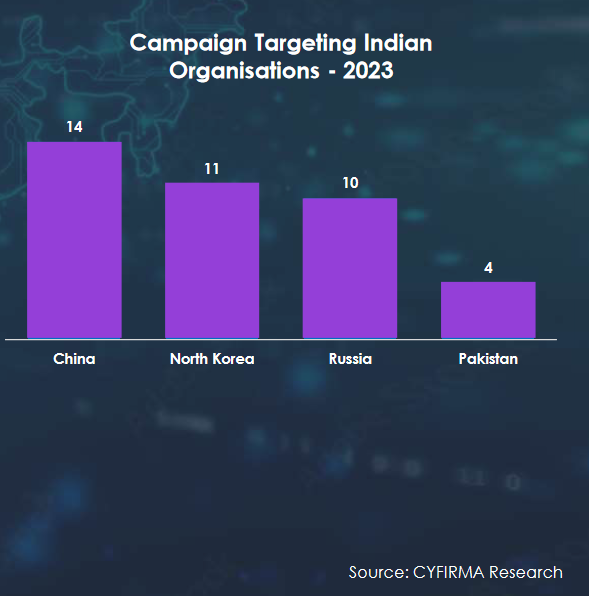
In the latest report on cybersecurity threats, the analysts have named India as the most-targeted country in SE Asia. According to CYFIRMA’s India Threat Landscape Report 2023, state-sponsored cyber attacks on Indian organizations grew by 100% in 2023, compared to the last year. India, accounting for 13.7% of all cyber attacks directed at an Asian country, faced major threats from criminals that are based in China, Pakistan, Russia, and N. Korea. These threat actors actively targeted India through FancyBear, Mission 2025 (China), TA505 (Russia), Transparent Tribe (Pakistan) Turla Group, Stone Panda, and Lazarus Group (North Korea).
So, what’s CYFIRMA?
CYFIRMA is a Singapore-based external threat landscape management (ETLM) platform provider. It combines cyber intelligence detection technologies to protect organizations against digital risks. The company leverages cloud-based artificial intelligence and machine learning techniques to provide predictive warning, personalized, contextual, outside-in, and multi-layered insights against the exploding external cyber landscape. Customers from manufacturing, financial services, retail, industrial products, natural resources, and pharmaceutical industries use CYFIRMA’s AI-based ETLM platform to prepare and recover from cyberattacks.
Here are the key takeaways from CYFIRMA’s latest report on the biggest cybersecurity threats against India and other SE Asian countries.
#1 These are the most targeted nations in the cybersecurity threat landscape.
- India (13.7 attacks)
- USA (9.6%)
- Indonesia (9.5%)
- China (4.5%)
#2 Government agencies have emerged as the number one target for cyber attackers in recent months.
In India, cyberattacks are commonly reported in these industries:
- Healthcare
- Education, and research
- Government
- Military
 #3 Attackers are sparing no one!
#3 Attackers are sparing no one!
SMEs and individual-led startups are equally vulnerable to cyber attacks as any large-sized enterprise. While attackers continue to target the critical infrastructures of reputed companies, they are also carpet-bombing SMEs, especially in the supply chain and manufacturing industries.
Kumar Ritesh, CEO and Founder, Cyfirma said, “It comes as no surprise that India is the most targeted country in the world by threat actors. India’s growing prominence on the world stage and push from Western economies to favor India over other large countries, a young and tech-savvy population with low cybersec maturity has played a key role in hackers coming after critical assets, govt agencies with an intent to breach them and harm India’s strategic interests. While sectors like BFSI, healthcare, and software companies have spent significantly on improving their security posture, there is an urgent need to understand the external threat landscape. We believe that unless you don’t know who to defend against, billions spent in cybersec will not yield expected results.”
#4 Funding comes from ransomware targeting financial organizations.
It’s not hard to guess who makes money from the ransomware attacks. But, did you know that cybercriminals are targeting financial institutions to fuel the dark web and IT terrorism against targeted nations? According to CYFIRMA’s report, different cybercriminal groups collaborate to take down an organization, an industry, or the entire economy. They collaborate by exchanging tools, vulnerabilities, and critical infrastructure to launder money and fund terrorist activities. These include supplying money to finance the proliferation of weapons of mass destruction, according to The Financial Action Task Force (FATF). In 2023, Indian cybersecurity researchers identified many ransomware attacks against the banking and financial sector. As per CYFIRMA, the top data leak activities in India are:
- The Institute of Chartered Accountants of India (July 2023)
- IDFC First Bank (March 2023)
- State Bank of India (July 2023)
- Federal Bank Limited (May 2023)
When it comes to phishing attacks, Hong Kong is the biggest victim, followed by Singapore, Vietnam, and Indonesia. By industry, software is the worst hit, followed by financial, cloud service, and government.
#5 Ransomware operators are focusing on kinetic cyberattacks
CYFIRMA’s latest report points to the growing menace of cyber-kinetic attacks that infiltrate public welfare systems and cripple the entire economy. These could be targeting water treatment plants, energy-producing power units, electricity grids, traffic management systems, healthcare services, and military installations.
How do the attackers become so confident about their targets?
Big cyber attack groups run their operations themselves. They have their IT infrastructure and employ skilled professionals who are at least two steps ahead of their victims. But, state-sponsored funding emboldened the attackers to target a nation based on the existing geo-political relations. In most cases, ransomware attackers emerge from the hostile nations. They could be following a 4-layer approach to cyberattacks. These are:
- Infiltrate into the target organization’s network.
- Exfiltrate and encrypt data.
- Demand ransom and “Name & Shame”.
- Leave behind footprints in the targeted organizations to come back and attack again
#6 Crimeware-as-a-Service
CaaS is toppling established organizations. A majority of victim organizations go out of business within 6 months of a cybercrime. Carpet bombing, dark web encryption, deep fakes, misinformation and fake news, spoofing, and unethical data collection are all part of this CaaS economy. CaaS providers provide custom spyware and exploit kits, along with human intelligence and a skilled workforce, to carry out a large-scale attack. In addition to these spyware suites, attackers also have access to multi-behavioral malware systems to target IT/OT and PII database hijacks.
Here are the five things offered in the CaaS-led attacks:
- SMS spoofing
- Phishing kits
- Money laundering channels
- Custom social engineering templates
- Custom spyware/ malware
- HACKer-fo-hire
#7 List of Top Active Malware Campaigns
CYFIRMA has listed the top malware campaigns that are targeting the Indian industries in 2023. These are:
- Double equal 7: Clop Ransomware, Dridex, and Winnti
- KDX-M7: Winnti
- UNC050: NukeSped RAT, FallChill
These campaigns also targeted organizations based in the US, Canada, South Korea, France, the UK, Germany, Australia, and the UAE.
Suspected threat actors behind these campaigns are:
- Lazarus
- MISSION2025 (APT 41)
- Stone Panda
- Turla Group
- Fancy Bear
- FIN11
- Transparent Tribe (APT36)
In a nutshell
It takes more than just strategic leadership and access to the best cyber intelligence tools to secure the critical infra against the most sophisticated cyberattacks and ransomware scams. It takes a very strong industry-wide policy and collaboration among all the players who can share maximum information about malicious practices, terror IPs, and cyber incident response for every attack. This is only possible by coming together on a common platform. A common platform for interaction on cyber threats and reporting insights such as CIO Influence can prepare stakeholders. CIOs, CISOs, security managers, and senior IT leadership could benefit from the latest news and analysis of the cybersecurity industry to develop custom risk-based tactical and strategic operational views.


