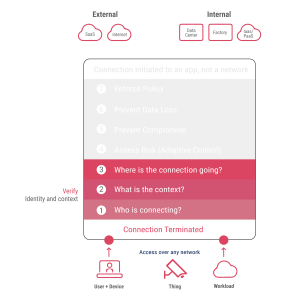
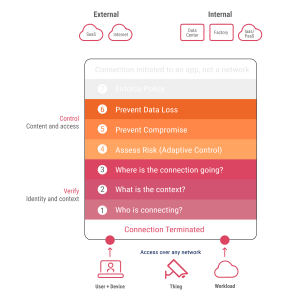
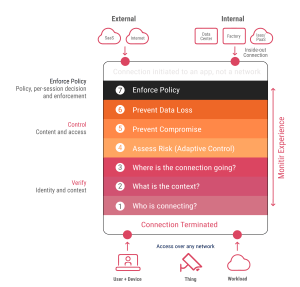
In 2021, the cyberattack on the Colonial Pipeline, a major oil pipeline in the US, spurred a nationwide push for modernizing and fortifying cybersecurity in critical infrastructure.
The rise in frequency and severity of such attacks raises the question: Is there an overreliance on trust in most organizations’ cybersecurity setups? And should IT teams adopt Zero Trust architecture to avert such security breaches going forward?
Trust has always been paramount in any business environment, often entailing significant costs if breached. Organizations must understand that security is not an optional add-on but a foundational aspect that should permeate all operations. In the digital transformation era, organizations now experience unprecedented benefits and chances, but they also face unmatched cybersecurity risks. Incidents such as data breaches, ransomware attacks, and supply chain breaches are not just loss of money but also degrade their trustworthiness among customers, employees, and partners.
The repercussions of a security breach go beyond the mere monetary implications; they destroy reputation and distort relationships with key stakeholders. The 2023 IBM-Ponemon Institute report on the cost of data breaches highlighted in its report underscores the need for organizations to prioritize security and adopt proactive measures that mitigate risks.
What is Zero Trust Architecture?
The Zero Trust Architecture is a strategic cybersecurity approach that has, at its core, eradicated implicit trust and its replacement with continuous verifications to establish the credibility of all digital interactions. It is founded on ‘never trust, always verify.’ This implies that verification of identities and access permissions will be strict and verified regularly.
 Key elements of Zero Trust are authentication methods, dynamic network segmentation, proactive measures to thwart lateral movement, advanced Layer 7 threat prevention mechanisms, and streamlined implementation of granular access policies.
Key elements of Zero Trust are authentication methods, dynamic network segmentation, proactive measures to thwart lateral movement, advanced Layer 7 threat prevention mechanisms, and streamlined implementation of granular access policies.
Elements of Zero Trust Architecture
- Identity and Access Management (IAM)
- Data Loss Prevention (DLP)
- Secure Access Service Edge (SASE)
- Enterprise Resource Ownership Catalog (EROC)
- Security Information and Event Management (SIEM)
- Policy-based enforcement points
- Unified Endpoint Management (UEM)
From the recognition that traditional models depend on outdated assumptions of unwavering trust within an organization’s network. The trust enables unrestricted access to users, including potential threat actors and malicious insiders, enabling lateral movement and unauthorized access to sensitive data. Zero Trust addresses these vulnerabilities by adopting security approaches and prioritizing verification and stringent access controls at every stage of digital interaction.
Also Read: Building Security from Scratch: Key Steps in Implementing Zero Trust Architecture
Insights from the Industry Experts
#1 ZTA from NordLayer’s Head of Platform Engineering Carlos Salas:
Zero Trust Architecture represents a shift in network security, acknowledging that traditional perimeter-based models are no longer sufficient in today’s IT environments. With the rise of remote work, cloud computing, and the proliferation of IoT devices, the notion of a trusted internal network has become obsolete. ZTA operates on the principle of “never trust, always verify,” treating every user, device, and connection as untrusted until proven otherwise.
At the core of ZTA lies the principles of continuous verification, limiting the blast radius, automating context collection and response, and implementing dynamic policies. This approach ensures that access to resources is granted only after rigorous authentication and authorization processes, minimizing the potential for lateral movement and limiting the impact of a successful breach.
Implementing ZTA is complex but offers numerous benefits that outweigh the challenges. By segmenting networks and enforcing granular access controls, organizations can significantly reduce their attack surface and mitigate the risk of data breaches and insider threats. Furthermore, ZTA enhances visibility and analytics, enabling real-time monitoring and swift incident response, ultimately strengthening an organization’s security posture.
One of the main advantages of ZTA is its adaptability to modern IT landscapes. By decoupling security from the traditional network perimeter, ZTA enables organizations to seamlessly extend their security controls to cloud environments, remote workers, and IoT devices, ensuring consistent protection across all endpoints and resources.
However, adopting ZTA has its challenges. Organizations must carefully assess their existing infrastructure, applications, and workflows to ensure compatibility with ZTA principles. Legacy systems may require significant updates or replacements, and the transition process can be disruptive if not properly planned and executed. Additionally, robust identity and access management solutions, including multi-factor authentication and risk-based access controls, are essential for successfully implementing ZTA.
As we look to the future, the adoption of ZTA is poised to accelerate, driven by the increasing sophistication of cyber threats and the ever-evolving IT landscape. Organizations that embrace ZTA will be better equipped to protect their critical assets, maintain regulatory compliance, and foster a culture of security-conscious collaboration.
#2 Arnab Bose, Chief Product Officer, Workforce Identity Cloud, Okta
1. What are the main drivers according to you behind the adoption of Zero Trust architecture in today’s cybersecurity landscape?
Amid today’s constantly evolving threat landscape, organizations are prioritizing zero-trust initiatives now more than ever. As cybercriminals get more creative and attack vectors grow more sophisticated, Zero Trust architecture supplies organizations with the foundation they need to monitor digital environments for unusual behavior.
Beyond the continual threat of cyberattacks, there are several other driving forces behind Zero Trust adoption. First, many organizations today are also undertaking digital transformation projects. Between the consolidation of tech stacks, changing architectures, and the introduction of more SaaS applications, Zero Trust can provide an additional layer of security to help minimize risks amid these major transformations.
The distributed workforce is also a major factor driving Zero Trust adoption. While some teams have returned to more traditional office settings, and others are still spending more time working remotely, organizations must account for security wherever employees are working. With modern teams comprised of full-time staff, contractors, partners, and more – all spread across multiple locations, often using both managed and unmanaged devices – IT and security personnel want to make sure all users, endpoints, and applications are secure.
2. How does Zero Trust differ from traditional perimeter-based security approaches?
Zero Trust is built on the premise that bad actors have already breached a system, meaning that illegitimate users are already in the system, hiding behind what appear to be legitimate credentials. This approach embodies the principle popular among security practitioners of “never trust, always verify” – an evolution of the now-outdated “trust but verify” mentality that previously shaped perimeter-based strategies.
Instead of attempting to barricade the perimeter like other, more traditional security approaches, the Zero Trust strategy focuses inward, continuously evaluating an organization’s digital environment. By comparing real-time user activity to a baseline of how a system’s credentialed users typically behave within that environment, Zero Trust is designed to help detect anomalous activity and identify when a user is exhibiting suspicious behavior.
