What Is SecOps (Security Operations)?
Security Operations (SecOps) is the synergy between IT security and operations teams for integrated tooling, processes, and technology to secure the enterprise and reduce risk. As information security groups within organizations grow in importance, a gap is usually created between them and IT operations teams because they have fundamentally different focuses. This may lead to conflicting efforts, overlapping tooling, and inefficient allocation of resources, causing a weaker security posture and the elevation of organizational risk. For example, the most effective security tools may block or shut down critical applications running time-critical operations due to an assumed cyber threat.
In a SecOps approach, the security and IT operations teams collaborate and share responsibility for ensuring that the enterprise environment is secure and productive. Through proactive collaboration, visibility is gained on the organization’s security vulnerabilities, enabling security issues to be quickly resolved while IT operations maintain full flexibility and resilience.
Also Read: Top 10 AI Companies for Data Center and Edge
Functions of Security Operations
IT organizations have set up Security Operations Centers where SecOps teams work together on security activities. The SOC is considered the central nervous system of an organization’s information security; SecOps has made it more effective, automated, and integrated.
Security Monitoring
The SecOps team monitors activity across the organization, including networks, endpoints, and applications in private, public, and hybrid cloud environments. This monitoring includes security events and the operational health and performance of applications and infrastructure.
Threat Intelligence
SecOps teams utilize third-party providers for gathering threat intelligence and integrate that into security processes. Threat intelligence refers to standardized data on cybersecurity threats, which can make the security team and its tools more effective. It may add context to SIEM alerts or give lists of known malicious IP addresses for immediate blocking by firewalls. Threat intelligence comes from free and commercial feeds, which SecOps teams organize and integrate into threat intelligence platforms.
Triage and Investigation
The SecOps teams analyze and investigate security events using sophisticated tooling; however, inconsistencies in threat detection, investigation, and response processes may lead to inefficiencies and gaps in detection. Modern SIEMs bring all processes end-to-end in workflows and prepackaged analysis, thus enabling SecOps teams to standardize and automate TDIR processes, achieving better threat detection and triage from day one without complex customization.
Incident Response
SecOps teams execute incident response plans to detect and react to cyberattacks. This includes incident response planning, incident detection and analysis, threat containment and eradication, system recovery, and post-incident review to improve security processes.
Forensics and Root Cause Analysis
SecOps teams conduct forensic analysis to identify the root causes of security incidents, performance issues, and other unexpected events. They use special software to identify the details of the incident, conduct root cause analysis, and respond to threats or malfunctions to minimize harm.
Also Read: Top 10 Cybersecurity Forecasts and Statistics of 2024
SecOps Challenges Large Enterprises Face
#1 Cloud Security Challenges
- Misconfigurations Leading to Data Breaches: Misconfigured cloud services frequently cause data breaches, thus emphasizing the need for robust cloud security protocols.
- Insecure APIs and Service Interfaces: The common use of APIs has introduced vulnerabilities, whereby insecure interfaces allow cybercriminals to intercept data or bring down services.
- Managing Multi-Cloud and Hybrid Environments: Ensuring security across multiple cloud services and hybrid environments remains a complex and formidable activity for large enterprises.
#2 Supply Chain Attacks
- Increase in Attacks on Third-Party Vendors: Attackers often target third-party vendors to gain backdoor access to larger enterprises.
- Cascading Effects Across Large Enterprises: A supplier’s systems compromise would have a cascading effect through all connected businesses.
- Strengthen Supply Chain Security: Enterprises need to extend security practices and expectations to third-party vendors in order to minimize the risk of supply chain attacks.
#3 Lack of Skilled Professionals in Cybersecurity
- Effect of the Skills Gap: The gap in cybersecurity skills has become a critical issue—under qualified professionals can effectively manage and respond to security incidents.
- Outsourcing Versus In-House Security Operations: Enterprises now face a dilemma between outsourcing their SecOps and introducing new risks or building them in-house, which is costly and time-consuming.
- Skills Gap Closure Initiatives: Specialized cybersecurity training programs are underway, which help to close the skills gap, and initiatives to get young people into security careers.
#4 Regulatory and Compliance Challenges:
- Keeping up with Evolving Privacy Laws and Regulations: Businesses have to quickly adapt to continuous changes in data protection and privacy laws, like the GDPR and CCPA, just to be compliant.
- Industry-Specific Compliance Issues: Certain industries, such as healthcare and finance, have unique regulatory demands that explain issues of data management and protection.
