Not long ago, analytics teams would support the business units but were really more of an internal utility provider and less of a strategic partner. With time, when data started to be critical to decision-making and the architecture of products, such teams became better armed with tools, they got more diversified in their roles, and clearer on what could be accomplished through data. For many businesses now, the data ecosystem is considered a part of their technology stack. Leading organizations are shifting toward a new paradigm: treating data as a product.
The evolution of DataSecOps parallels a very similar transformation that took place within application security following the introduction of CI/CD and DevOps. First, agile software development and cloud-based applications pushed the creation of DevOps. This exposed security flaws, showing security that drove inside the DevOps process. This gave rise to the DevSecOps methodology.
According to the Cybersecurity & Infrastructure Security Agency (CIS), 65% of Americans received at least one online scam offer, over 600,000 Facebook accounts are hacked daily, 47% of American adults have had personal information exposed by cyber criminals, and 1 in 3 homes with computers have been infected with malware.
Data’s move to the cloud followed a similar pattern. While not all data from an organization or individual has moved there, the cloud is an integrated part of how data is stored and applications are supported. To a large degree, this shift entailed the invention of a whole new approach to data security—what is now known as DataSecOps.
DataSecOps is an agile, holistic approach to infusing security into data operations. It puts a premium on the rapid delivery of data value with integral competencies in data privacy, safety, and governance. A distinguishing factor from prior methods is that DataSecOps