From placing orders in cafes and restaurants to paying the final bill, QR codes have become integral to our daily activities. According to research by QR Tiger, QR code scans reached 26.95 million in 2023—a 433% increase over the past two years. However, with the rising prevalence of QR codes in everyday life, attackers have found ways to exploit them for malicious purposes. Between June and August 2023, there was a significant surge in QR code phishing emails. Systems detected 8,878 such incidents, indicating a worrying shift in cybercriminal tactics. June saw the peak of this trend, with 5,063 reported cases of QR code phishing.
Also Read: Top 10 Anomaly Detection Software for Secured Enterprise
The use of QR codes in cyberattacks has grown across all companies from SMBs to large enterprises. With a 50% spike in these types of attacks this quarter.– SlashNext Research
Understanding QR Code
QR codes, or quick response codes, have surged in popularity and become essential in our digital era. Originally designed for industrial tracking, their ease of use has made them a go-to information-sharing tool. With the rise of digital payments in the smartphone era, QR codes have become ubiquitous, facilitating transactions and swift data access.
There are two main types of QR codes: Dynamic QR codes, which can be updated regularly but are vulnerable to cyberattacks, and static QR codes, which remain fixed and stable but can also be targeted by cybercriminals. As we explore the world of QR codes, it is crucial to understand their dynamics and potential risks, shedding light on the darker side that accompanies their widespread popularity.
What does QR Code Phishing mean?
Quishing, or QR code phishing, is a cyberattack in which cybercriminals exploit QR codes to trick users into providing sensitive information or downloading malicious content. Here, the attackers pretend to be someone or some organization, sending the realistic-looking QR code to the targets to trick them into scanning it for some apparent reason. When the target scans the code, it directs the target to the destination of choice for the attacker, either a spoofed login page or a landing page filled with malware.
Similar to other types of phishing, QR phishing can be launched through various means for any purpose. The cybercriminal’s purpose and resources can be several things. QR phishing can be delivered via email, text message, or even print material—anything that can get users to scan the code. Cybercriminals use social engineering tricks to get their targets to scan the codes quickly with the least amount of forethought.
A QR code can point to any page the attacker wants. Technically, it works differently from traditional phishing, which involves links or attachments, but it’s a very similar experience from the target’s perspective. Instead of being asked to click a link they don’t recognize or download an attachment they don’t expect, they are asked to scan a QR code.
Although the attacker can misuse their victims’ information in many ways, most phishing efforts often aim to achieve one of two primary objectives:
- Money: Cybercriminals often send messages with fake invoices or pleas for financial help, using deceit and social engineering to convince the target to send money urgently.
- Data: QR code phishing can yield sensitive information like login credentials, personally identifiable information, and other data that can be precious to bad actors.
QR Code Phishing vs. Traditional Malicious Attachments or Links
In contrast to traditional phishing methods, which typically involve targeted emails containing malicious attachments or links, QR code lures present a unique approach to cyber-attacks.
Traditional phishing attacks often employ deceptive emails impersonating familiar individuals or organizations. These emails entice users to open attachments or click on links embedded within the email body. The attachments may be Microsoft Word documents or URLs presumed to be trustworthy by the recipient.
However, in QR code attacks, the adversary incorporates a QR code directly into the body of the phishing email. The recipient is prompted to scan the QR code using a mobile device, which is then directed to open a specific attachment or web link. To access the content, users must utilize QR code scanning apps or built-in scanning functions on native camera apps.
The content linked to these QR codes can vary significantly. Attackers may direct users to fraudulent web pages resembling legitimate login portals, aiming to steal credentials upon login attempts. Alternatively, the QR code may lead to a malicious attachment that installs malware onto the target’s device.
Detailed Analysis of the QR Phishing Attack Process
Creation of Malicious QR Codes
Cybercriminals design real-looking QR codes but redirect users to fraudulent websites or prompt the download of malicious content.
Social Engineering Techniques
Phishers use persuasive messages to manipulate users into scanning the malicious QR codes. These messages may promise rewards, discounts, or urgent alerts to create a sense of urgency or excitement.
Distribution Channels
Malicious QR codes are disseminated through various channels, including phishing emails, fake advertisements, and physical items like posters and flyers, exploiting unsuspecting victims online and offline.
Camouflaging Techniques
Attackers often craft malicious QR codes to be visually indistinguishable from legitimate ones by mimicking branding, logos, and design elements. This deception makes it challenging for users to distinguish between authentic and malicious codes.
