Honeywell has released its 2024 USB Threat Report, which provides new insight into how “silent residency” is an increasing cyber threat for industrial and critical infrastructure facilities. In the report, Honeywell highlighted the growing risk of “living off the land” (“LotL”) attacks. In which adversaries use USB devices to gain access to industrial control systems. This helps hide and observe operations before launching attacks that evade detection and manipulate the target systems.
Also Read: What is Digital Operational Resilience Act?
Targeted cyber-physical attacks are more than zero-day exploits that take advantage of an unknown or unaddressed vulnerability. Instead, they are now also about silent residency – using LotL attacks to wait until there is an opportune moment to turn a system against itself.” – MICHEAL RUIZ, vice president of OT cybersecurity for Honeywell
What USB Threat Report Covers?
The sixth year of the report underscores the severe risk USB-borne malware poses to industrial and critical infrastructure facilities. Key findings indicate that adversaries now have a strong understanding of industrial environments and how they operate. According to the report, most malware detected on USB devices by Honeywell’s Secure Media Exchange could cause an industrial process loss of view or control.
Research Findings Reveal
The 2024 report is based on the Honeywell Global Analysis, Research and Defense (GARD). The report includes the team’s tracking and analysis of aggregated cybersecurity threat data from hundreds of industrial facilities globally over 12 months.
Several of the report’s additional key findings included:
- USB devices continue to be used as an initial attack vector in industrial environments, as 51% of malware is designed to spread via USB, a nearly six-fold increase from 9% in 2019.
- Content-based malware, which maliciously uses existing documents and scripting functions, is on the rise, accounting for 20% of malware.
- Over 13% of all malware blocked specifically leveraged the inherent capabilities of common documents, such as Word, Excel and PDF documents.
- 82% of malware can disrupt industrial operations, resulting in loss of view, loss of control, or system outages in OT environments.
Key Insights from the Report
Increased Sophistication and Targeting of Malware
The report notes continued increased sophistication in attacks and targeting of USB-borne malware. These attacks are part of a broader cyberattack campaign against industrial targets and continue highlighting capabilities that could lead to loss of control or system outages in OT environments.
Prevalence of Content-based Malware
Large proportions of malware analyzed—20 percent—utilized content-based malware, for example, maliciously using common documents and scripting functions. This increase in content-based malware illustrates a trend toward exploiting existing functionalities and system vulnerabilities rather than a willingness to invest in new attack methods.
Expansion of Targets Beyond Windows
Attacks have moved beyond Windows to include Linux and other operating systems commonly used in industrial environments. This is due to an increasing understanding of industrial facilities’ technology landscape.
Prominent ‘Living Off the Land’ Tactics
The report revealed a trend toward ‘Living Off the Land’ tactics, wherein attackers take advantage of inherent abilities in the system to attack against itself. The mechanism is more about manipulating the system’s existing functionalities than deploying malware.
