Gone are the days when basic antivirus software sufficed. Organizations are increasingly aware of advanced cyberattacks and demand a more robust defense. This is when Endpoint Detection and Response (EDR) comes in.
The rise of remote work has expanded the attack surface, with employees accessing networks from various devices and locations. EDR provides the essential visibility and control needed to secure these diverse endpoints. It goes beyond traditional defenses by:
- Detecting advanced threats: EDR can identify sophisticated malware, zero-day attacks, and persistent threats that might bypass legacy solutions.
- Offering real-time insights: EDR continuously monitors endpoints, providing immediate threat detection and allowing for swift response.
- Automating actions: EDR can automate responses to contain threats, minimizing damage and saving valuable time.
Despite its advantages, some organizations struggle with EDR implementation due to skilled personnel shortages, budget constraints, and integration complexities. According to Exactitiude Consultancy report, the market size of global Endpoint Detection & Response (EDR) is predicted to grow from USD 2.65 Billion in 2023 to USD 9.50 Billion by 2030, at a CAGR of 20% during the forecast period. The benefits of EDR are undeniable. It’s a vital investment for businesses looking to:
- Gain comprehensive endpoint visibility.
- Enable real-time threat detection.
- Automate response actions.
With the rapid evolution of cyber threats, EDR solutions are also evolving. This article will explore EDR’s future through the lens of Managed Security Operations Centers (MSOCs). We’ll understand how EDR will adapt to address emerging challenges.
What is Endpoint Detection and Response?
Endpoint Detection and Response, or endpoint detection and threat response (EDTR), is an endpoint security solution that constantly monitors end-user devices to detect and respond to cyber threats like ransomware and malware.
EDR, the term coined by Gartner’s Anton Chuvakin, is a solution that “records and stores endpoint-system-level behaviors, uses various data analytics techniques to detect suspicious system behavior, provides contextual information, blocks malicious activity, and provides remediation suggestions to restore affected systems.”
EDR security solutions help security teams monitor endpoints and workloads for hidden threats. By recording activities and events, EDR brings improved visibility, allowing security professionals to uncover incidents that traditional methods might miss.
For comprehensive defense, an EDR solution should be a well-armed investigator. It should provide advanced threat detection, investigation, and response capabilities. This includes features like incident data search and triage, validation of suspicious activities, proactive threat hunting, and the power to contain malicious activity.
Five Features of EDR Solutions
EDR features that must be known include automated remediation, behavioral analytics, vulnerability management, threat intelligence integrations, and device monitoring and control.
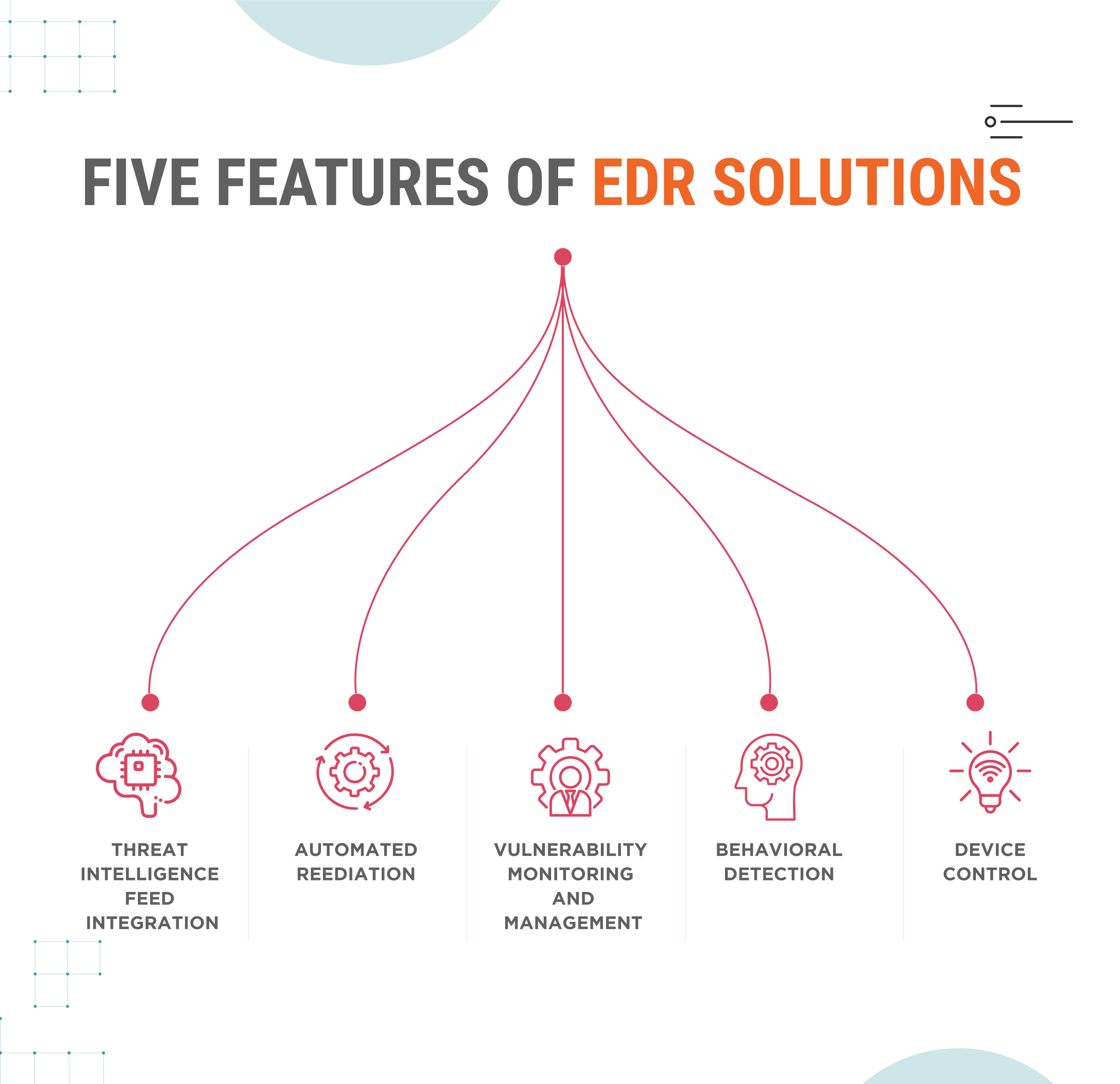 Threat Intelligence Feed Integration
Threat Intelligence Feed Integration
Threat intelligence integrations are required, as they include threats, indicators of compromise (IoC), and more, so the security team can assess a wide range of behaviors and threats. EDR tools combine with third-party threat intel solutions so that security teams have ample information to keep the business on top of vulnerabilities.
Automated Remediation
Security teams configure automatic threat remediation by setting remediation rules in advance or using prebuilt ones. A particular action on an endpoint prompts a predefined remediation policy without human interaction. The EDR tool sets remediation in motion. Automation is helpful because it lessens manual remediation work for security admins. It’s a particularly good feature for small security teams.
Vulnerability Monitoring & Management