Redirecting to Fraudulent Websites
Once the QR code is scanned, victims are redirected to fake websites that mimic legitimate ones. These sites prompt users to enter sensitive information, such as usernames, passwords, or financial details.
Downloading Malicious Content
In some instances, scanning a malicious QR code initiates malware download onto the user’s device, compromising security and potentially leading to further cyberattacks.
Data Harvesting and Identity Theft
Phishers harvest the information victims enter on fake websites, leading to identity theft, financial losses, or unauthorized access to personal accounts.
Also Read: Building Security from Scratch: Key Steps in Implementing Zero Trust Architecture
Best Practices to Protect from QR Code Phishing
To safeguard yourself from QR code phishing, follow these essential steps:
- Exercise Caution: Treat QR codes with the same scrutiny as any other link or URL. Only scan codes from trusted sources, and if uncertain, refrain from scanning altogether.
- Verify URLs: Before scanning a QR code, inspect the destination URL. If it appears suspicious or differs from the expected location, avoid scanning it.
- Use Secure QR Code Scanners: Opt for QR code scanner apps equipped with security features like URL validation and malware detection to enhance protection.
- Keep Devices Updated: Regularly update your smartphone’s operating system and applications to ensure you have the latest security patches installed.
- Enable Two-Factor Authentication (2FA): Implement 2FA wherever feasible to add an additional layer of security to your accounts, mitigating the risk of unauthorized access even if passwords are compromised.
- Stay Informed: Stay abreast of the latest cybersecurity threats, including QR code phishing, to recognize potential dangers promptly.
- Report Suspicious Codes: If you encounter a malicious QR code, promptly report it to relevant authorities or the platform where you found it.
Mitigating QR Code Attacks: Strategies for Security Teams
QR code attacks are almost impossible to detect with human awareness and traditional security solutions. In contrast with the usual link-based attacks, QR codes can divert victims to phishing pages without elevating the same suspicion level as they emerge in business communication.
QR code attacks mostly pass by security tools undetected due to their minimal text content and without apparent malicious links. This lack of more indicators of traditional attacks limits the power of conventional security measures.
QR code attacks shift the attack surface from the secure email environments to the users’ mobile devices, which mostly don’t have the same level of lateral protection and posture management present in cloud-based business environments. This is partly why 27% of phishing attacks utilize fake MFA notifications targeting users.
Combating these evolving threats requires proactive action. Security teams must adopt the following measures:
- Avoid Unknown QR Codes: Educate individuals not to scan QR codes from unknown sources; however, this may prove challenging since most legitimate uses in today’s digital landscape involve scanning QR codes.
- Non-QR Code-Based MFA: Implement MFA that does not involve QR codes to avoid complacency in employees and to discourage trust in emails containing QR codes. Emphasize secure MFA methods like SMS, time-based passwords, or biometrics.
- Advanced Security Awareness Training: Incorporate QR code attacks into security awareness training simulations to make employees understand this new phishing method.
- Email Security Solutions: Implement email security solutions with features specifically for QR code detection. These solutions parse QR code images and associated links for malicious activities, increasing detection efficacy with other indicators such as unfamiliar senders or alarming language.
Top Solution Providers to Prevent QR Code Phishing
#1 Microsoft Defender for Office 365
Microsoft Defender for Office 365 detects the QR code phishing as the attack pattern evolves. The platform detection capabilities offer online protection depending upon the specific license. The following are the capabilities of Microsoft Defender for Office 365:
Image Detection
The system extracts URL metadata from a QR Code and feeds that signal into our existing threat protection and URL filtering capabilities. These signals can also send the underlying URL to a sandbox environment for detonation, and malicious threats are proactively identified and blocked before they reach a user’s mailbox.
Threat Signals
Defender for Office 365 and Exchange Online Protection uses various mail flow signals to determine and act on a message. Essentially, no single input determines the final classification of an email. It is always a composite of several signals to construct a robust context.
URL Analysis
The URLs extracted from QR Codes are analyzed by machine learning models, checked against both internal and external sources of reputation and, for Microsoft Defender for Office 365 Plan 1 / Plan 2 licenses, sandboxed for further investigation as needed to assess the risk of detonation.
Heuristics-based Rules
This capability constitutes one of our most flexible and fastest-moving mitigations, and it is used extensively to mitigate attack patterns as they morph daily during major campaigns such as QR Code phishing.
