Cybersecurity for the healthcare industry is at risk of security breaches, which may include cyber threats and data breaches. The more medical equipment and healthcare institutions rely on technology daily, the higher the risk of cyber threats and data breaches. The global healthcare market is witnessing tremendous growth, divided across geographical regions like North America, APAC, Europe, the Middle East, and Africa as the EMEA region. The marketsandmarkets report shows the global healthcare IT market by revenue is projected to reach $974.5 billion in the year 2027.
Here’s an overview of the market size and trends in these regions:
North America
The North American healthcare IT market was valued at approximately USD 85.08 billion in 2023. It is estimated to rise to USD 178.93 billion by 2028, with a CAGR of approximately 16.03%. Driven by advanced healthcare infrastructure in the region, high expenditure in healthcare, and the substantial presence of significant healthcare IT companies. (Source)
Asia-Pacific (APAC)
The APAC healthcare market is growing exponentially due to increasing healthcare spending, technological advancements, and demand for healthcare services. BMI Research estimates that the Asia Pacific healthcare market will hit USD 2.3 billion as the expansion of universal healthcare increases the demand for medical care. It is growing despite a corresponding surge in lifestyle diseases and diseases related to an aging population.
By 2030, APAC is forecasted to be the fastest-growing region for healthcare spending, contributing over 20% to global spending. According to Bain, consumers are more engaged and responsible for their health; hence, they are willing to spend more on better health outcomes and experiences.
The market in healthcare analytics in the APAC region is also growing rapidly. According to Grand View Research, it is forecasted to grow by 22.9% in CAGR from 2024 to 2030 due to technological advancement, economic development in important nations like China and India, and the increasing adoption of healthcare analytics to improve patient care and operational efficiency.
Europe, the Middle East, and Africa (EMEA)
The EMEA region witnessed that in 2023, the value of the Emergency Medical Services market was pegged at approximately USD 8.70 billion and is slated to reach USD 11.69 billion by 2034, with an average growth rate of 2.7% over this period. According to FM Insights, the market was dominated by key segments such as Advanced Life Support in 2023, hence a huge demand for specialized emergency services.
Regarding healthcare asset valuation, notable transactions in the UK summed around £7.2 billion, marking very strong activity in the market, which is forecasted to remain strong in performance. This is according to Colliers Commercial.
Why do cybercriminals target healthcare service providers?
Cybercriminals increasingly target healthcare service providers due to the industry’s increasing vulnerabilities. High-value private sensitive data makes healthcare organizations lucrative targets for hackers, who exploit weaknesses within the digital infrastructure. Attacks are possible due to the digitally connected nature of medical devices, the reliance on old technology and few cybersecurity measures taken.
The need for seamless collaboration and data sharing among healthcare professionals influences the need to access sensitive information remotely, thus expanding the attack surface area. In addition, small healthcare enterprises—given their small security budgets and reliance on old technology—present as easier targets for cybercriminals looking to infiltrate the networks of larger healthcare organizations. In this sense, healthcare organizations struggle with the evolving threat to their systems, and robust cybersecurity solutions are essential in safeguarding patient data and minimizing the risk of disruptive cyberattacks.
5 Biggest Cyber attacks on the healthcare organization
#1
Company Name: Change Healthcare
Date of Event: February 2024
Type of Attack: Data Breach, Lack of Multifactor Authentication (MFA) and Ransomware Attack
Patients affected: one in every three people in the U.S. might have had their health details exposed due to the cyberattack on Change Healthcare.
Issue: The attack exploited several weaknesses in the cybersecurity posture of Change Healthcare, the chief of which was the absence of multi-factor authentication (MFA) on critical systems, a standard security practice. This created a vulnerability that was used to infiltrate and break many healthcare transactions and management systems of patient records. The nature of this attack was further complicated by the fact that it involved ransomware as a service, meaning the ransomware code is sold or given to other hackers to carry out attacks, further complicating the issue.