EDR solutions constantly monitor endpoints, warning security teams when the software discovers vulnerabilities that could be exploited. These include outdated operating systems, backdoors, and misconfigurations. Automated searches for vulnerabilities are more efficient and allow IT and security teams to catch vulnerabilities quickly and spend time on other tasks.
Behavioral Detection
EDR leverages the power of machine learning technology to analyze a vast ocean of user and device behaviors. This allows it to spot anomalies that might signal a cybercriminal at work or a sneaky malware infection. Unlike manual methods, behavioral detection sifts through massive amounts of data to automatically pinpoint potential threats, saving security teams precious time. It’s a game-changer, especially when facing never-before-seen attacks (zero-day attacks).
Device Control
EDR solutions screen USB devices and other direct-attached storage for malicious behavior. Threat actors use USB and flash drives to infect systems with malware, and employees often plug unknown storage devices into computers without knowing what’s on them. EDR tools allow admins to set strict policies for device use and determine when to give remote access permissions to USB devices.
Key Functions of Endpoint Detection and Response (EDR)
Exposes Hidden Attackers
EDR technology combines complete visibility across all endpoints with IOAs and applies behavioral analytics, which analyzes billions of events in real time to detect traces of suspicious behavior automatically.
Understanding individual events as part of a broader sequence allows the EDR tool to apply security logic derived from Intelligence. The EDR tool will identify the activity as malicious and automatically send a detection alert if the sequence of events matches a known IOA.
Incorporates Threat Intelligence
Integration with cyber threat intelligence provides faster detection of the activities, tactics, techniques, and procedures (TTPs) identified as malicious. This delivers contextualized information that includes attribution where relevant, offering details on the rival and any related information known about the attack.
Managed Threat Hunting for Proactive Defense
EDR empowers your security team to become cyber detectives. They can proactively hunt for threats lurking within your environment, investigate suspicious activity, and advise on the necessary action. This collaborative approach ensures threats are identified and contained before they escalate into full-blown breaches.
Real-time and Historical Visibility Offering
Think of EDR as a security DVR for your endpoints. It continuously records critical events, like process creation, driver loading, and network connections, clearly showing what’s happening on your devices. This unmatched visibility helps uncover hidden threats that might have bypassed traditional security measures.
Accelerates Investigations
Endpoint detection and response can increase the speed of investigation and, ultimately, remediation because the information gathered from your endpoints is stored in the cloud, which has an architecture based on a situational model.
Using a massive, powerful graph database, the model tracks all the relationships and contacts between each endpoint event. This database provides details and context rapidly and at scale for both historical and real-time data, enabling security teams to investigate incidents quickly.
This speed and level of visibility, combined with integrated, contextualized intelligence, provides the information needed to understand the data thoroughly. This enables security teams to effectively track even the most sophisticated attacks and promptly uncover incidents, triage, validate and prioritize them, leading to faster and more precise remediation.
Benefits EDR for Cybersecurity
- EDR as Your Security Watchdog: EDR acts as your company’s security watchdog, continuously monitoring endpoints and the network. This real-time visibility empowers you to detect and swiftly respond to threats, including malicious traffic like malware and ransomware.