- Cross-border data transfer and storage complications: Since data flows across borders, an enterprise must navigate the diverse set of international laws governing data transfers and storage.
SecOps Solutions to Address the Challenges
Proactive Detection and Response of Threats: Implementing proactive mechanisms for threat detection and response mitigates the impact of security incidents.
Security awareness and training programs: The security awareness and training programs will help continuously raise the level of security consciousness among all staff.
Leveraging AI and Automation: Utilizing AI and automation improves the efficiency and effectiveness of security operations.
Implementing a Zero Trust Security Model: The basis of modern cybersecurity strategies is the Zero-Trust model, founded on the principle of “never trust, always verify.”
Regular security audits and incident response drills: These solutions achieve preparedness and resiliency against any possible breach.
Recommended: Building Security from Scratch: Key Steps in Implementing Zero Trust Architecture
Top Ten SecOps Tools in 2024
1. Splunk Enterprise Security
Splunk Enterprise Security is a sophisticated security information and event management (SIEM) solution offering real-time visibility into security threats. It empowers security teams to respond swiftly by leveraging machine learning algorithms to detect anomalies and identify potential threats. Additionally, Splunk Enterprise Security integrates with various security tools, providing a comprehensive and unified security solution.
2. Elastic Security
Elastic Security is an open-source SIEM solution that offers real-time threat detection and response. It leverages machine learning algorithms to detect anomalies and identify potential security threats.In addition, the company also provides network security monitoring, endpoint security, and threat intelligence capabilities.
3. IBM Qradar
IBM QRadar redefines SIEM to uncover analyst potential and outpace adversaries with speed, scale and accuracy. This tool offers Risk-based alert prioritization, Sigma community rules, Threat Intelligence, Federated search, User behavior analytics (UBA), and Network threat analytics. IBM Security QRadar SIEM uses multiple layers of AI and automation. These multi-layers help to enhance alert enrichment, threat prioritization and incident correlation—presenting related alerts unified in a dashboard, reducing noise and saving time.
4. Checkmarx
Checkmarx is a comprehensive SAST solution that can help speed development by identifying and remediating security vulnerabilities. The tool’s main features include code analysis, support for multiple languages and frameworks, integration with CI/CD pipelines, and compliance management.
5. Tenable
Tenable is a vulnerability management solution providing real-time visibility into your organization’s vulnerabilities. It helps you get the context to make more informed decisions based on your actual cyber risk, from vulnerability management to cloud security, identity security to external attack surface management, and more.
6. Qualys
Qualys, Inc. is a technology firm based in Foster City, California, specializing in cloud security, compliance and related services. The company provides a scalable, cloud-based vulnerability management, compliance, and web application security solution. It also provides continuous monitoring and automatic updates for real-time threat intelligence.
In addition, it delivers a holistic view of all IT assets, making managing and securing them easier. Qualys is suitable for businesses of all sizes looking for a scalable, cloud-based threat management solution.
7. FireEye
FireEye is an intelligence-led security company. It is a seamless, scalable extension of customer security operations that offers a single platform that blends innovative security technologies, nation-state-grade threat intelligence, and world-renowned Mandiant consulting. Using this approach, the company eliminates the complexity and burden of cyber security for organizations struggling to prepare for, prevent, and respond to cyber attacks.
8. McAfee
McAfee’s security operations solutions gather, enhance, and distribute data seamlessly, regardless of scale. Their flexible architecture accelerates investigations by guiding data streams toward analytical tools to produce pertinent, prioritized insights. With preconfigured scenarios, analysts can dive into their tasks instantly, aided by automated processes and expert direction for streamlined threat assessment.
9. Cisco Security
Cisco Security Cloud makes security easier for IT and safer for everyone anywhere security meets the network.
It offers:
Smarter and Stronger security: Across a multi-cloud environment it helps in protecting and simplifying security operations, improving scalability, and driving data-informed outcomes powered by Cisco Talos.
Improved user experiences: this tool enables access from any device, anywhere, and adds more proactive security controls to create a seamless experience that challenges attackers, not users.
Delivers cost-effective defenses: consolidating vendors, reducing complexity, and integrating security. This tool helps reduce costs.
Strengthen security resilience: Unified, end-to-end protection maximizes value, minimizes risk, and closes security gaps everywhere to defend against evolving threats.
10. Chef Inspec
Chef InSpec offers a testing framework enabling automated evaluation of your organization’s compliance, security, and policy standards.
