Digital transformation in the financial sector and technology dependency to deliver its financial services make the sector more vulnerable to cyberattacks. IBM’s Cost of Data Breach Report 2023 states that the financial industry ranks second in the global cyber incident damage statistics. Financial organizations incurred losses of approximately $5.9 million per cyber incident. This increase in cyberattacks and cyber incidents concerning information and communication technology (ICT) and the growth in digitalization led to the establishment of the Digital Operational Resilience Act (DORA).
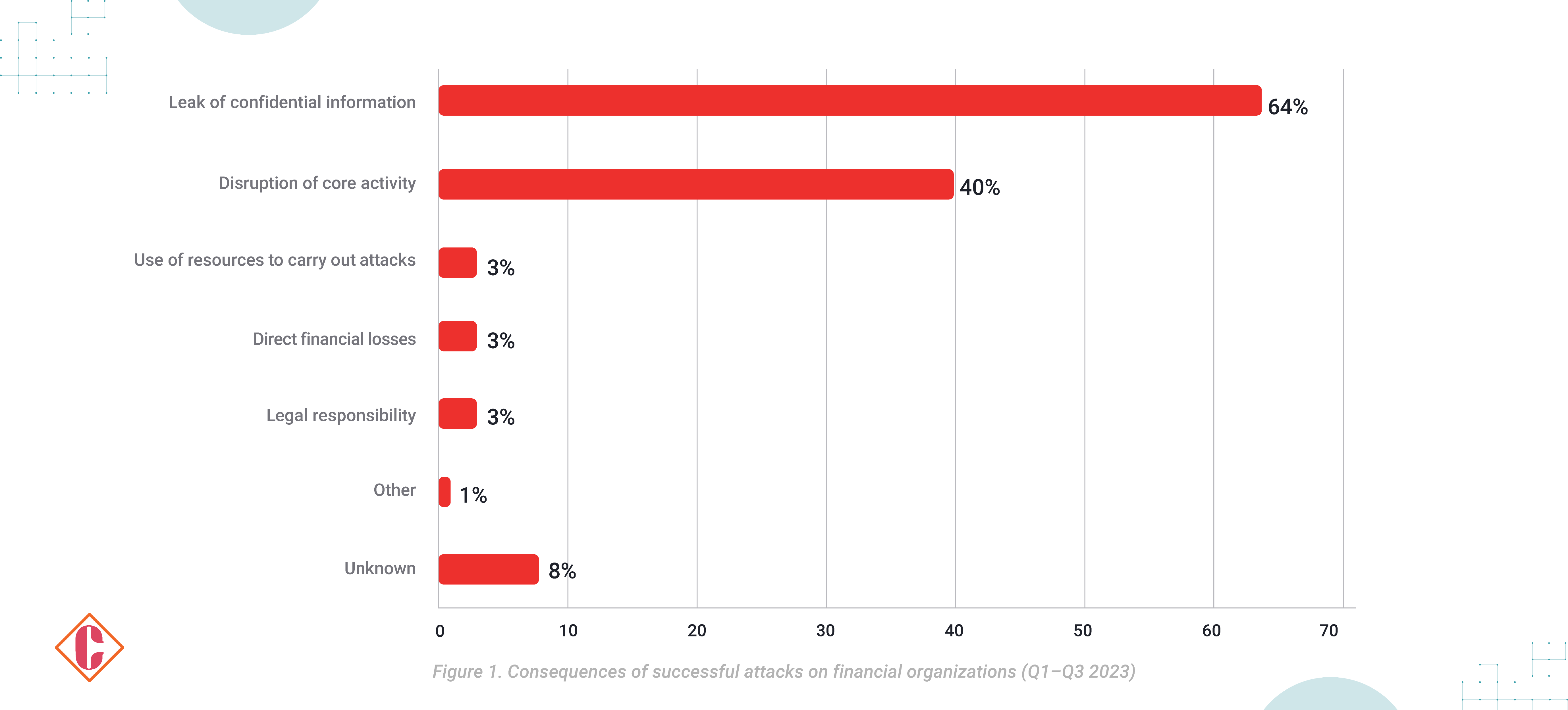
According to Positive Technologies’ research findings, successful cyberattacks in the financial sector are growing Year over Year. In the third quarter of 2023, cyber incidents doubled compared to the previous year. The consequences of attacks include 64% data leaks and 40% disruption of services. Attacks on well-established and protected financial organizations with the goal of malware activities have been reduced by implementing streamlined ransomware attacks and large customer data leaks.