- Deep Dives and Forensics: EDR dives deep into endpoints, revealing details on processes, applications, files, and registry settings. This allows for swift threat identification, remediation, and even prevention. Additionally, EDR monitors user activity, helping you spot suspicious behavior and stay ahead of potential threats.
- Compliance Made Easy: Many industries face regulations like HIPAA and GDPR regarding data storage and access. EDR simplifies compliance by enabling you to monitor for suspicious activity and investigate potential threats. This proactive approach ensures adherence to industry standards. Furthermore, EDR helps identify potential compliance issues before they arise, allowing for swift corrective actions. Detailed reports generated by EDR serve as valuable documentation for demonstrating compliance to auditors.
- Reducing Your Risk Landscape: EDR continuously monitors your environment, minimizing your risk profile. By enabling rapid threat detection and response, EDR helps you mitigate the impact of attacks. The detailed information gleaned from EDR allows you to identify and patch vulnerabilities before they’re exploited. As mentioned earlier, EDR’s user activity monitoring helps reduce the risk of malicious insider attacks. Finally, comprehensive threat reports from EDR empower you to manage your overall security posture proactively.
- Cost Savings Through Security: EDR translates into cost savings by minimizing the financial burden of security incidents. The continuous monitoring allows for swift threat detection and response, reducing the potential damage from an attack. EDR also helps identify and remediate threats quickly, potentially avoiding fines or penalties associated with breaches. Ultimately, EDR helps prevent costly security incidents, saving your company money in the long run.
- Building a Robust Security Posture: EDR strengthens your overall security posture by offering a multi-layered defense. It minimizes false positives while effectively detecting real threats, allowing for a swift and appropriate response. This proactive approach safeguards your business from unauthorized access attempts to steal sensitive information.
Also Read: CIO’s Guide to Preventing Ransomware Attacks in B2B Enterprises
9 Must-Haves for Your EDR
The top 9 features to consider when picking the perfect EDR solution for your business.
- Future-Proof Protection: Can it handle today’s threats and adapt to what’s coming?
- Ransomware Shield: Does it defend against ransomware attacks, even on offline devices (using AI/ML)?
- Beyond Marketing Hype: Look past vendor claims. Check MITRE ATT&CK results – are they stopping attacks, not just detecting them?
- Guarding the Core: Does it prevent tampering with your device’s firmware (like a firewall for the core)?
- OS Compatibility: Does it work on all your devices, even those with older operating systems? Are server and workstation licenses separate?
- Lightweight Champion: Choose a solution that won’t slow down your systems (aim for less than 1% CPU usage).
- Automating the Fight: Does it automate tasks (unlike basic antivirus)? Look for a strong policy engine and integrations with other security tools.
- XDR: Beyond the Buzzword: Don’t be fooled by “XDR” claims. Choose established companies with built-in SIEM and SOAR, not solutions relying heavily on third-party connections.
- Managed Security Backup: To help your security team, consider EDR with Managed Detection and Response (MDR) services. Ask about deployment options, the MDR team’s expertise, and global support.
Top EDR Solutions
#1 CrowdStrike Falcon Insight
CrowdStrike Falcon Insight caters to teams seeking a powerful EDR solution with extensive response capabilities. While renowned for its near-perfect MITRE scores and robust security, CrowdStrike empowers the team’s threat management expertise.
Falcon Insight equips your team with advanced features like threat hunting, prioritization, and security posture assessments. These tools empower them to identify, analyze, and respond to threats efficiently.
CrowdStrike actively invests in XDR, expanding its reach to cloud, network, and managed protection services. Falcon Insight can become a springboard for your team’s security growth, offering them opportunities to hone their expertise in a constantly evolving threat landscape.
Key Features:
- Threat Response Arsenal: Includes threat hunting, prioritization tools, and security posture assessments for a comprehensive response strategy.
- In-Depth Threat Visibility: Falcon Sandbox allows deep analysis of unknown malware, and Falcon Insight provides threat attribution with MITRE ATT&CK mapping to provide a thorough understanding of detections.
#2 Cynet 360 AutoXDR
 Cynet 360 AutoXDR simplifies security management for organizations with hybrid infrastructure. It offers on-premises, cloud (SaaS and IaaS), and hybrid deployment options, providing flexibility for your needs.
Cynet 360 AutoXDR simplifies security management for organizations with hybrid infrastructure. It offers on-premises, cloud (SaaS and IaaS), and hybrid deployment options, providing flexibility for your needs.
Built-in MDR for Mid-Sized Businesses:
For mid-sized businesses seeking a comprehensive XDR solution with MDR (Managed Detection and Response) capabilities, Cynet 360 AutoXDR stands out. MDR services are free, providing expert security analysts to bolster your team’s threat response efforts.
Deception and Integration Powerhouse:
Cynet shines in its use of deception technology and strong integration capabilities. Honeypots lure attackers, helping to identify malicious activity proactively. Additionally, Cynet integrates seamlessly with RMM solutions and Active Directory, streamlining your security workflow.
Key Features Removed:
- Cynet Responder, Asset Inventory, and Device Control: These features are generic to many EDR solutions and might create confusion.