For Zero Trust to function effectively, organizations must constantly authenticate, authorize, and validate their users and devices since the modern perimeter has been extended to each individual team member wherever they happen to be working.
3. What challenges do organizations typically encounter when implementing Zero Trust, and how can they overcome them?
We recently conducted a survey on Zero Trust adoption that polled more than 800 information security decision-makers from around the globe. We found that while organizations are increasingly implementing strategic Zero Trust initiatives – or have plans to do so on the horizon – respondents have generally encountered the same recurring hurdles.
According to the survey, the top three barriers to Zero Trust adoption were cost concerns, technology gaps, and privacy regulations/data security. Despite the inevitable challenge of managing costs, the survey did reveal some good news for security leaders. Zero Trust budgets are continuing to expand, with 80% of respondents saying their purses increased over the previous year. In North America, that number reached nearly 90%, indicating that some relief is on the way for decision-makers.
For teams looking to tackle technology gaps and keep pace with evolving privacy regulations, the answer could lie in more cross-functional team collaboration. As one example, team control over identity and access management (IAM) within companies has largely transitioned away from an exclusively IT consideration to a shared responsibility with security teams, which allows organizations to better address potential gaps in technology.
One of the other most common challenges impacting Zero Trust implementation is the talent shortage gap. Organizations across the tech industry, ourselves included, are actively working to eliminate this gap through investments in cybersecurity education and training for the next generation of talent. These efforts will help meet the rising demand for skills spanning security, machine learning, automation, AI, and more.
#3 Steve Winterfeld, Advisory CISO, Akamai
While Zero Trust architecture is not a new idea, it does require us to redefine or rethink how we build out our IT security controls. Traditionally, security strategies relied on perimeter defenses with the focus on low friction, so we moved to single sign-on then didn’t really track much beyond that initial authentication. However, the rise of breaches that are tied back to compromised credentials combined (often a result of social engineering attacks) in addition to emerging focus by sophisticated cyber threats using zero day attacks, particularly ransomware, has demonstrated we need to rethink and reinvest in deploying a full zero trust based architecture.
NIST calls out the need for zero trust to both authenticate users and authorize need for access teamed with preventing unauthorized lateral movement. This is most evident in the material impacts from attacks like Ransomware. In a recent Akamai report we showed that the abuse of zero-day / one-day vulnerabilities led to a 143% increase in victims in 2022 – 2023. Even as I talk about the need for multiple integrated security controls, I worry about the complexity and vendor fatigue it introduces. This drives to one thing we have been thinking about, which is the need for vendor consolidation into fewer platforms. At Akamai, we recently launched the Akamai Guardicore Platform to integrate our capabilities into one solution to simplify management and analytics. One of our focus areas when building this platform was flexibility to allow organizations to protect their employee’s entire data journey – whether it’s ZTNA, MFA, microsegmentation and DNS firewall the security team can leverage the modules based on ever changing business models.
While LLM AI is a hot topic, Zero Trust Architecture is one place we can leverage the benefits of GenAI to streamline management and analytics by using natural language communication to allow a broader set of users to more easily analyze activity network logs, set up labeling for asset inventory, develop queries for vulnerability assessments or potential risks from zero days, and develop policy recommendations. We have found that AI can take tasks that were previously manual and time-consuming and turn them into automated processes like compliance scoping, incident response, and network labeling so security professionals can focus their efforts on more complex issues or threats.
Implementing Zero Trust Architecture: A Practical Guide
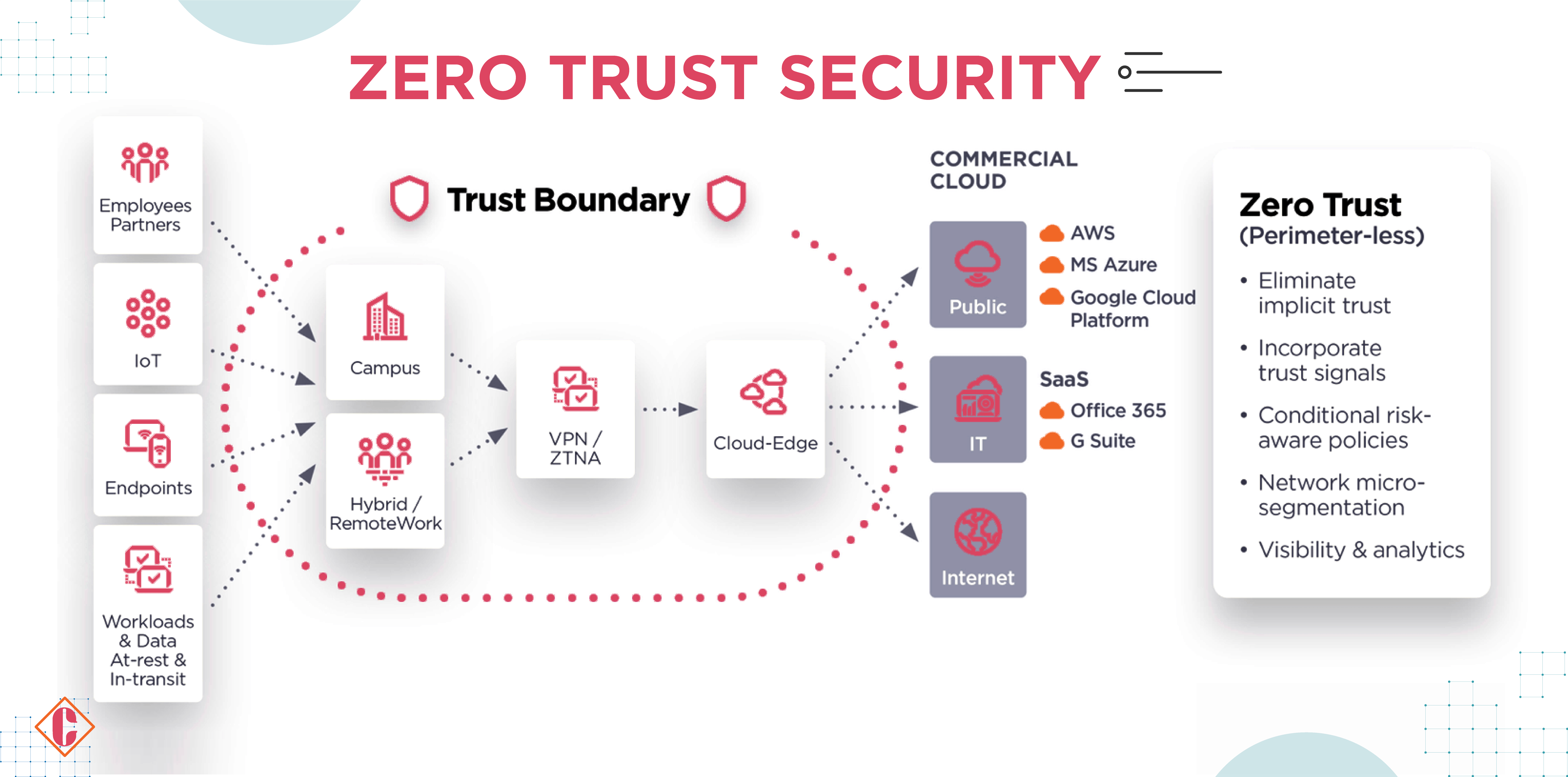
Zero trust represents a pivotal shift in security, moving away from traditional castle-and-moat defenses to protect modern hub-and-spoke networks. This advanced architecture ensures secure connections for users, workloads, and devices, authorizing access solely to sanctioned applications from any location and network, without exposing them to potential exploitation.
