Welcome to the recap and the takeaways of the previous webinar of IBM on “Cybersecurity in the era of AI” that was held on April 23, 2024. As virtual space gets faster and the digital realm takes a more prominent place, cybersecurity threats continue to grow up and down, which require immediate solutions to improve every day. Within this framework, the role of artificial intelligence (AI) comes to the forefront – not only stimulating growth but becoming a necessity.
In this webinar, IBM defines the crossroads of AI and cybersecurity, ensuring the utilization of AI in its full superpowers while protecting AI applications from the most sophisticated ICT crimes. With AI development we see that new complexities and vulnerabilities are introduced. Therefore, COVID-19 has shown us how essential the use of AI in the protection of systems is; while at the same time, it has shown us the need to defend AI systems.
Also Read: Top IT, Cloud, Cybersecurity News Updates: Weekly Highlight
In addition, the webinar covered the speculations that are unique to AI’s risks, concentrating on the latest development of Generative AI. An expert recommendation was given to equip the guidance that can suppress these threats by possibly securing data and AI systems against emerging risks. Also, shaping innovative AI-powered cybersecurity solutions customized for today’s world in the exhibition while helping organizations remain ahead of the game will be showcased.
Whether your job function is that of a Chief Information Security Officer (CISO), VP/ Director of security, Senior IT manager, Chief risk/compliance officer, Security/IT architecture, Database administrator (DBA), or Security/Data Security Analyst, this recap provides vital knowledge from the webinar.
Topics Discussed during the Webinar:
#1 IBM’s Cybersecurity and AI Strategy