Response: Change Healthcare, part of UnitedHealth Group, distributed over $3.3 billion in payments to healthcare providers and hospitals affected by the breach to attempt to reduce financial damage and help stabilize operations in healthcare organizations. Further in the aftermath of the attack, UnitedHealth Group was criticized for what was seen as initially weak support offers to the affected entities, even though these responses were adjusted over time to accommodate better the needs of the impacted hospitals and healthcare providers. Recovery efforts included extended timelines for restoring services and are complicated by the continued risk of data leaks, even after the ransom payment to the attackers.
#2
Company Name: Banner Health
Year of Event: 2016
Type of Attack: Malware
Patients Affected: 3.7 million
Issue: Attackers breached the payment processing system of Banner Health’s food and beverage outlets, using this system as a gateway to access Banner Health Network servers with patient data.
Response: Banner Health upgraded to comply with the payment card industry data security standard (PCI DSS), ramped up its security monitoring for cyber threats and risks, and implemented tighter cybersecurity practices overall. In addition, started with program governance, identity and access management (IAM), and network and infrastructure security.
#3
Company Name: Medical Informatics Engineering (MIE)
Year of Event: 2015
Patients Affected: 3.9 million
Type of Attack: SQL Injection/ Malware
Issue: Attackers logged in to the network with hacking credentials and introduced an SQL injection exploit into a company database. A few weeks later, the attackers launched a second offensive, using c99 web shell malware to reach additional files.
Response: MIE notified the FBI and hired a team of third-party experts to remediate the attack vectors the cybercriminals used successfully. In addition, the organization has also significantly invested in safeguards and security measures such as security personnel, policies, procedures, controls, and monitoring and prevention tools.
#4
Company Name: Community Health Systems
Year of Event: 2014
People Affected: 4.5 million
Type of Attack: Data Breach
Issue: The company suffered a network data breach exposing information of around 4 million people. The data included personal details of individuals, including name, age, contact numbers and more.
Response: The company contacted outside forensics experts to conduct an investigation and incident remediation. In addition, it implemented efforts for future intrusions, including auditing and surveillance technology and advanced encryption technologies.
#5
Company Name: University of California, Los Angeles Health
Year of Event: 2015
Patients Attacked: 4.5 million
Type of Attack: Malware
Issue: Cyber attack on systems containing patient data, including social security numbers, dates of birth, health plan identification numbers and other medical data.
Response: Following a class-action lawsuit, UCLA Health agreed to enhance its cybersecurity practices and policies. The organization collaborated with the FBI and engaged computer forensic experts to secure its network. Measures included assessing emerging threats and identifying vulnerabilities to bolster their cybersecurity defenses.
How cyber attacks impact healthcare organizations
Clinical and Administrative Damage
Modern digital systems with IoT devices and interoperable capabilities in healthcare organizations provide numerous functionalities, including workforce planning, appointment scheduling, patient care, recordkeeping, and equipment management. A cyberattack on these systems can halt operations, delay treatments, cancel operations, and break down healthcare service delivery. This indicates that real-world health services can be vulnerable to cyber threats.
Example:
- In 2021, a strong cyberattack targeted one of the healthcare providers in the state of California. Patient data was stolen, and ransomware was spread, forcing the healthcare provider to shut down all its IT systems, including backup servers.
- This resulted in staff adopting manual processes to perform even the most basic operations, such as monitoring patient vital signs, which was disrupted.
- It took weeks to restore all the digital systems; patient care was affected. Consequently, the median waiting time increased by 47.6% at other regional hospitals because of the diversion of patients.
- The incident reportedly had close to $120 million in losses.
Why do Attacks happen despite IT preparations
Top attack types: ransomware, DDoS attacks
1. Ransomware: Healthcare organizations depend heavily on data and networked systems for patient care. Cyberattacks, such as ransomware, may render these systems paralytic in terms of further use by demanding a ransom for their release. It causes treatment delays, compromising patient safety and obstructs access to medical records.
