As cyber threats become increasingly sophisticated, organizations must take proactive measures to safeguard their sensitive data and critical infrastructure. The numbers tell a chilling story: data breaches surged by 34.5% in 2023, underscoring the urgency for businesses to address vulnerabilities in their systems effectively.
In response to this alarming trend, organizations are turning to threat intelligence platforms—powerful tools designed to identify, understand, and mitigate risks by providing real-time data, actionable insights, and in-depth analysis. These platforms consolidate threat information from diverse sources, empowering security teams to prioritize threats, make informed decisions, and prevent potential attacks before they occur.
The threat intelligence market is experiencing unprecedented growth, driven by an escalating demand for advanced cybersecurity solutions. Valued at $4.93 billion in 2023, the market is projected to reach $18.11 billion by 2030, growing at an impressive compound annual growth rate (CAGR) of 20.4%. This surge highlights the critical role of these platforms in addressing the increasing sophistication of cyber threats.
Also Read: Modernizing Legacy IT: A Critical Challenge for Decision-Makers
What are Threat intelligence Platforms?
Threat intelligence platforms (TIPs) play a pivotal role in enhancing an organization’s ability to defend against cyber threats. These platforms equip security teams with the tools needed to proactively identify, analyze, and respond to emerging risks in a dynamic threat landscape.
Designed to streamline and enhance cybersecurity workflows, TIPs provide comprehensive insights into known threats, such as malware and cyberattacks, enabling swift and accurate detection and mitigation. By automating the aggregation and management of threat data, these platforms allow analysts to focus on deeper investigations and strategic response planning rather than manual data collection.
Additionally, TIPs facilitate seamless collaboration between threat intelligence teams, stakeholders, and other security systems by simplifying the sharing of threat intelligence. These platforms are available as flexible solutions, including both software-as-a-service (SaaS) and on-premises deployments, catering to the diverse needs of organizations.
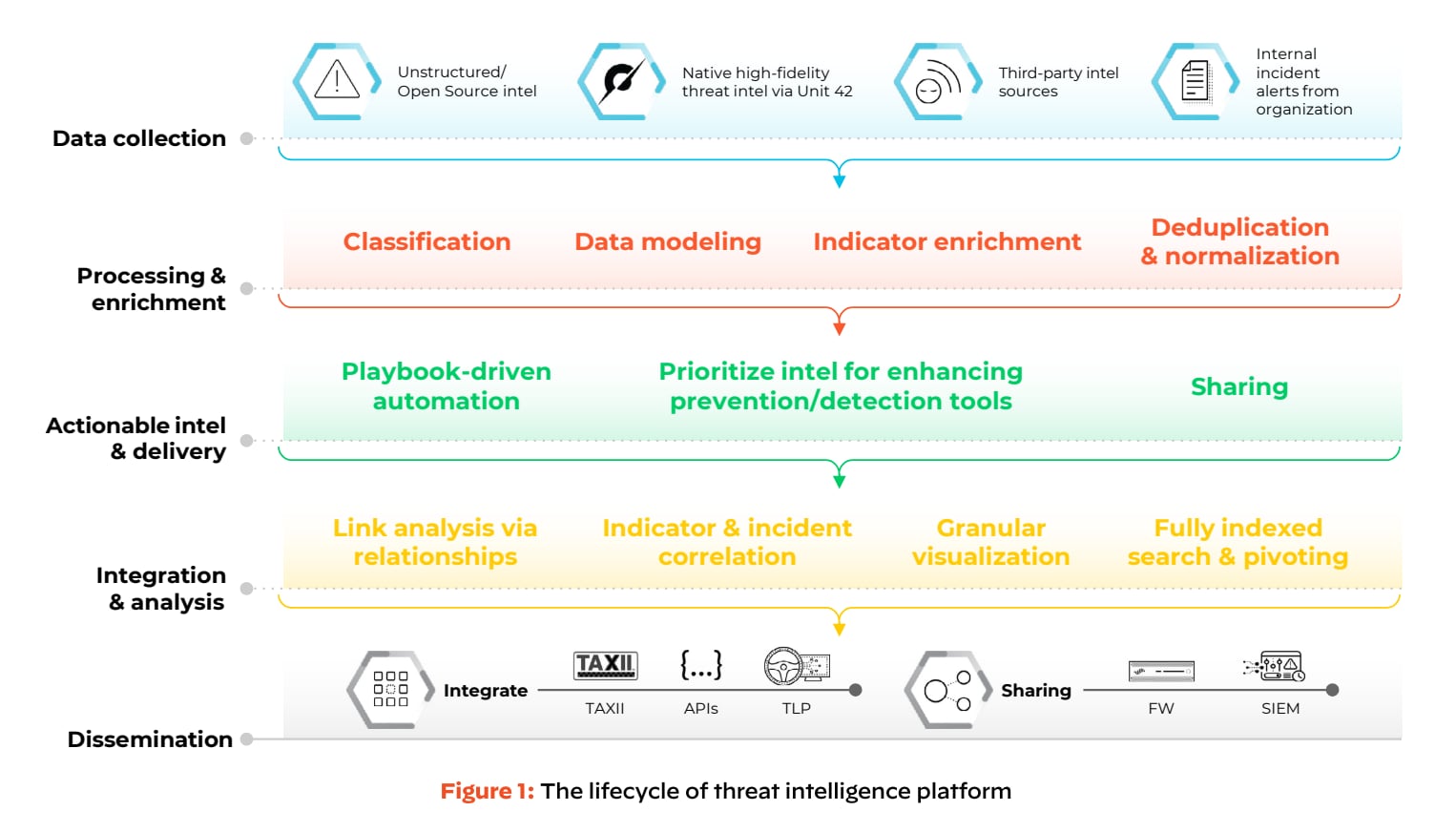
Manually aggregating, analyzing, and sharing this data is not only time-intensive but also increasingly impractical. This is where Threat Intelligence Platforms (TIPs) prove invaluable. Historically, security teams relied on fragmented tools and manual processes to gather intelligence from diverse formats like STIX/TAXII, JSON, XML, PDF, CSV, and even emails. They then shared insights through spreadsheets, online portals, or email chains. However, this method has become insufficient due to the sheer volume of data, the sophistication of modern threats, and the urgency required to mitigate risks.
