With the increase in businesses migrating to the cloud for vital strategy formulation, extension and competition, companies recognize the requirement for new security concerns. Surprisingly, as it would seem, among the respondents to the Ermetic-IDC survey, two-thirds of CISOs claim that their organizations have been victims of a cloud data breach during the last 18 months. Remember, 38% targeted them much more frequently, with 10 or even 100 breaches.
The benefits of cloud computing are evident, but its risks also have to be protected. Organizations must be cautious while treading this modern information technology landscape. They need to understand both what cyber security can offer them in terms of improvements and what it will take to protect the accountability of their business, staff, and clientele from cyber threats.
What is Cloud Security Architecture?
Cloud security architecture reveals the approach of both the provider and the user in their joint effort to ensure the security of the cloud. It divides the responsibility of those who are supposed to safeguard and the ways.
People involved in business, providers or customers, handle the specific technical features in their related sectors or departments. Secure cloud applications and the control of access to them also occur.
For securing apps, examples of measures include:
- Encoding data for transfer and keeping it as safe as possible while it is being stored
- Developing tools like website application firewalls or bot management to prevent system attacks and secure data extraction.
- Detecting and destroying malware. Preventing unauthorized access to critical data is significant.
- Monitoring the reports and log activities throughout the cloud environment.
For access to apps, security measures include:
- Regarding network security solutions, SASE (secure access service edge) is the most prospective as network protection must rely heavily on the cloud, combined with SD-WAN, secure web gateway, and cloud access security broker.
- Authentication techniques like multi-factor authentication (MFA) and single sign-on (SSO) are umbrellas to protect the organization and users from data breaches and fraud.
- Remote access mechanisms are designed through the recommended VPN-less proxy secure digital offices.
The security architectural design is significant because cloud security is complex. Risks such as uncontrollable device access, failure of MCNPs, and hazards like APTs require attention. The abbreviations as a service include models like infrastructure as a service (IaaS), platform as a service (PaaS), software as a service (SaaS) and desktop as a service (DaaS), where both the provider and the customer manage their unique architectures.
When it comes to cloud security, who should take responsibility?
The answer to what security tasks in the cloud are shared by the cloud service provider and the user might ultimately depend on the type of service and how it will be used; however, cloud security duties are usually shared to some extent. Another example is when customers engage the services of an IaaS provider from a public cloud provider. The provider will take care of the physical interfaces, the hypervisors and the data storage layer. Meanwhile, customers will only handle the application level or the Operating System/Data layer.
This infrastructure is the cloud, where the provider takes care of the low-level details like the optimal software for computing, database, and other hardware usually maintained by the cloud center. Meanwhile, the client will instead concentrate on the aspects, such as permission to access and firewall configurations.
In Public Cloud services like Platforms as a Service (PaaS), Software as a Service (SaaS), and Desktop as a Service (DaaS), more security features are provided by the cloud provider, unlike in Infrastructure as a Service (IaaS), where the responsibility for security falls more on the cloud consumer. For instance, in a SaaS setting, consumers are not required to be in charge of server administration, database management, encryption encodings, and so on. However, this shouldn’t discourage businesses from recognizing that SaaS still carries risks; users must assess the provider and determine how to manage application access securely.
The ownership of the private and hybrid clouds is typically attributed to the companies that are solely meant for their use. This type of cloud shifts the responsibility of cybersecurity to the companies. On one hand, there is undoubtedly an increase in the level of security in private as well as hybrid cloud data, brought about by a reduced dependence on shared infrastructure; on the other hand, there arises a requirement for greater involvement on the part of the client in the security of his data.
What are the main security challenges of primary clouds?
There are numerous security challenges in the cloud or heightened relative to their on-premises counterparts. These include:
- Traffic Filtering, Monitoring, and Blocking: WAFs play a vital role in cloud security and in handling the humongous volume of traffic from various cloud applications. Failure to screen this traffic could result in it transmitting malware and requests from malicious bots.
- Protection of APIs: The numerous cloud APIs connecting to other services may result in costly data breaches if improperly protected and allow unauthorized data transfer.
- Bot identification and management: Botnets are responsible for numerous automated cyberattacks and, therefore, require proper identification and management to avoid issues like brute-force login attempts.