- AI-Driven Productivity: The webinar kicked off with a discussion on how foundational models and generative AI are going to break human bottlenecks in cybersecurity. Repetitive tasks of summarizing alerts or log analysis, etc., are done by AI, leaving human teams to focus on strategy.
- AI for Security: The quickness of generating security content with AI was covered with examples of creating detections, workflows, and policies to rapidly adapt to new threats in security.
- Security for AI: Secure AI models and datasets are essential. The talk covered IBM’s Adversarial Robustness Toolkit as one method to help protect against data leakage, evasion, poisoning, and other attacks on AI.
#2 Open Best Practices to Secure AI
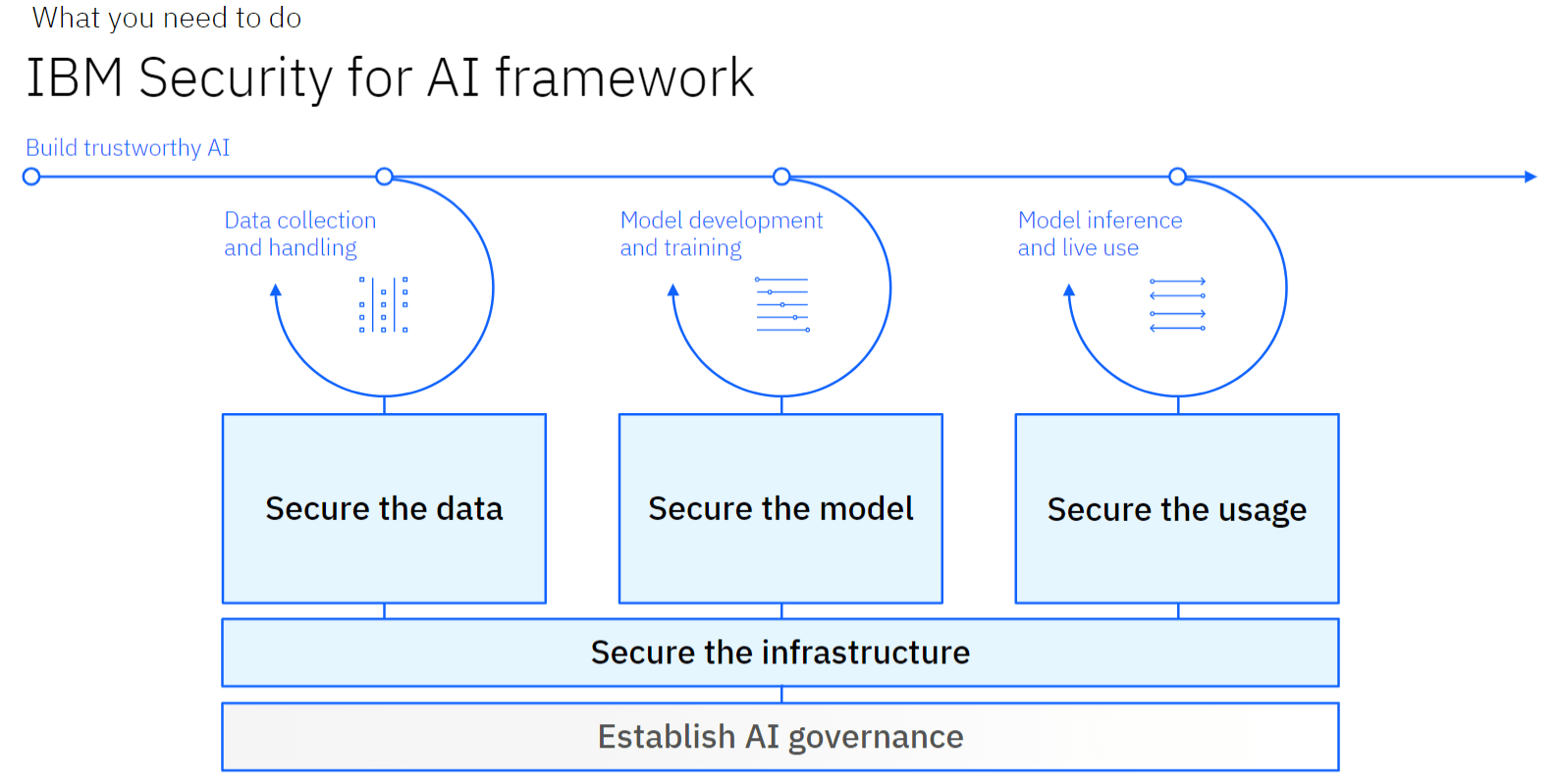
- Comprehensive Guidelines: The talk went on to cover the OWASP Top 10 for LLM Applications and ATLAS Matrix, outlining strategies for securing AI systems against common vulnerabilities, such as prompt injection, training data poisoning, and model theft.
- Security Measures: A list of seven best practices was covered in detail, including securing access to AI systems, safeguarding against adversarial attacks, and data privacy in the operations of AI.
#3 Leading Use Cases for Watson for IBM Security Clients
- Automation and Efficiency: The webinar showed how Watson automates menial work and creates playbooks for incident response. 40% of a security analyst’s time can be saved through the automation of tasks with AI.
- Proactive Measures: The validity of AI in threat hunting and predictive insights was demonstrated, by which AI will spot the potential attacks and repeat offenders, which significantly boosts the readiness of a response.
#4 AI and Automation Infused Threat Lifecycle Components
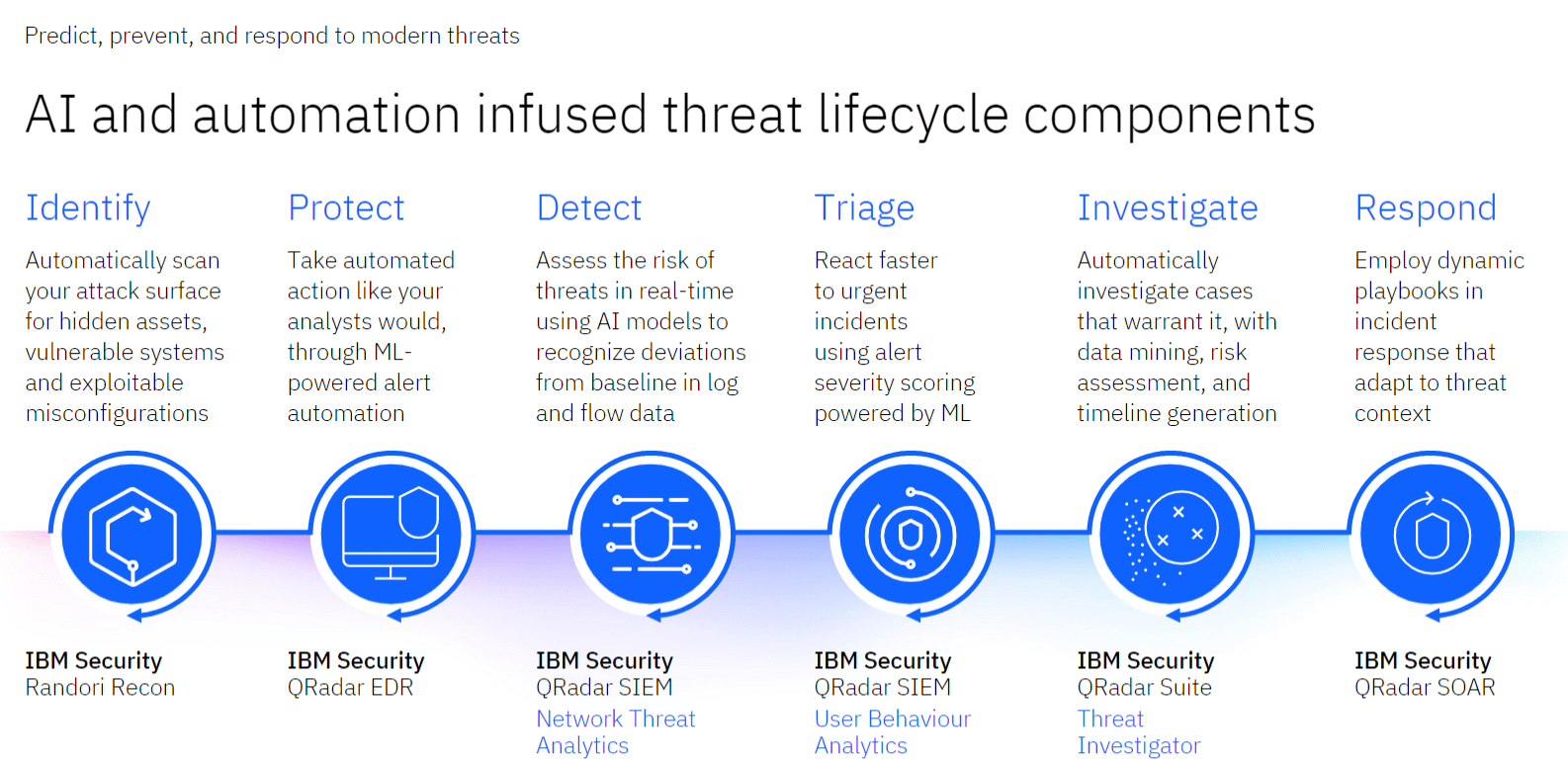
