Cybersecurity has become critical to overall security in the modern digital landscape. With the surge in cyberattacks, organizations increasingly rely on security analysts to ensure their systems’ integrity and confidentiality. These professionals face numerous challenges, including protecting sensitive government data and the security of private organization servers.
The prevalence of cyberattacks has escalated significantly. According to Check Point Research, global cyberattacks surged by 38% in 2022 compared to 2021. This alarming rise can be attributed to several factors, such as the expansion of remote work, the growing reliance on cloud computing, and the enhanced sophistication of cybercriminals.
Today’s cyber threats are particularly concerning due to the widespread use of hands-on or “interactive intrusion” techniques. Unlike traditional malware attacks that rely on automated scripts and tools, interactive intrusions involve adversaries actively engaging with the host systems to achieve their objectives. These attackers mimic legitimate user and administrator behavior, posing a significant challenge for defenders to distinguish between normal activity and malicious actions.
In 2023, CrowdStrike reported a 60% year-over-year increase in interactive intrusion campaigns, with a 73% spike in the latter half of the year compared to 2022. The technology sector emerged as the most frequently targeted industry for interactive intrusions, continuing a trend observed in 2022. The data highlights the relative frequency of intrusions across the top ten industry verticals and various geographical regions.
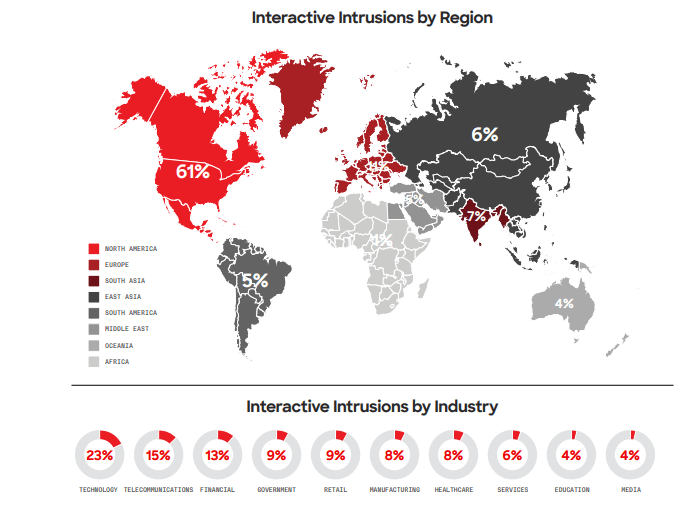 These developments underscore the evolving nature of cyber threats and the imperative for robust cybersecurity measures. Organizations must remain vigilant and adaptive, continuously enhancing security protocols to counteract cyber adversaries’ sophisticated tactics.
These developments underscore the evolving nature of cyber threats and the imperative for robust cybersecurity measures. Organizations must remain vigilant and adaptive, continuously enhancing security protocols to counteract cyber adversaries’ sophisticated tactics.
The role of machine learning in modern cybersecurity
Machine learning (ML) is emerging as a crucial technology in the fight against the increasing number and complexity of cyber attacks. Its capacity to analyze vast amounts of data and identify patterns makes it exceptionally suited for detecting attacks at their earliest stages, exposing network vulnerabilities, and predicting the timing and nature of future cyber threats.
While many industries already benefit from the capabilities of ML, its application in cybersecurity is still in the nascent stages. This early deployment reveals a significant gap between research advancements and practical implementation. The primary reason for this gap is the inability to delineate the role of ML in cybersecurity fully. Unlocking the full potential of ML in this field requires a comprehensive understanding of its advantages and limitations, accessible to a wide audience.
This article aims to bridge this gap by providing a holistic understanding of ML’s role in threat detection. Doing so seeks to pave the way for more effective integration of ML technologies in cybersecurity strategies, enhancing organizations’ ability to defend against sophisticated cyber threats.