- Malware, APTs, and cyberattacks: The public accessibility of the cloud computing stack exposes it to constant and widespread pressure from various cybersecurity threats, which may cause access disruptions and compromise sensitive information. Thus, it is one of the fundamental cloud security risks.
- Inadequate or ill-defined security measures in cloud security controls: The failure of companies to update security controls that are necessary while migrating applications into the cloud is one of the common reasons, and this can cause problems relating to the lack of proper security.
- Misconfiguration: Incorrect configurations of cloud resources can go unnoticed for an extended period before a security breach occurs.
- Network/WAN security: The transition from the MPLS WAN architecture through SD-WAN to support cloud applications mandates adopting new security mechanisms and architectures like Secure Access Service Edge (SASE) for secure access to Software as a Service (SaaS) and replacing the traditional centralized security model of WANs.
Top AWS Services for Cloud Security
#1 AWS Identity and Access Management (IAM)
AWS Identity and Access Management (IAM) refines precise access control, helping to set permissions to determine who can access which AWS resources and under what conditions. Use this fine-grained access control to protect AWS resources while targeting the principle of least privilege.
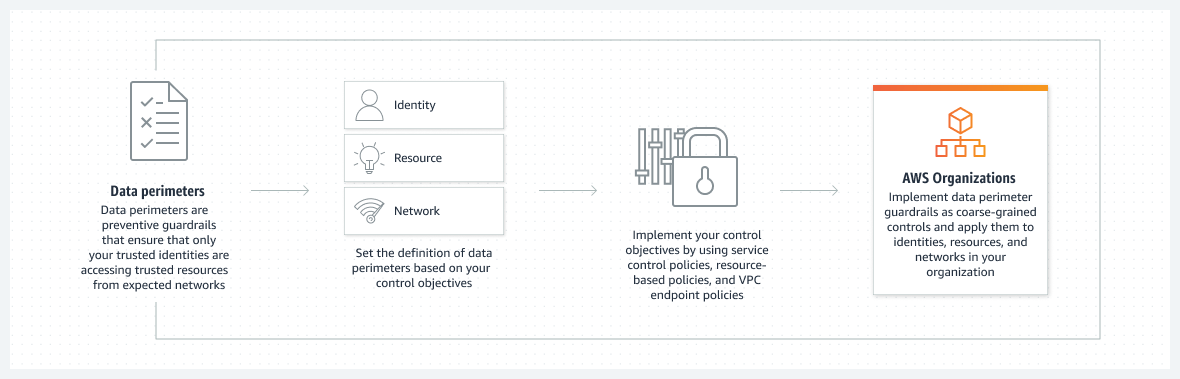
- How it works: To define access permissions to AWS resources, IAM policies do it. These policies can be attached to IAM roles in the account or to specific AWS resources. When a request is made by a client to AWS, IAM evaluates this request against the policies and either permits or denies it. The “Understanding how IAM works” section in the IAM User Guide should be referred to for more details.
- The IAM Policy Language: IAM uses a policy language known as JSON to enable users to precisely state their access requirements using actions, resources, and conditions specified in policies. For more insights, see the IAM JSON policy reference.
- Types of Policies for Access: IAM offers the flexibility to apply policies to both IAM roles and the AWS resources supporting resource-based policies. Identity-based policies and resource-based policies collaborate in defining access control. Visit the “Policies and permissions in IAM” section of the IAM User Guide for more information about the policy types.
- Preventive guardrails: Preventive guardrails allow for the establishment of boundaries for maximum permissions in IAM roles. Service control policies, permissions boundaries, and session policies can be utilized to control the permissions assigned to an IAM role. To learn more about establishing a preventive guardrail, look at the “Data perimeters on AWS” resource.
#2 Amazon GuardDuty
Amazon GuardDuty is a cloud security tool that seeks to detect threats across AWS environments by consistently monitoring for malicious activities and unauthorized actions. Utilizing machine learning, anomaly detection, and malicious file discovery, it integrates AWS and third-party sources to protect any AWS accounts, workloads, and data.