 What is DORA?
What is DORA?
DORA stands for the Digital Operational Resilience Act. It is an EU regulation that entered into force on 16 January 2023. This regulation determines technical standards and develops a risk management framework for the financial sector of the European Union (EU) and its third-party service providers.
The purpose of DORA regulation is to strengthen IT security for financial organizations. It includes investment firms, banks and insurance companies. DORA will allow European financial sector companies to stay resilient when there are any events or occurrences of severe operational disruptions.
As an EU regulation, financial services institutions within its scope must comply with it by 17 January 2025, regardless of whether individual member states pass laws to enforce it.
DORA harmonizes the rules governing the financial sector’s operational resilience. It applies to twenty different types of financial organizations and ICT third-party service providers.
Five Pillars of DORA
- Resilience testing demonstrates the software’s recovery ability after momentary outages and other stressors.
- Risk management: To identify, analyze, evaluate and treat losses.
- Third-party Risk management: To focus on identifying and reducing risks relating to the use of third parties
- Incident management: To respond to an unplanned event.
- Information sharing: To share information possessed by one entity with another entity.
What are the Key Areas Addressed by the DORA Regulation?
- ICT risk management: Fundamentals and requirements on ICT risk management framework.
- ICT third-party risk management: Monitoring third-party risk providers for key contractual provisions.
- Digital operational resilience testing: Basic and advanced testing.
- ICT-related incidents: Reporting of major ICT-related incidents to competent authorities.
- Information sharing: Exchange of information and intelligence on cyber threats.
- Oversight of critical third-party providers: Oversight framework for critical ICT third-party providers.
What is the purpose of the DORA Regulation for the Financial Sector?
DORA has been developed with two main objectives: addressing comprehensive risk management in the financial service sector and harmonizing the ICT risk management regulations for EU member states.
Before DORA, risk management regulations for financial institutions in the EU primarily focused on ensuring that firms had enough capital to cover operational risks. Before a unified approach, European Union regulators issued various ICT and security risk management guidelines. However, these guidelines lacked consistency. They applied unevenly to different financial institutions and often focused on broad principles instead of providing clear technical standards. This resulted in a fragmented regulatory landscape across EU member states, creating challenges for financial entities trying to comply.
Risk management for financial institutions initially focused on having enough capital to manage operational risks. The ICT guidelines released on security risk management did not apply to all financial institutions equally. Those guidelines relied on specific technical standards, and in their absence, the EU member states issued their requirements. This created difficulty for financial entities to navigate. Then, DORA was established to provide a universal framework for managing and overcoming ICT risks. DORA seeks to remove the gaps and conflicts by harmonizing risk management rules across the EU.
Why is DORA Regulation Needed for the Financial Sector?
The Digital Operational Resilience Act establishes comprehensive rules for managing cyber risks in the European financial industry. Here is a breakdown of its essential requirements:
Stronger Leadership and Governance
- DORA places the responsibility for ICT management squarely on the shoulders of an entity’s governing body. Board members and senior leadership are accountable for defining risk management strategies, actively implementing them, and staying informed about cyber threats.
Comprehensive Risk Management Framework
- Covered entities must create a detailed ICT risk management framework. This includes mapping critical systems and assets, identifying dependencies, and conducting ongoing risk assessments.
- Business impact analyses are crucial to understand how disruptions could affect operations. This information informs risk tolerance levels and ICT infrastructure design.
- Implementing robust cybersecurity measures, such as access controls, patch management, and advanced tools like extended detection and response (XDR) and security orchestration, automation, and response (SOAR) is essential.
- Business continuity and disaster recovery plans are mandatory to address various cyber risk scenarios, including data recovery, system restoration, and communication protocols.
Enhanced Incident Response and Reporting
- DORA mandates systems for monitoring, logging, classifying, and reporting ICT incidents. Reporting requirements depend on the severity of the incident, potentially involving regulators, clients, and partners.
- Three reports are required for critical incidents: initial notification, progress updates, and a final root cause analysis.
- Specific rules for incident classification, reporting thresholds, and timelines are still under development.
- Standardization efforts are underway for a central reporting hub and standard report templates.
Regular Testing for Resilience
- Entities must regularly test their ICT systems to assess their defenses and uncover vulnerabilities. Test results and remediation plans will be reported to and validated by relevant authorities.