Threats such as malware, ransomware, phishing, botnets, and DDoS attacks are growing exponentially, generating millions of indicators of compromise daily. For organizations, responding promptly and accurately to these threats is critical to minimizing potential damage. Yet, traditional processes often overwhelm security teams, creating noise, false positives, and difficulty in discerning actionable insights from irrelevant data.
TIPs address these challenges by automating the aggregation and analysis of threat data, enabling security teams to focus on high-priority risks. They streamline workflows, filter out irrelevant noise, and provide clear insights into genuine threats, helping organizations mitigate risks efficiently. By adopting TIPs, businesses can elevate their threat intelligence efforts, ensuring a faster and more effective response to the ever-growing cyber threat landscape.
Leading Threat Intelligence Platforms to Know in 2025
Crowdstrike Falcon Intelligence
CrowdStrike Falcon Intelligence is a cutting-edge threat intelligence platform designed to provide real-time visibility into cyber threats. By leveraging the power of its Falcon platform, CrowdStrike delivers industry-leading endpoint and workload security, enabling organizations to detect, investigate, and mitigate threats with unmatched efficiency.
Features
Comprehensive Threat Intelligence
Falcon Intelligence goes beyond traditional security measures by integrating advanced threat feeds, proactive threat hunting, and intelligence sharing. Its extensive database of threat actors and attack patterns empowers security teams to stay ahead of evolving cyber risks.
Advanced Detection and Response
Renowned for its Endpoint Detection and Response (EDR) capabilities, CrowdStrike enhances security operations with in-depth behavioral analytics and automated threat analysis. These capabilities enable organizations to identify and neutralize complex threats before they escalate.
AI-Driven Innovation
Powered by machine learning and behavioral analytics, CrowdStrike Falcon Intelligence continuously evolves to detect sophisticated cyber threats. Its ability to analyze attack patterns and predict malicious activities makes it a top-tier choice for enterprises seeking robust cybersecurity defenses.
By combining real-time intelligence, automation, and advanced analytics, CrowdStrike Falcon Intelligence sets the benchmark for modern threat intelligence, equipping organizations with the tools needed to combat the ever-changing cyber threat landscape.
Palo Alto Nеtworks WildFirе
Palo Alto Networks WildFire is a cloud-based malware analysis solution designed to detect and prevent unknown threats, including zero-day exploits and advanced malware. By leveraging multi-technique detection and real-time threat intelligence, WildFire enhances cybersecurity across networks, endpoints, and cloud environments.
Key Capabilities
- Ultra-Fast Threat Response – WildFire can automatically orchestrate prevention measures within 300 seconds of detecting a threat, minimizing potential damage.
- Global Intelligence Network – With over 85,000 subscribers, WildFire benefits from a vast community that continuously shares threat intelligence, strengthening collective defense mechanisms.
- Seamless Security Integration – Designed to work effortlessly with Palo Alto Networks’ Next-Generation Firewall and AutoFocus, WildFire enhances contextual threat intelligence and security automation.
- Multi-Technique Threat Detection – WildFire leverages dynamic analysis, static analysis, machine learning, and bare-metal analysis to identify even the most sophisticated cyber threats.
IBM X-Forcе Exchangе
IBM X-Force Exchange is a cloud-based threat intelligence platform designed to enhance cybersecurity posture through collaborative and actionable insights. Launched in 2015, it enables security professionals to research global threats, aggregate intelligence, and respond to potential attacks more effectively.
Features
- Seamless Security Integration – IBM X-Force Exchange supports API-based integration with various security tools, allowing organizations to incorporate threat intelligence into their existing security frameworks.
