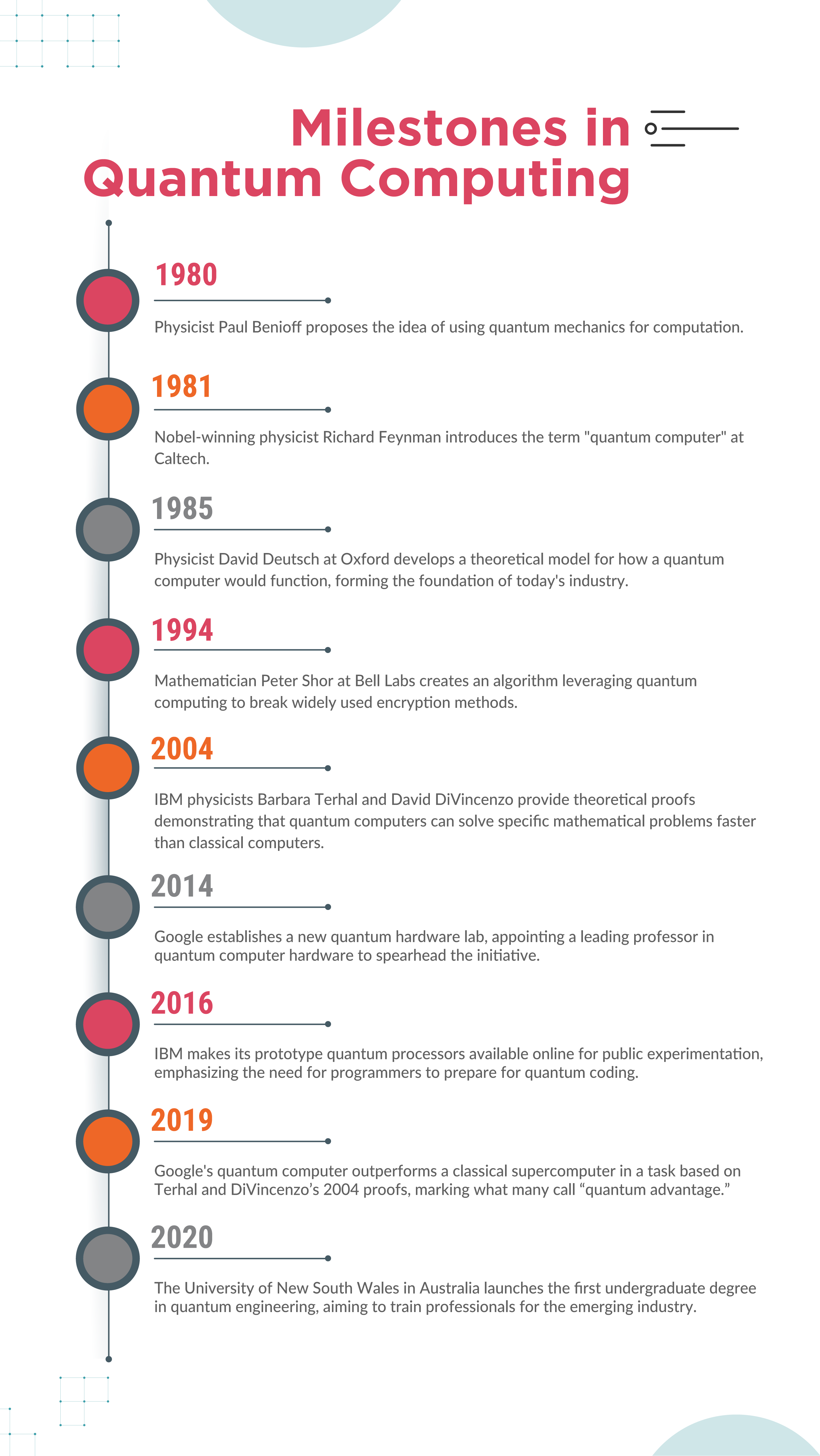
In 1994, mathematician Peter Shor revolutionized computational theory by introducing an algorithm that drastically reduced the time required for prime factorization. This breakthrough significantly impacts the foundation of modern encryption and information security infrastructure, which relies heavily on prime factorization. Seven years later, IBM scientists successfully demonstrated Shor’s algorithm on a quantum machine, marking the first practical application of quantum computing.