According to the cybersecurity firm Emsisoft, 46 hospital systems were hit by ransomware in 2023, up considerably from 25 in 2022 and 27 in 2021. The assaults directly disrupted at least 141 hospitals, as IT systems and patient data could not be used.
2. DDoS Attacks: Distributed Denial of Service (DDoS) attacks overload networks so they can no longer function. Health providers who use networks for patient care, email communication, and other record access are greatly impaired in their operations. The reason for an attack is usually social, political, ideological, or financial, as is the case with hacktivists and cybercriminals.
In 2014, the hacktivist group Anonymous attacked Boston Children’s Hospital. Due to the controversial custody case, the network went down for almost a week. The medical operations suffered when the hospital and affiliated networks, which included Harvard University hospitals, lost access to the Internet. The recovery and mitigation efforts spent more than $300,000.
Data breaches, IT breakdown, Business Email Phishing
The healthcare sector is constantly attacked by data breaches; headlines now come almost daily. Those affected get e-mailed offers for free credit and identity monitoring—a familiar routine nowadays in life online.
According to the Ponemon Institute and Verizon Data Breach Investigations Report, the healthcare sector experiences more breaches than any other sector.
According to the HHS breach report, more than 15 million health records have already been exposed by breaches.
How frequent are data breaches in the healthcare industry? The scale of such events has been steadily increasing year after year. While in 2016, there were 329 reported breaches, in 2023, the number went through the roof at almost 739 breaches. There are almost two breaches every single day. Before 2019, there were fewer than 500 breaches annually, but since 2020, more than 660 breaches have happened yearly.
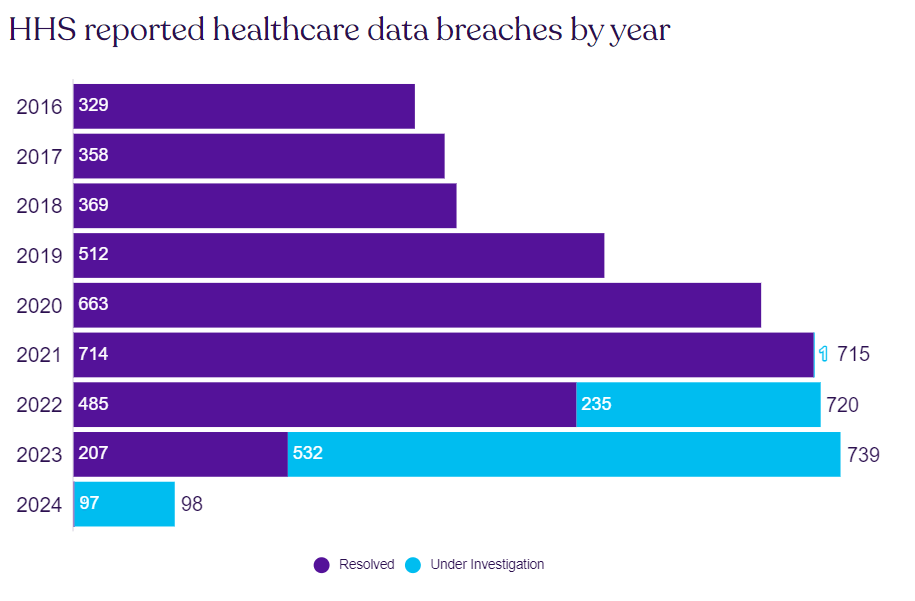 As of February 2024, the healthcare industry has already seen nearly 100 data breaches; the trend will continue.
As of February 2024, the healthcare industry has already seen nearly 100 data breaches; the trend will continue.
Email security has been a major concern with the online reports and data shared by the hospitals to the patients. According to Verizon, 93% of all cyber-attacks begin with a phishing email. The increase in email-related phishing in the healthcare sector has been staggering. According to Centripetal’s report, there were only 4% of phishing cases in 2012; in 2020, the number reached 42%. Most cyber-attacks, i.e., 91%, happen with phishing emails. Phishing is prevalent in healthcare, allowing cyber attackers to take advantage of often overworked professionals. The number of email phishing attacks has increased during the COVID-19 pandemic as the employees could not verify their suspicious links or threats as effectively.