GuardDuty analyzes vast amounts of data from various AWS sources, such as CloudTrail logs, VPC Flow Logs, and DNS query logs. Additionally, it monitors S3 data events, Aurora login events, and runtime activity for services such as EC2, ECS, and EKS—covering serverless container workloads on Fargate.
Key Features include:
– Accurate threat detection at the account level.
– Continuous monitoring across AWS accounts and workloads without complexity or added cost.
– Cloud-optimized threat detections.
– Priority threat severity levels.
– Automated threat response and remediation.
– Fully managed, scalable threat detection.
– Simple one-step deployment without the need for extra software or infrastructure management.
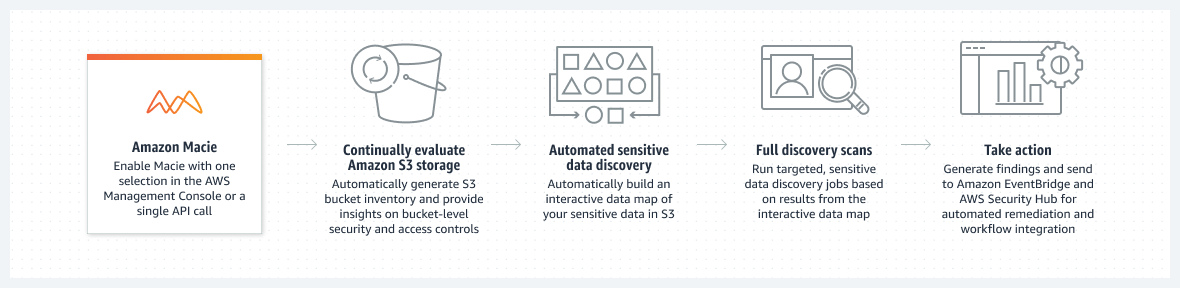
#3 Amazon Macie
Amazon Macie is a cloud security service that employs machine learning and pattern matching to find sensitive data. It offers insights into data security risks and facilitates automated protection measures.
With Amazon Macie, users can:
– Improve their data security posture by discovering sensitive data across their S3 environment, enhancing visibility, and automating the remediation of data security risks.
– Ensure compliance with scheduling data analysis to ensure sensitive data is found and adequately protected.
– Protect sensitive data at any migration process to verify if it has been appropriately protected during data ingestion.
– Continuously monitor business-critical data automatically and continually.
How it works
#4 AWS Config
AWS Config helps configure and evaluate all AWS resources against best practices and internal policies. This information can be used during operational troubleshooting, audits, and compliance.
The benefits that users get from AWS Config are:
– Managing the change of resource configurations
– Evaluating configurations against desired states
– Simplify troubleshooting and remediation processes
How it Works
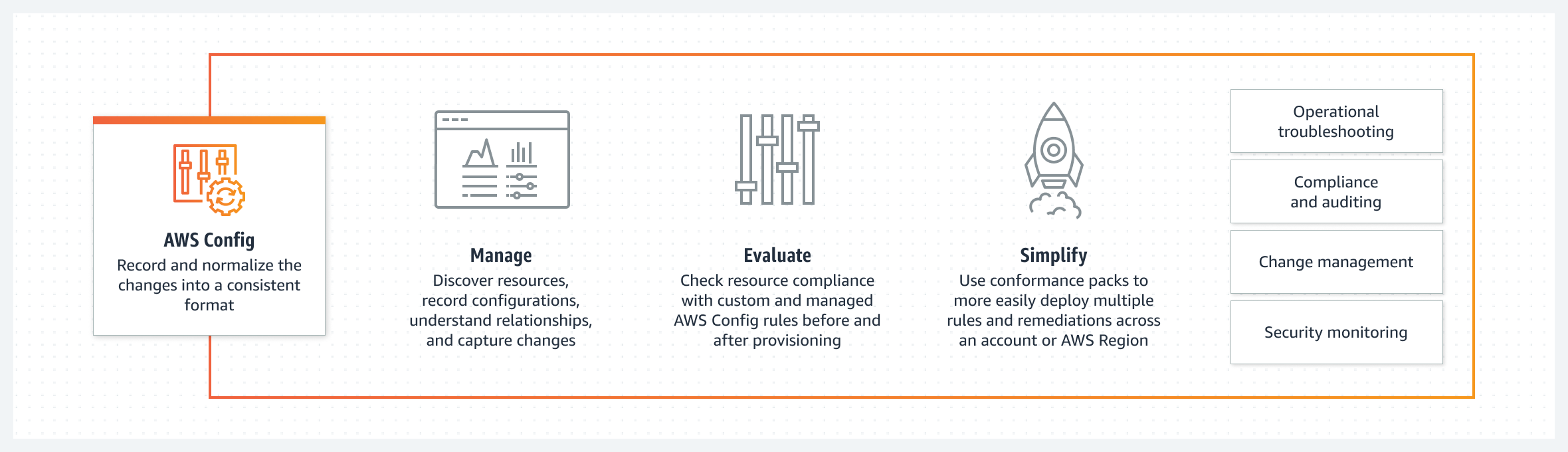 Use cases of AWS Config:
Use cases of AWS Config:
– Streamline operational troubleshooting and change management by identifying existing resources and quickly capturing configuration changes to address operational issues.
