Introduction
IT security, commonly known as cybersecurity, involves safeguarding computers, servers, mobile devices, electronic systems, networks, and data from digital threats. These threats range from malicious software, such as viruses and ransomware, to unauthorized access and data breaches.

A report by Cybersecurity Ventures predicts that global cybercrime costs will surpass $10.5 trillion annually by 2025, highlighting the critical need for robust cybersecurity measures. Data protection and privacy stand out as paramount concerns in this landscape.
Encryption emerges as a potent and reliable solution for securing data. It transforms information into an unreadable format, ensuring only authorized parties possessing the corresponding decryption key can access and comprehend the data.
Understanding Encryption
What is Encryption?
Google Cloud’s definition: Encryption is the process of protecting information or data by using mathematical models to scramble it in such a way that only the parties who have the key to unscramble it can access it. That process can range from very simple to very complex, and mathematicians and computer scientists have invented specific forms of encryption that are used to protect information and data that consumers and businesses rely on every day.
Encryption is a vital aspect of securing various information technology (IT) assets, serving the following purposes:
- Confidentiality: Encodes the content of the message.
- Authentication: Verifies the origin of a message.
- Integrity: Ensures the contents of a message remain unchanged since being sent.
- Nonrepudiation: Prevents senders from denying sending the encrypted message.
Encryption is commonly employed to safeguard data in transit and at rest. It is extensively used in everyday activities, such as ATM transactions and online purchases via smartphones, to protect transmitted information. Businesses increasingly rely on encryption to shield applications and sensitive data from potential reputational damage from data breaches.
An encryption system comprises three key components: the data, the encryption engine, and the key management. However, in application architectures, these components are typically distributed to mitigate the risk of compromising the entire system in case of a single component breach.
Encryption Algorithms
Symmetric Encryption:
All parties use a single key for encryption and decryption in this encryption type. For instance, when you encrypt an email with a unique key, your recipient, Tom, uses the same symmetric key to unlock or decrypt the email. 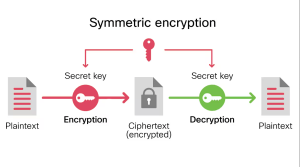
Practical examples of symmetric encryption include:
- Secure Messaging Apps (e.g., WhatsApp, Signal):
- Uses symmetric encryption (e.g., Signal Protocol) for end-to-end encrypted messages.
- File Encryption Software (e.g., VeraCrypt, AxCrypt):
- Employs symmetric encryption algorithms like AES to protect sensitive data on devices.
- BitLocker:
- Activated on Windows computers to encrypt hard drives. The user unlocks the PC with a passcode to decrypt data without exposing the encryption key.
Asymmetric Encryption:
In contrast, asymmetric encryption addresses the challenge of sharing a single encryption key for encryption and decryption.
P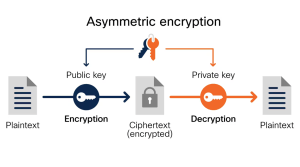 ractical examples of asymmetric encryption include:
ractical examples of asymmetric encryption include:
- Secure Email Communications (e.g., PGP, S/MIME):
- Utilizes asymmetric encryption in secure email protocols (e.g., PGP, S/MIME) for confidentiality and message integrity.
- Digital Signatures for Document Authenticity (e.g., Adobe Sign, DocuSign):
- Asymmetric encryption is used in digital signature services (e.g., Adobe Sign, DocuSign) to verify document authenticity and integrity.
- Secure Key Exchange in SSL/TLS Protocol for Websites:
- Asymmetric encryption is vital in SSL/TLS protocols for secure key exchange between a user’s browser and a website. This ensures efficient and secure communication by combining the security advantages of asymmetric encryption with the speed of symmetric encryption.
Types of Encryption
- Bring Your Own Encryption (BYOE): BYOE is a cloud security model that allows customers to use their encryption software and manage encryption keys. It deploys virtualized encryption software alongside cloud-hosted business applications.
- Cloud Storage Encryption: Cloud storage providers transform data using encryption algorithms before placing it in cloud storage. Customers must understand provider policies to match encryption with data sensitivity.
- Column-level Encryption: Database encryption where every cell in a column has the same password for access, reading, and writing.
- Deniable Encryption: Cryptography enables encrypted text to be decrypted in multiple ways for misinformation or anticipating interception.
- Encryption as a Service (EaaS): A subscription model for cloud customers lacking resources to manage encryption. Addresses regulatory compliance concerns and protects data in multi-tenant environments.
- End-to-End Encryption (E2EE): Ensures attackers cannot view data sent between parties. Implemented through encrypted communication circuits like TLS and messaging apps (e.g., WhatsApp, Signal).
- Field-level Encryption: Encrypts specific fields on a webpage, such as credit card or health-related information.
- Full-Disk Encryption (FDE): Hardware-level encryption converts data into an unreadable form. Data remains inaccessible without the authentication key, even if the hard drive is moved to another machine.
- Homomorphic Encryption: Converts data into ciphertext, allowing analysis without compromising encryption. Enables mathematical operations on encrypted data.