-
Verify Identity and Attributes:
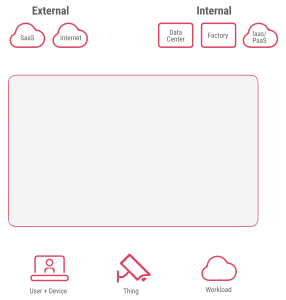
- Authenticate the user/device, IoT/OT device, or workload by integrating third-party identity providers (IdPs) within the enterprise’s identity and access management (IAM) framework.
-
- Validate connection attributes such as role, time, location, and circumstances, aggregated from multiple sources, including IDps and third-party integrations.
- Confirm that the verified identity possesses the necessary context and rights to access the requested resource based on segmentation rules integral to zero trust.
2. Control Content and Context:
-
- Dynamically assess the risk associated with the connection request using AI-driven analysis of device posture, threats, behavior, and policy adherence.
- Employ inline decryption and deep content inspection to
- identify and thwart malicious content, thus preventing compromise.
- Mitigate data loss risks by inspecting and controlling entity-to-resource traffic for sensitive data through prevention measures or isolation within a secure environment.
3. Enforce Policy, Per-Session Decisions, and Enforcement:
-
- Utilize outputs from previous steps to enforce policy decisions, determining whether to allow or block the requested connection based on contextual insights.
- Upon an “allow” decision, establish a secure connection to the designated application, whether internal or external, through encrypted outbound-only tunnels, minimizing potential attack surfaces.
Also Read: The Preflight Checklist For SASE and SSE
The Significance of Zero Trust Architecture for Organizational Trust
In today’s digital landscape, the relevance of zero-trust architecture cannot be overstated. As organizations grapple with the complexities of expansive networks and the proliferation of off-site or cloud-based data and services, the imperative for a robust cybersecurity approach becomes increasingly evident.
Cyber threats, perpetuated by hackers and cybercriminals, evolve incessantly, necessitating a dynamic and assertive defense strategy. Zero trust architecture emerges as a formidable solution by challenging the inherent trust traditionally bestowed upon users and devices within a system. Zero trust security instills confidence in the network’s resilience and integrity by eradicating this implicit trust, ensuring comprehensive protection against potential breaches and unauthorized access.
By 2025, at least 70% of new remote access deployments will be served predominantly by Zero Trust Network Access rather than VPN services—up from less than 10% at the end of 2021. – Gartner
Zero Trust Network Access (ZTNA) is the cornerstone technology within Zero Trust architecture. It encapsulates a comprehensive approach to network security that integrates various principles and technologies. This methodology introduces an additional layer of defense to mitigate the risk of lateral movement within a network, thereby reducing the potential impact of security breaches.
According to insights from a Gartner report on ransomware attacks, approximately 60 percent of organizations will adopt Zero Trust as a foundational element of their security strategies by 2025. Furthermore, recent findings from an IDC survey indicate that within the BFSI vertical, 77.8 percent of enterprises have already implemented solutions and policies supporting a software-defined perimeter. Additionally, 52.2 percent actively consider adopting and investing in SD-Branch components, while 54.4 percent plan to implement a Zero Trust architecture alongside related security solutions.
Traditional security paradigms prove insufficient in safeguarding organizations effectively in the face of evolving and intricate cyber threats. The conventional perimeter-based approach, reliant on implicit trust within the network, fails to adequately address the multifaceted nature of modern threats from internal and external sources. Therefore, embracing a zero-trust approach emerges as a strategic imperative for organizations, fostering a culture of security within the workplace and enhancing productivity, transparency, and data integrity.
Also Read: Guide to Implementing Zero Trust Security in Enterprise Networks
Benefits of Zero Trust Architecture in IT Security
Traditional security models assume internal traffic safety. However, in today’s reality, internal actors contribute to 36% of data breaches in enterprises and 44% in SMBs, according to Verzions Data Breach investigations report. These users are often not malicious but rather careless with their passwords and may have accumulated unnecessary privileges over time.
In contrast, the zero-trust security paradigm regards everything and everyone as untrustworthy until proven otherwise. Access undergoes evaluation in each case, is subjected to risk and trust assessments, and is granted only necessary access for job functions. Requests are assessed based on micro-segmentation of user types, locations, and other identifying data to determine trust, access permissions, and duration.
Zero Trust Identity, facilitated by identity access management (IAM), Identity Governance and Administration (IGA), and Cloud Privileged Access Management (CloudPAM), extends beyond access control to encompass continuous monitoring, management, remediation, and recovery. For instance, IGA systems evaluate risk and trust, assigning only essential privileges.
By reducing standing privileges, organizations can mitigate damage in the event of compromised credentials or malware infiltration. Compared to conventional methods, this approach enhances security for remote workforces and boosts productivity and organizational agility.
However, the Zero Trust framework requires a new mindset and buy-in from all organizational levels, as it isn’t a set-and-forget solution. This post delves into the significant benefits of transitioning from traditional network security to a modern, identity-based Zero Trust architecture.
1. Enhance Enterprise Visibility
With a zero-trust approach, no assumptions are made about trust, allowing you to tailor your security strategy based on criticality and risk. Ephemeral resources like containers and serverless processes pose challenges in the modern cloud era. To address this, a Zero Trust framework necessitates visibility into both legacy and contemporary resources, requiring organizations to develop a solution capable of discovering, onboarding, and monitoring access to these resources.
Once monitoring is established to encompass all assets and activities, complete visibility is achieved into who or what accesses the network, including details such as time, location, and associated applications for each access request. An effective security system identifies unusual behaviors and Separation of Duties (SoD) conflicts, while diligently tracking all activity.
2. Streamline IT Management
With Zero Trust relying on continual monitoring and analytics, automation can assess access requests. If the privileged access management (PAM) system deems key identifiers in the request low-risk, access is granted automatically. Approval is only required when the automated system identifies suspicious requests.
This benefit is substantial. An ISSA 2021 report states that 62% of organizations face a cybersecurity skills shortage. Automating tasks reduces the need for human resources, freeing up time for innovation and manual administration.
3. Boost Efficiency for Security Staff
A zero-trust approach enables your security team to operate more efficiently. Centralized monitoring generates reliable data stored in a single location, facilitating robust analytics. This provides your team with valuable insights to uphold a secure environment. Within a Zero-Trust architecture, a unified event store can monitor and analyze activity, minimizing distractions and enabling operations staff to concentrate on genuine threats.
4. Improve Data Protection
Implementing a Zero Standing Privilege framework alongside just-in-time (JIT) access diminishes the risk posed by rogue employees or malware gaining extensive network access. In the event of a firewall breach by malware, the swift extraction of customer data or intellectual property could tarnish your reputation and erode your competitive edge.
Restricting user access and imposing time-bound limitations significantly mitigates the impact of breaches. By confining access to a limited dataset, malicious actors face greater difficulty in locating sought-after data.