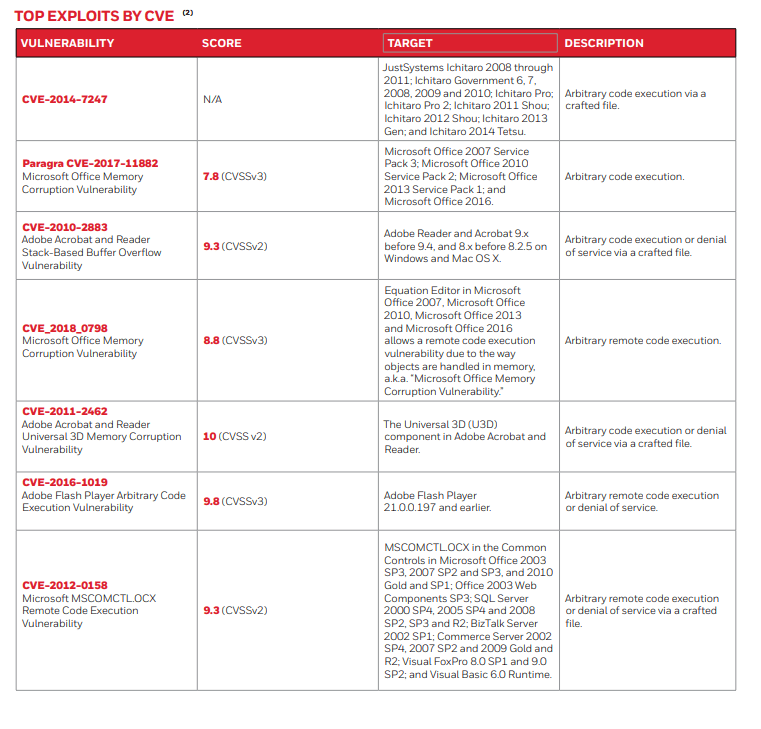
Prevalence of ‘Living off the Land’ CVE Exploits
The analysis revealed several CVEs that the malware exploited. These include CVEs in Microsoft Office, Adobe Acrobat and Reader, and Adobe Flash Player. This suggests a preference for targeting widely used software applications.
Multi-Stage, Disruptive Malware
Most of the malware detected was capable of causing significant disruptions, which is why robust security measures in industrial control systems are critical. These could include significant downtime and operational hazards.
Increase in Overall Malware Frequency
There is a noticeable increase in the frequency of malware detection compared to the previous year, with a 33 percent increase in malware detected and blocked. This is evidence of the growing chasm in securing OT environments from USB-borne threats.
Security Implications and Recommendations
The report stressed the need for strict policies and technical controls over the use of USBs in industries, along with frequent updates in antivirus software, increased monitoring, and incidence response schemes to minimize risks.
Notable Threats and Variants
The new variants of malware, such as Qbot, and the persistent threats posed by ransomware like DarkSide and REvil underline the dynamic nature of the threat landscape. Thus, continuous vigilance and adaptive security strategies are suggested.
Document Management and Control
The report recommended strict document management and control practices, including monitoring for spreading malware through manipulated files, highlighting the emphasis on document-based malware.
Conclusion
Threats targeting industrial/OT environments have grown in sophistication, frequency, and operational risk for six consecutive years. USB-borne malware is a feature of many industrial-targeted cyberattacks, reinforced by ATT&CK techniques analysis and the presence of malware associated with key cyber-physical attack campaigns. Modern malware uses USB standards to bypass network defenses and compromise air-gapped industrial facilities.
Among the leading malicious techniques that overlap with LotL tactics are information gathering, evasion of detection, and direct manipulation of systems. Common exploit techniques include document-based infections and misuse of internal scripting. Strong controls for USB security are a must against the continuing threat from USB. Completing internal operations assessments is recommended, especially concerning document handling and file sharing.
FAQs
1. What does the Honeywell 2024 USB Threat Report stress?
It is focused on the escalating cyber threat to industrial and critical infrastructure facilities, especially that posed by the use of USB devices.
2. What is the “Living Off the Land” (LotL) attacks as per the report?
The LotL attacks demonstrate adversaries allowing USB devices to creep into industrial control systems, silently observing operations before employing undetectable attacks.
3. What are some critical findings on USB-borne malware per the report?
USB-borne malware is extremely dangerous to industrial facilities; over 90% of malware can cause loss of view or control over critical industrial processes.
4. How was the data for the report collected, and what are some critical research findings?
The report is based on the aggregated cybersecurity threat data obtained by Honeywell’s Global Analysis, Research, and Defense (GARD) team from hundreds of industrial facilities worldwide. Key findings include that USB has emerged as the primary initial attack vector, content-based malware has risen, and over 95% of malware can disrupt industrial operations.
5. What recommendations have been provided in the report to mitigate the threats of USB-borne malware?
It stresses strict policies and technical controls for the use of USB, regular updating of antivirus software, and better monitoring and incident response capabilities.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]