Chef InSpec is platform-agnostic, compatible with all major operating systems, and can operate locally or remotely via SSH or WinRM. It’s built on a free, open-source language, facilitating easy extensions to cover new operating systems, devices, or applications.
Best Practices for Implementing SecOps
Security operations are beneficial for enterprises if implemented correctly. After the integration of IT operations and security teams, not every step is automated. The base needs to be set by the management to exchange information and tools. The Security operations process improves service availability when implemented correctly. The following are the best steps or methods to implement the SecOps process:
#1 Discover the scope of SecOps: It is important to analyze the enterprise requirements to draft the security operations strategy well. The SecOps use cases are different for all the companies. There cannot be a standard SecOps strategy that all organizations can follow. Determining what the organization is looking for to improve its security operations process is vital.
The company can choose to outsource some monotonous tasks while forming the SecOps strategy to allow the security teams to focus on crucial tasks. There must be a clear communication process between IT operations and security teams. This will help eliminate cybersecurity threats without hampering service availability.
#2 Build or Develop Workflows to depend on: The SecOps teams face different challenges. The operations team uses a process-driven approach by applying comprehensive processes across applications, servers and environments. With the synergy of security and operations teams, the process is extended by implementing security processes through automated pipelines and LAC tools.
With the different security threats, an effective SecOps process must encompass the complete IT infrastructure, addressing most of the threats. In addition, SecOps teams need to reconfigure the tools regularly for evolving threats.
#3 Conduct SecOps team training: Just forming the team for SecOps will not help improve service availability; training the teams for future challenges is important. The red-blue exercise is the most vital and effective exercise for SecOps teams. Creating two teams consisting of internal employees, where the red team will hack the system, and the blue team will try to mitigate the risks. With this experiment, the security operations teams are well-versed in coordination and work well together.
#4 SecOps Process Automation: ‘Automation is the key when implementing the SecOps process effectively. It becomes difficult and time-consuming if all the security tasks are handled by internal employees in large and distributed IT environments. For the redundant tasks that can take working hours, organizations look for AIOps-based analytics platforms. This platform can automate different security tasks such as data cleaning, event correlation, root cause analysis, pattern discovery and synthetic monitoring. Internal employees can work on the crucial security tasks that need a human touch.
#5 Incorporating SecOps’ Role throughout the delivery pipeline: Adding threats at all the stages of the security delivery pipeline is vital for SecOps teams. With updated and modern security operations teams determining vulnerabilities at an early stage, conducting scans as and when developers write new codes helps reduce future threats. The SecOps team performs security tests throughout the software delivery lifecycle. It constantly monitors applications for bugs and vulnerabilities.
Use Cases of Automating SecOps
1. Phishing Response
Phishing emails are dangerous and frequent, easily executable, and harmful security attacks that organizations—regardless of size—still face today. Responding to a phishing email involves coordinating responses and responding to end users, and these tasks can easily take 30–45 minutes per incident.
Automation “phishing playbooks” can help you execute repeatable tasks at machine speed, identify false positives, and prime your operations for standardized phishing responses at scale.
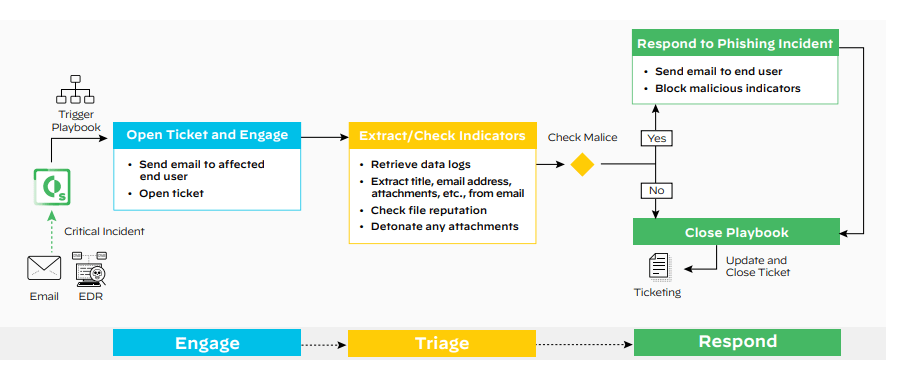 In addition, quickly identifying and resolving false positives gives you more time to deal with genuine phishing attacks and prevents them from slipping through the cracks. An advanced phishing response solution like Cortex XSOAR has machine learning intelligence built in, allowing you to “train” the phishing engine to recognize future phishing attacks. The workflow of automating phishing response follows three simple steps:
In addition, quickly identifying and resolving false positives gives you more time to deal with genuine phishing attacks and prevents them from slipping through the cracks. An advanced phishing response solution like Cortex XSOAR has machine learning intelligence built in, allowing you to “train” the phishing engine to recognize future phishing attacks. The workflow of automating phishing response follows three simple steps:
Engage: Where SOAR platform ingests suspected phishing emails from detection sources. Once the email is ingested, the playbook is triggered to automate enrichment and response. The users get automated emails to the affected user and let the suspected phishing emails be investigated.