According to a collaborative research report by KuppingerCole and HP, 84% of IT decision-makers express concern that remote workforce behaviors heighten the risk of security breaches.
5. Streamline User Access
Amid the pandemic, the swift deployment of VPNs resulted in configuration errors and security lapses, fostering breaches and workflow interruptions. Employees’ VPN usage caused performance challenges in accessing necessary resources.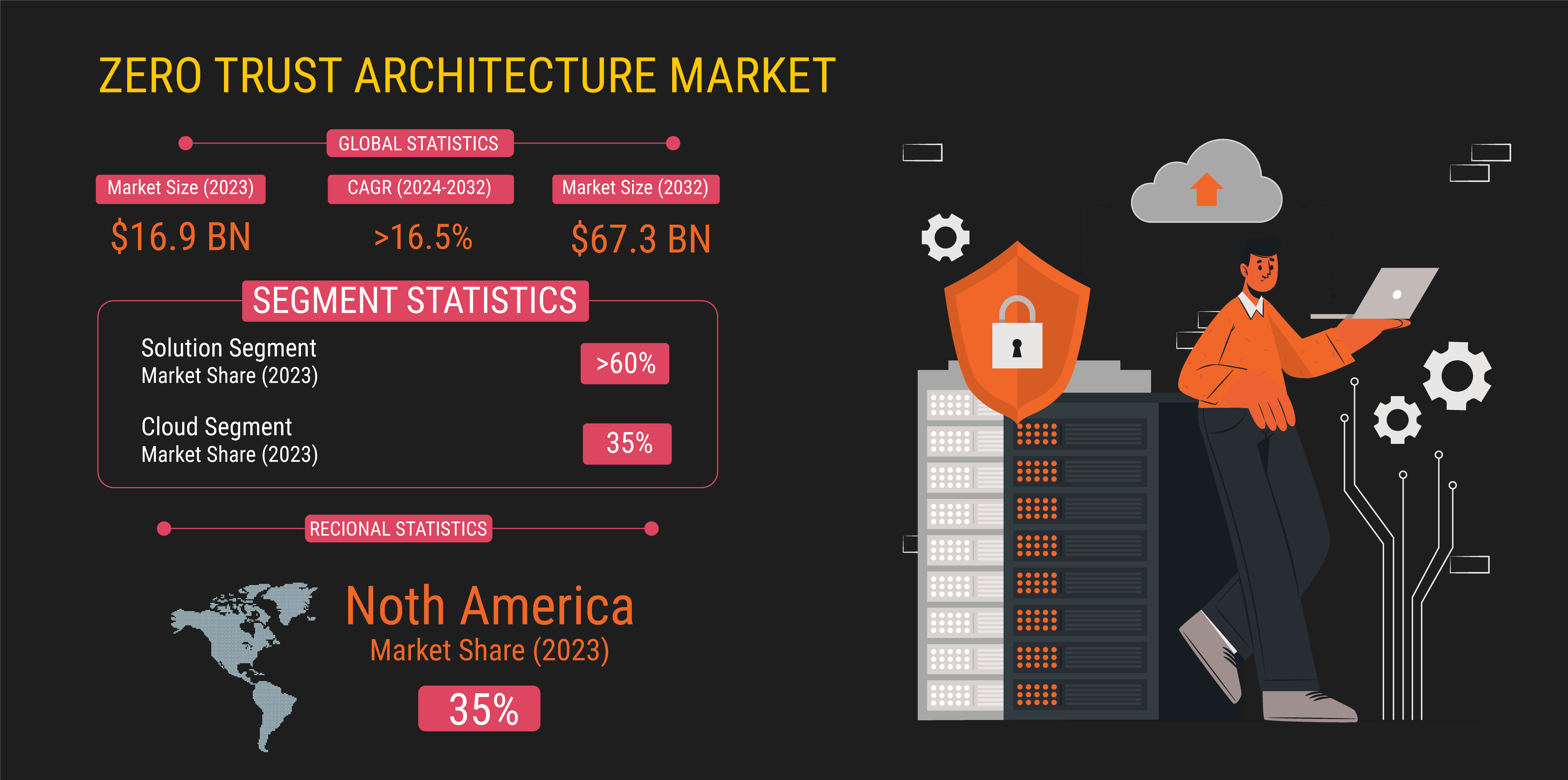
Through a zero-trust framework, automation simplifies access to essential resources without reliance on administrator approval. Manual intervention is necessary only for requests flagged as higher risk.
Zero Trust Architecture Market Insights
The Zero Trust Architecture Market reached USD 16.9 billion in 2023 and is projected to exhibit a Compound Annual Growth Rate (CAGR) of over 16.5% from 2024 to 2032 as per Global Market Insights report. The increasing frequency and complexity of cyber threats and attacks have been pivotal in driving the adoption of zero-trust architecture. Traditional security models, relying on perimeter defenses, are inadequate against advanced and targeted attacks. Zero trust prioritizes continuous verification and authentication of users and devices, irrespective of location, rendering them more resilient against evolving cyber threats.
Digital transformation and remote work trends significantly influence the zero-trust architecture market’s trajectory. A survey conducted by FlexJobs revealed that 57% of employees would consider changing their jobs if their employer discontinued remote work options. This underscores workers’ importance on the flexibility and autonomy associated with remote work. Moreover, 65% of respondents preferred full-time remote work, highlighting the widespread popularity of this work model. Additionally, 32% indicated a preference for a hybrid schedule, combining the benefits of remote work flexibility with collaborative opportunities presented by in-office work.
The Future of Zero Trust: Key Cybersecurity Trends
Adoption of Zero Trust via Remote Browser Isolation (RBI)
Zero-trust architecture may see widespread use of remote browser isolation (RBI) by 2024. Web browsers are a common way for cyber-attacks to happen, so businesses will likely use RBI to apply zero-trust rules when accessing the web. RBI technology separates browsing from the user’s device and company network. It runs browsing in a secure remote environment instead. Malicious content from browsing is contained in this isolated area. This greatly lowers the risk of compromising devices or networks.
Adopting remote browser isolation (RBI) proactively reduces potential risks, especially for businesses with many remote workers. When integrated into Zero Trust frameworks in 2024, RBI will secure networks and deliver a safer, smoother web experience. This reinforces overall cybersecurity amid rapidly changing web threats.
The remote browser isolation market is expected to grow over 40% from 2020 to 2026. This shows rising awareness of RBI’s role in strengthening zero trust architectures by mitigating web-based threats.
Embracing a “Never Trust, Always Verify” Philosophy
Companies will adopt a new mindset in 2024. They will say “never trust, always verify” everything. This means they won’t automatically trust anyone or anything for access, inside or outside their network. Over 60% will stop using old VPNs. They will instead use “zero trust network access“. This checks every request for access thoroughly. Companies now realize that just having a secure perimeter is not enough. Cyber threats have become too advanced. The “never trust, always verify” approach means not blindly trusting anything. It’s a shift from the old way of doing security perimeter checks. This new philosophy emphasizes constant verification as threats evolve.
Enhanced Identity and Access Management (IAM)
In the year 2024, verifying who can access data and systems will advance. Using multiple factors like biometrics and behavioral analysis to confirm identities will become normal practice. Businesses must properly manage access permissions to protect sensitive information from unauthorized individuals. This upgraded identity and access control is crucial for zero trust security architectures. Experts predict the identity and access management market will expand rapidly from $12.3 billion in 2020 to $24.1 billion by 2025, growing annually at 14.4% (Markets and Markets, 2021). This significant growth highlights increased adoption of advanced identity verification solutions within secure zero-trust frameworks.
