Growing digitalization has led to an increase in the need for digital security and privacy. With this comes the requirement to have secured operating systems. Operating System (OS) security protects sensitive data and maintains personal privacy. As awareness grows regarding the associated privacy risks of conventional systems, like those provided by Windows and ChromeOS, there tends to be an increasing inclination toward alternative systems emphasizing security, privacy, and anonymity.
This comprehensive approach provides a complete understanding that can help you make the right decision regarding the secure OS that would comply with your requirements. As cyber-attacks continue to rise and data breaches become regular, one question follows: What OS provides the most protection? But it’s not as straightforward as one might be led to believe.
Macs are often considered virus-free, and Windows systems are considered less safe than any other OS on the market. However, ChromeOS was intentionally built with security in mind and has often been the safe choice. That’s all good, except its user base is only relatively small.
The bottom line is that no OS is completely immune. With the constantly changing landscape of cyber threats, today’s secure OS can be vulnerable tomorrow. It’s, therefore, very reasonable to spend a little money on affordable antivirus options such as Surfshark One, no matter what one’s OS may be.
In this article, you’ll explore the operating systems, gaining valuable insights into their privacy features and security measures. It will give an overview and review criteria, encompassing factors such as ease of use, compatibility, and performance. Let’s understand each OS’s emphasis on privacy, security, and anonymity, scrutinizing their key security features, practical applications, and strengths and weaknesses.
Privacy, Anonymity, and Security
Three fundamental principles apply when defining secure operating systems: privacy, anonymity, and security. These principles, applied correctly, provide a working background for choosing an operating system.
Privacy ensures that all your activities are hidden from evil eyes, but your identity is known. It entails protecting sensitive information, such as the data associated with you and information that you send and receive, from a breach or leak.
Imagine sending a sealed letter in an envelope with your name and the contents being sealed. Your contents are hidden, but you are known.
On the other hand, Anonymity ensures that the identity is hidden, but the actions are known. Protecting against targeted attacks due to online behavior and maintaining freedom of expression online is necessary.
Anonymity is likened to sending a postcard without a return address. Your message is seen, but your identity is not known.
Security is the ability of assets, such as privacy and anonymity, to withstand adversaries. It involves protection using a Virtual Private Network, encryption, and regular software updates. Security measures are designed to consider various threats and adversaries, provided that technology, practices, and protocols are involved.
Imagine sending letters that are locked. Your post will be safe, and these changes will keep your privacy and anonymity from theft or tampering.
While privacy, anonymity, and security differ, they are interrelated and help protect your digital identity. The elements must be balanced properly as perfect privacy, security, and anonymity are impossible simultaneously and could be for individuals based on one’s requirements and conditions.
What is an Operating System?
An Operating System is a major intermediary between the user of a computer and the hardware constituent of a computer. It is a software platform that performs primary activities like file management, memory management, process coordination, and handling of inputs and outputs, as well as peripheral devices like disk drives and printers.
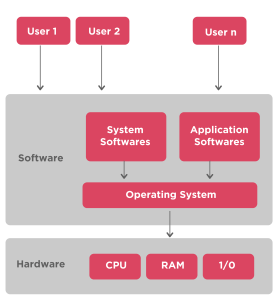 An operating system is software that ensures interaction between applications and computer hardware. The kernel, which contains the core functionalities, is the main part of an operating system.
An operating system is software that ensures interaction between applications and computer hardware. The kernel, which contains the core functionalities, is the main part of an operating system.
An operating system’s main functions include providing the means for interaction between applications and hardware and managing a system’s hardware and software resources.
Operating Systems are everywhere and can be found on almost every type of device, including but not limited to mobile phones, personal computers, mainframe computers, automobiles, televisions, toys, and many others.
Types of Operating Systems
Operating systems have evolved since the earliest computer generations, adapting to the changing technological landscape. This chapter explores several essential types of operating systems commonly used today.
1. Batch Operating System:
In a batch operating system, users don’t directly interact with the computer. Instead, they prepare their jobs offline, typically using punch cards, and submit them to a computer operator. Similar tasks are grouped together to expedite processing. The operator organizes programs with similar requirements into batches.
Challenges with Batch Systems:
- Limited user interaction with jobs.
- CPU idle time due to slower mechanical I/O device speeds.
- Difficulty in providing desired priority levels.
2. Time-Sharing Operating Systems:
Time-sharing allows multiple users at various terminals to simultaneously utilize a single computer. This technique, an extension of multiprogramming, enables the processor’s time to be shared among users. Unlike multiprogrammed batch systems, where the focus is on maximizing processor use, time-sharing systems prioritize minimizing response time.