The Evolution of Threat Detection
The history of cyberattacks dates back to the 1970s with the discovery of the self-replicating virus Creeper, which was followed by the creation of the first antivirus software, Reaper. With the evolution of cyber threats driven by technological progress, detection mechanisms have to be evolved in parallel.
Earlier, infection detection focused on identifying the presence of infections on user machines. The detection mechanisms were primarily based on signature detection and were intended to detect viruses, worms, and malware. However, the threat landscape has changed significantly in the past few years, and it is necessary to revisit the detection strategy in place.
Present-day adversaries are organized, have well-defined motives, and operate as a team, challenging conventional ways of defense. To thwart a breach effectively, insight into adversaries, including their motives, tactics, and targeting strategies, is needed. Intelligence on adversaries is important, and one useful way is to use tactical and strategic threat intelligence.
ML algorithms can analyze network traffic, system logs, and online activity data to identify aberrant behaviors or patterns. This can indicate possible activities for cyberattacks such as malware, ransomware, or phishing. Such proactive detection helps prevent breaches.
Role of Machine Learning in Threat Detection
Machine Learning has completely changed threat detection and how organizations identify and respond to threats, particularly in cyberspace. This is how ML is changing the scenario of threat detection:
- Advanced Anomaly Detection: ML algorithms analyze huge volumes of data to establish baseline behavior within networks or systems. When deviations from the baselines occur, ML quickly identifies them as potential threats, thus helping in the detection of zero-day attacks and unseen vectors.
Also Read: Top 10 Anomaly Detection Software for Secured Enterprise
- Behavioral Analysis: Models based on ML learn the behavioral patterns of users and devices, detecting activities or behaviors that are unusual or suspicious—such as unauthorized access attempts, data exfiltration, or privilege escalation—often remaining unnoticed in rule-based systems.
- Threat Intelligence: Threat intelligence feeds are seamlessly incorporated by ML from varied sources, with a constantly updating knowledge base to keep an organization ahead of evolving threats and adjust their defense accordingly.
- Automation of Routine Tasks: Routine tasks, such as log analysis and incident triage, are automated with ML, giving the security professional time for other, more complex tasks and incident handling.
- Real-time Threat Detection: The ML model works in real-time. It is associated with immediate alerting whenever it identifies an anomaly or threat to reduce reaction time and minimize potential damage.
- Scalability: ML-based threat detection systems scale efficiently with the quantity of data and network traffic, making them ready for all enterprises of any size.
- Dynamic Adaptive Defense: ML models adapt to evolving attack tactics and modify detection strategies. This is very dynamic in nature, which is important in the context of the dynamic threat landscape.
- Reduced False Positives: ML algorithms significantly reduce false positive alerts since they learn to distinguish genuine threats from benign anomalies, thus improving the accuracy of threat detection systems.
Machine Learning Applications in Threat Detection
Detecting Threats in Early Stages
Machine learning can process huge amounts of data. This means it can identify threats early and eliminate them before executing their malicious deeds.
An example includes Microsoft’s Windows Defender, which, in a span of 12 hours in 2018, prevented a potentially devastating cyber attack that aimed to infect more than 400,000 users with a cryptocurrency miner. Backed by multiple layers of machine learning, Windows Defender could quickly prevent the attack, thus thwarting any further significant damage.
Introducing Network Vulnerabilities
Organizations are now taking a more proactive approach to cyber threats. They are conducting penetration tests using machine learning. These tests essentially subject a network to a simulated cyber attack to uncover potential weak points in the network, its firewall, or its systems. Machine learning automates this process and then executes solutions to identified weaknesses, such as deploying software patches and code fixes.
In addition, machine learning can detect abnormal software and user behavior in these simulations. By analyzing past cyber attacks, machine learning can identify some of the most devastating threats based on the organization’s unique vulnerabilities.
Lowering IT Workload and Cost
Machine learning is automated. This method relieves IT teams of the burden of routine jobs, such as sending security updates, conducting penetration tests, and monitoring devices. This enables the IT team to focus on more severe cybersecurity issues and become more efficient.