Micro-segmentation of Networks
Businesses in 2024 will increasingly employ micro-segmentation to divide networks into smaller, isolated zones, limiting lateral movement within the network and thwarting access to sensitive data even in the event of outer defense breaches. Studies indicate that micro-segmentation can reduce the cost of a data breach by up to 50% (Ponemon Institute, 2021), highlighting its growing importance in enterprise security strategies, particularly within the context of zero trust.
AI and Machine Learning Integration
Artificial intelligence (AI) and machine learning will play a significant role in zero-trust frameworks by 2024, continuously analyzing network patterns and user behavior to detect anomalies indicative of security threats. Investments in AI are projected to exceed $300 billion by 2026, with a substantial portion aimed at bolstering cybersecurity (IDC, 2022), underscoring the pivotal role of AI and machine learning in evolving zero trust security models.
Cloud Security Posture Management (CSPM)
With businesses increasingly relying on cloud services, Cloud Security Posture Management will become integral to zero-trust strategies. CSPM tools will aid in continuously monitoring and managing cloud security postures, ensuring compliance and mitigating the risk of misconfigurations and other common cloud-based vulnerabilities. Gartner predicts that by 2027, 80% of vendors will offer CSPM as a feature of their cloud security platforms, compared to 50% in 2022, reflecting the growing relevance of CSPM in zero-trust strategies amidst continued cloud migration.
Comprehensive Endpoint Security
Endpoint security will evolve to be more comprehensive in 2024, with businesses adopting advanced endpoint detection and response (EDR) solutions capable of protecting against known threats and using behavioral analysis to detect unknown threats. The endpoint security market is forecasted to grow from $12.8 billion in 2019 to $18.4 billion by 2025 at a CAGR of 7.4% (Markets and Markets, 2020), underscoring the rising need for advanced endpoint security solutions, including EDR, in the context of zero trust.
Regulatory Compliance and Zero Trust
Zero trust will likely intersect with regulatory compliance as it becomes more conventional. In 2024, businesses may witness regulations requiring specific zero-trust measures, particularly in industries handling sensitive data, such as finance and healthcare. A Deloitte survey revealed that 47% of organizations view aligning cybersecurity with regulatory requirements as a top driver for cybersecurity strategy, highlighting the increasing integration of Zero Trust models with regulatory compliance.
Top Zero Trust Architecture Companies
#1 Cloudflare
#2 Zscaler
#3 Palo Alto Networks
#4 Akamai
#5 NordLayer
#6 Okta
#7 Fortinet
#8 CrowdStrike Zero Trust
#9 Broadcom
#10 Twingate
Zero Trust Architecture Use Cases
All businesses can use zero trust principles. Many have added zero trust elements or are adding them through strong security steps. Zero trust architecture (ZTA) works well for businesses with workers spread out or always on the move. But ZTA helps all businesses, too. ZTA is useful as businesses may use it for traditional security. Enterprises with offices and employees scattered across different locations benefit from having secure access. Workplaces that let workers to use devices like laptops and phones outside the office need extra protection. Companies with sensitive data and private customer information are required to prevent theft or unauthorized access. Firms upgrading security systems or switching to the cloud find zero trust architecture a secured option.
1. Geographically Dispersed Enterprises
In most cases, the enterprises have a single headquarters or are more geographically dispersed with separate enterprise-owned physical network connections. The employees working remotely cannot access all the enterprise-owned local networks. They still need to access enterprise resources to perform tasks. Some resources, such as employee calendars and email, need access, while some sensitive resources, such as HR databases, need restricted access. An endeavor takes place to address the needs; thus, an enterprise implements zero-trust architecture (ZTA).
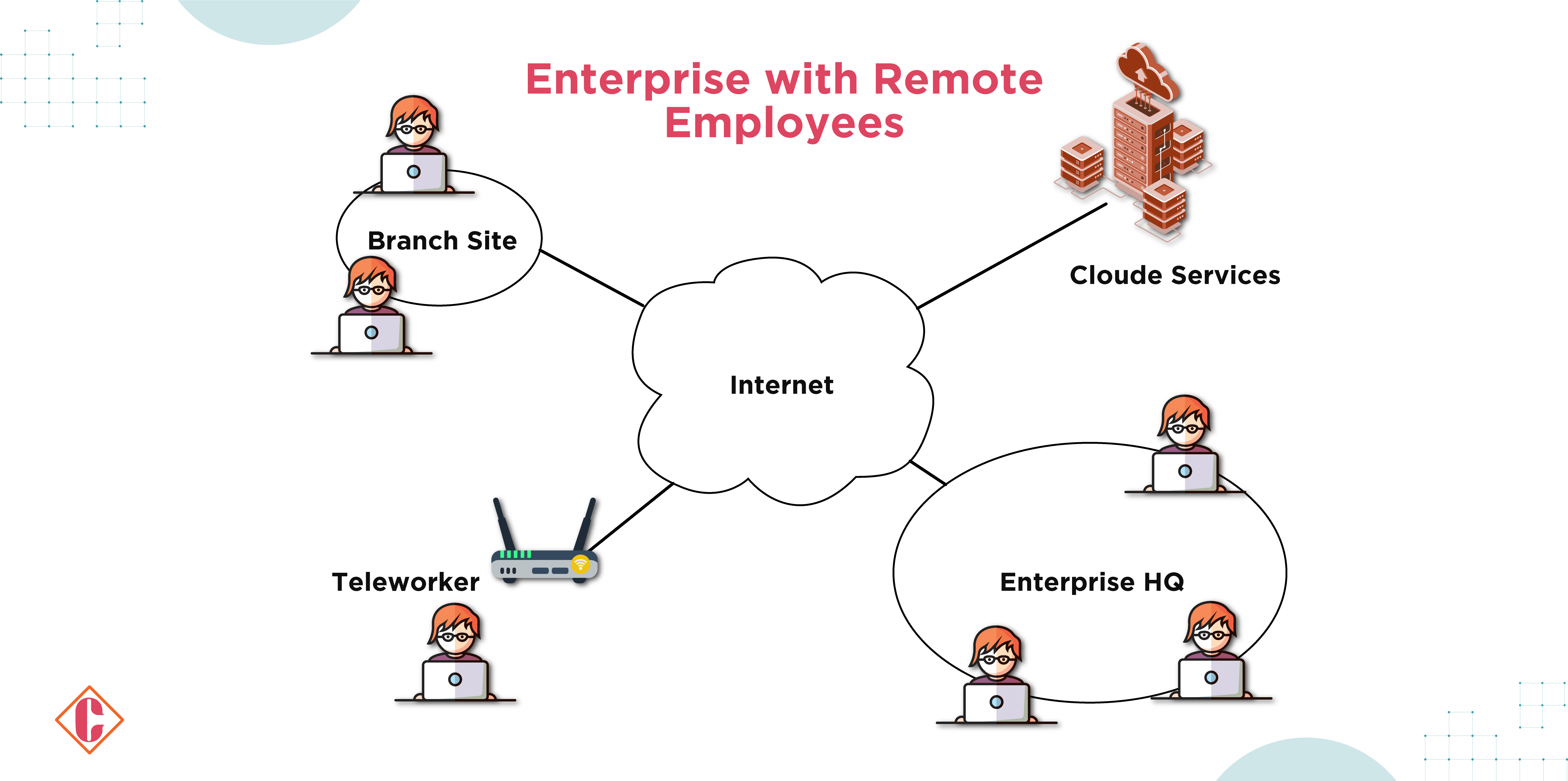 At times, the Policy Enforcement/Policy Administration (PE/PA) components are hosted as a cloud service, delivering high availability and lessening the enterprise infrastructure’s dependence on accessing cloud-based resources. End assets come with installed agents or access resource portals toward secure connectivity. This setup optimizes responsiveness by minimizing the need to route all traffic through the enterprise network to access cloud-hosted applications and services.