Advantages of Time-Sharing Operating Systems:
- Quick response times.
- Avoidance of software duplication.
- Reduction of CPU idle time.
Disadvantages of Time-Sharing Operating Systems:
- Reliability concerns.
- Security and integrity issues regarding user programs and data.
- Data communication challenges.
3. Distributed Operating System:
Distributed systems utilize multiple central processors to handle various real-time applications and users’ needs. Processing tasks are distributed among processors, which communicate via communication lines like high-speed buses or telephone lines. These systems, also known as loosely coupled systems, offer advantages such as resource sharing, faster data exchange, and enhanced service provision.
Advantages of Distributed Systems:
- Resource sharing across multiple sites.
- Enhanced data exchange through electronic mail.
- Continuity of operations if one site fails.
- Improved customer service and reduced load on host computers.
4. Network Operating System:
A Network Operating System operates on a server, facilitating data, user, group, security, and application management. It enables shared file and printer access among multiple computers in a network, fostering collaboration and efficiency.
Advantages of Network Operating Systems:
- Stable centralized servers.
- Server-managed security.
- Seamless integration of new technologies.
- Remote server access from different locations and system types.
Disadvantages of Network Operating Systems:
- High acquisition and operational costs.
- Dependency on a central server for operations.
- Ongoing maintenance and updates.
5. Real-Time Operating System:
Real-time systems process and respond to inputs with minimal delay, controlling their environments effectively. They are utilized in scenarios requiring precise time constraints, such as scientific experiments, medical imaging, industrial control, and air traffic control.
Types of Real-Time Operating Systems:
- Hard Real-Time Systems: Ensure critical tasks are completed on time, often with limited or no secondary storage.
- Soft Real-Time Systems: Provide flexibility, with critical tasks taking priority over others but less strict timing constraints.
Real-time operating systems play critical roles in various applications, from industrial control to multimedia and scientific projects.
Top 4 Operating Systems
ChromeOS – The Secure Option
- Google’s ChromeOS stands out as an ultra-secure operating system that in many ways surpasses Windows, macOS, and Linux in terms of security.
- Security-wise, ChromeOS is based on a Linux kernel deliberately built and fine-tuned to be secure. Automated updates ensure that users are always updated with the latest security patches.
- It uses sandboxing, where a site and an app are isolated into separate processes to avoid the spread of malware. Even if one of the user’s website accesses is malicious, the damage is confined only to that sandbox.
- Its architecture, such as read-only operation and verified boot mechanisms, further protects ChromeOS against ransomware and malicious modification attempts.
- Moreover, ChromeOS comes with specific anti-phishing measures, which help prevent such attacks from breaking through.
Linux – A Historical Fortress
It has long been touted that Linux is one of the most secure operating systems. Unlike Windows, Linux denies root-level access, which improves its security by limiting the attack surface.
Linux is open-source, and a community of developers has worked hard to identify and bug-fix security issues in its codebase. The open-source code and distribution model of Linux provide variants such as Qubes OS.
Although its popularity has surged recently, Linux’s smaller user base has traditionally scared away large-scale malware development. However, recent trends have shown that the threat environment of Linux systems is growing.
macOS – Security with Apple’s Seal
MacOS boasts strong security features, dispelling the myth of invulnerability associated with Apple products. Integration on such a tight level between hardware and software allows Apple to provide users with seamless security updates and strong hardware barriers.
- Gatekeeper and XProtect are just some of MacOS’s security tools. They inspect app downloads and scan documents for malicious code, respectively.
- Although macOS isn’t, to date, unscathed by malware, its security features do provide strong protection against cyber threats. In recent years, a spurt of Mac-specific malware has been observed, though such malware is still smaller in
- Windows, the most popular operating system, was and still is the first to be scrutinized. The multi-user system was generally vulnerable and gave instant access to system-level privileges upon login.
Whereas Linux and macOS enjoy the open-source transparency by which it was developed, Windows leans upon Microsoft’s engineering prowess to discover and patch vulnerabilities.
Windows—A Widely Targeted Frontier
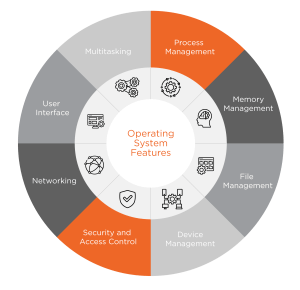
Operating System Features
 Process Management
Process Management
- Functionality: It manages program execution by handling processes, including scheduling, creation, termination, and synchronization.