#3 Palo Alto Cortex XDR
For security teams seeking an advanced feature set, Palo Alto Cortex XDR stands out. With capabilities like sandboxing and forensics tools, it empowers in-depth threat analysis. Backed by perfect scores in the 2023 MITRE tests, Cortex XDR leverages Palo Alto’s established security expertise.
Built for Scalability:
Cortex XDR is a cloud-native platform that ensures scalability and ease of deployment. Its open API allows it to integrate seamlessly with existing security tools, allowing you to build a cohesive security ecosystem.
Ideal for Large Enterprises:
Cortex XDR is a powerful solution for large enterprises with dedicated IT and security teams. Its advanced features and robust protection can be a game-changer for your organization’s security posture – potentially one of the best security investments you can make.
Key Features Removed:
- Cynet Responder, Deception technology, Asset inventory, and Device control: These features are not specific to Palo Alto Cortex XDR and might create confusion.
#4 Cybereason Defense
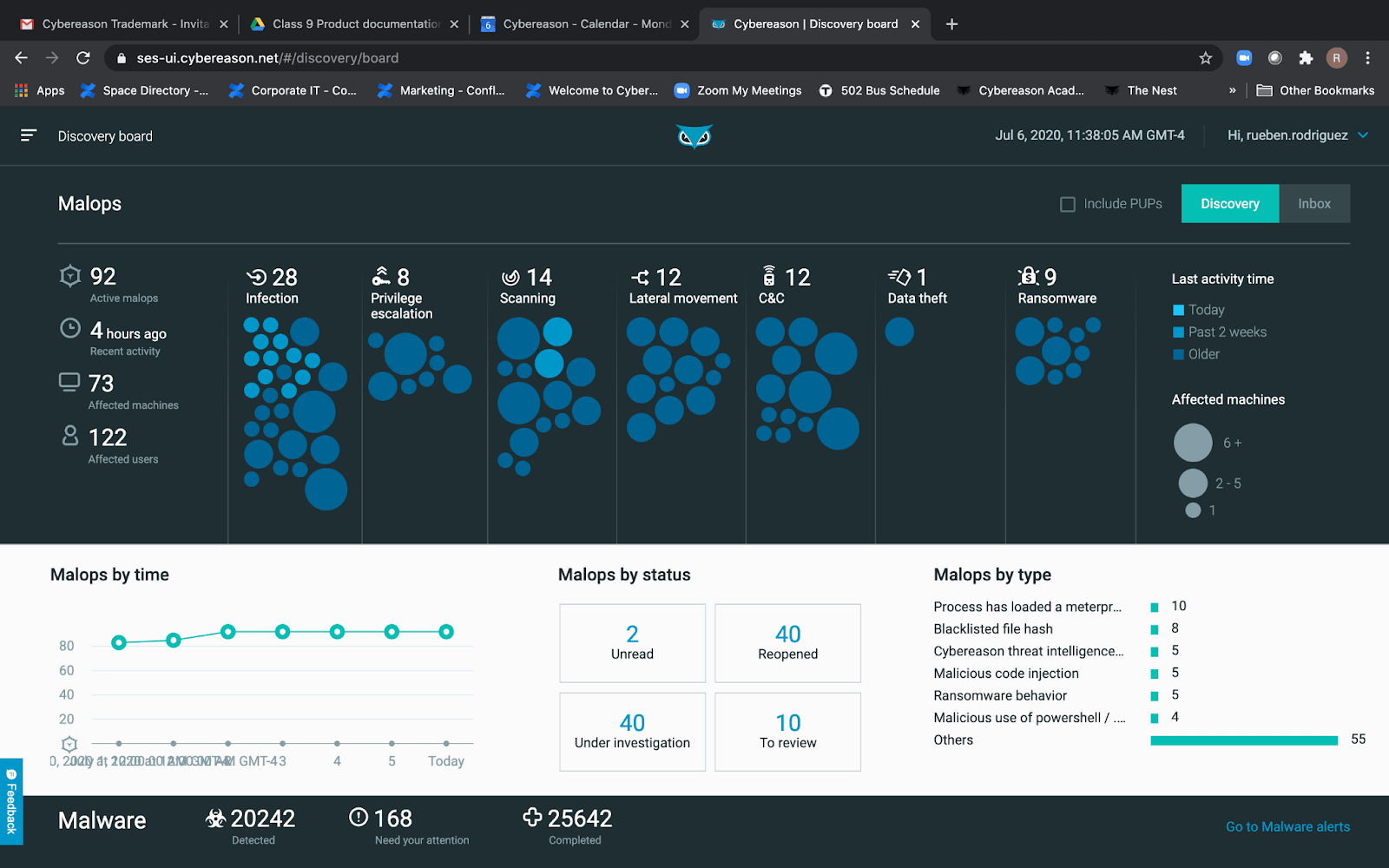 Cybereason’s Defense Platform stands out for its robust detection and response capabilities, backed by extensive documentation and training resources. It impressed this year’s MITRE tests, achieving a perfect detection score and missing only one step out of 143 evaluated.
Cybereason’s Defense Platform stands out for its robust detection and response capabilities, backed by extensive documentation and training resources. It impressed this year’s MITRE tests, achieving a perfect detection score and missing only one step out of 143 evaluated.
