First-of-its-kind guidance arms enterprises with the technical requirements, integrations and workflows needed to reduce Insider Risk amid the shift to a hybrid workforce
Code42, the Insider Risk Management leader, published guidance for enterprises with remote and hybrid workforces to build an effective Insider Risk Management (IRM) program. The first of its kind, Code42’s Insider Risk Management framework provides a practical guide for deterring Insider Risk without disrupting legitimate business. It includes a technical roadmap for enterprises using myriad collaboration tools that are rethinking the functionalities and capabilities they need to effectively improve their organization’s risk posture when it comes to data leaks, loss and theft from insiders.
Recommended ITech News: IDrive Online Backup Releases IDrive Compute – a VPS Hosting and Edge Computing Service for Developers & Enterprises
“Remote and hybrid work demand technologies that make it easy to collaborate and move files. Security teams’ traditional response – to block data movement – runs counter to what leaders and employees demand”
Insider Risk, not to be confused with insider threat, is any data exposure event – security, compliance or competitive in nature – that jeopardizes the financial, reputational or operational well-being of a company and its employees, customers and partners. Today, organizations need a new paradigm for data security and a better approach to mitigate Insider Risk. Gartner has termed this Insider Risk Management. Code42’s new IRM framework comes on the heels of the company’s designation as a Representative Vendor in the December 2020 Gartner “Market Guide for Insider Risk Management Solutions” report.
“Remote and hybrid work demand technologies that make it easy to collaborate and move files. Security teams’ traditional response – to block data movement – runs counter to what leaders and employees demand,” said Joe Payne, president and CEO, Code42. “To break the deadlock, organizations need to look to Insider Risk Management. It wraps a layer of security around collaboration tech while allowing employees to share files without being disrupted. Drawing on our deep IRM experience, we developed this IRM framework to guide companies as they secure their collaborative work models and trade secrets.”
Recommended ITech News: NEXCOM to Develop Advanced Ethernet Solutions Powered by NVIDIA
About Code42 Insider Risk Management
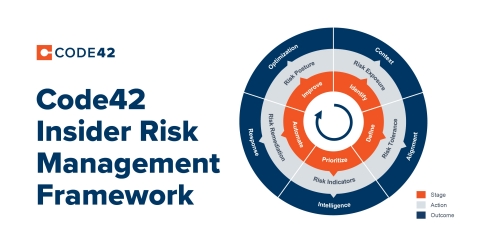
The Code42 IRM solution offers a new framework to protect data and stands in stark contrast to traditional data loss prevention (DLP) approaches, which are rooted in identify, classify and block tenets known for disrupting employees’ legitimate work. When followed, the Code42 IRM framework enables security teams to comply with data use policies, foster a more risk-aware and collaborative culture and speed time to value of their security investments. The five core stages of the Code42 IRM framework include fundamental technical requirements:
- Identify: It is crucial to have IRM technology in place that can monitor all files, vectors and users in its environment regardless of classification or privileges.
- Define: Using IRM technology, security teams must define trusted versus untrusted activities, scenarios and risk severity to align on organization-wide Insider Risk tolerance and right-sized response.
- Prioritize: It is crucial that IRM technology can triangulate individual aspects of file, vector and user context to surface leading indicators of risk whether that be source code exfiltration, suspicious file type mismatches, syncs to personal cloud storage or departing employees.
- Automate: Automate a combination of human and technical actions to accelerate Insider Risk response. Because not all Insider Risk is malicious, response actions should be right-sized to the risk severity and situational context.
- Improve: Continually measure and optimize the organization’s overall Insider Risk posture and maturity by improving technology implementation and processes over time.
Recommended ITech News: European Cloud Storage Firm pCloud Launches Data Backup Service
Code42’s Incydr data risk detection and response product is the purpose-built solution for Insider Risk Management. Incydr surfaces the top indicators of Insider Risk and accelerates an organization’s ability to detect and respond to data exposure and exfiltration events. Incydr is cloud-native and built to directly address the gaps in conventional data security solutions. Organizations looking for detailed security intelligence about on- and off-network file movements can use Incydr to help identify and act on the greatest indicators of risk to their data.
- Read this case study to learn how Snowflake leveraged Incydr as part of their IRM program.
Critical Resources About the Code42 Insider Risk Management Framework
There is a library of resources about the Code42 IRM framework. Security architects and security developers can:
- Read our book, Inside Jobs: Why Insider Risk is the Biggest Cyber Threat you can’t Ignore.
- Download the complementary technical white paper: An Overview of Technical Requirements and Integrations for an Insider Risk Management Strategy.
- Take a spin through an interactive demo of Incydr in our free sandbox environment.
- Watch the on-demand event: Why Stolen IP, Departing Employees, and Remote Work Demand a New Approach to Data Protection.
- Read the IRM executive summary: Insider Risk Management – A Better Way to Prevent Data Leaks.
- Learn how to build integrations and scripts using the Code42 Developer Portal.
Recommended ITech News: ASRY Modernisation Continues with Infor Cloud-Based Digital Transformation Platform