fuses security as one continuous component of data processes and not merely as an afterthought. This facilitates data democratization through the conformance of security with the evolving tempo of data usage.
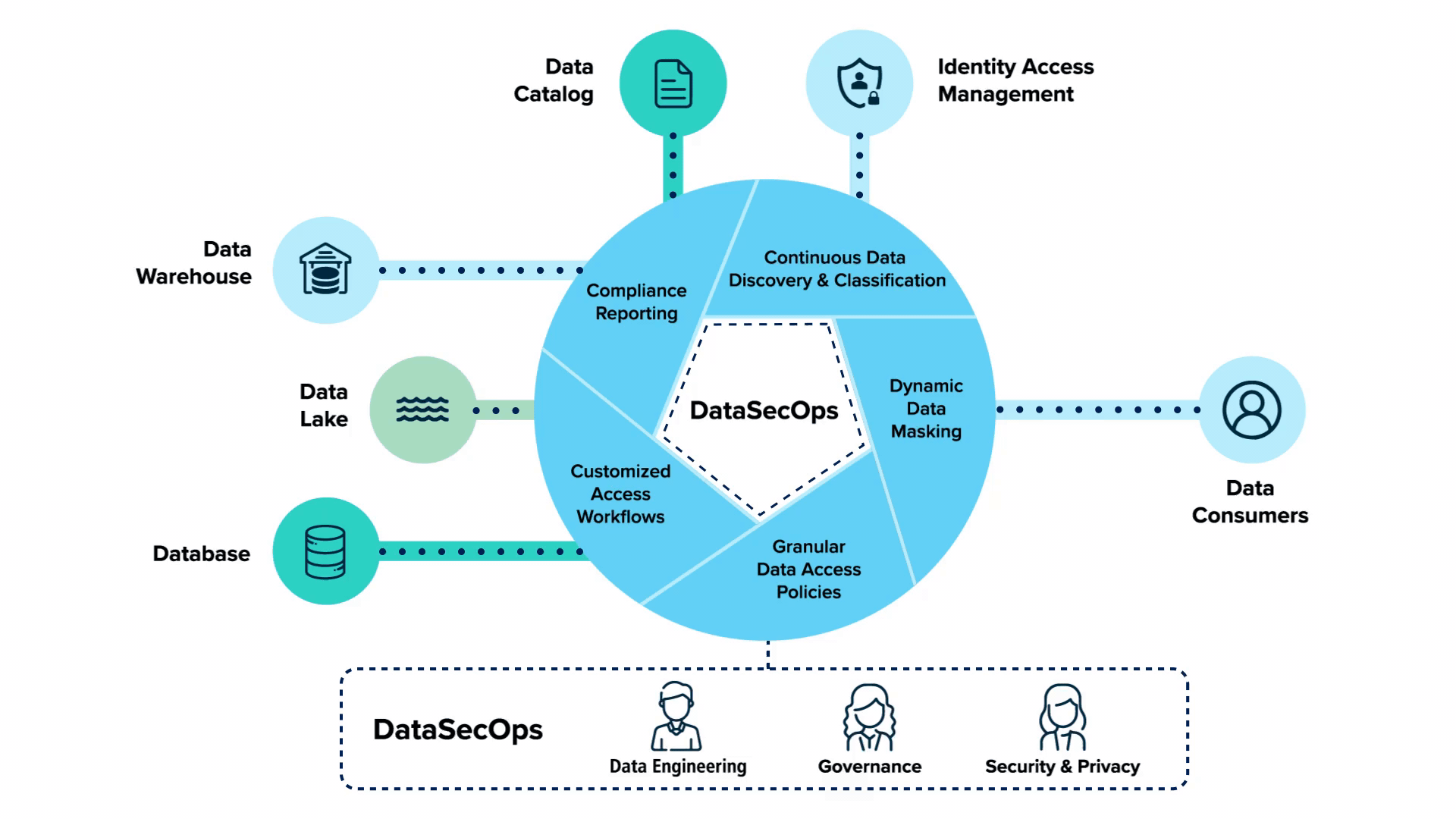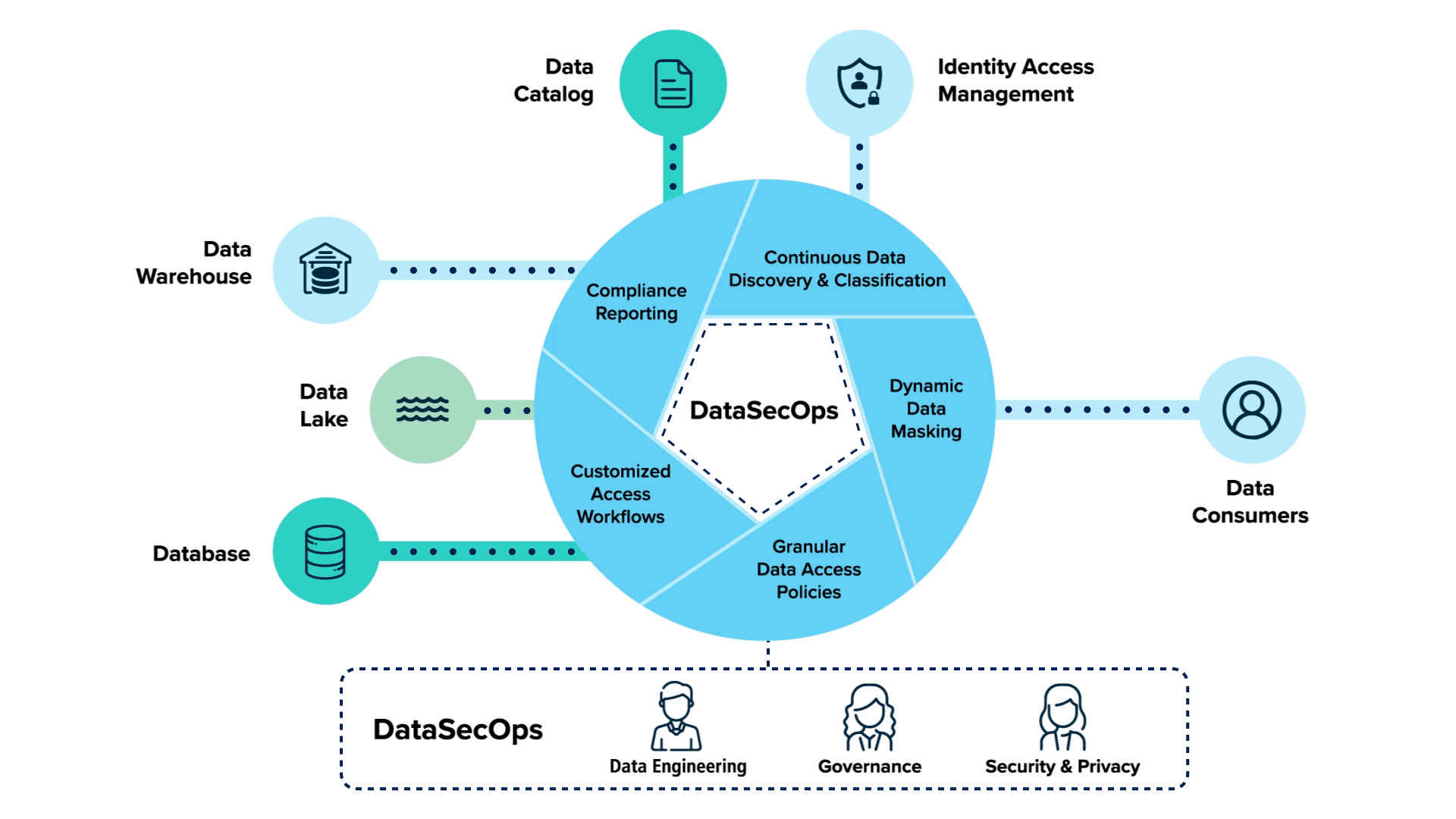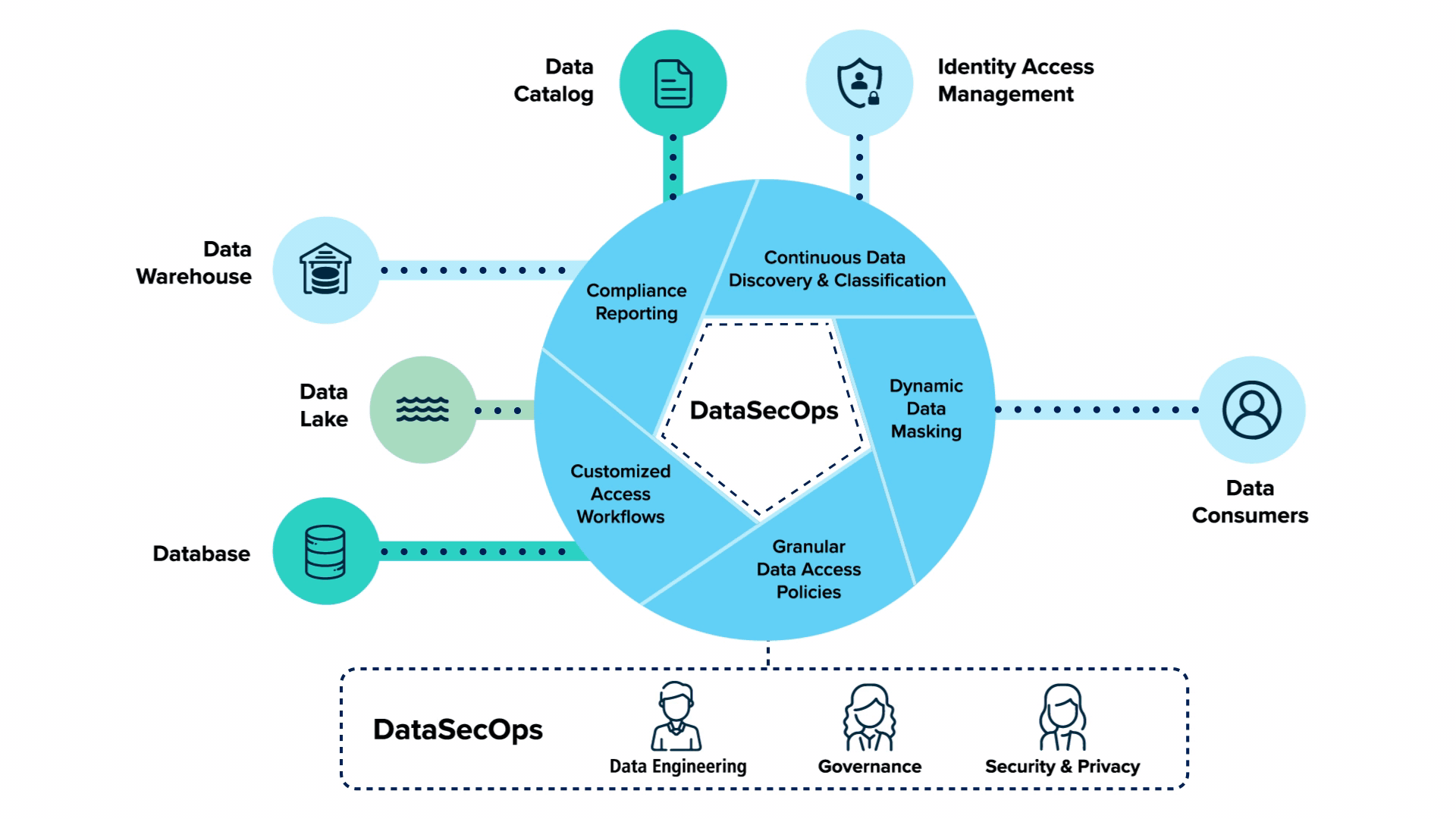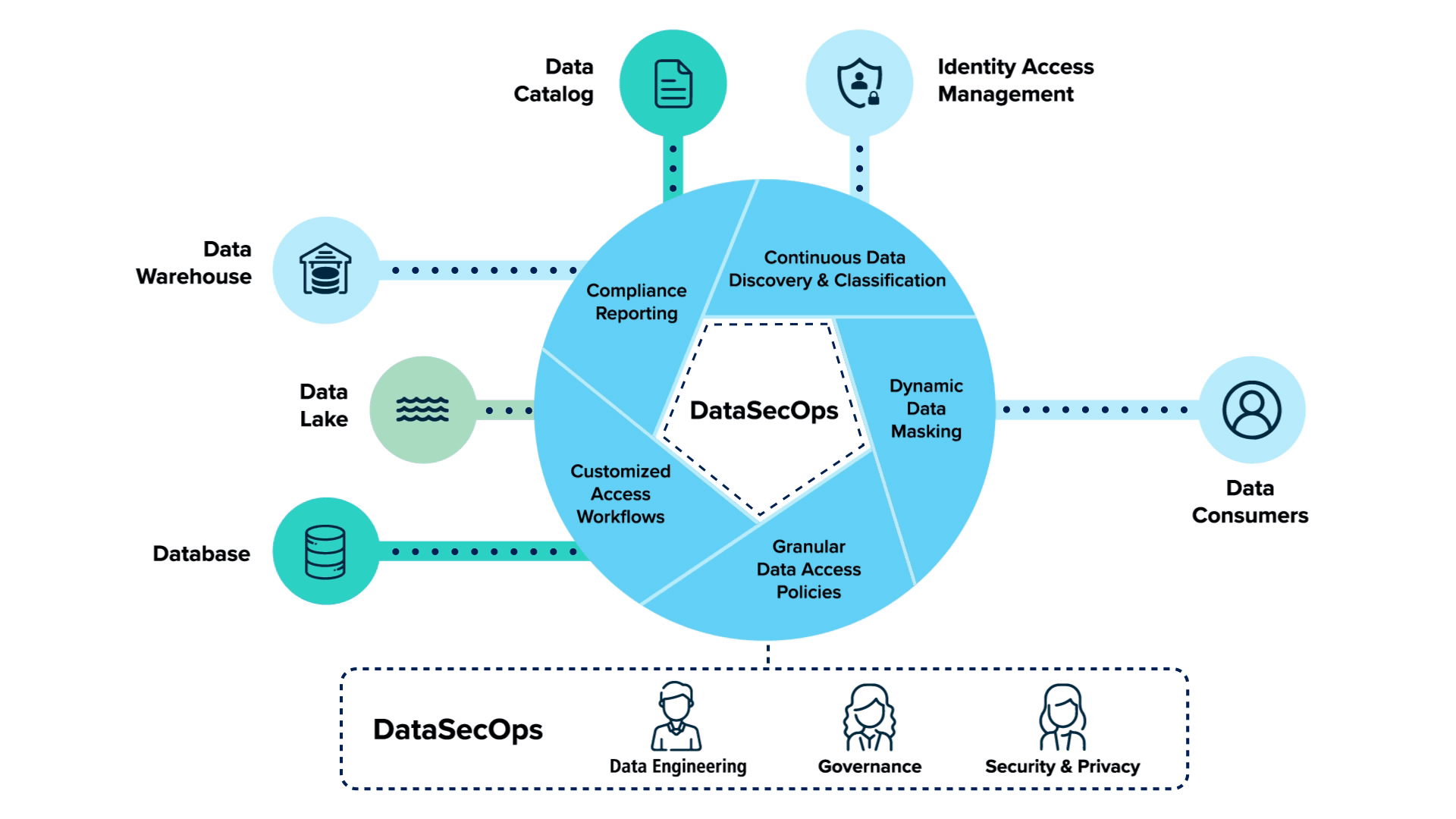
In addition, DataSecOps embodies some evolution into how organizations are handling security for their data. By integrating security deep into data operations, an organization will be certain about the security of its data assets and business objectives.