Decoding Malicious Operations (MalOps):
Cybereason takes a comprehensive approach, analyzing threat data to build a detailed “attack story” that provides a rich context for security teams. This focus on MalOps makes Cybereason ideal if your team prioritizes in-depth threat visualizations.
Pros:
- Strong Detection and Visualization: Achieves near-perfect scores in MITRE tests and offers detailed attack story visualizations.
- Cloud-Ready: Protects public cloud environments and analyzes cloud workloads, including containers.
- Extensive Resources: Provides thorough documentation and training materials.
Cons:
- No F*********: Limits hands-on evaluation before purchase.
- No Rogue Device Discovery: Cannot identify unauthorized devices.
- Limited Pricing Transparency: Pricing information may require contacting sales.
Key Features:
- Cloud Integrations: Supports major cloud providers like Google Cloud Platform, Amazon Web Services, and Microsoft Azure.
- Cloud Workload Analysis: Extends XDR capabilities to containerized environments.
- Digital Forensics: Offers root cause analysis tools for in-depth incident investigations.
- MalOps Visualizations: Centralizes data to comprehensively view threats through attack story visualizations.
#5 Trend Micro Vision One
Trend Micro XDR, built on the Vision One platform, goes beyond just XDR. It offers a comprehensive attack surface management solution, making it a strong contender in the security landscape. Their impressive security suite spans cloud, containers, network security, and endpoints, providing a holistic approach.
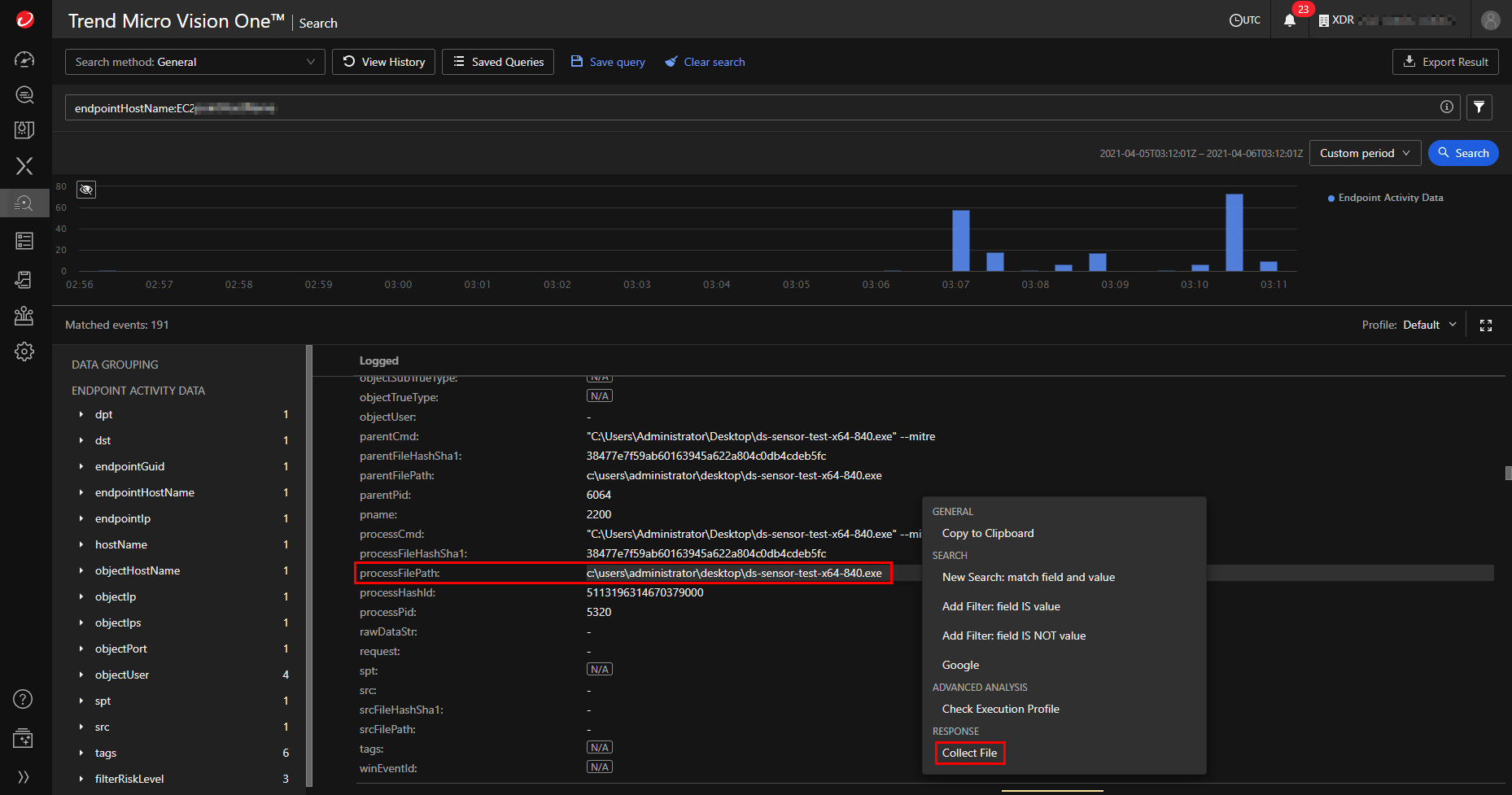
Built for Integration:
Vision One integrates seamlessly with third-party security solutions like Splunk, IBM QRadar, and Palo Alto Cortex XSOAR. This makes it ideal for businesses with existing security infrastructure, allowing them to build a cohesive and centralized system.