- HTTPS (HTTP over TLS): Enables website encryption by running HTTP over the TLS protocol. Requires a public key certificate for all content sent by a web server.
- Link-level Encryption: Encrypts data when it leaves the host, decrypts at the next link, and re-encrypts before reaching the recipient. Each link may use different keys or algorithms.
- Network-level Encryption: Applies crypto-services at the network transfer layer using IPsec standards for private communication over IP networks.
- Quantum Cryptography: Utilizes quantum mechanical properties to protect data. Quantum-encoded data cannot be copied without changing or notifying of any unauthorized access.
Encryption and Regulatory Compliance
Encryption aims to secure data by transforming it into a format that can only be read or processed after decrypting, which requires a specific key or method. Regulatory compliance, on the other hand, refers to the requirement that organizations follow laws, regulations, and guidelines relevant to their operations, particularly those that govern data protection and privacy.
Key Regulations Influencing Encryption:
- General Data Protection Regulation (GDPR): This EU regulation mandates the protection of personal data and privacy for individuals within the European Union and the European Economic Area. It requires data processors and controllers to implement appropriate technical measures, like encryption, to secure personal data.
- Health Insurance Portability and Accountability Act (HIPAA): In the United States, HIPAA requires protection of sensitive patient health information. Encryption is recommended as a security measure to protect health information stored or transmitted electronically.
- Payment Card Industry Data Security Standard (PCI DSS): This standard requires merchants and other entities that handle credit card information to protect cardholder data. Encryption is a key requirement for data in transit and at rest.
- Sarbanes-Oxley Act (SOX): SOX affects publicly traded companies and their financial practices, including the secure management of electronic records. While not explicitly mandating encryption, the act’s requirements for data protection can necessitate encryption to ensure the confidentiality and integrity of financial data.
- Federal Information Security Management Act (FISMA): FISMA requires federal agencies in the U.S. to develop, document, and implement an information security and protection program. Encryption is a critical component in safeguarding federal information and assets.
Challenges and Solutions in Encryption Implementation
Exploring Challenges
- Managing Encryption Keys: Key management requires significant overhead and is complex due to the need to protect, store, back up, and organize encryption keys effectively. This complexity increases with the scale of an organization’s operations and the volume of data to be secured.
- Accessing Encrypted Data: Accessing encrypted data is a common issue, as encryption can complicate retrieval processes, making it challenging for authorized users to access the data efficiently.
- Performance Issues: Key management systems can sometimes hinder performance, impacting the speed and efficiency of systems that rely on encrypted data.
- Integration with Cloud-Based Systems: Integrating encryption solutions with cloud-based systems often presents challenges, particularly due to infrastructure differences between on-premises environments and cloud providers.
Adopting Solutions
- Enhanced Data Security and Protection: Effective encryption key management enhances data security, minimizes the risk of data breaches, and ensures compliance with regulatory requirements, thereby providing a solid foundation for protecting sensitive information.
- Advancements in Encryption Standards: Staying updated with advancements in encryption standards, such as TLS 1.3, offers enhanced security and privacy through forward secrecy. However, this also requires strategies to address visibility challenges in monitoring network traffic.
- Automated Key Management Systems (KMS): Implementing automated KMS can reduce the overhead of managing encryption keys by automating key lifecycle management processes. This includes the rotation, storage, and deletion of keys, thereby mitigating human error and improving efficiency.
- Interoperability and Cloud Integration: Utilizing key management systems that support interoperability and integrate seamlessly with existing technology and cloud infrastructures. This approach enables organizations to leverage encryption across diverse environments without disrupting workflows.
- Restoring Visibility into Encrypted Data: Developing strategies to restore visibility into encrypted data without compromising security. This includes using advanced monitoring techniques and collaborating with industry experts to ensure effective monitoring and analysis of network traffic.
- NIST and NCCoE Initiatives: Following guidelines and participating in initiatives by the National Institute of Standards and Technology (NIST) and the National Cybersecurity Center of Excellence (NCCoE). These institutions work on addressing encryption challenges, including the automation of cryptographic module validation programs and exploring practical solutions for securing data amidst evolving encryption challenges.
A Few of the Best Encryption Software and Tools
Cisco Secure Email Encryption Service
Trend Micro Endpoint Encryption
Vaultree
IBM Security Guardium
Micro Focus CyberRes
Virtru
Emerging Trends in Encryption
Quantum Computing’s Impact
Quantum computers, on the cusp of a revolution, pose challenges and opportunities for encryption. While they may render certain methods obsolete, quantum encryption and key distribution offer theoretically unbreakable security. The evolving landscape anticipates an arms race between those creating and breaking codes.
AI and Machine Learning Integration
Fusing artificial intelligence with encryption presents challenges and innovations. AI aids in developing complex encryption algorithms and real-time threat adaptation. Machine learning, especially in traffic analysis, detects anomalies in encrypted traffic accurately, preemptively identifying potential threats.