At times, the Policy Enforcement/Policy Administration (PE/PA) components are hosted as a cloud service, delivering high availability and lessening the enterprise infrastructure’s dependence on accessing cloud-based resources. End assets come with installed agents or access resource portals toward secure connectivity. This setup optimizes responsiveness by minimizing the need to route all traffic through the enterprise network to access cloud-hosted applications and services.
2. Multi-Cloud Enterprise
Zero-trust architecture (ZTA) is increasingly utilized when a company involves multiple cloud service providers (see Figure 9). In this case, the enterprise supports applications and data deployed across two or more cloud providers. Mostly, applications are run separately from their corresponding data sources, requiring direct connections for efficient performance and good management.
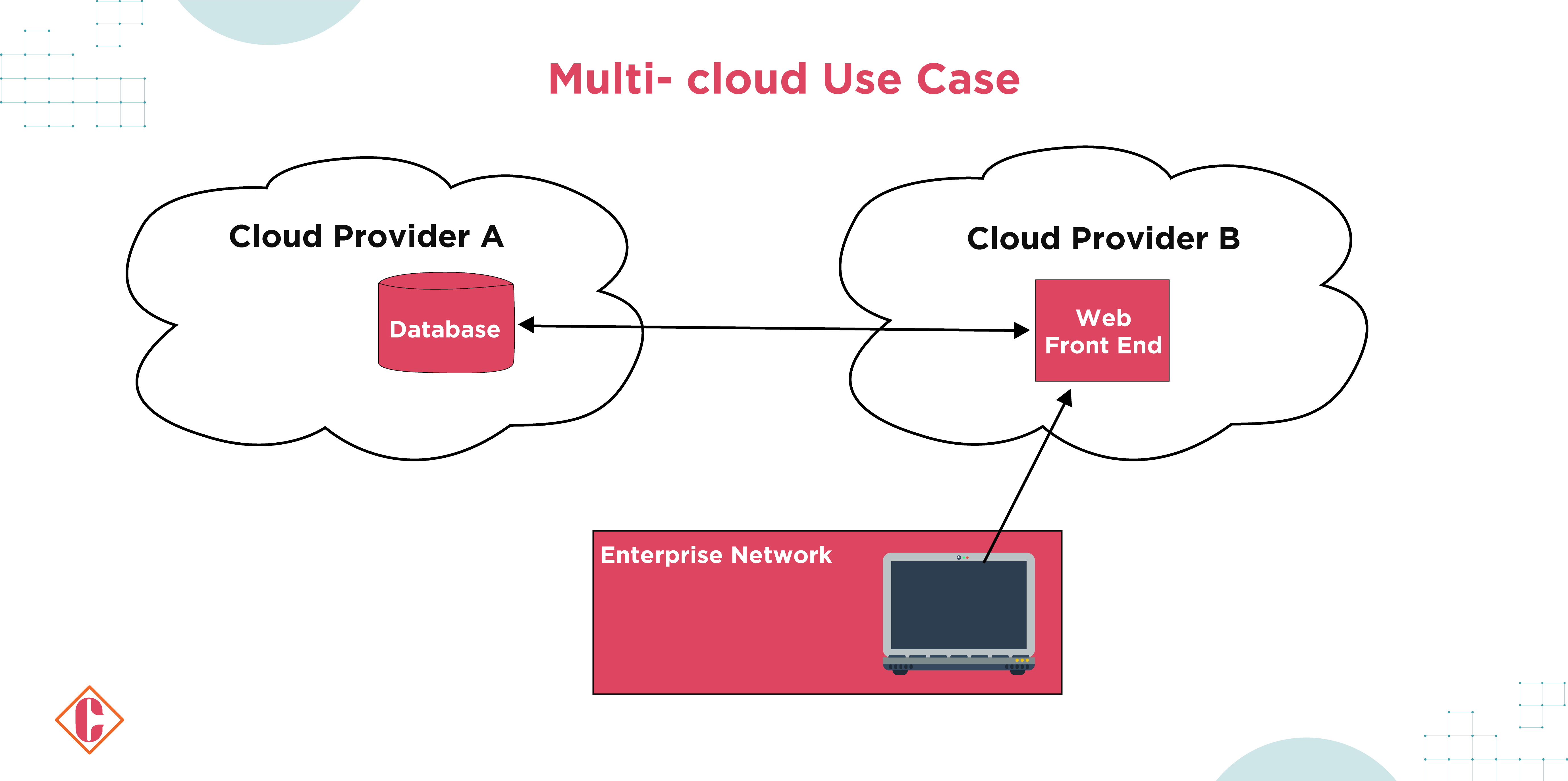 This use case corresponds well to the server-server implementation of the Cloud Security Alliance’s (CSA) software-defined perimeter (SDP) specification. As enterprises move to cloud-hosted applications and services, traditional perimeter-based security measures are insufficient. ZTA principles propose consistent security measures across all network infrastructures regardless of ownership.
This use case corresponds well to the server-server implementation of the Cloud Security Alliance’s (CSA) software-defined perimeter (SDP) specification. As enterprises move to cloud-hosted applications and services, traditional perimeter-based security measures are insufficient. ZTA principles propose consistent security measures across all network infrastructures regardless of ownership.
Implementing ZTA in a multi-cloud environment includes deploying Policy Enforcement Points (PEPs) at access points for every application and data source. The Policy Enforcement (PE) and Policy Administration (PA) components will be hosted as services within any cloud provider. Clients access PEPs directly through a portal or a locally installed agent, enabling centralized access management, even for resources hosted outside the enterprise network.
However, implementing ZTA across multiple cloud providers imposes challenges that vary across the multi-cloud infrastructure. The enterprise architects must handle those variations as best as possible for effective ZTA implementation within their multi-cloud infrastructure.
3. Enterprises with Contracted Services and Non-Employee Access
Another perspective for implementing zero-trust architecture (ZTA) considers the accommodation of on-site visitors and service providers having contracted with the enterprise and requiring restricted access to enterprise resources. For instance, the enterprise could have internal applications, databases, assets, and other services outsourced to providers that are occasionally on-site for maintenance tasks, such as smart heating and lighting systems.