Scalable Security:
Trend Micro offers managed XDR services, which are perfect for smaller organizations lacking extensive IT resources. These services allow them to benefit from XDR’s capabilities without the burden of managing it in-house.
Key Features:
- Guided Investigation: This feature assists security teams in identifying the best remediation strategies for discovered threats.
- Expert-Driven Detection Rules: Trend Micro continuously updates detection rules based on the latest threat intelligence from their security experts.
- Dynamic Policy Adjustments: Vision One automatically recommends policy adjustments based on real-time insights gleaned from the platform.
- Customized Dashboards: Role-based dashboards provide tailored views of security posture, empowering different teams to focus on specific areas.
#6 Microsoft Defender XDR
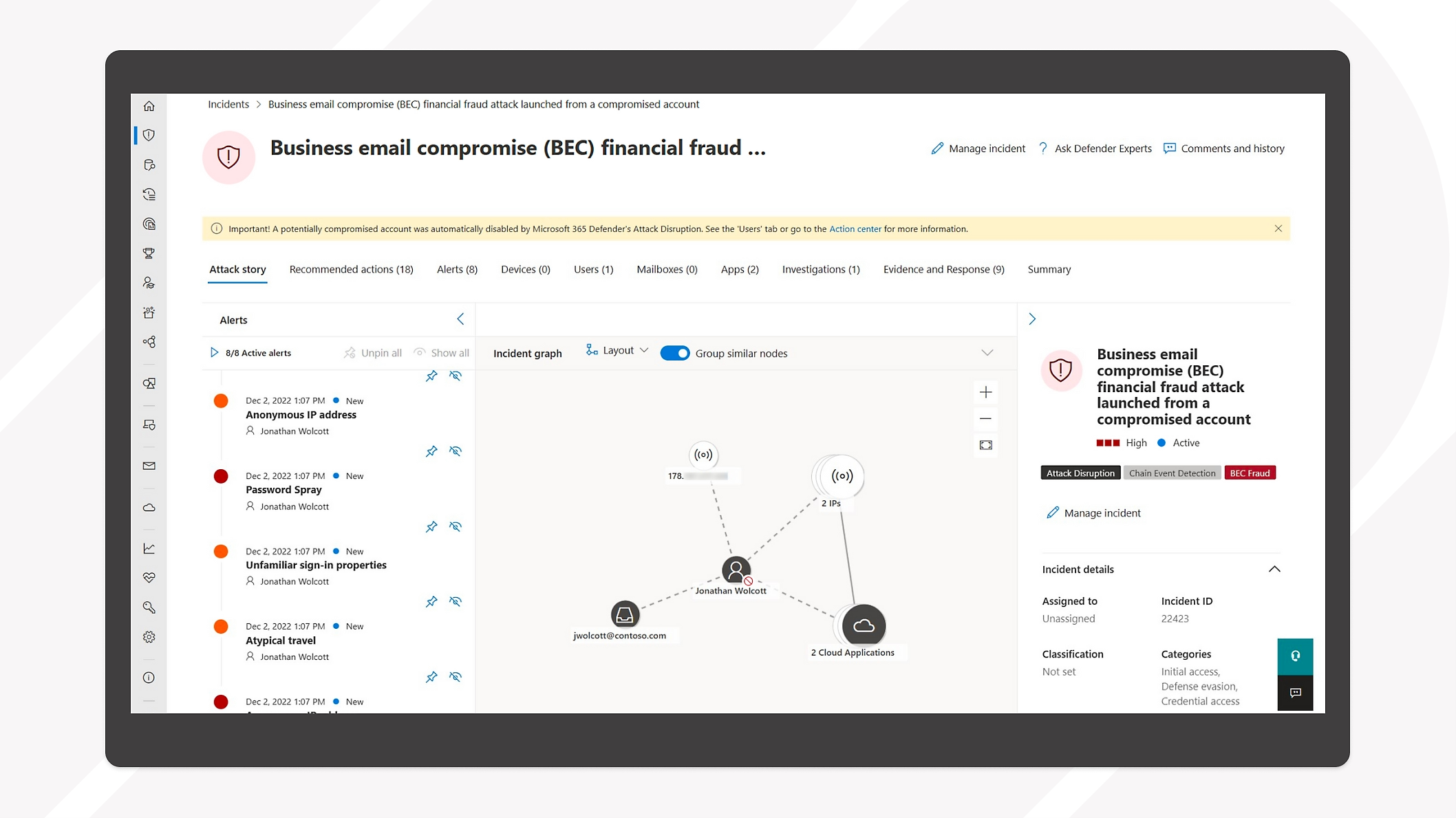 Microsoft Defender XDR is a detection and response solution software for endpoints, cloud apps, collaboration software, and identity management. Microsoft has a proven track record in security, consistently achieving high scores in MITRE evaluations. Defender XDR is a compelling choice if you prioritize ease of use and comprehensive documentation. Moreover, Microsoft offers many training videos to empower you and your team to leverage Defender XDR’s full potential.