Triage: In this process, the playbook extracts and enriches indicators. In a later step, the playbook looks at email indicators and assigns incident severity by cross-referencing the details. Post-enrichment, the playbook checks if malicious indicators were found, and then the different branches of the playbook respond.
Respond: If malicious indicators were detected, the playbook sends an email to the affected user with further instructions. If no malicious indicators are detected, there are still precautions to be taken before confirming that the
email is harmless.
Threat intel analyses are then presented in an incident war room for the analyst to do a final check. Once the analyst is satisfied that the email isn’t malicious, the playbook sends an email to the affected user, apprising them of the false alarm. The incident ticket is marked closed.
2. Malware Investigation and Response:
Playbooks of automation simplify the investigation and response to endpoint security alerts, lowering the time for dwell in the network.
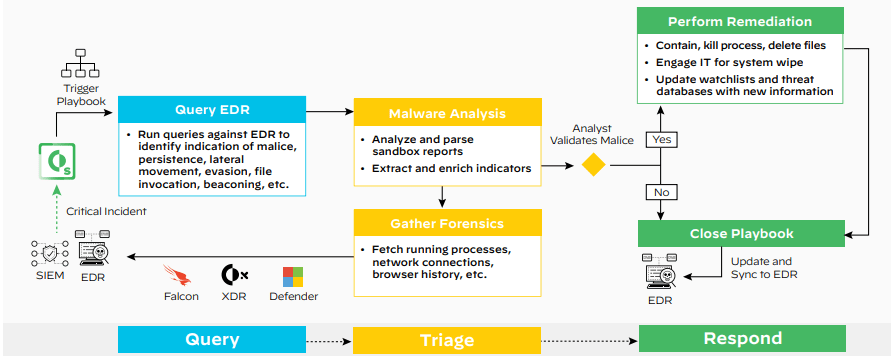 Query: Upon receiving an endpoint security alert, automation playbooks will initiate queries for evidence of malice, such as:
Query: Upon receiving an endpoint security alert, automation playbooks will initiate queries for evidence of malice, such as:
- Attempted lateral movement
- Persistence mechanisms, including scheduled jobs and registry, writes
- Digital signature of the file
- Process execution chain
- Beaconing behavior
- PowerShell execution
Triage: Automated playbooks do the detonation of suspicious files in sandboxes and gather forensics, which includes running processes and network connections, to avoid manual data collection and documentation.
Respond: If malice is confirmed, playbooks update watchlists, quarantine infected endpoints, kill malicious processes, remove infected files, and integrate new threat intelligence across security tools.
3. Threat Intelligence Management:
Automation playbooks improve the integration and management of threat intelligence, enhancing security operations.
Proactive Blocking of Threats: Playbooks aggregate, normalize, score, and prioritize indicators from various threat feeds, ensuring that the latest threats are always reflected in the EDLs.
Continuous Incident Enrichment: Playbooks automatically enrich the alerts with curated threat intelligence, providing early warnings and context to analysts on emerging network threats.
Creation and Dissemination of Weekly Threat Reports: Playbooks automate the generation of threat intelligence reports, enabling analysts to distribute relevant information to business units and stakeholders easily.
Threat Modeling of External Threat Landscapes: Playbooks assist threat intelligence teams in profiling threat actors and their techniques, sharing the details of the attack with security operations and leadership to tighten organizational defenses further.
4. Provisioning Remote User Access:
Automation playbooks improve the security and operational efficiency of remote work access provisioning.
Failed Logins: After several failed login attempts, playbooks send an automated email to users to verify the login attempts. Based on the user’s response, playbooks reset the password or escalate further investigation for potential account takeovers, like identifying the IP address of the attempts and quarantining affected endpoints.
Logins from Unusual Locations: Playbooks enforce MFA for logins from untrusted or unknown IPs. Integration with IAM systems ensures that egress IPs are automatically updated, providing a seamless login experience for the user.