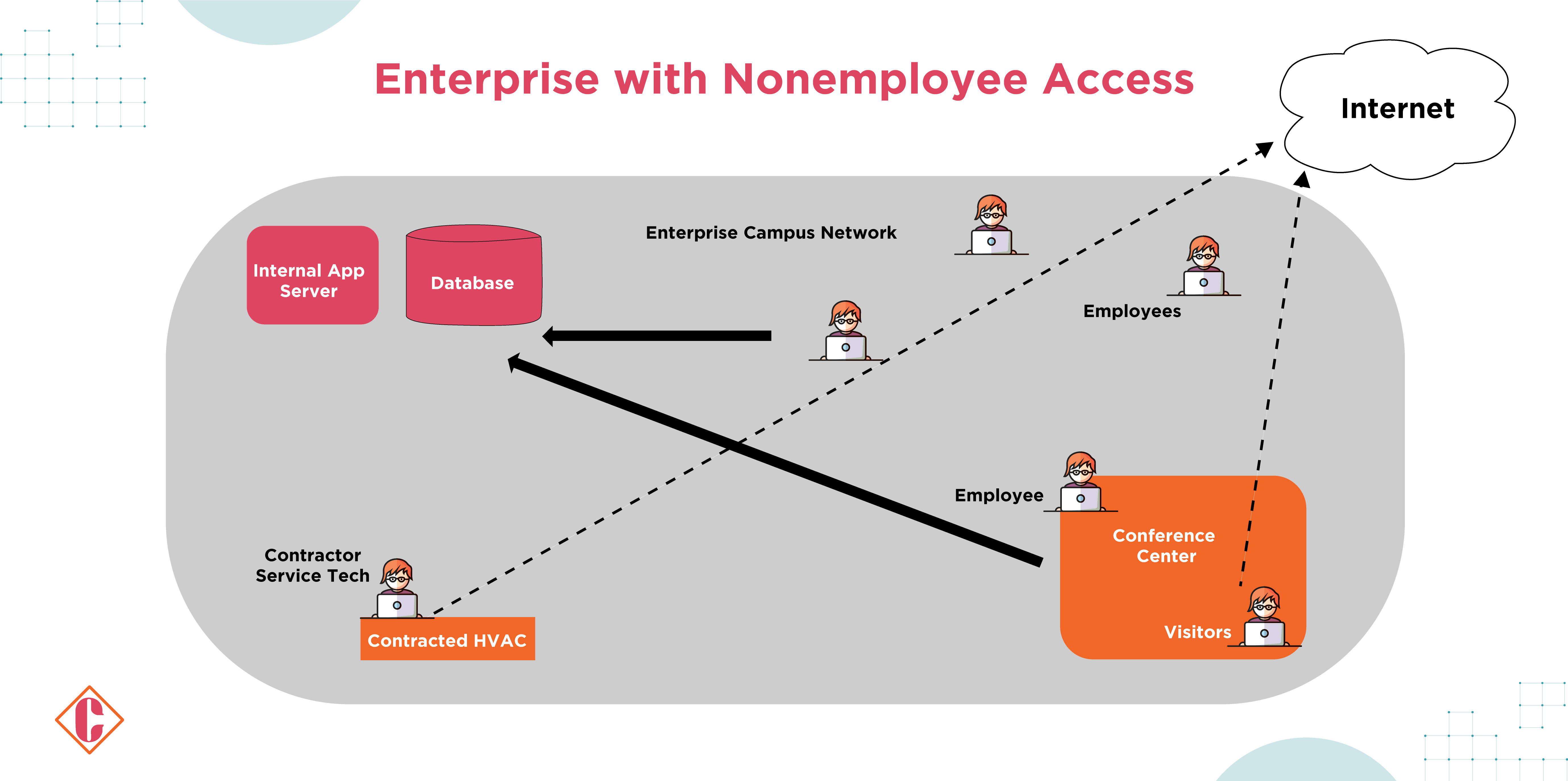 A zero-trust approach can be used to manage network connectivity for these visitors and service providers while protecting enterprise resources from unauthorized access. This means allowing internet access to devices and visiting technicians while concealing enterprise resources.
A zero-trust approach can be used to manage network connectivity for these visitors and service providers while protecting enterprise resources from unauthorized access. This means allowing internet access to devices and visiting technicians while concealing enterprise resources.
Besides, an enterprise may have conference rooms where workers interact with visitors. With the help of the ZTA using Software Defined Perimeters (SDPs), employee devices and authorized subjects will be allowed to access the appropriate enterprise resources, while visitors will be given internet-only access. Active network reconnaissance and east-west movement are prevented to prevent unauthorized access attempts.
4. Cross-Enterprise Collaboration
Cross-enterprise collaboration between A and B takes place for a joint project. This collaboration could include two federal agencies (G2G) or a federal agency and a private enterprise (G2B). Where A hosts the project database but needs to grant access to specific members of B.
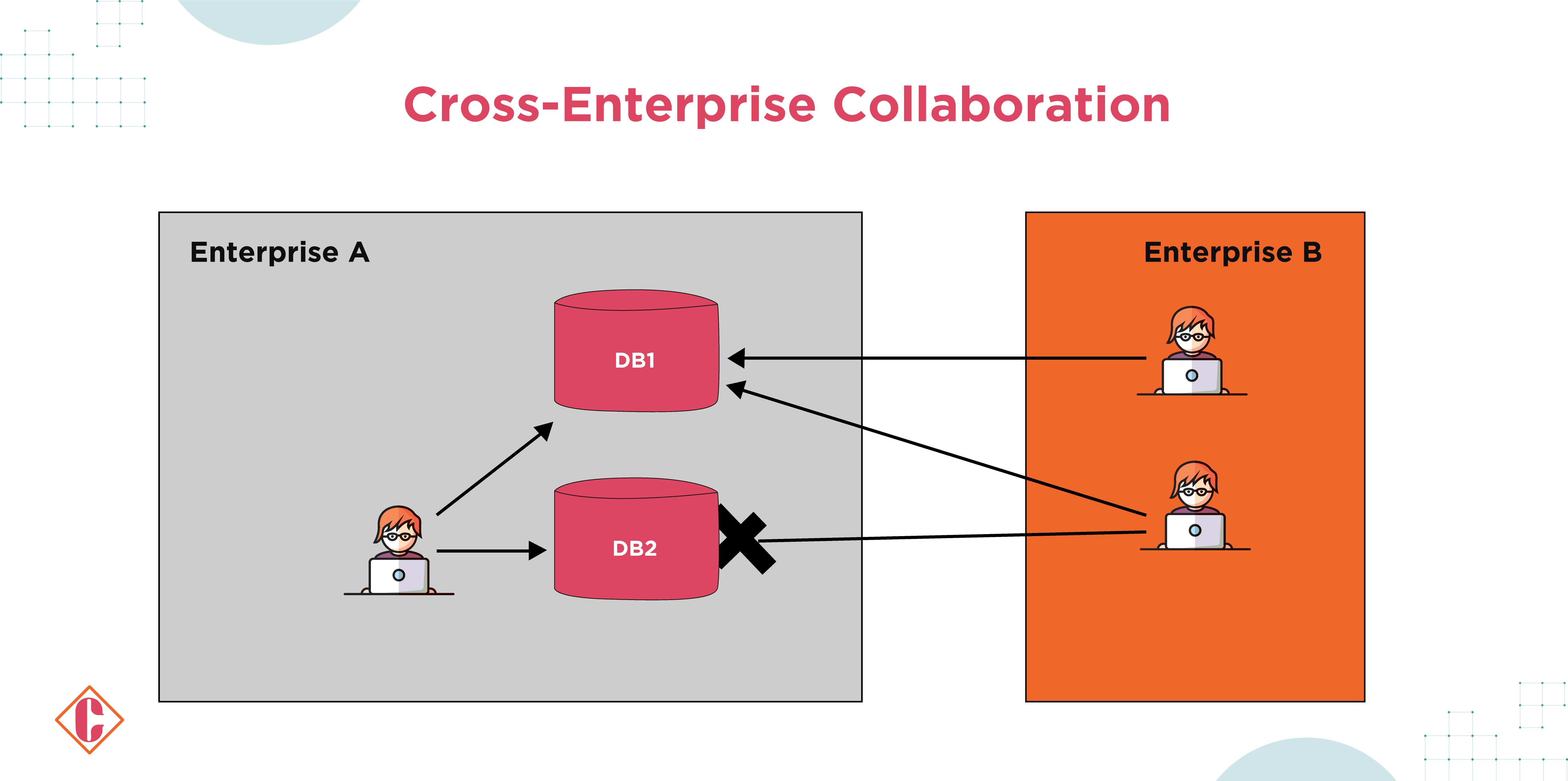 It is challenging to manage access for employees of Enterprise B, who are not present on their respective network infrastructures, to the required data while denying access to other resources. It can be implemented by rapidly introducing such relationships, provided that both organizations’ Policy Enforcement Points (PEPs) can authenticate subjects in a federated ID community.