- Details: It uses scheduling algorithms to determine which CPU should access it first and resolves deadlocks brought about by resource conflict.
Memory Management
- Functionality: It allocates memory space to processes to isolate programs and thus properly use them.
- Details: It uses paging and segmentation techniques to efficiently use memory and provides virtual memory, whereby the increased RAM can be used by extending the disk.
File Management
- Functionality: Data storage, retrieval, and organization on storage devices, as well as the management of file systems, directories, and access permissions.
- Details: It implements file systems like NTFS and ext4 and facilitates operations such as file reading and writing, as well as the ability to create and delete files.
Device Management
- Functionality: It controls the input/output devices such as keyboards, disk drives, printers, and monitors using drivers.
- Details: It interacts with the hardware through device-specific drivers to such an extent as to facilitate data transfer to printers and disk operations.
Security and Access Control
- Functionality: Secure access to system resources is provided by implementing security protocols and user authentication methods.
- Details: It manages user permissions and uses encryption tools to ensure that data is protected and cannot be accessed by unauthorized users.
Networking
- Functionality: Data exchange over network connections is controlled, with routing, connectivity, and data integrity across networks being handled.
- Details: It uses network protocols such as TCP/IP to facilitate communication between computers and devices.
User Interface
- Functionality: Provision of interfaces that allow for user interaction, including graphical and command-line interfaces.
- Details: GUIs provide visual interaction, while CLI allows for text-based command execution, allowing users to do things.
Multitasking
- Functionality: Concurrent execution of software processes on a single processor through the process of time-sharing of CPU.
- Details: It creates the illusion that a process is running all at once.
Benefits of Operating Systems
- Proper and effective use of computer hardware
- Multiple applications can be run simultaneously
- Easy management of files and folders
- Provides easy access for the user
- Strong security
- Efficient management of the system’s resources
- Print management made easy
- A platform for software development
Drawbacks of Operating Systems
- Complex and difficult to handle
- Costly in purchasing and maintenance
- Arenas for virus and other attackers who are malicious.
Safe OS vs Antivirus: Make the Right Choice
As cybersecurity evolves, “normally” operating systems are developed with a different attitude toward security. When choosing an operating system, having a great word about security is important. Not only that but there will also be gaming applications that do not need to win every fight with the operating system or old habits related to vision and experience.
Gaming, therefore, is a domain where Windows-based systems offer better compatibility and rendering compared to Chromebooks, which often have no extensive local storage availability. Linux doesn’t seem to be the best choice for the average user because of the minimalistic user interface and the complexity.
While no operating system is by default unsafe, some are widely appreciated for their security-first philosophy. To make your operating system safer, it’s a good idea to install a robust antivirus solution. Even if the major antivirus makers like BitDefender or Norton are among the best, there are many alternatives out there, like Surfshark Antivirus, that should be lightweight yet effective for scanning and analyzing files and downloads.
Since Windows malware is a widely used malware category, installing Surfshark One or similar antivirus software is more than a must among Windows PC users. Nevertheless, it should complement the native security, which can be switched on or off whenever required.
FAQs
1. What makes an operating system secure?
A secure operating system prioritizes protecting user data, implementing robust security measures, and offering privacy and anonymity features. It often includes mechanisms such as automatic updates, sandboxing, and encryption to thwart cyber threats.
2. Are there any operating systems considered virus-free?
While certain operating systems like macOS are less prone to viruses due to their architecture and security features, no OS is entirely immune to malware. It’s crucial to implement additional security measures like antivirus software to enhance protection.
3. Which operating system is the most secure?
The security of an operating system depends on various factors, including its design, updates, and user practices. ChromeOS, macOS, and Linux are often lauded for their security features, but each has its strengths and weaknesses. Users should assess their specific security needs before choosing an OS.
4. Do I need antivirus software for a secure operating system?
Despite using a secure operating system, it’s advisable to install antivirus software as an additional layer of defense against malware. Antivirus programs can detect and remove threats that may evade the OS’s built-in security measures.
5. How can I enhance the security of my operating system?
To bolster OS security, users should regularly update their systems, enable built-in security features, use strong passwords, avoid downloading from untrusted sources, and implement firewall protection. Additionally, practicing safe browsing habits and staying vigilant against phishing attempts can further mitigate security risks.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]



 Process Management
Process Management