Case study: top 5
The importance of application security, Firewalls
Zero trust, SASE MANAGEMENT, Managed Detection
Mobile device management
disaster recovery
Data backup as a service
Case Study 1: University of Vermont Health Network
Incident Overview: The University of Vermont Health Network (UVMHN) faced a significant cyberattack in October 2020, disrupting its IT systems across six hospitals. The attack, identified as a ransomware attack, affected various critical systems, including those used for patient care and administrative functions.
Response and Recovery: UVMHN implemented a robust disaster recovery plan and utilized data backup (DBaaS) service to mitigate the damage. The disaster recovery strategy included:
- Data Backup: Regular, secure backups of all critical data ensured that patient records and essential services could be restored quickly. DBaaS allowed UVMHN to store data offsite securely, reducing the risk of data loss during the attack.
- Disaster Recovery Plan: A well-prepared disaster recovery plan enabled the organization to respond swiftly to the attack, prioritizing restoring essential services and minimizing the impact on patient care. This plan included predefined roles and responsibilities, communication strategies, and step-by-step procedures for system recovery.
Outcome: The network restored critical services more quickly, minimizing patient care and administrative operations disruption. The incident underscored the importance of a comprehensive disaster recovery and data backup strategy to ensure operations continuity during cyberattacks (Source).
Case Study 2: Universal Health Services (UHS)
Incident Overview: In September 2020, Universal Health Services (UHS) experienced a significant ransomware attack that forced systems shutdown across more than 400 facilities in the U.S. The attack disrupted various hospital services, affecting patient care and the use of electronic health records (EHR) and clinical systems.
Response and Recovery: UHS’s response included the implementation of Zero Trust architecture and managed detection and response (MDR) services:
- Zero Trust Architecture: UHS adopted Zero Trust principles to enhance its cybersecurity posture. This involved strict access controls, where every access request was authenticated and authorized based on least privilege principles. This approach reduced the risk of lateral movement by attackers within the network.
- Managed Detection and Response (MDR): MDR services provided continuous monitoring and rapid incident response. These services helped detect the attack early and enabled quick containment and mitigation efforts, reducing the attack’s overall impact.
Outcome: Implementing Zero Trust and MDR services helped UHS recover from the attack more effectively and reinforced the importance of proactive cybersecurity measures. The incident highlighted the need for continuous monitoring and strict access controls to protect sensitive healthcare data and maintain operational integrity (Source).
Case Study 3: Finnish Psychotherapy Center Vastaamo
Incident Overview: In 2020, the Finnish psychotherapy center Vastaamo experienced a severe data breach. Patient records were stolen and used for blackmail. The breach exposed sensitive information, including therapy session notes, affecting thousands of patients.
Response and Recovery: Vastaamo’s response included enhancing application security and deploying advanced firewalls:
- Application Security: The center focused on improving secure coding practices and conducting regular penetration testing to identify and mitigate vulnerabilities. This included updating their electronic health record (EHR) systems and ensuring all applications were secure by design.
- Firewalls: Advanced firewalls were deployed to protect the network perimeter and monitor traffic for suspicious activity. This included configuring firewalls to prevent unauthorized access and detect potential threats in real-time.
Outcome: By enhancing application security and deploying robust firewalls, Vastaamo improved its cybersecurity posture and reduced the risk of future breaches. The incident highlighted the critical need for secure application development and continuous network traffic monitoring to protect sensitive healthcare data (Source).
Case Study 4: Paris Public Hospital System (AP-HP)
Incident Overview: In 2021, the Paris Public Hospital System (AP-HP) experienced a cyberattack that resulted in the theft of personal data from 1.4 million individuals tested for COVID-19. The attack exploited the hospital’s IT infrastructure vulnerabilities, including remote access systems.