Importance of AI and ML in Modern Cybersecurity and DataSecOps
Artificial intelligence is the process of simulating human intelligence in machines programmatically set to learn from data, reason, and make decisions. Cybersecurity AI, through the analysis of huge volumes of data, may identify possible threats or predict future attacks, enabling an organization to react more efficiently and effectively.
Machine Learning, simply a subset of AI, specifically focuses on the development of algorithms that will allow a program to learn without explicit programming. In other words, it detects patterns in data, thereby making decisions or predictions possible based on those patterns. Therefore, machine learning makes it possible to identify cyber threats accurately and react to them.
AI and ML in cybersecurity hold an array of advantages in terms of threat detection, faster response times, and automation of commonplace security tasks. These technologies have been designed to learn from data and tune their algorithms toward the detection of new and emerging threats involved in data breaches and other cyber-attacks. In this way, AI and ML can be leveraged to enhance threat detection and response within an organization.
Also Read: AI in Cybersecurity a Threat or Not?
Increasing Demand for AI and Machine Learning in Cybersecurity and DataSecOps
In the face of ever-increasing levels of sophistication and complexity in cyber threats, the demand for technologies that could detect and respond to them is increasing. AI and ML answer this demand by using machine learning algorithms and advanced analytics that let one quickly and efficiently identify patterns and anomalies indicative of malicious activity.
AI and ML in cybersecurity are assumed to be genuinely growing in importance, considering the increasing adoption of these technologies across industries. According to MarketsandMarkets, a report suggests that, after being valued at USD 9 billion in 2020, the global AI in cybersecurity market is likely to reach USD 38 billion by 2026. The growth is derived specifically from the need for next-generation threat detection and response capabilities and an adequate supply of data and computing power fueling these technologies.
An important area where AI and ML are expected to play a major role is the identification of zero-day threats. Traditional cybersecurity solutions, generally rule-based in order to identify threats, have been found ineffective against new or evolving threats. On the other hand, AI and ML learn from the data and identify unknown prior threats by recognizing the patterns and anomalies indicative of malicious activity.
Apart from threat detection, AI and ML automate routine security tasks and reduce the workload for human security professionals. For example, AI and ML can automatically detect and respond to low-level threats such as phishing attacks or malware infections, freeing security professionals to handle more advanced threats.
The growing importance of AI and ML in cybersecurity can be explained in general by the increasing necessity of detecting and monitoring sophisticated cyber threats with the help of advanced technologies. Organizations, under constant pressure of ever-increasing volume and complexity, need to invoke AI and ML to keep up the pace in securing the digital assets from such cyber-attacks.
Also Read: Redefine IT Security Paradigms with Zero Trust Architecture
DataSecOps Principles
Continuous Security Integration
Continuously integrate security in data operations than integrating it when required. Out-of-place security processing at project inception averts costly changes at later stages. The implementation cost reduces by addressing security issues as and when reported.
Adopt Continuity
Avoid ad-hoc security projects but introduce security, privacy, and governance without any break. Security, privacy, and governance continuously need refreshing to cope up with the changes made in data and the user’s profile.
Abstraction of Environments and Automation
Keep separate testing, staging, and production environments for data operations. Configure continuous automated testing that will ensure the security configurations and restriction to access of the data are functioning as intended.