It is challenging to manage access for employees of Enterprise B, who are not present on their respective network infrastructures, to the required data while denying access to other resources. It can be implemented by rapidly introducing such relationships, provided that both organizations’ Policy Enforcement Points (PEPs) can authenticate subjects in a federated ID community.
Like previous use cases, employees may not be located on their respective network infrastructures, and the required resources may be located in the cloud or within one enterprise environment. This eliminates the need for complex firewall rules or enterprise-wide access control lists (ACLs) based on IP addresses.
Using a cloud-hosted Policy Enforcement (PE) and Policy Administration (PA) service, accessibility to all parties without establishing a VPN can be offered. Depending on the technology in use, Enterprise B employees may need to install a software agent on their assets or access data resources through a web gateway.
5. Enterprises with Public- or Customer-Facing Services
Enterprises carry out public-facing services that may or may not require user registration and can be used by the general public, existing customers, or other user groups, such as employee dependents. Such a scenario may mean that the enterprise does not own the requesting assets and, thus, is incapable of enforcing internal cybersecurity policies.
For public-facing resources that do not require user login credentials (e.g., public web pages), the traditional zero-trust architecture (ZTA) principles may not apply. The enterprise lacks strict control over the state of requesting assets, and anonymous access to public resources may not demand credentials.
However, enterprises may establish policies concerning password management, lifecycle, and multi-factor authentication (MFA) options for registered public users like customers or special users like employee dependents. However, enterprises are bound to face challenges in implementing policies for these users.
To mitigate the risks, enterprises may monitor incoming requests to detect any unusual access patterns that may be indicative of automated attacks. For instance, a sudden surge in requests from unknown or outdated web browsers may indicate an attack. The enterprises must also ensure that such compliance statutes and regulations exist for collecting and recording information about the requesting users and assets.
FAQs
1. What Makes Zero Trust So Crucial for Security in Today’s Landscape?
Zero trust is important because today’s work environment is changing fast because of the widespread use of cloud computing and remote working. Traditional security perimeters have been losing their effectiveness in protecting against cyber threats. Zero trust architecture ensures strong access controls, continuous monitoring, and data-centric security mechanisms. This adaptive approach offers proactive security methods against insider threats and many advanced cyberattacks as they are active today.
2. Can ZTA eliminate cybersecurity risk?
No, any enterprise can eliminate the cybersecurity risk only through another organization’s efforts and when the provided experts deem so. ZTA, when complemented with other cybersecurity policies, guidance on identity and access management, continuous monitoring, and general cyber hygiene, can significantly reduce overall risk and protect against common threats.
3. What are the unique threats associated with implementing ZTA?
- Policy Engine and Administrator Subversion: The policy engine and administrator are essential components of ZTA. Any erroneous configuration of the components or compromised access can disrupt enterprise operations.
- Denial-of-Service or Network Disruption: Attackers disrupting or denying access to policy enforcement points (PEPs) or PE/PA can impact enterprise operations. Mitigation can be achieved through securing cloud environments and following cyber resiliency guidelines.
- Compromised Credentials/Insider Threat: Although ZTA reduces risk, stolen credentials or insider threats remain concerns. Multi-factor authentication (MFA) and contextual trust algorithms assist in mitigating such risks.
- No Visibility on the Network: Limited network traffic visibility from non-enterprise assets poses challenges. Machine learning techniques and metadata analysis assist in identifying potential threats.
- Storage of System and Network Information: Stored data for contextual policies and network analysis become targets for attackers. Proper measures to ensure the protection of the data, along with restricted access, are imperative.
- Reliance on Proprietary Data Formats or Solutions: Such a problem depends on the fact that interoperability difficulties with proprietary data formats mean dependence on specific providers to execute business functions. Evaluate the providers based on security controls and other factors.
- Use of Non-Person Entities (NPE) in ZTA Administration: Risks include false positives/negatives impacting the organization’s security posture, as well as attackers coercing NPEs to perform unauthorized tasks. Regular analysis and stringent authentication measures can help mitigate such risks.
4. How does Zero Trust architecture relate to the NIST Privacy Framework?
Zero Trust architecture emphasizes inspecting and logging network traffic, which may contain private information. Organizations adopting Zero Trust should identify and mitigate privacy risks, a process facilitated by the NIST Privacy Framework.
5. What is the history of zero-trust efforts in federal agencies?
Federal agencies have advocated zero-trust principles for over a decade, predating the term itself. Early strategies such as DISA and the black core of DoD have emphasized a transaction-focused model over a perimeter-based one. Zero trust moves on from concepts of reparameterization to purely transactional trust evaluation. From the development of FISMA, RMF, FICAM, TIC, and CDM, federal initiatives and guidance underline this dynamic and granular access control shift to limit data exposure and improve cybersecurity posture.
Conclusion
Zero Trust is far more than a product or status; this has to be a fundamental concept for organizations to attain clarity on data processing activities, identify sensitive or critical data, and put appropriate levels of protection, detective, and reactive security measures in place.
It is also important to remember that trust cannot be based on promises from vendors, providers, or accepted policy statements. Trust needs to be proven at policy enforcement points or policy decision points before access is granted to data enclaves or network segments. This will require network segmentation and the use of centrally managed next-generation firewalls as PEPs in front of data enclaves, whether the cloud, on-premises, or with an IT provider.
Finally, for efficient cyberattack detection and unauthorized access to sensitive data, centrally processing all security-relevant information and logs is needed. This end-to-end security monitoring will provide insight into the identification of unauthorized data processing using insights derived from legitimate day-to-day data use, threat intelligence, and correlation. PEPs and PDPs provide the data that can be correlated to support automation and to contain suspicious transactions.
[To share your insights with us as part of editorial or sponsored content, please write to psen@itechseries.com]