- Basic vulnerability assessments and scenario-based testing are required annually. Critical financial institutions will undergo additional penetration testing every three years, with participation from their key ICT providers. Technical standards for penetration testing are expected to align with the TIBER-EU framework.
Third-Party Risk Management: A Shared Responsibility
- DORA uniquely extends its reach beyond financial entities to its ICT service providers.
- Financial institutions must actively manage third-party risk. Outsourcing critical functions requires robust contracts covering exit strategies, audits, performance targets for security, and more. Entities cannot contract with non-compliant providers. The authorities hold the power to suspend or terminate non-compliant contracts. Standardized contractual clauses are under consideration to simplify compliance.
- Mapping third-party ICT dependencies and avoiding overreliance on single providers are crucial aspects of third-party risk management.
- Critical ICT service providers will face direct oversight from European Supervisory Authorities (ESAs). The criteria for designating essential providers are still being defined. Lead overseers will enforce DORA requirements and even prevent non-compliant providers from entering into contracts with financial institutions or other ICT service providers.
Information Sharing: Learning from Each Other
DORA encourages financial institutions to participate in voluntary threat intelligence-sharing arrangements to learn from internal and external incidents. However, data protection regulations like GDPR must be observed when sharing information.
DDORA’sNon-compliance Penalties
DORA extends the applicability of existing regulatory fines. It prevents late actions through multi-faceted enforcement:
- Significant Financial Fine: Companies are liable to pay a penalty of up to 1% of their average daily worldwide turnover for the previous year daily—until they comply with the mandates for six months. This introduces a significant disincentive for late actions.
- Criminal Liability and Criminal Responsibility: DORA increases the heat with the threat of imprisonment and personal fines for officers in charge of noncompliance.
- Reputation Impact: Combined with the financial loss from service disruption and the ongoing damage to reputation that comes with security incidents, the potential results from DORA are nothing short of catastrophic. DORA aids organizations in avoiding those disastrous outcomes by delivering robust data and cyber operating resilience.
Sustained Active Enforcement by National Authorities
The EU member states identify “competent authorities” who will actively ensure compliance. Competent authorities can and will:
- Order Specific Security Measures: Competent authorities may order entities to implement specific security measures to remediate vulnerabilities.
- Order remediation of gaps: Competent authorities may order remediation of identified security gaps or vulnerabilities.
DORA Extends to Third-Party Service Providers
One key difference between DORA and all other regulations is that it applies not only to financial institutions but also to the third parties that provide their services: hyper scalers, cloud service providers, hosted data centers, etc. All these entities are obliged to adhere to DORA requirements. This approach of the whole financial sector ensures that cyber resilience runs end to end.
Conclusion
DDORA’s comprehensive approach, with active enforcement mechanisms for financial institutions and their critical ICT providers, promises to enhance cybersecurity across the entire EU financial sector significantly. It proactively requests security measures and enforces remediation and penalties for noncompliance.
DORA compels financial entities to establish a well-defined incident management process. This structure empowers responders to manage their work and thoroughly document incidents effectively. Organizations already adhering to ITIL methodologies have many of the necessary processes and procedures for incident management and reporting.
Additionally, DORA introduces a critical distinction. Unlike traditional business continuity and disaster recovery plans, cyber incidents demand a more in-depth approach. Extensive investigation and threat mitigation become essential before systems can be safely restored.
FAQs
1. What are the objectives of the DORA regulation?
The main objectives of DORA are to enhance comprehensive risk management in the financial sector and harmonize ICT risk management regulations across EU member states.
2. How does DORA improve cybersecurity in the financial sector?
DORA mandates more decisive leadership and governance, comprehensive risk management frameworks, enhanced incident response and reporting, regular resilience testing, and shared responsibility for third-party risk management.
3. What are the consequences of noncompliance with DORA?
Noncompliance with DORA can result in significant financial fines, criminal liability for officers, reputation damage, and active enforcement measures by national authorities.
4. How does DORA extend to third-party service providers?
DORA applies to financial institutions and third-party service providers, ensuring end-to-end cybersecurity resilience across the financial sector.
5. What distinguishes DORA from traditional cybersecurity regulations?
DORA goes beyond traditional cybersecurity regulations by focusing on comprehensive risk management, incident management, and response explicitly tailored to cyber incidents in the financial sector.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]