Microsoft Defender XDR is a detection and response solution software for endpoints, cloud apps, collaboration software, and identity management. Microsoft has a proven track record in security, consistently achieving high scores in MITRE evaluations. Defender XDR is a compelling choice if you prioritize ease of use and comprehensive documentation. Moreover, Microsoft offers many training videos to empower you and your team to leverage Defender XDR’s full potential.
It’s challenging to integrate a large number of third-party apps with Defender. However, it’s a good choice for teams with an existing Windows ecosystem. Defender also offers many advanced EDR features, such as threat hunting and incident triage, for teams that need those.
Also Read: Top 10 Endpoint Management Software Picks for CIOs
Advantages:
- Ease of use and customer support
- Strong security performance per MITRE scores
- Works well with other Microsoft products
Features of Microsoft Defender XDR
- Automated remediation: Automatic incident response helps teams prioritize threats.
- Sandboxing: Intensive malware analysis allows teams to explore behavior in detail.
- Third-party integrations: Partner products include Splunk and Bitdefender GravityZone.
- Unchecked device mapping: Defender XDR helps teams find unprotected devices.
EDR Trends of 2024
Endpoint Detection and Response (EDR) has become a vital security tool, but it’s constantly adapting to address the evolving threat landscape. Here are some key trends shaping the future of EDR:
1. Expanding Reach: Beyond Desktops
- Mobile Device Management: The rise of remote work necessitates mobile device security. EDR solutions incorporate mobile device management (MDM) to protect smartphones and tablets.
- Addressing IT Complexity: Modern IT environments are complex, with a mix of on-premises, cloud-based, and virtual systems. EDR adapts to this complexity by focusing on browser security, zero-trust principles, and cloud application integration.
2. New Threats, New Focus
- Supply Chain and Third-Party Risks: Attacks targeting third-party endpoints and the supply chain are rising. EDR solutions are evolving to encompass these endpoints and offer features for isolating third-party content.
- BEC vs. Ransomware: Business Email Compromise (BEC) attacks surpass ransomware as a top concern. EDR solutions are being enhanced to prioritize the detection and mitigation of BEC attempts.
3. The Future of EDR
- Deeper Integration: Expect stronger integration between EDR and other security tools like SIEM, NTA, and vulnerability scanners. This unified approach will provide a holistic view of security posture and streamline threat response.
- Mobile and IoT Security: As mobile and IoT devices proliferate, EDR solutions will expand to secure these endpoints effectively, addressing their unique security challenges.
- Cloud-Native EDR: With the rise of cloud adoption, cloud-native EDR solutions will gain traction. These solutions offer scalability, flexibility, and cost-efficiency for managing security across hybrid and multi-cloud environments.
4. AI, Zero Trust, and the Evolving Threat Landscape
EDR solutions are constantly innovating to combat ever-more-sophisticated cyberattacks. Here are some key trends shaping the future of endpoint security:
- AI and Machine Learning Take Center Stage:
Fueled by advancements like ChatGPT, AI and machine learning (ML) are poised for a significant leap in endpoint security. These technologies can rapidly analyze vast data, enabling real-time threat detection and mitigation. However, the game of cat and mouse continues – attackers, too, will leverage AI and ML to craft more evasive threats.
- Zero Trust Goes Mainstream:
The adoption of Zero-Trust Architecture (ZTA) will continue to surge in 2024. ZTA assumes no inherent trust and enforces strict access controls regardless of user location or device. With the rise of remote work, continuous verification of users and devices—a core ZTA principle—will be crucial for bolstering defenses. Endpoint protection is vital in ZTA, acting as the first line of defense between the external world and sensitive information.
- Securing the Broader Connected Landscape:
The proliferation of the Internet of Things (IoT) demands a broader approach to endpoint security. Solutions will evolve to secure a wider range of connected devices – not just traditional computers and mobiles – addressing the diverse threats an interconnected world poses.
- Hardware Meets Security:
The increased checkpoints associated with ZTA might lead to a rise in secure storage solutions, particularly for data at rest (DAR). We may see more adoption of certified storage devices, similar to those used in the military, to build secure and encrypted storage solutions for sensitive data.
Five Reasons Why EDR is Essential for Modern Security
Endpoint Detection and Response has become a vital tool for businesses facing today’s complex cyber threats. Here are five key use cases that highlight EDR’s growing importance:
1. Securing the Mobile Workforce:
The rise of smartphones and tablets in the workplace challenges traditional security solutions. Mobile devices often lack the robust security features of laptops and desktops, making them vulnerable targets. EDR extends its reach to mobile devices, providing consistent security across all endpoints, regardless of platform. This ensures all devices are visible and protected, eliminating blind spots in your network.
2. Staying Ahead of Evolving Threats:
Cyberattacks constantly evolve, with hackers developing new methods to bypass traditional antivirus software. EDR goes beyond signature-based detection, focusing on behavioral analysis to identify suspicious activities. This proactive approach helps detect and respond to even the latest and most sophisticated threats before they can cause significant damage.
