Software applications today are complex and vulnerable to cyber threats and security issues. These issues include bad code, misconfigurations, and authorization failure. Companies and development teams must consider the security implications of overcoming this difficulty and vulnerability.
SecDevOps is a software development method that helps overcome security vulnerabilities in development operations. It depends on automation and best practices that allow the software development operations to move rapidly. This article will cover the importance of SecDevOps and how it works.
What is SecDevOps?
SecDevOps is a security-focused approach to software development aimed at moving security to the left in a project’s life cycle. Other methods that intermittently test security are replaced by SecDevOps, which places risk prevention first and leads to more resilient programs and smoother production pipelines.
Rather than delegate the burden of security to one team, SecDevOps works toward making each member—from senior developers to new hires—a member with a shared responsibility. Each learns the basic skills of a security analyst, ensuring that each one follows security best practices, understands security principles, and uses modern tools and automation to maintain efficiency. This avoids wasting time fixing vulnerabilities that were missed earlier in the process.
While emphasizing security might seem like a compromise, the benefits are enormous. The term SecDevOps is not a compromise but a response to modern security challenges. It works based on two foundations: security as code and infrastructure as code.
Also Read: Top 10 DevOps Automation Tools for Software Developers in 2024
Benefits of SecDevOps
In SecDevOps, the security team leads the way in developing fundamental policies from the beginning. These policies include coding standards, testing policies, static and dynamic analysis guidelines, and rules against malpractices like bad APIs, lousy encryption, etc. The security team would need to be human-involved in additional policies, such as changes in authentication, the authorization model, or any other critical security area.
The team qualitatively enhances their experience in this area as security is embedded into development. This, in turn, reduces vulnerabilities in the pipeline by the end. In case of still vulnerabilities, investigations and updating the process become easy.
Root cause analysis applies further improvements to the security policies and guidelines. In other words, better results are achieved with every cycle due to iterative improvements that reduce late-stage escalations.
SecDevOps offers the following benefits:
- More Quickness and Velocity for the Security Teams: Security teams carry out their tasks with better productivity and speed.
- Rapid Responses to Change and Demands: The methodology allows quick responses to changing demands and situations.
- Improved Cooperation and Communication: SecDevOps helps to create better collaboration and communication in different departments.
- More Opportunities for Automation: The methodology provides automation for builds, quality assurance, and security testing.
- Detection of Code Vulnerabilities Earlier: When vulnerabilities are detected in the code earlier, risks are low.
- Frees Your Team Members from Routine Work: Eliminating routine activities allows team members to focus on high-value activities.
Also Read: CIO Interview with Joey Fitts, Vice President, Analytics Product Strategy at Oracle
Functionality of SecDevOps
Security considerations have been migrated to the prior stages of development in SecDevOps. Unlike normal models, where security is always an afterthought, SecDevOps integrates security thinking right at the beginning of the planning stage.
Developers are the primary agents of imbuing security into every aspect of the development process.
Developers tend to use threat models, and a test-driven development environment is maintained with security test cases. Continuous integration and an automated security testing approach become part of the process.
Understanding the application’s functionality is at the forefront of identifying vulnerabilities. This is often highlighted through the application of threat models throughout the development process.
Let us take a look at the normal SecDevOps workflow to understand how it works:
Version Control Management System:
Developers use a version control management system to track changes in software development projects, enabling collaboration.
- Code Creation and Commit: Developers develop code within the system and commit code changes.
- Code Analysis: Another developer retrieves code for analysis and specifies his focus on security defects or bugs in static code.
The SecDevOps workflow then flows into:
- Infrastructure as Code (IaC) Implementation: Developers use Puppet, Chef, and Ansible to create an environment for deploying the application.
- Automated Testing: A whole set of test automation is run against the newly deployed application. These tests include backend, integration, API, security, and UI.
- Dynamic Testing: Automated dynamic testing of the deployed application is conducted in a test environment to detect vulnerabilities.
- Production Deployment: The application is deployed in the production environment if the tests are successful.
- Continuous Monitoring: The production environment is constantly monitored for active security threats, nullified as soon as necessary.
Difference Between DevSecOps and SecDevOps
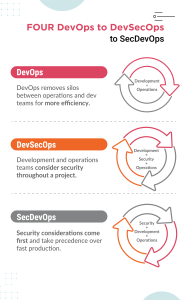 The DevSecOps pipeline introduces a continuous and agile software development process that seamlessly integrates development, security, and operations. However, it works only if there is collaboration across teams at all pipeline stages. Sometimes, DevSecOps is implemented incorrectly.
The DevSecOps pipeline introduces a continuous and agile software development process that seamlessly integrates development, security, and operations. However, it works only if there is collaboration across teams at all pipeline stages. Sometimes, DevSecOps is implemented incorrectly.