#2 Cofense
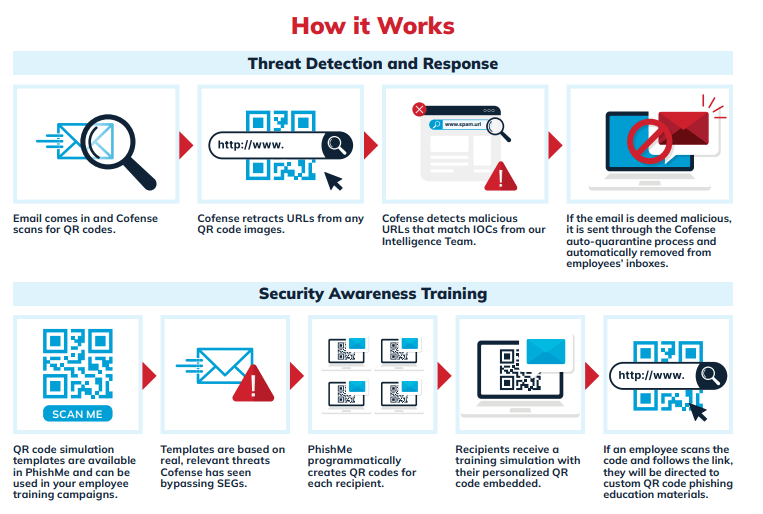
Cofense is a leading provider of email security solutions, offering QR code training simulations and real-time phishing content to educate employees on emerging threats. Our email threat detection and response solution equips Security Operations Centers (SOCs) with tools to identify and remove QR code threats automatically. Leveraging phishing intelligence from 35+ million human reporters globally, Cofense delivers the industry’s most comprehensive QR code solution.
#3 Abnormal Security
 Abnormal detects QR Code Phishing attacks by analyzing behavioral signals to identify communication patterns commonly associated with attacks. It then parses the QR code to determine if the associated link is suspicious.
Abnormal detects QR Code Phishing attacks by analyzing behavioral signals to identify communication patterns commonly associated with attacks. It then parses the QR code to determine if the associated link is suspicious.
Abnormal detects malicious QR codes through the following methods:
- Link Parsing: It parses links embedded in images like QR codes and sends the extracted signals to the AI-native detection engine.
- Natural Language Processing/Understanding (NLP/NLU): Abnormal utilizes NLP/NLU to identify fraudulent topics, tone, sentiment, urgency, and formality often linked with QR code-based attacks.
- Behavioral Analysis: It detects unusual behavioral signals by comprehending typical business relationships and communication patterns.
#4 DarkTrace
Darktrace recognizes all emails as spoofing and impersonation attempts and applies the relevant tags to them, namely “IT Impersonation” and “Fake Account Alert,” depending on the choice of personal field and subject. The senders of the five emails had no prior history or association with the recipient or the company, as no previous correspondence had been observed between the sender and recipient.
DarkTrace uses the following to prevent attacks:
- Anomaly Detection
- QR Code Scanning and Link Analysis
- Blocking Phishing attempts
Conclusion
Phishing attacks are dynamic and can pose major risks to financial loss, compromised sensitive data, and other valuable assets. Utilizing QR codes to execute such schemes has become increasingly prevalent as technology evolves, moving toward digital transformation. QR codes are used for everything from accessing digital menus in restaurants to making mobile payments, so there seems to be an embedded sense of trust associated with them, especially from familiar sources.
However, security measures have to be sought and cared for by individuals and organizations. QR code scanning must be done very vigilantly to avoid becoming a victim of phishing attempts masquerading behind the innocuous-looking QR codes. It is very important to be duly careful and confirm the source before scanning.
FAQs
1. When were QR codes invented?
In 1994, Japan invented QR Codes for the automotive company Denso Wave. The invention was to assist in labeling.
2. How do threat actors employ QR codes for phishing?
Threat actors employ QR codes as deceptive tools for conducting phishing scams. By embedding malicious code within these codes, they deceive unsuspecting users into scanning them, redirecting them to fraudulent websites or installing malware on their devices.
3. What is the sequence of QR Code Attack?
Cybercriminals employ a systematic approach to deceive users, known as the “QR Code Attack Sequence”:
- The user receives and opens an email.
- The user scans the QR Code using a mobile device.
- The user is redirected to a phishing webpage.
- The user is then prompted to enter their credentials.
4. What are the common types of QR Code phishing attacks?
- Malware downloads.
- Invoice fraud.
- Login hijacking.
- Email impersonation.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]


