Common Vulnerability Scoring System (CVSS) is a standardized ranking method of security vulnerabilities. The goal of this structured system is to help organizations compare vulnerabilities in different applications and from different vendors. The process to do these is a standardized, vendor-agnostic and repeatable approach.
CVSS provides a numerical score from 0 to 10, representing the severity of any information security vulnerability. Information security teams commonly use this scoring system under the vulnerability management program. These scores provide a point of comparison and can focus on the most critical vulnerability first and reduce the overall risk to the organization.
History of CVSS
The original CVSS scoring system was introduced by the National Infrastructure Advisory Council (NIAC) in 2003/2004. In April 2005, NIAC selected the Forum of Incident Response and Security Teams (FIRST) to become the custodian of CVSS v1.
Version 2 specifications were released in 2007, and version 3 specifications were released in 2015. The latest version in use is 3.1, introduced in 2019.
Factors Considered in CVSS Scoring
#1 Attack Vector: The attack vector can be classified into four values:
-
- Network,
- Adjacent,
- Local, or
- Physical.
- This reflects how an attacker can access the system, with the Network presenting the highest risk.
#2 Attack Complexity: It defines the difficulty in exploiting the vulnerability.
- Two values exist:
- Low or
- High.
- A low complexity indicates the highest risk.
#3 Privileges Required: This specifies the level of privileges the attacker needs before exploiting the vulnerability.
- Possible values include:
- None,
- Low, or
- High.
- None implies no access, Low indicates basic user capabilities, and High requires administrative privileges.
#4 User Interaction: It determines whether user engagement is necessary to exploit the vulnerability.
- Options are:
- None or
- Required.
- No user interaction results in the highest impact on the CVSS score.
#5 Scope: It assesses if the vulnerability can affect components outside of its security authority.
- Values include:
- Unchanged or
- Changed.
- A scope change has the most significant impact.
#6 Confidentiality: It gauges the potential for unauthorized access to sensitive information.
- Values are:
- High,
- Low, or
- None.
- High signifies the most severe impact.
#7 Integrity: This measures the potential for unauthorized data modification, breach, or deletion.
- Values include:
- High,
- Low, or
- None.
- High represents the highest severity.
#8 Availability: It evaluates the potential for denial of access to authorized users.
- Values are:
- High,
- Low, or
- None.
- High signifies the most severe impact on availability.
How do CVSS Score Metrics Work?
A CVSS score is a collection of metrics, including basic, temporal and environmental. Each metric has its own underlying scoring components.
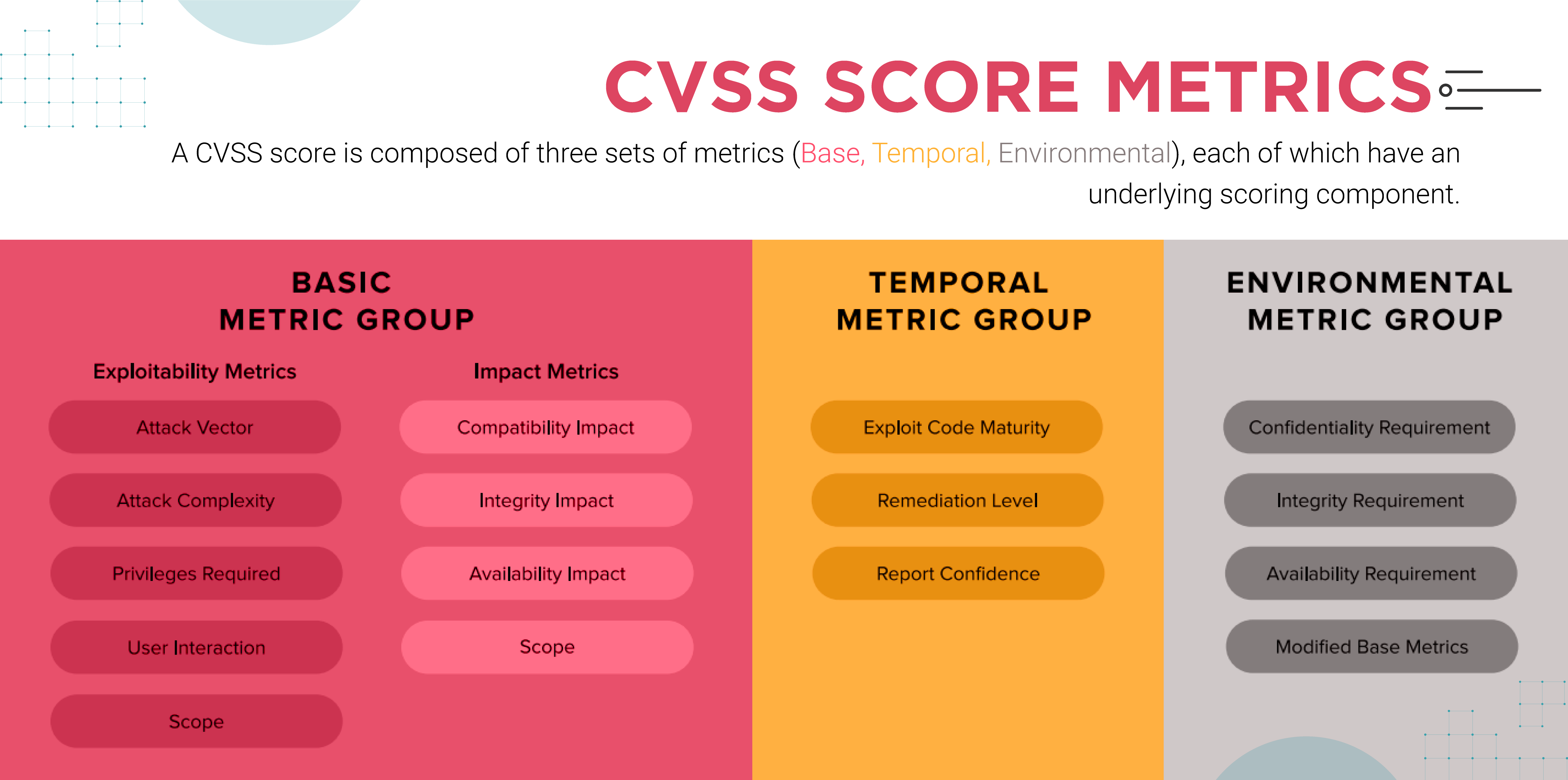 1. Base Metric Group
1. Base Metric Group
The base Factor represents the vulnerability characteristics itself. The characteristics remain constant irrespective of any real-world exploitation or other compensating factors that the enterprise has to implement to prohibit exploitation. The CVSS Base Metrics are based on three core elements including:
Exploitability:
This is created of the vulnerable component and is made up of four sub-components, including:
- Attack Vector—The score for the attack vector differs with the level of access needed to exploit the vulnerability. The score for exploits that can be executed remotely is higher than for exploits that require physical presence.
- Attack complexity—The score for attack complexity depends upon the factors that are outside the attacker’s control but need to exploit the vulnerability. An exploit that requires additional work on the attacker’s part will have a higher score than an attack that requires no additional effort.
- Privileges required—The requirements for privileges to conduct the exploit vary. Vulnerabilities that require administrative privileges will have higher scores compared to those that require zero authentication on the attacker’s part.
User Interaction—The score differs depending on whether the attacker is willing or unwittingly participating in completing the task. When the attacker can operate autonomously or without any user participation, the scores are higher.
Scope:
Scope addresses whether a vulnerability in one component can propagate to others. The scope score rises if propagation is possible. Examples of scope include being able to access and exploit the base operating system given a vulnerability in some software application or an attacker having access to a backend database after successfully exploiting a vulnerability in a web server.
Impact:
It focuses on the actual impact/outcome that an attack can get from exploiting the vulnerability in a question. The measurements of impact are done through the following three sub-metrics:
- Confidentiality – The score will be high if the all the data on the impacted system the attacker can access and low score when the data is not accessible.
- Integrity – For complete or several data modification availability the score is higher.
Availability – The score will be high if the system is no longer accessible or usable for authorized users as a result of the attack.
2. CVSS Temporal Metrics
CVSS Temporal Metrics describe the dynamic characteristics of vulnerabilities over time. They evaluate a vulnerability’s current exploitability and the availability of remedial measures, such as patches. These subcomponents include Exploit Code Maturity, Remediation Level, and Report Confidence.
Exploit Code Maturity:
Before a vulnerability can be exploited, it is relatively benign. However, as the exploit code matures, becoming more stable and widespread, this subcomponent scores increase.
Remediation Level:
Initially, when a vulnerability is discovered, there may be no patches or workarounds in place. In time, workarounds, temporary fixes, and official patches become available, lowering the vulnerability score as remediation improves.
Report Confidence:
Confidence measures how much validation exists to prove that a vulnerability is both real and exploitable.
3. CVSS Environmental Metrics
CVSS Environmental Metrics allows organizations to modulate the Base CVSS score based on their security needs and changes in Base Metrics.
Security Requirements:
These define the importance of the asset being talked about. Mission-critical assets get a higher score than others considered less significant. For example, a vulnerability in a database holding customer data would gain a higher score than one in a non-privileged user’s workstation.