– Develop a compliance-as-code framework by translating the compliance needs in AWS Config rules and then automating the assessment of resource configurations across the organization.
– Constantly audit security monitoring and analysis by assessing resource configurations for potential vulnerabilities and reviewing configuration history to analyze security posture after any potential incidents.
#5 AWS CloudTrail
AWS CloudTrail allows users to track activity and API usage for auditing, security monitoring, and operational troubleshooting. It logs all the account activity related to actions across your AWS infrastructure, offering control over storage, analysis, and remediation actions.
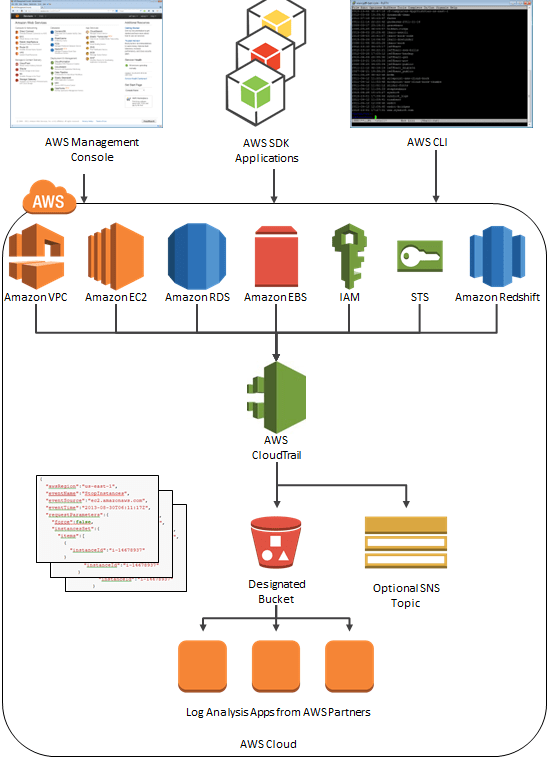 Benefits of CloudTrail:
Benefits of CloudTrail:
- Demonstrating compliance, enhancing security posture, and consolidating activity records across Regions and accounts.
- Providing visibility into user activity by documenting actions taken on your account.
- Documenting each of the crucial data elements that touch every action, like the requester, services utilized, actions executed, action parameters, and AWS service response elements.
- This information facilitates tracking of changes made to AWS resources and resolves operational issues. It aids in putting a protective fence around compliance with internal policies and regulatory standards.
#6 Amazon Inspector
Amazon Inspector is a cloud service that automatically detects workloads such as Amazon EC2 instances, Lambda Functions and containers. It scans them to identify software vulnerabilities and united network exposure.
Key Benefits of Amazon Inspector:
- Identify and find software Vulnerabilities.
- Centrally manage software bill of materials for all monitored resources.
- Using risk score helps prioritize remediation, reducing mean time to remediate (MTTR).
- Scans and maximize vulnerability assessment between agent-based and agentless scanning.