Today, quantum computing is on the edge of transforming enterprise IT. CIOs and IT leaders have an unprecedented opportunity to steer their companies toward this technological frontier. Quantum computing promises to redefine how organizations develop and execute business applications and analytics, ushering in a new era of computational power and efficiency.
Quantum Computing Basics
According to IBM – Quantum computing uses specialized technology—including computer hardware and algorithms that take advantage of quantum mechanics—to solve complex problems that classical computers or supercomputers can’t solve or can’t solve quickly enough.
Components of a Quantum Computer
Quantum computers, like classical computers, consist of hardware and software.
Quantum Hardware
Quantum hardware comprises three main components:
- Quantum Data Plane: This is the core of the quantum computer, containing the physical qubits and the necessary structures to hold them in place.
- Control and Measurement Plane: This plane converts digital signals into analog or wave control signals, which perform operations on the qubits in the quantum data plane.
- Control Processor Plane and Host Processor: The control processor plane executes the quantum algorithm or sequence of operations. The host processor interacts with the quantum software and provides digital signals or classical bit sequences to the control and measurement plane.
Quantum Software
Quantum software implements specific quantum algorithms using quantum circuits. A quantum circuit is a computing routine that defines a series of logical quantum operations on the qubits. Developers utilize various software development tools and libraries to code these quantum algorithms.
 Use Cases of Quantum Computing in Enterprise IT
Use Cases of Quantum Computing in Enterprise IT
Quantum computing has the potential to transform various industries. Here are some key use cases:
Machine Learning (ML)
Machine learning involves analyzing vast quantities of data to improve predictions and decisions. Quantum computing research explores the physical limits of information processing, leading to breakthroughs in fundamental physics. These advancements benefit fields such as chemistry, optimization, and molecular simulation. In financial services, quantum computing aids in predicting market movements, while in manufacturing, it enhances operational efficiency.
Optimization
Quantum computing can optimize research and development, supply chains, and production processes. For instance, it can reduce manufacturing costs and cycle times by optimizing path planning in complex processes. In finance, quantum optimization of loan portfolios helps lenders free up capital, lower interest rates, and enhance their offerings.
Simulation
Simulating complex systems, such as drug molecules and materials, requires immense computational effort. Current supercomputers, even with approximation methods, cannot achieve the necessary accuracy. Quantum computation can address these challenging problems in chemistry, enabling precise chemical simulations. For example, Pasqal’s QUBEC software automates the execution of quantum computational tasks, from provisioning computing infrastructure to running classical calculations and error mitigation.
Cybersecurity
The ability of quantum computers to factor large numbers rapidly could render current encryption methods obsolete, prompting the development of quantum-resistant cryptography. Enterprises could use quantum algorithms to enhance security measures, detect anomalies, and protect data more effectively against cyber threats.
Financial Modeling
Quantum computers could improve financial services through more complex simulations, better risk analysis, and faster valuation of financial instruments. Applications include optimizing portfolios, pricing derivatives, and managing risk more effectively, leading to more robust financial strategies and operations.
Drug Discovery and Materials Science
In the pharmaceutical and materials industries, quantum computing can simulate molecular and chemical interactions at an unprecedented scale. This could accelerate the discovery of new materials and d****, significantly reducing costs and time to market for new products.
Database Searching and Management
Quantum algorithms, like Grover’s algorithm, can potentially speed up unstructured database searches, improving the efficiency of querying, sorting, and managing large datasets. This can enhance the performance of enterprise databases handling complex queries over large scales.