3. Streamlining Threat Investigation:
EDR simplifies threat hunting and investigation. Traditional methods can be time-consuming and resource-intensive, leaving security teams struggling to keep up. EDR solutions provide automated alerts and investigation tools, allowing security teams to pinpoint suspicious activity and respond quickly.
4. Securing Cloud Environments:
Cloud adoption is increasing rapidly, but it also introduces new security challenges. Cloud-based resources often lack the same level of visibility as on-premises infrastructure. EDR can monitor endpoint behavior within the cloud, detecting anomalies and triggering alerts to help maintain security across hybrid and multi-cloud environments.
5. Addressing the IoT Challenge:
The Internet of Things (IoT) is transforming various industries, creating significant security concerns. Many IoT devices have weak security built-in, making them vulnerable to exploitation. EDR can help mitigate these risks by monitoring IoT device behavior and identifying potential threats before they compromise your network.
FAQs
1. Why EDR is a Cybersecurity Game Changer?
Endpoint Detection and Response (EDR) systems rely on data – a fancy way of saying detailed information collected from your devices. This constant data stream makes EDR so powerful in the fight against cyber threats.
2. What is the key difference between EDR response and reporting?
EDR(Endpoint Detection Response) solutions continuously monitor endpoints for indications of malicious behavior. EDR systems gather and examine information from various sources, including endpoint sensors, network traffic, and system logs. Using algorithms and machine learning, EDR Systems recognize dangers and highlight odd behavior that can point to an attack.
3. Why Open Source EDR: Cost-Effective Defense for Your Endpoints?
Endpoint Detection and Response (EDR) is a vital security tool, but traditional solutions can be expensive. Open-source EDR offers a compelling alternative, providing businesses with several advantages:
Cost Savings: Unlike proprietary EDR solutions, open-source options eliminate licensing fees, making them a budget-friendly choice for businesses of all sizes.
Enhanced Visibility and Control: Open-source EDR solutions provide deep visibility into endpoint activity, allowing security teams to understand what’s happening at the critical intersection between internal systems and the external internet. This empowers them to identify and address potential threats before they can cause damage.
Streamlined Security Management: Open-source EDR centralizes security controls for the most vulnerable points in the network. This simplifies security management for IT staff, allowing them to monitor and respond to threats more efficiently.
Customization and Flexibility: Open-source EDR offers greater flexibility and customization than pre-built solutions. Businesses can tailor the software to meet their specific needs and security posture.
4. EDR vs. Antivirus: What’s the Difference?
While both Endpoint Detection and Response (EDR) and antivirus software play a role in endpoint security, they have distinct functions:
- Antivirus: The Firewall Analogy
Think of antivirus software like a firewall. It acts as a first line of defense, automatically blocking known threats like malware before they can infect your system. Antivirus relies on signature-based detection, identifying threats based on pre-defined patterns.
- EDR: The Detective Approach
EDR goes beyond simple blocking. It acts more like a detective, continuously monitoring endpoint activity for suspicious behavior. This allows EDR to identify even the most sophisticated threats, including those that might evade traditional antivirus.
- Working Together for Stronger Security
EDR and antivirus can be a powerful combination. Some EDR solutions even integrate EPP (Endpoint Protection Platform) capabilities, including antivirus. This layered approach provides comprehensive protection, with antivirus acting as the initial shield and EDR offering deeper investigation and response capabilities.
5. Importance of Managed EDR for Security?
Endpoint Detection and Response (EDR) is a powerful tool for combating advanced threats. However, deploying, managing, and monitoring EDR effectively, especially for large organizations, can be a challenge.
Managed EDR solves this problem by providing you with a team of security specialists to handle everything EDR-related. Here’s how it benefits you:
- Expert Threat Management: Your EDR solution will be managed by a dedicated team of endpoint security analysts, incident responders, and security engineers.
- Enhanced Threat Detection: These experts have the experience and knowledge to distinguish normal activity from suspicious behavior, ensuring timely identification of potential threats.
- Faster Response and Resolution: The team can quickly investigate alerts, determine their severity, and initiate appropriate responses to contain threats and minimize damage.
- Actionable Insights: Based on the data collected by the EDR solution, you’ll receive ongoing feedback and guidance on improving your overall security posture.
Conclusion
It is vital for organizations seeking to protect their digital assets to keep pace as endpoint detection and response evolve. Anticipating the EDR trends shaping 2024, it’s obvious that a multi-faceted approach that covers advanced technologies, strategic architecture, user empowerment, and secure SSD storage will be crucial for building resilient and adaptive endpoint security strategies. Organizations can protect their defenses by improving these trends and confidently navigating the evolving threat landscape.
Investing in endpoint detection and response (EDR) services is one-way businesses can protect themselves from cyberattacks while ensuring compliance with industry regulations regarding how data must be stored and accessed securely within their networks.
By continuously monitoring all endpoints on their networks for malicious activity, businesses benefit from improved visibility into who is accessing what information and increased security posture, which reduces the risk of data breaches due to human error or malicious intent from outside sources attempting unauthorized access into their systems.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]