VPN Tunnel Health Monitoring: Playbooks monitor the status of VPN tunnels and alert the security or IT operations team via Slack if any tunnels are down, ensuring continuous connectivity and uptime for remote users.
5. Cloud Security Incident Response:
Automation playbooks streamline and enhance incident response across multi-cloud and on-premises environments.
Cloud Threat Detection: Playbooks ingest cloud security alerts from AWS, Google Cloud, Microsoft Azure, and Prisma Cloud to automate or partially automate incident response, such as crypto mining alerts.
Extract: The playbook extracts indicators (IPs, URLs, hashes) from incident data and opens a ticket for the incident.
Enrich: The playbook enriches indicators with reputation data from threat intelligence tools and context from SIEMs and other event management tools to identify the full extent of the attack. It checks if the indicators are malicious.
Respond: For malicious indicators, the playbook retrieves instance details and security group details takes volume snapshots, and tags the EC2 instance for isolation in a separate virtual private cloud (VPC). It gathers running processes, analyzes results, and notifies the analyst for review. If indicators are not malicious, the playbook involves a security analyst to verify and close the incident as a false positive.
6. Zero-Day Threat Response:
Automation playbooks improve the response to zero-day threats and ransomware breaches through instant, vigorous action.
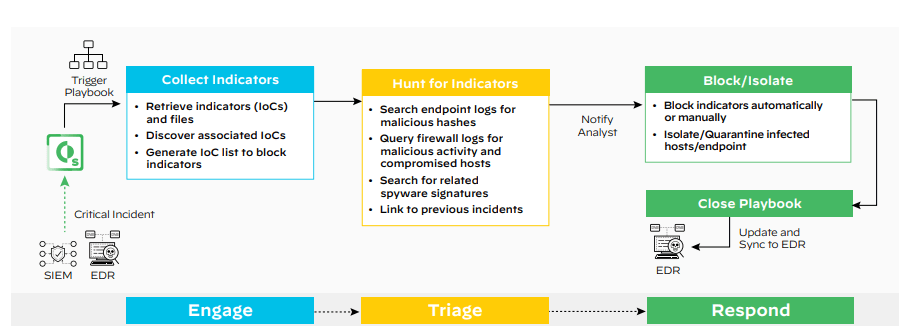 Engage & Triage: Playbooks immediately retrieve and discover indicators of compromise in a detected breach alert. They query the endpoints, firewalls, and other incidents in seconds, leaving the team to secure the defenses.
Engage & Triage: Playbooks immediately retrieve and discover indicators of compromise in a detected breach alert. They query the endpoints, firewalls, and other incidents in seconds, leaving the team to secure the defenses.
Respond: The playbooks perform the initial response actions, which include blocking indicators, isolating or quarantining infected hosts, or updating threat intelligence databases for future use. This ensures fast containment and prevention of attacks through the same indicators.
These automated playbooks streamline responses to high-profile breaches, accelerate investigation efforts, and enhance overall security posture.
Final Note
Security leaders are adopting a post-breach concept focused on detection and response. They admit that the case of a breaching organization has become different from mounting an effective security operations (SecOps) response.
According to TrendMicro’s report, 51% of organizations no longer use many monitoring tools, not because they are outdated, but because they can’t be integrated as they lack the skills to operationalize. For organizations to maximize the effectiveness of SecOps teams, there is a need for a more strategic approach or adoption of automation. SecOps teams need a single source of the analysis truth to rely on. The data from multiple layers upon which intelligent analytics is applied to correlate and prioritize alerts.
FAQs
1. What are the benefits of Security Operations?
- Deliver Efficient Security Response
- Streamline Remediation
- Visualize Security Posture
2. How to integrate threat intelligence and security operations (SecOps)?
The first step starts with security operations teams or SOC teams. Once the team is finalized, focus on your frontline analysts to continuously triage new threats and events. Later, invest in the right tools, hire experienced analysts and even bring in outside managed security services to improve overall operations.
3. What does a SecOps center do?
- A security operations center (SOC) enhances an organization’s threat detection, response and prevention capabilities by unifying and coordinating all cybersecurity technologies and operations.
- It detects, analyzes and responds to real-time incidents.
- It selects, operates and maintains the organization’s cybersecurity technologies and constantly analyzes threat data to find ways to improve the organization’s security posture
4. What are the roles of a SecOps team?
- Chief Information Security Officer
- Security Manager
- Security Engineer
- Security Analyst
- IT Operations Manager
- System Analyst
- System Admin
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]