#7 AWS Security Hub
AWS Security Hub is a service that provides cloud security posture management (CSPM) and analyzes resources in your AWS accounts, workloads, and resources for deviations from best security practices using automated and continuous security checks. It allows you to detect misconfigurations and aggregate security alerts (referred to as findings) in a standardized format, enabling you to get an integrated view of security issues that are more easily investigated and remediated.
What are the key benefits of Security Hub?
Security Hub simplifies the management and enhancement of security across your AWS accounts, workloads, and resources. With a simple click, one can detect deviations from security best practices at the account and resource levels against controls outlined in the AWS Foundational Security Best Practices standard and others supported, such as the CIS AWS Foundations Benchmark, the National Institute of Standards and Technology (NIST), and the Payment Card Industry Data Security Standard (PCI DSS).
It automatically aggregates security findings from AWS and partner services in a standardized data format. It gathers findings from all enabled security services running across your AWS accounts, including intrusion detection findings from Amazon GuardDuty, vulnerability scans from Amazon Inspector, and sensitive data identification findings from Amazon Macie. Also, it gathers findings from partner security products using a standardized AWS Security Finding Format, eliminating time-consuming data parsing and normalization efforts. This enhances mean time to resolution by automated response and remediation actions.
One can set custom automated response, remediation, and enrichment workflows using Security Hub integration with Amazon EventBridge and other integrations to create Security Orchestration Automation and Response (SOAR) and Security Information and Event Management (SIEM) workflows.