- Fully Homomorphic Encryption (FHE) Advancement: Fully Homomorphic Encryption (FHE), a groundbreaking technique, enables computations on ciphertexts without decryption. This innovation addresses data privacy concerns, allowing operations on encrypted data and maintaining privacy during computation, especially in cloud computing scenarios.
- Adaptive and Self-Evolving Encryption: Future encryption systems may adapt to threats by changing their structure. Picture an algorithm modifying itself in response to repeated access failures or detecting patterns indicative of decryption attempts.
- Global Collaborative Standards: With advancing encryption technologies, international collaboration becomes crucial. Setting global standards through organizations like the International Standards Organization (ISO) and the National Institute of Standards and Technology (NIST) ensures interoperability and consistent security levels across borders.
Insights from the 2023 DBIR
The 2023 Data Breach Investigations Report (DBIR) offers detailed insights into cybersecurity trends, threat actor behaviors, incident types, and industry-specific data breaches that implicitly underline the importance of encryption as a defensive measure.
Encryption is a critical layer of data confidentiality and integrity protection, making unauthorized access to sensitive information significantly more challenging for cybercriminals. In the context of the DBIR’s findings, where various forms of data breaches are analyzed, it’s clear that encryption can mitigate the impact of breaches involving data exfiltration or unauthorized access.
Here are some considerations derived from the report that highlight the benefits of investing in encryption:
- Data Breach Trends: The report details the prevalent methods used by threat actors, such as exploiting vulnerabilities, using stolen credentials, and deploying malware, including ransomware. Encryption can render stolen data useless to attackers, particularly in cases where data exfiltration occurs.
- Threat Actor Motivations: With financial gain being a primary motive for a significant percentage of breaches, encrypting sensitive data can reduce the potential financial rewards for cybercriminals, lowering the target attractiveness.
- Industry-Specific Insights: Different industries face varying levels of risk and types of threats. Encryption strategies can be tailored to protect each sector’s most sensitive and targeted data, aligning cybersecurity investments with specific industry risks.
- Incident Types and Patterns: Understanding the common incident patterns and types that affect organizations can guide where to prioritize encryption efforts. For example, sectors more prone to web application attacks might focus on encrypting data transmitted to and stored on web servers.
- Compliance and Regulatory Requirements: Many industries are subject to regulations that mandate the protection of personal and sensitive data. Encryption can help organizations meet these requirements, avoid regulatory fines, and maintain customer trust.
Case Studies: Successful Implementation of Encryption
Case Study Overview from Thales Group
The Thales Group case study highlights a major European energy provider implementing comprehensive encryption across all customer data, focusing on securing business-critical and sensitive information. This initiative was part of their broader strategy to protect financial assets and sensitive data in the face of evolving security challenges within the financial services industry. Thales Group’s solutions enabled the organization to meet compliance mandates across various jurisdictions, including GDPR, PCI DSS, HIPAA, and more, by implementing strong authentication methods and data protection strategies for cloud services, IoT, and software applications.
Key Takeaways
- Customized Encryption Strategies: emphasize the importance of tailored encryption strategies that align with specific business needs and compliance requirements.
- Comprehensive Data Protection: Implementing encryption across all customer data ensures comprehensive protection against unauthorized access and data breaches.
- Compliance and Regulation Adherence: Meeting global and regional compliance mandates is critical to successful encryption strategies in B2B enterprises.
- Advanced Encryption Technologies: Advanced encryption technologies and services, including cloud and on-premises solutions, provide a robust framework for securing sensitive business data.
In a Nutshell
In an era where data is crucial, protecting it is essential. Encryption serves as a strong defense, blocking unauthorized access to sensitive information. By using encryption techniques and following protocols, you can enhance data security and ensure the safety of valuable assets.
Take control of your data security now! Partner with CMS IT Services to implement cutting-edge encryption solutions, strengthening your databases against potential threats. Safeguard your organization’s reputation and build customer trust with our specialized data security services.
FAQs on IT Security and Encryption
- What is IT security, and why is it important?IT security, or cybersecurity, involves protecting computers, networks, and data from digital threats like viruses and unauthorized access. It is crucial to safeguard valuable assets and prevent data breaches.
- Why is encryption important in IT security?Encryption transforms data into an unreadable format, ensuring only authorized parties with the decryption key can access it. It is vital for maintaining confidentiality, authentication, integrity, and nonrepudiation in various IT assets.
- What are the main purposes of encryption in information technology (IT)?Encryption in IT serves the purposes of confidentiality (encoding message content), authentication (verifying message origin), integrity (ensuring message content remains unchanged), and nonrepudiation (preventing senders from denying sending messages).
- What are the common encryption algorithms used in IT security?Two main types are symmetric encryption (using a single key for encryption and decryption) and asymmetric encryption (using different keys for encryption and decryption). Examples include AES for symmetric and PGP for asymmetric encryption.
- How is encryption applied in everyday activities like online transactions?Encryption is widely used in activities such as ATM transactions and online purchases via smartphones to protect transmitted information and prevent reputational damage from potential data breaches.
[To share your insights with us, please write to sghosh@martechseries.com]