In an incorrect DevSecOps implementation, three different teams are asked to collaborate while being organized as different departments. For example, the development team works on design and building. In contrast, the operations team manages the underlying infrastructure, and finally, the security team takes up the responsibility of testing the application after the whole process is done.
The concept of SecDevOps arose to ensure genuine collaboration in the process. A SecDevOps pipeline shifts security entirely to the left, breaking silos and removing bottlenecks. Teams collaborate closely to try to develop high-quality, secure applications. Every individual contributes to quality and security, changing the culture.
Efficient implementation of the SecDevOps model requires taking full advantage of tools that automate repetitive tasks as much as possible. Automation plays a crucial role in the pipeline, increasing productivity. Moreover, pipelines require tools to integrate the technology stack and provide a centralized interface. Teams should be able to share tools and resources to address security issues adequately.
Best Practices of Implementing SecDevOps
SecDevOps embed security into every person’s workflow to make risk prevention the top priority. Because there is no dedicated security team in place, every person must also follow these best practices:
Develop Clearly Defined Security Policies for Staff:
Develop complete security policies that are tied to your business needs. These policies should include testing guidelines, encryption protocols, coding best practices, code review standards, and policies for work devices. Clarity mitigates the risk of data breaches and makes things clear for developers on what needs to be done, which will improve the quality of the products they produce.
Train All Employees in Secure Development:
Training for secure development should be a priority for experienced developers and newcomers. Even experienced developers will need to change their ways of doing things, as they have been trained in a security-centric approach to software development. Though they may not need to become as specialized in security as a dedicated security team, every new hire should be trained on basic digital security best practices, becoming familiar with integrating security into everyday practices and using basic security tools. Use standardized practices within the company and outline expectations for individual and team responsibilities.
Make Security Everyone’s Business:
Assign security responsibilities to all team members rather than a single point person or security team. Integrate security considerations into training, routine practices, and assessments. Promote personal responsibility while cultivating a security-first mindset throughout the company. Managers and senior developers should closely monitor systems, paying attention to suspicious activity. They should lead by example and reinforce the security-first mindset.
Adopt Version Control Practices and Tools:
Stress the importance of version control or the management and tracking of software changes. Developers should adopt version control when working on scripts, templates, and applications. Beyond managing code changes, version control provides audit evidence for compliance with the law, shows when vulnerabilities were introduced into a program, traces suspicious code additions or modifications, and outlines features vulnerable to data breaches.
Automate Standard Processes:
Automation reduces risk while increasing throughput. Processes and tools can speed up workflows without sacrificing product security. Automation includes repetition, thus freeing developers to do more work. It specifically helps with code reviews, latency issues, vulnerability assessments, and other rote tasks.
SecDevOps the New Way of Cybersecurity
Secure DevOps is a core practice that needs to be in place for organizations that desire to develop a robust software development process with underlying security. Through security integration into DevOps workflow, organizations are afforded the prerogative of handling and thoroughly resolving security vulnerabilities in the early stages of development. A preemptive posture in this regard reduces the chances of security incidents and subsequently lifts the defense level of the business enterprise.
The priority should be ensuring SecurityDevOps, a strong security culture that integrates security practices, tools, and processes throughout the Software Development Life Cycle (SDLC). The objective is to have teams pool together, automate security measures along with continuous solicitation inputs, and fix any security issues that crop up without fail.
FAQs
1. How does SecDevOps differ from traditional approaches to security in software development?
Traditional approaches often relegate security to a separate team or phase in the development process. In contrast, SecDevOps promotes a collaborative environment where security is everyone’s responsibility. It emphasizes security practices, automation, and continuous improvement, ensuring security considerations are integrated at every stage of the Software Development Life Cycle (SDLC).
2. How does SecDevOps work in practice?
SecDevOps integrates security measures into every employee’s workflow, from senior developers to new hires. It requires establishing clear security policies, providing security training to all employees, making security a company-wide priority, adopting version control practices and tools, and automating standard processes. By embedding security into every stage of the SDLC, organizations can effectively mitigate security risks and enhance their overall security posture.
3. How can SecDevOps be implemented successfully in organizations?
A combination of leadership commitment, employee training, team collaboration, appropriate tools and technology, along with continuous monitoring and improvement of security practices, would ensure successful implementation of SecDevOps in organizations. Organizations have to maintain security as a core value and resource allocation toward the proper implementation of SecDevOps principles.
4. What are the essential components of a SecDevOps approach?
The essential components of a SecDevOps approach include:
- Integration of security into every stage of the SDLC
- Collaboration among cross-functional teams
- Automation of security measures and standard processes
- Continuous monitoring and improvement of security practices
- Cultivation of a security-first mindset throughout the organization
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]