Security Hub Automation Rules can automatically update or suppress findings in real-time. Customize your Security Hub dashboard with information specific to you, allowing for easy identification of patterns, vulnerabilities, and threats and leading to more timely responses. Customize the view of Security Hub, be able to choose and modify widgets displayed, apply and save filters to create contextual views based on specific criteria, and prioritize the view of your organization’s security posture according to your needs.
#8 AWS Shield
AWS Shield is an advanced, tailored protection program that arranges data across the AWS cloud by identifying threats using exabyte-scale detection.
The Functioning of AWS Shield
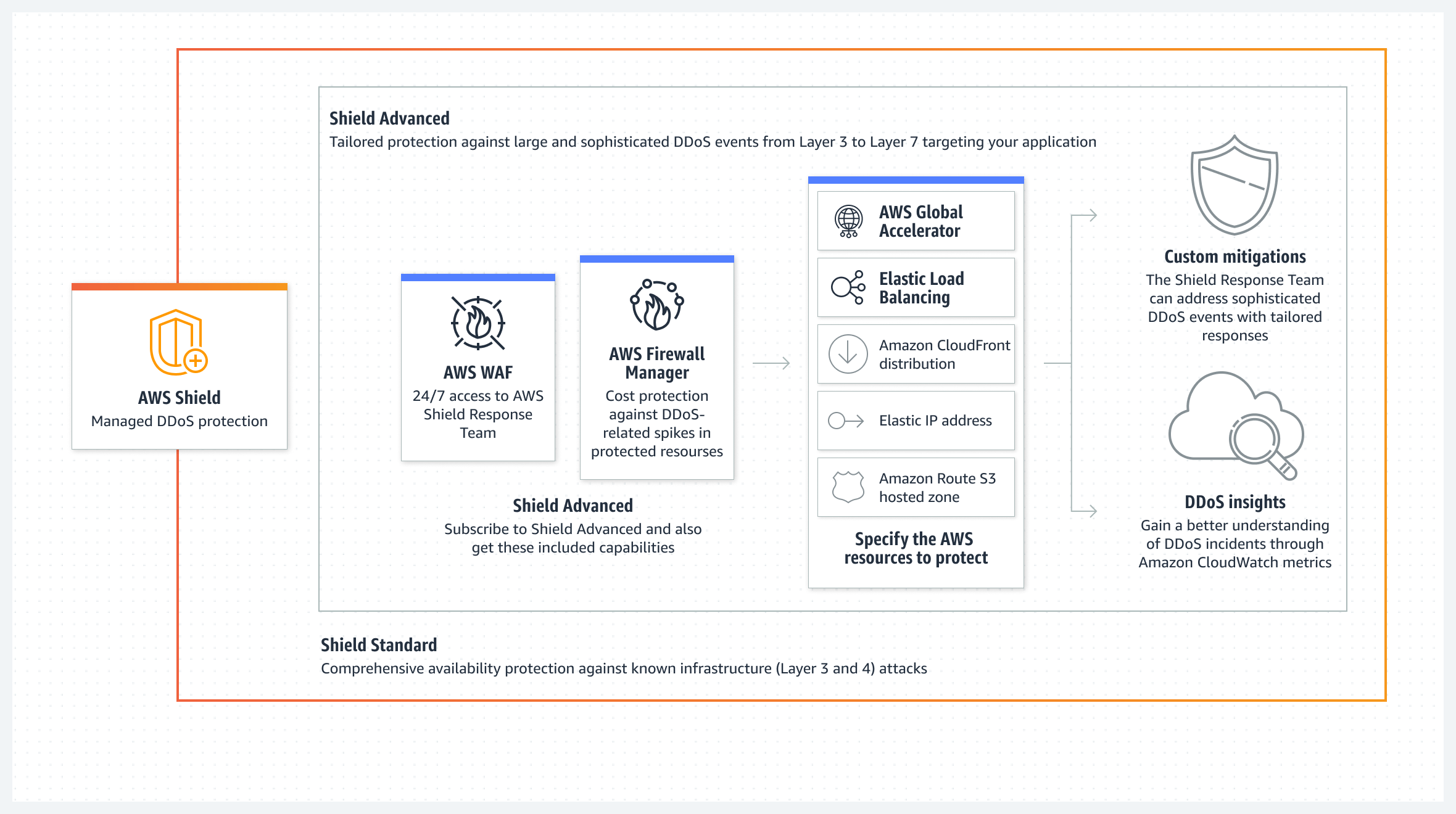 Key Benefits:
Key Benefits:
- Automatic detection and mitigation of sophisticated network-level distributed denial of service (DDoS) events.
- Custom application protection against DDoS risks via Shield Response Team integrations.
- Improved Visibility, better insights and cost savings for DDoS events.
#9 AWS Secrets Manager
AWS Secrets Manager is a service for managing secrets, focusing on guarding access to applications, services, and IT resources. With this service, it will be much easier for businesses to administer, rotate, and retrieve database credentials, API keys, and other secrets throughout their lifecycle. In this way, Secrets Manager ensures that the secrets businesses have to manage to access resources across the AWS Cloud, third-party services, and on-premises environments are secured and administered.
AWS Secrets Manager Features:
- Automatic secrets rotation without disrupting applications
- Automatic replication of secrets to multiple AWS Regions
- Programmatic retrieval of secrets
- Audit and monitor secret usage
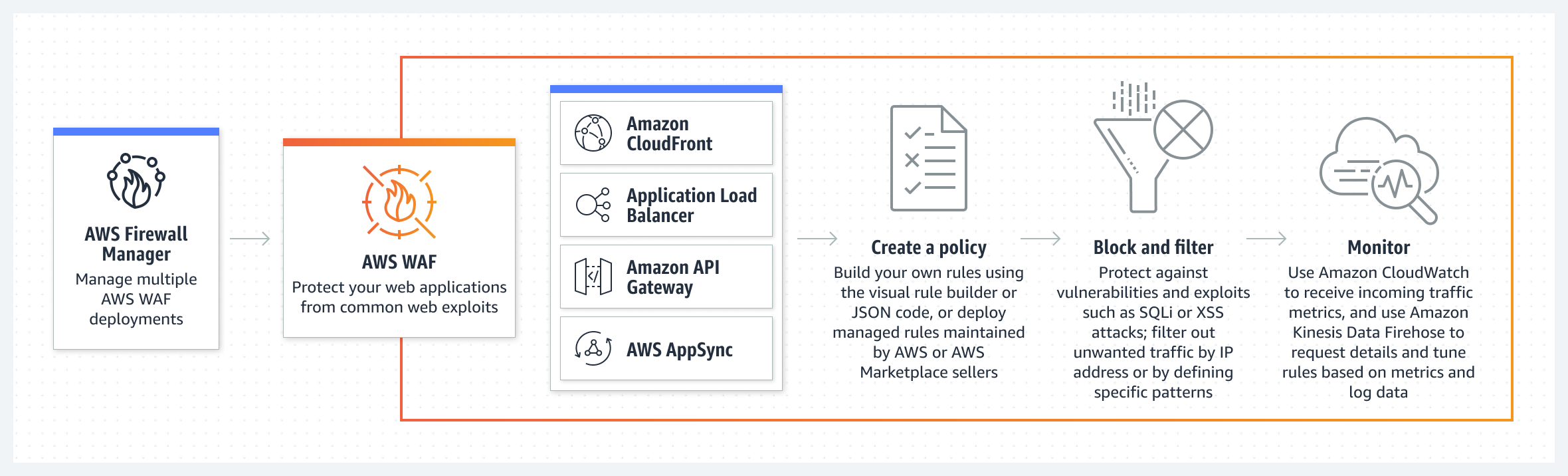
#10 AWS WAF
AWS web application firewall (WAF) helps protect web applications from attacks. It allows businesses to configure rules that block, monitor or allow counts of web requests. It is configured based on conditions that businesses as users define. It additionally simplifies creating rules to block typical web exploits like SQL injection and cross-site scripting. The conditions include IP addresses, HTTP headers, HTTP body, URI strings, SQL injection and cross-site scripting.