Response and Recovery: AP-HP’s response included enhancing mobile device management (MDM) and securing remote access:
- Mobile Device Management (MDM): Implementing MDM solutions ensured that all mobile devices used within the hospital system were securely configured and regularly updated. This included enforcing security policies, such as device encryption and remote wiping capabilities, to prevent unauthorized access.
- Secure Remote Access: Enhancing secure remote access involved updating VPN configurations and implementing multi-factor authentication (MFA) for all remote connections. This reduced the risk of unauthorized access and ensured that only authorized personnel could access the hospital’s network remotely.
Outcome: The enhanced mobile device management and secure remote access solutions helped AP-HP protect sensitive patient data and reduce the risk of future cyberattacks. The incident highlighted the importance of securing mobile devices and remote access systems in healthcare environments. (Source)
Case Study 5: University of California, San Francisco (UCSF)
Incident Overview: In June 2020, UCSF’s School of Medicine was targeted by a ransomware attack that disrupted IT systems and encrypted vital data. The attack affected research and clinical operations, highlighting vulnerabilities in the university’s cybersecurity measures.
Response: Confronted with the critical decision of either paying a ransom to recover crucial research data and sensitive medical records or recovering it independently, officials at UCSF refused to pay the ransom. Instead, the university engaged its cybersecurity team and collaborated with law enforcement, cybersecurity professionals, and third-party service providers. They investigated the cyberattack, contained it, and set recovery efforts into motion with available backups and set up restoration processes.
Outcome: If the cyber attackers had demanded payment of a ransom, then the university would have faced great challenges. Although it could recover most of the compromised data and then return it to research, the case halted projects under process and delayed academic activities. Also, it brought about huge costs associated with recovery.
The ransomware attack also revealed weaknesses in UCSF’s cybersecurity framework. In reaction, the institution promised massive investments to strengthen its defenses, including establishing stronger security protocols and increasing cyber threat awareness among its faculty, staff, and students.
Although this has caused a lot of difficulties and expenses for the recovery process, it helps the institution uphold the integrity of research data and maintain ethical standards. This helps to reiterate that paying ransomware is neither a feasible nor an acceptable solution. Besides, it highlighted how strategic cybersecurity and an effective incident response plan were necessary to safeguard critical information and help maintain the confidence of all stakeholders. (Source)
Top Vendors and their Solutions
1. Verizon
Verizon is a leading provider of wireless and wireline communications services and products such as corporate networking solutions, data center and cloud services, security and managed network services, data, voice, local dial tone and broadband services, and local and long-distance voice services. It offers the healthcare sector an advanced 5G Network and real-time connectivity, enhances patient experiences and safeguards sensitive information
Offerings:
Digital Intelligence:
Verizon’s solution offers healthcare organizations real-time in-building connectivity and operational efficiency with 5G, mobile edge computing and network-as-a-service solutions.
Patient Experience:
With the omnichannel and digital customer experience, healthcare organizations can increase the satisfaction and loyalty of their patients.
Security and Privacy:
It helps healthcare companies secure sensitive information by proactively identifying and responding to threats.
Remote Care:
Verizon’s solution for the healthcare sector offers streamlined telehealth for expanded reach, convenience, and patient care effectiveness.
2. Palo Alto Networks/ Unit 42
Unit42 by Palo Alto is a global leader in incident response and security. It brings together threat researchers, incident responders and security consultants to create an intelligence-driven organization that manages cyber risks.
What Unit42 Do?
Unit consulting helps security leaders proactively manage cyber risk and respond to more than 1,000 incidents in a year. It utilizes threat intel to eradicate the threat.
Incident Response – It uses Palo Alto technology to respond to complex incidents.
Threat Intelligence – Security research puts threats into context, aiding products, services and the security community in defending against cyber attacks.
3. Arctic Wolf
Artic Wolf Network is a leading cybersecurity company that offers monitoring services to detect and respond to cyber threats. It monitors on-premises computers, cloud-based information assets, and networks from malicious activities, including ransomware, breaches, software attacks and more.