Modified Base Metrics:
Organizations can modify the values of the Base CVSS Metrics based on mitigants in place. For example, actions like “air gapping” a server or removing external network connections would prevent adversaries from exploiting remotely accessible vulnerabilities. Consequently, in these situations, the Attack Vector Base Metric is reduced.
The CVSS is a scoring system that rates vulnerabilities on a numerical scale from 0 to 10; the higher the number, the more critical the vulnerability. Qualitative ratings map these scores so that non-technical decision-makers can easily understand them. In the CVSS, the higher the number, the more critical the severity of the vulnerability.
| CVSS Score |
Qualitative Rating
|
| 0 | None |
| 0.1 – 3.9 | Low |
| 4.0 – 6.9 | Medium |
| 7.0 – 8.9 | High |
| 9.0 – 10.0 | Critical |
- Calculation Process: Aggregation of Subgroups: Various score subgroups are aggregated to produce the comprehensive CVSS score.
- Base and Temporal Scores: The Base score is mandatory, and the Temporal score is optional, provided by the vendor or analyst.
- Environmental Score: The end user calculates the Environmental group score; it is optional, as well, but it provides a better assessment.
- Base Score Subcomponents: The Exploitability, Impact, and Scope subscores must be filled in. This information is used to classify a vulnerability with a CVSS score. These subcomponents of a base score combine in a weighted form to compute the base score.
- Temporal Score Calculation: The Temporal score is calculated by multiplying the Base score by three metrics within the Temporal metric.
- Environmental Score Complexity: The Environmental score is a slightly more complex calculation. The end user would re-calculate the Base and Temporal scores using five Environmental metrics to assess the vulnerability ratings more critically.
CVSS Benefits for Enterprise Security
- Establishing an open framework: The CVSS framework provides the parameters organizations can use to score vulnerabilities. It provides transparency, which helps in the clear understanding of vulnerability scores and aids security teams in prioritizing fixes effectively.
- Development of mitigation for vulnerabilities: Software developers use CVSS scores to point out the essence of security tests and address critical vulnerabilities at the software development level to reduce risks in the software life cycle.
- Adherence to standards of security: CVSS helps organizations meet the security requirements of various standards. For example, it keeps the organization in line with the standards of the Payment Card Industry Data Security Standard by addressing its vulnerabilities with a score of four or higher.
- Transparent and effective communications: The CVSS provides a standard way to assess and communicate the severity of vulnerabilities. Organizations can thus prioritize and address these critical vulnerabilities.
Conclusion
With the evolving cyber threats, the CVSS framework plays a pivotal role in safeguarding an organization’s technology infrastructure. With a comprehensive understanding of CVSS and its components, security professionals can adeptly navigate potential risks and safeguard sensitive data.
FIRST continuously enhances and updates the CVSS framework to ensure it remains aligned with emerging threats and vulnerabilities. Therefore, staying current with the latest version of CVSS is imperative for organizations to maintain the accuracy and efficacy of their vulnerability management practices.
FAQs
1. What is the difference between CVSS and CVE?
CVE stands for Common Vulnerability Enumeration, a unique identifier for each vulnerability listed in the NIST NVD. It is simply a list of all publicly disclosed vulnerabilities that include the CVE ID, a description, dates, and comments.
CVSS stands for Common Vulnerability Scoring System, which indicates the severity of each CVE. The CVSS score is not reported in the CVE listing, so organizations must use the NVD to find assigned CVSS scores.
2. What are the limitations of CVSS?
- Limited environmental context
- CVSS may not always match real-world scenarios
- It does not take into account the effectiveness of security controls to mitigate vulnerability exploitation.
3. Who Utilizes CVSS?
The National Infrastructure Advisory Council (NIAC) was submitted to the President in January 2005. Encouraged by the Department of Homeland Security (DHS) and CVSS developers, widespread, voluntary adoption is being promoted. Numerous organizations, including several NIAC member companies (Akamai, American Water, Symantec, Union Pacific), as well as other entities (CERT/CC, Cisco, HP, IBM, NIST, Oracle, Qualys, US-CERT), have since embraced CVSS.
4. What is a CVSS Score?
The CVSS score is a computation of base metrics that reflect how much risk a vulnerability poses to network security. Base metrics include access (from local to remote), access complexity, required authentication, impact on data confidentiality, data integrity, and data availability.
The CVSS system rates all vulnerabilities on a scale of 0.0 to 10.0, with 10.0 representing the greatest security risk. A ranking of 4.0 or higher indicates failure to comply with PCI standards.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]