Prioritize Sensitive Data
Apply especially to the securing of sensitive data. Resources should be focused on protecting sensitive data. It involves identifying and understanding sensitive data and controlling access, implementing necessary protections.
Establish Clear Data Ownership
All data objects must have clearly assigned owners. Ensure owners manage access to their data and understand how it’s used, particularly sensitive data.
Simplify and Standardize Data Access
Simplify the process of data access. Reports massage requests for access are consistent, and wherever possible, policies of withheld access ought to be automated to enable fast and safe access to data.
Accelerating DataSecOps Adoption
Companies are attempting to adopt DataSecOps across model tools and stakeholders to make business value realization quicker. They are digitizing data governance and containerization, and providing support for this through automation and self-service tools, thereby adding value to delivery. Other components include data lineage, data security, data quality, and environment abstraction. They now come with data and logic tests to support self-service and ensure a better quality of the data service.
Enterprises must organize the whole data estate into DataSecOps pipelines, break up data silos, and offer a cohesive Data Factory view. Enterprises can evaluate the advantages of the tools and techniques involved in the data estate by building pipeline-as-code with end-to-end integration across the data fabric. The partial integration of DataOps will be driven by modern technologies.
AI and ML Applications in DataSecOps
Threat detection and prediction
AI systems are now a cornerstone in cybersecurity decision-making. These systems adeptly address a broad spectrum of threats, automating highly accurate incident response strategies. This evolution is pivotal in handling the rapidly evolving nature of cyber threats and managing vast volumes of threat intelligence inputs.
AI-powered threat detection is highly effective, but cybercriminals constantly evolve their attack strategies to evade it. They leverage advanced techniques such as polymorphic malware, zero-day exploits, and generative AI-driven phishing attacks.
AI-based threat detection is designed to counteract these evolving tactics, including expanding attack vectors like IoT devices, cloud deployments, and mobile devices. Its objective is to address the increasing volume and velocity of cyberattacks, particularly ransomware.
Anomaly detection
“AI in anomaly detection is one particular field that is gaining traction. Several industries have used anomaly detection to improve operations successfully. As a result, the market for anomaly detection is anticipated to grow to USD 4.45 billion by 2023.” – Veritis
Machine learning and AI is crucial for anomaly detection due to its ability to handle complex technical challenges. Anomaly detection identifies deviations from expected patterns, and its integration with machine learning is essential as organizations expand and operations become more intricate.
First, machine learning processes large volumes of diverse data, including transactions, textual data, images, and videos, which is impractical for manual inspection due to time constraints and resource limitations. Second, it excels in processing unstructured data like documents, emails, and images, which traditional methods struggle to analyze. Third, machine learning offers versatile algorithms tailored to specific anomaly detection challenges and data types.
In addition, AI/ML enables real-time anomaly detection, which is critical for domains such as fraud detection and cybersecurity, enhancing operational efficiency through automation. Deploying machine learning algorithms strengthens organizational systems against potential threats and vulnerabilities, creating a secure and resilient operational environment by predicting and addressing vulnerabilities before they escalate.
Automated incident response
AI and ML are revolutionizing incident management with their ability to analyze large datasets, identify anomalies, and predict potential issues. These technologies are particularly effective in handling the unpredictability of engineering-caused incidents.
In a technology company, AI and ML algorithms continuously monitor application performance and user interactions. Recognizing patterns that precede incidents enables the incident response team to act proactively, minimizing user disruption. Integrating AI and ML with observability tools such as Datadog and collaborative platforms such as Slack Enterprise Grid enhances predictive incident management.
AI and ML’s anomaly detection capabilities are transformative in observability and monitoring. A software development team using AI-driven anomaly detection with tools can identify anomalies in user interactions that indicate potential code bugs. This allows the incident response team to address issues early, preventing significant disruptions.
Predictive maintenance and system optimization
AI-driven predictive maintenance involves real-time monitoring of machines and equipment, utilizing advanced analytics and machine learning algorithms to identify potential malfunctions before they occur. This approach optimizes asset performance and extends the lifespan of equipment.