Additionally, an organization will save on hiring costs required to replace the work that machine learning can undertake. This is especially helpful for smaller organizations that want to maximize their funds but not necessarily their employee number.
Also Read: Security Operations Center (SOC) Best Practices and Steps in Building Process
Constraints of Machine Learning in Threat Detection
- Sufficient, High-Quality Data: Effective machine learning models require access to substantial, high-quality datasets for both training and testing. Testing datasets should be independent of the training data to evaluate the models unbiasedly. Poor quality or insufficient quantities of data can exclude certain problem domains from the scope of applied machine-learning solutions.
- Interpretability: The capability to explain a model’s functioning—how and why it makes its decisions—is essential for transparency, accountability, and meeting the required data policies. Understanding factors influencing model performance informs continuous improvement and builds trust in machine learning systems.
- Trade-off Between True and False Positives: Model sensitivity must be calibrated effectively to balance detecting true threats while maintaining minimal false positives. This calibration will optimize detection performance while maintaining true threat identification.
- Repeatability: Machine learning experiments must be repeatable consistently to ensure that the models are transparent and to reduce errors during deployment and future model updates. Repeatability also ensures clarity around the models, training data, and software environments, thus building trust and reducing ambiguity.
- Optimization for Target Environment: Models must be optimized for production environments, especially regarding computational resources, memory, and connectivity. The deployment environment must host the model for optimal performance without service disruption.
- Hardening against Adversarial Attacks: Machine learning models can be vulnerable to adversarial attacks because adversaries may try to manipulate or exploit their operations. To address this, training a model includes hardening to ensure robustness in the face of potential attacks, thus minimizing the risk of misclassification and exploitation.
Companies Using Machine Learning in Cybersecurity and Threat Detection
1. CrowdStrike
2. Microsoft
3. Splunk
4. Forcepoint
5. Chronicle
Integrating Machine Learning into Existing Security Frameworks
Integrating machine learning into security infrastructure is a giant leap toward proactive defense strategies. It does not need a total makeover of an existing system but works in collaboration with the setup of established cybersecurity tools and frameworks, thereby lending an element of aptitude and stepping up digital defense.
This integration allows organizations to synergistically leverage the strengths of traditional and modern technologies to improve overall cybersecurity resilience. Machine learning works effortlessly with existing security protocols by bringing an intelligent layer into the setup that has an innate ability to avert emerging threats preemptively.
Future Outlook
In this modern, AI-driven world, machine learning constantly evolves as an invaluable powerhouse aiding cybersecurity and IT teams. AI is not a universal solution, but it does ease the burden on cybersecurity teams because it can perform some tasks much more efficiently than humans.
When everyday more and more devices are connecting to company networks, you can’t afford to monitor every device manually, so AI-based device profiling will improve endpoint fingerprinting and help with better segmentation and unauthorized device connection prevention.
Machine learning also helps generate policy recommendations for security devices such as firewalls, having learned typical device behavior and proposing the proper access control measures.
FAQs
1. What role does artificial intelligence play in cybersecurity beyond threat detection?
AI facilitates advanced and precise threat detection by empowering machine learning algorithms to analyze extensive datasets. These algorithms can swiftly identify patterns, anomalies, and potential threats in real time. This proactive methodology enables the early detection of emerging threats, even previously unseen or highly sophisticated.
2. What are the key trends shaping the future of cybersecurity beyond threat detection?
- Securing the Internet of Things
- Quantum Computing Threats and Defenses
- Zero Trust Architecture Adoption
- AI in Cyberdefence
3. Why is IoT cybersecurity important in today’s digital landscape?
4. What are the benefits of adopting machine learning in cybersecurity?
- Automation
- Rapid threat detection
- Scalability
- Cost-effectiveness
- Reduced human errors
[To share your insights with us as part of editorial or sponsored content, please write to psen@itechseries.com]