Quantum Cloud Services
As quantum technology matures, cloud-based quantum computing services could become a part of enterprise IT infrastructure, allowing businesses to access quantum processing power on demand. This would enable smaller enterprises without the resources to own quantum computers to leverage quantum computing capabilities.
Also Read: Decoding the Impact of Quantum computing on Data Security: What CIOs Need to Know
Top Quantum Computing Challenges for Enterprises
Despite significant advancements, quantum computing still faces several challenges that must be addressed to unlock its full potential. However, these challenges also present opportunities for the computing, scientific, and business communities.
Challenges:
- Availability of Qubits: There is a shortage of high-quality, error-corrected qubits. Addressing this requires effective quantum memory management, which involves matching qubits with suitable tasks.
- Limited Connectivity: Long-range entanglement remains infeasible due to limited connectivity in current devices. Ideally, entanglement should allow the manipulation of many qubits for a single operation, but this is difficult with existing technology.
- Circuit-Level Fault Tolerance: While progress has been made in error correction for fault-tolerant qubits, integrating them into universal computing systems remains a challenge.
- Verification and Debugging: Verifying and debugging quantum computations, especially in larger systems, is challenging due to the effects of quantum measurement.
The Potential of Enterprise Quantum Computing
CIOs planning for quantum computing should focus on the technology’s most useful characteristics. These features can help identify business-specific priorities, foster innovation, and develop the company’s talent pipeline.
Suseel Menon, practice director at Everest Group, highlights three essential characteristics of quantum computing:
- Superposition: A qubit can represent and process multiple possibilities simultaneously. This capability can significantly enhance data processing, as qubits can handle multiple states at once.
- Factorization: Quantum computers excel at factorization problems, which are crucial for cryptography, data compression, and control systems.
- Optimization: Quantum computers effectively solve optimization problems by identifying the most efficient options or actions. Quantum annealing, a method used in optimization, already shows promise for specific business applications.
Top Quantum Computing Companies
IBM
Microsoft
Quantinuum
Atos
Also Read: Impact of Quantum Computing on Finance Sector
Addressing Misconceptions about Quantum Computing
Case Study: BT and Toshiba’s Quantum-Secured Network
BT, a major telecommunications company, in partnership with Toshiba, launched a quantum-secured metro network in London, UK. This initiative represents a practical application of quantum technology aimed at enhancing cybersecurity.
Objective: The objective was to implement Quantum Key Distribution (QKD) to secure data transmission across a metropolitan area network. This technology ensures that any attempt at intercepting the communication would be detectable as it alters the quantum state of the data.
Implementation: The quantum-secured network links major data centers and corporate offices in London, providing ultra-secure communication channels resistant to all forms of cyber intrusion, including those potentially using quantum computers in the future.
Results: The deployment was successful, providing a proof-of-concept for the viability of quantum communications in commercial telecommunications services. It highlighted the potential for broader application in securing sensitive data transfers in various industries.
Innovation and Impact: The project stands as a significant milestone in practical quantum application, paving the way for future advancements in secure communications technology. It positions BT and Toshiba at the forefront of the adoption of quantum technologies in cybersecurity.
Final Thoughts
Enterprises are now deciding whether to wait or start to shift towards quantum. This is rather an investment that has to be permanently reconsidered with the changes in the ecosystem. The quantum hardware is the quantum computer itself, whose middleware compiles classical programs to the quantum format and aids in the removal of noise and errors. In the top layer, the company’s application stack includes libraries and tools for new algorithm optimization.
All organizations should monitor these developments even if they are not investing immediately. At the same time, organizations should be encouraged to support the development of their own talent through quantum-computing programs at local universities and sponsor the next generation going into advanced quantum-computing degrees.
It is critical to prepare for this quantum-secure world, connecting with the dawn of a new computing era, human in its revolutionary character. Making our digital infrastructure resilient to absorb this game-changing wave in quantum computing will only be possible through risk identification, workforce education, system assessment, and transition to quantum-resistant technologies.
[To share your insights with us as part of editorial or sponsored content, please write to psen@itechseries.com]