Adopting a proactive maintenance strategy, AI-driven predictive maintenance addresses equipment issues preemptively to avoid downtime. The machine learning model analyzes factors correlated with machine failure, notifying maintenance personnel and executives in advance to enable proactive intervention while the machine remains operational. This distinguishes it from reactive maintenance, which addresses repairs only after a breakdown occurs.
Interrelation between AI and DataSecOps
Under the rapidly evolving landscape of data management and analytics, one of the most critical developments is incorporating security within data ops—DataSecOps. This ensures that provisions for security are no longer retrofitted but intrinsic to the life cycle of data. Considering the trend set by growing complexity and scale in data environments, the role of AI and ML in enhancing these processes has become absolutely indispensable.
Improve Efficiency and Accuracy of Data Management
AI and ML are exceptionally good at processing large amounts of data efficiently. In DataSecOps, they automate the parsing and analysis of data streams and logs, flagging patterns and exceptions that could signal potential data breaches or compliance issues rapidly. For instance, AI algorithms could establish a prediction for—thereby recognizing—unauthorized access or unusual patterns of data usage, which immediately activates precautionary security measures.
Reducing Human Error
AI Integrate into DataSecOps significantly reduces the incidence of human error. Activities for management and securing of data are complex, sometimes mundane, and can easily be overlooked when managed manually. The systems that AI provides monitor relentlessly and precisely for the integrity and security of data without continuum fatigue or bias that humans happen to have.
Response Times Acceleration to Security Incidents
Equipped with advanced, AI-driven capabilities, DataSecOps can trace a plethora of threats or vulnerabilities at a speed no human can. In turn, this fast detection offers an organization the ability to respond almost instantaneously to data security incidents and reduce potential damage. Fast, automated responses are critical in high-stakes industries that have to protect sensitive information, such as finance and healthcare.
Optimize Data Operations
AI technologies further enhance these feedback loops within DataSecOps processes by evaluating operations and security feedback in order to improve data handling practices. This is not only going to improve the security posture but may also benefit the general efficiency and quality of data operations. Besides that, AI can automate all mundane and repetitive tasks, freeing data professionals to focus on more strategic and value-added activities.
Implementing AI in DataSecOps
#1 Identify high-value use cases and focus on these first
Spot high-value areas of usage in streamlining the integration of AI within cybersecurity frameworks. Emphasis needs to be given to those areas where AI can bring payload instantly, such as threat detection and response. Apply AI to large datasets analyzed at higher speeds than traditional methods in identifying threats. In doing this, it strengthens security posture and proves a case of value AI in cybersecurity for wide-scale adoption.
#2 Invest in Data Infrastructure and Governance
Design resilient data infrastructure and stringent governance processes that can leverage AI for cybersecurity. Allow accessibility, reliability, and scalability by putting in place secure storage solutions, efficient processing capabilities, and reliable transmission systems. Clearly provide policies on the quality, privacy, and security of data to be maintained so that integrity and compliance with set regulations are observed. These aspects will, in a real sense, provide the kind of backbone that support any effective AI-driven strategy related to cybersecurity.
#4 Focus on explainability and fairness
Ensure that AI systems used in cybersecurity are explainable and fair. Develop AI models that justify their conclusions in understandable terms. This enables the security professionals to build trust and effectively use the decisions from AI. Design AI to avoid biases that may compromise security measures or lead to unfair targeting. Bias is rigorously tested and refined within algorithms to make sure that it’s not something allowed to perpetuate from historical data. This approach deploys effective and ethical AI solutions for better security without let-ups in equity and transparency.
#5 Bake Security into AI Development Tools
Embed security processes into the development lifecycle of AI to reduce AI’s vulnerability. This includes strong encryption, timely security audits, and grants of the principle of least privilege for access to data. Integrate these practices to make AI systems secure, transparent, and fair. Such a holistic, multi-layered approach continues strengthening defenses against emerging cyber-attacks with continued integrity and confidentiality of sensitive information.
Ethical Considerations of Using AI in DataSecOps
- Privacy and Data Protection: A very important part of AI systems in DataSecOps deal with huge amounts of sensitive data. Ensuring that such systems respect rules and regulations relevant to privacy protection, such as GDPR or CCPA, and protecting privacy would be an important task. It raises ethical concerns related to unauthorized access to such data and the misuse of personal data.