With AWS WAF, individuals can build a centralized set of deployable rules across many sites. This means you can create a single set of rules that applies to all the sites in an environment containing hundreds of websites and web applications. Users can use these rules across applications, eliminating the need to create new rules whenever they want to apply them to a new application.
Features of AWS WAF:
- Web traffic filtering
- AWS WAF Bot Control
- Account Takeover Fraud Prevention
- Full feature API
- Real-time visibility
How does AWS WAF work
 Conclusion
Conclusion
These are the top 10 AWS cloud security services, providing many tools to fortify your cloud infrastructure against security threats. Incorporating these services into business workflows will elevate the security posture and streamline security tasks, establishing a robust and proactive defense against the continuously evolving landscape of cyber threats.
FAQs
1. What is IaaS?
Infrastructure as a Service
2. What are hypervisors?
A hypervisor is software used to host multiple virtual machines on a single physical server. Each virtual machine operates independently with its own OS and applications. The hypervisor manages and allocates CPU, memory, and other resources to ensure efficient utilization of the underlying hardware.
3. How does cloud security differ from traditional IT security?
Cloud security involves unique challenges such as shared responsibility models, increased reliance on automation, and the need to secure data across multiple environments. Unlike traditional IT security, cloud security requires a more dynamic and scalable approach.
4. What are the main security challenges of cloud computing?
Some primary security challenges of cloud computing include traffic filtering and monitoring, protection of APIs, bot identification and management, malware and cyberattacks, inadequate security controls, misconfigurations, and network/WAN security issues.
5. Who is responsible for cloud security, the provider or the user?
The cloud service provider and the user share responsibility for cloud security, depending on the service and deployment model. While providers manage certain aspects like physical infrastructure, users are responsible for securing their applications and data.
6. How can businesses ensure compliance and regulatory adherence in the cloud?
Businesses can ensure compliance and regulatory adherence in the cloud by implementing security best practices, regularly auditing their cloud environment, using compliance frameworks, and leveraging cloud security services that offer compliance capabilities.
7. What are some best practices for enhancing cloud security?
Best practices for enhancing cloud security include implementing strong access controls, encrypting sensitive data, regularly monitoring and auditing cloud environments, educating employees about security risks, and staying updated on security trends and technologies.
8. How can AWS cloud security services help businesses mitigate security risks?
AWS cloud security services offer a range of tools and capabilities to help businesses mitigate security risks. These services include identity and access management, threat detection, secrets management, web application firewall, and compliance monitoring, among others.
9. What are the benefits of using AWS cloud security services?
Benefits of using AWS cloud security services include improved security posture, simplified management of security tasks, automated threat detection and response, compliance assurance, and scalability to meet evolving security needs.
10. How can businesses ensure proper configuration and management of AWS resources for security?
Businesses can ensure proper configuration and management of AWS resources for security by following AWS best practices, regularly reviewing and updating security configurations, implementing automation for security tasks, and leveraging AWS security tools for monitoring and remediation.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]




 Conclusion
Conclusion