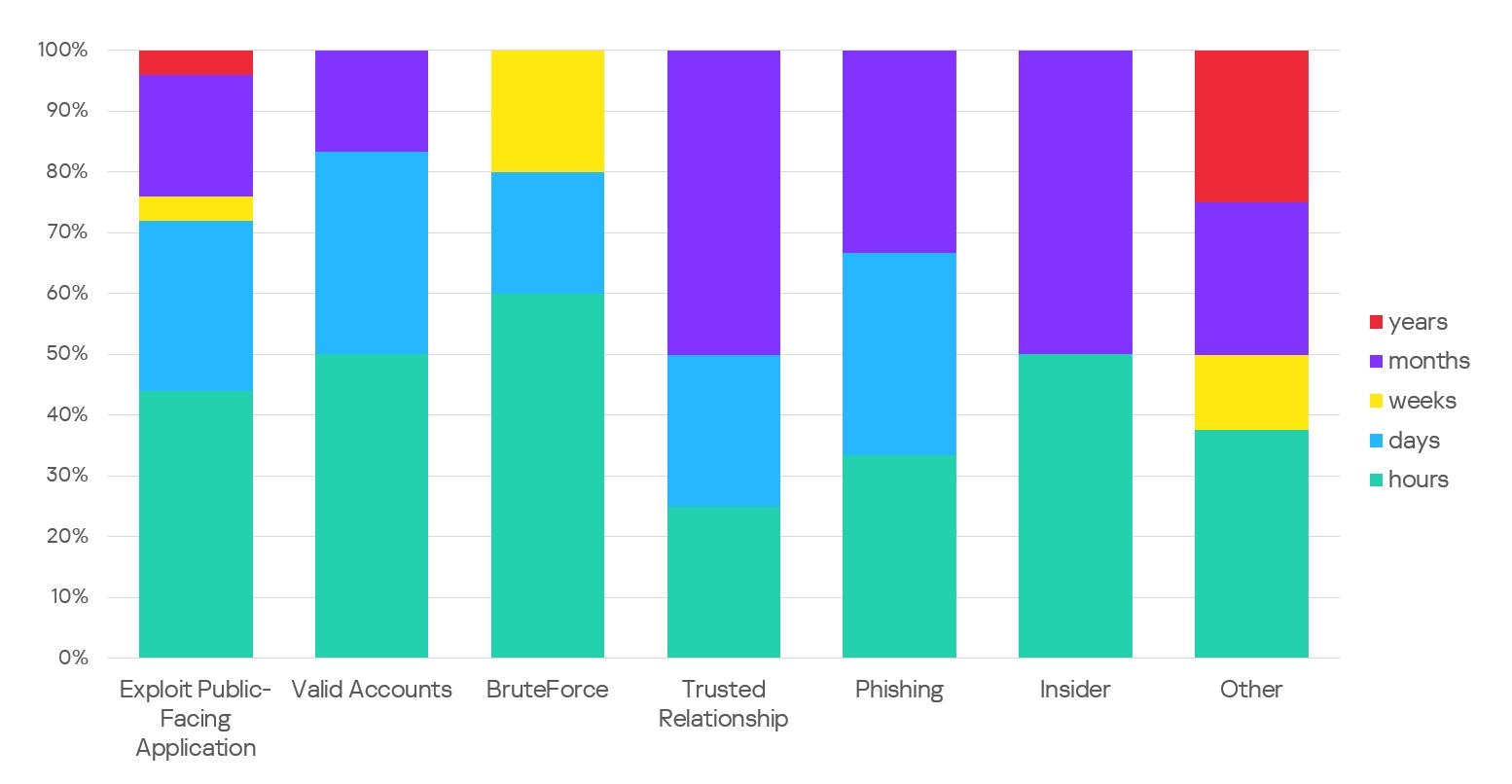
Long-lasting cyberattacks that persist for more than a month constituted 21.85% of the total, increasing by 5.55% from 2022. One significant trend observed in these attacks was exploiting trusted relationships as a primary vector. Compromises leveraging trusted relationships have occurred previously, but in 2023, their frequency increased, accounting for 6.78% of the total number of attacks.
What are the Risk Mitigation Strategies that the Incident Response Report Highlights?
- Establish a culture of security awareness with employees.
- Restrict public access to management ports.
- Adopt a zero-tolerance policy for patch management or take compensatory controls for internet-exposed applications.
- Regularly back up critical data to help limit any potential damage.
- Use strong password policies and implement two-factor authentication.
- Enhance your company’s defenses against the most complex attacks and detect threats as early as possible with managed security services such as Kaspersky MDR.
- Get immediate help from cyber experts once suspicious activity of potential breaches, or confirmed incidents occurs.
Primary Cyberattack Trends Identified in the Report
- Rise in attacks facilitated through service providers. This tactic offers attackers the advantage of executing large-scale attacks with reduced effort compared to targeting individual victims directly.
- Ransomware continued to be prominent in cyber threat landscapes, with one in three incidents in 2023 attributed to ransomware attacks.
- Most data encryption attacks concluded swiftly, with 43.48% resolved within a day and 32.61% within days.
FAQs
1. Why is incident response considered critical for organizations?
Incident response is essential because it helps organizations prepare for, manage, and recover from cyberattacks, minimizing damage and reducing recovery time and costs.
2. What are the most common initial vectors for cyberattacks?
The most frequent methods of initial compromise include exploitation of public-facing applications, use of compromised accounts, and attacks through trusted relationships.
3. What recommendations does Kaspersky provide for improving incident response?
Recommendations include implementing robust password policies, multifactor authentication, regular patch management, and enhancing detection capabilities to identify and respond to attacks more effectively.
4. How can organizations detect and mitigate attacks using legitimate tools?
The report discusses the misuse of legitimate tools like Mimikatz and PsExec in attacks and recommends employing security solutions that can detect unauthorized use of such tools.
5. How long do cyberattacks typically last?
The duration of attacks varies, but the report categorizes them into three types: high-velocity attacks lasting less than a week, average attacks lasting up to a month, and long-lasting attacks that persist for more than a month.
6. What are the most common vulnerabilities highlighted in the report?
The most prevalent vulnerabilities present in our dataset for 2023 were related to SMBv1 (CVE-2017-0144 and CVE-2017-0143), Microsoft Exchange Server (CVE-2021-27065 and CVE-2021-26855) and FortiOS (CVE-2023-22640, and CVE-2023-25610). 62% of the vulnerabilities detected in attacks lead to Remote Code Execution (RCE), with public exploits available on the surface web, making it easy for adversaries to exploit them and gain access to the target system.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]