- Bias and Fairness: AI models can further the biases that were already periodized into the training data. An example is in DataSecOps; such disproportionate security measures may result from flagging suspicious activity from a specific user or group. It is ethically paramount to ensure fairness and reduce bias from AI algorithms.
- Transparency and Explainability: AI decisions could have huge impacts on data security practices and compliance. Ethical usage of AI should thus come with transparency on how decisions are made and the ability to explain them—especially in security measures that affect user access or privacy.
- Accountability: The question of accountability is a troublesome one in the case that AI systems make any decision affecting the security of the data. It is essential to define lines of responsibility concerning an AI system’s actions, including failures and breaches.
- Security of AI Systems: The protection of AI systems from attacks that intend to disturb their integrity or functionality is necessary. Protection against data poisoning, model theft, or other adversarial attacks specifically designed to mislead or deceive AI.
Top AI & ML Providers for DataSecOps
-
- IBM Watson for Cyber Security: IBM’s Watson integrates AI into security operations. It helps in automating the analysis of large volumes of risk data and supports real-time threat detection and response.
- Splunk: Offers advanced analytics driven by machine learning to enhance threat detection, investigation, and timely response. It’s particularly useful for gaining insights from big data and automating routine tasks.
- Microsoft: This is a scalable, cloud-native, SIEM and SOAR system. Azure Sentinel uses AI to analyze large volumes of data across an enterprise rapidly.
- Palo Alto Networks, Cortex: Provides AI-based continuous security operations. It uses machine learning to improve security across network, endpoint, and cloud environments.
- Darktrace, Enterprise Immune System: Uses machine learning and AI algorithms to detect and respond to cyber-threats across diverse digital environments.
- CrowdStrike, Falcon Platform: Leverages AI to offer next-generation antivirus, endpoint detection and response (EDR), managed threat hunting, and much more.
- Google Cloud, Chronicle: Part of Google Cloud, Chronicle is a global security analytics platform that helps enterprises manage and understand their security data more effectively with machine learning.
- McAfee, Enterprise Security Manager (ESM): Utilizes machine learning to enhance threat management, helping organizations identify, investigate, and respond to threats faster.
- Cisco, SecureX: An integrated platform that uses machine learning to enhance visibility, automate workflows, and strengthen security across network, endpoint, cloud, and applications.
Conclusion
AI and ML have impacted DataSecOps transformationally, enabling organizations to deal with the rising complexity and volume of cyber threats. Equipped with advanced capabilities in threat detection and prevention, data discovery and classification, incident response, and recovery, an organization can enhance the capability for threat detection, streamlining of security operations, and security posture. The future of AI and ML in data security operations presents very exciting opportunities for organizations to proactively protect against new threats and apply proactive strategies in securing their data assets.
FAQs
1. How does DataSecOps differ from traditional cybersecurity practices?
Traditional cybersecurity practices often involve reactive measures implemented after development, focusing on perimeter defense and endpoint protection. In contrast, DataSecOps integrates security into every stage of development and operations, promoting automation, collaboration, and continuous monitoring to prevent and respond to security incidents swiftly.
2. What role does automation play in DataSecOps?
Automation plays a critical role in DataSecOps by streamlining repetitive tasks such as vulnerability scanning, compliance checks, and incident response. Automated processes ensure consistency, reduce human error, and enable faster response times to security incidents.
3. How does AI and ML contribute to DataSecOps?
AI and ML enhance DataSecOps by enabling advanced threat detection, anomaly detection, and predictive analytics. These technologies automate routine security tasks, improve response times to security incidents, and provide insights for proactive risk management.
4. What challenges might organizations face when adopting DataSecOps?
- Integration complexity: Adapting existing workflows and tools to include security measures.
- Skill gaps: Ensuring teams have the necessary expertise in both security and DevOps practices.
- Tool proliferation: Managing multiple security tools and ensuring they work together seamlessly.
- Compliance: Meeting regulatory requirements while maintaining agility in development cycles.