- Collaborative Threat Intelligence – Security teams can share insights and validate threats within private groups, fostering a collective defense strategy.
- Automated Threat Feeds – The platform generates real-time, automated threat feeds that integrate with firewalls, intrusion detection systems, and other security solutions, providing immediate visibility into emerging threats.
Microsoft Defender Threat Intelligence
Microsoft Defender Threat Intelligence (Defender TI) is a powerful platform designed to enhance threat hunting, incident response, vulnerability management, and intelligence analysis. By consolidating and streamlining threat infrastructure analysis, Defender TI enables security teams to assess alerts accurately and respond to threats in real-time.
What it can do?
Efficient Threat Intelligence Workflow – Defender TI reduces the time analysts spend on data discovery, collection, and parsing, allowing them to focus on deriving actionable insights about threat actors.
Centralized Threat Data – Instead of navigating multiple repositories, analysts gain a unified view of threat indicators, including DNS data, WHOIS information, malware signatures, and SSL certificates, enhancing their ability to detect and mitigate threats effectively.
Seamless Threat Correlation – Defender TI automates data aggregation and ensures structured intelligence, enabling security teams to pivot between data sets effortlessly and make timely assessments of suspicious domains, hosts, and IP addresses.
Cyberint
Cyberint is a leading cybersecurity provider, specializing in threat intelligence and digital risk protection. By leveraging insights from the open, deep, and dark web, Cyberint helps businesses proactively detect, analyze, and mitigate cyber threats before they escalate.
Core Offerings
- Threat Intelligence: Collects real-time intelligence from multiple sources, including social media, dark web forums, and threat feeds, to provide a comprehensive view of potential risks.
- Attack Surface Management: Identifies and monitors exposed assets, vulnerabilities, and external attack vectors, reducing the likelihood of cyber incidents.
- Phishing Detection & Mitigation: Detects brand impersonation, phishing campaigns, and social engineering attacks, helping organizations respond swiftly.
- Digital Risk Protection: Monitors for brand abuse, data breaches, and reputational threats, ensuring companies can take action before damage occurs.
- Threat Hunting & Investigation: Equips security teams with the tools and expertise needed to conduct proactive investigations and hunt for cyber threats.
Also Read: Combatting the rise in AI-assisted fraud in 2025
Implementing a Threat Intelligence Platform
Successfully implementing a Threat Intelligence Platform (TIP) involves a strategic and structured approach to ensure its effectiveness and alignment with an organization’s cybersecurity objectives. Here are the key steps:
1. Assessing Intelligence Needs
Organizations must first define their unique security goals by understanding their specific threat landscape. This includes identifying high-risk assets, potential impacts of various threat scenarios, and the types of threats most relevant to their environment. The primary objective is to enhance the detection, identification, and investigation of security threats and malicious actors.
2. Selecting the Right Platform
Choosing a TIP that seamlessly integrates with existing security tools is essential. The platform should be capable of aggregating and analyzing data in formats compatible with the organization’s current systems, such as SIEM, firewalls, and intrusion prevention systems. Flexibility and compatibility with diverse data sources are key factors to consider.
3. Training Security Teams
Proper training is critical to maximize the TIP’s potential. Security personnel need to understand the platform’s technical capabilities, interpret threat intelligence accurately, and prioritize actionable insights. A cross-functional approach that shares threat-related information across various teams ensures comprehensive threat management.
4. Integration with Security Ecosystems
The TIP must integrate seamlessly with existing security tools and protocols. This includes establishing workflows for automated responses and ensuring the platform enhances overall security operations. Best practices involve embedding the TIP into broader security processes, such as monitoring, planning, remediation, and automated threat sharing, to streamline defenses and response efforts.
5. Continuous Evaluation and Optimization
The dynamic nature of the cyber threat landscape necessitates regular evaluation and updates to the TIP. Staying ahead of emerging threats requires modernizing security processes, automating workflows, and maintaining a proactive approach to threat intelligence. Continuous improvement ensures that the TIP evolves alongside the ever-changing threat landscape.
In the End
Cyber threats are evolving fast, and businesses can’t afford to be reactive anymore. With attacks growing in scale and sophistication, having a solid defense strategy is no longer optional—it’s a necessity. That’s where Threat Intelligence Platforms (TIPs) come in.
For industries like finance and healthcare, where data security is critical, TIPs offer a way to stay ahead of cybercriminals by detecting threats early, preventing breaches, and strengthening overall security. They automate threat detection, reduce false positives, and streamline security operations, giving teams the time and insights needed to tackle real risks.
Beyond security, TIPs also make financial sense. With cybercrime losses reaching trillions, investing in a strong threat intelligence solution helps prevent costly breaches and protects brand reputation. By integrating TIPs into their cybersecurity strategy, organizations can move from playing defense to taking a proactive stance—ensuring long-term security and business resilience.