Solutions:
- Managed Detection and Response
- Managed Risk
- Cloud Security Posture Management
- Managed Security Awareness
- Incident Response
Offerings:
- Round the cloud coverage
- Complete visibility
- Continuous security posture improvement
- Strategic guidance
- Access to security Operations Experts
CyberArk
CyberArk is an identity security provider focused on privileged access management. It offers the most comprehensive security offerings across business applications, distributed workforces, hybrid cloud workloads and throughout the DevOps lifecycle. CyberArk also delivers targeted security solutions that help leaders stop reacting to cyber threats and prevent attack escalation before it harms or affects the business.
The Platform it offers:
- Access Management
- Identity Governance and Administration
- Privileged Access
- Secret Management
- Endpoint Privilege Security
- Secure Cloud Access
Check Point Software
Check Point Software Technologies is one of the leading AI-powered cloud-delivered cybersecurity platform providers. The company leverages AI to improve cybersecurity efficiency and accuracy. Check Point’s integrated healthcare cybersecurity solution enhances security and reduces costs by providing unified threat prevention across networks, cloud, mobile endpoints, and IoT, ensuring seamless protection without disrupting critical business and medical processes.
It offers:
- Cloud security solutions for advanced threat prevention, automated security and unified security for multi-cloud.
- Enterprise Mobile Security is for unified management, corporate data on personal access, data security, network security, threat prevention, and remote access.
- IoT Security Solutions for Enterprise, Industrial and Healthcare to prevent unauthorized access and lateral movement and real-time IoT threat intelligence.
Conclusion
The healthcare industry has higher stakes in cybersecurity compared with any other industry. The ‘why’ is very simple: it contains highly sensitive data, including personal information and patients’ financial and health-related data, which are prone to attacks and can cause huge losses. Cybersecurity attacks in the healthcare sector don’t mean causing business disruptions but can cause patient care delays.
According to a Black Book Market Research survey of CIOs, 59% of health systems surveyed are shifting cybersecurity strategies to mitigate and address user authentication and access to data. The motivation behind the healthcare sector’s being targeted for malicious cyber attacks, extortion, espionage and even cyberwarfare is the huge amount of data for which the security measures taken are minimal. The IBM X-Force Threat Intelligence Index 2023 found that the proportion of healthcare cases to which X-Force has responded has remained at approximately 5% to 6% for the past three years.
Additionally, government officials, tech experts, and security officers have long warned about cyber threats. Organizations such as the Joint Commission, ECRI, and the FBI are also increasing the number of alarms to notify about the threats and attacks that can have a dire impact. In 2022, the FBI ranked the healthcare sector as the most vulnerable of 16 important sectors for ransomware attacks.
FAQs
1. How can cyber attacks in healthcare be prevented?
- Educating the staff on why cybersecurity
- Prevention-first endpoint protection includes a multi-layered approach
- Implementing Zero trust enables healthcare to grant minimal credentials needed for tasks
2. What are the elements of healthcare cybersecurity?
- Protect Patient Data
- Secure IoMT Devices
- Ensure Continuity of Services
3. What is the HIPPA Security rule all about?
The HIPAA Privacy Rule establishes a federal baseline of standards for protecting individually identifiable health information by all health-overseen entities, including health plans, healthcare clearinghouses, and any healthcare provider that transmits health information in electronic form. The rule thus mandates the appropriate use and disclosure of such information and sets restrictions on it without an individual’s authorization.
4. What are the high-risk cyber attacks on the healthcare sector?
- DDoS
- Ransomware
- Insider Threats
- Supply chain Risks
- Data Breach
- Phishing
5. What are Healthcare cybersecurity best practices?
- Establish a security culture
- Use firewalls
- Implement Zero Trust as a core strategy
- Limited network access
[To share your insights with us as part of editorial or sponsored content, please write to psen@itechseries.com]