- Threat Lifecycle Management: The webinar showed an AI-infused threat lifecycle comprising the identification, protection, detection, triaging, investigation, and response of threats, helped with AI.
- Integrated Solutions: IBM’s suite of solutions including QRadar, Randori Recon, and QRadar SIEM were discussed in terms of the threat detection and response strategy.
Introducing the AI Superpower for Time and Cost Reductions - AI Capabilities: IBM’s AI-infused capabilities, including QRadar Threat Investigator, were demonstrated for security operations automation and the reduction of human intervention.
Client Outcomes: Impressive client outcomes included 55% quicker alert investigation and 90% lower false positive rates.
#5 An Open Architecture to Implement Security Across the Hybrid Cloud
- Security Architecture: The need for an open architecture that integrates multiple tools and data to bring visibility and efficiency while reducing costs was highlighted.
- Hybrid Cloud Approach: QRadar, Guardium, and Trusteer were called as part of a single approach to detecting threats, securing data, and ensuring compliance for identity, fraud, and device management.
#6 Key Considerations When Maximizing the Impacts of AI in Cybersecurity
- Strategic Deployment: Open architecture for speed and scale was emphasized while highlighting how AI, when added to data models, gives added speed and accuracy for proactive protection and detection.
Security Teams Must Contend with the Adversarial Risks of AI Adoption - Adversarial Risks: AI adoption risks have been highlighted, including model evasion and data poisoning. How these risks are managed is discussed in the webinar.
Also Read: CIO Influence Interview with Janet Ravin, VP of Marketing at Rimini Street
Conclusion
The webinar ended with key information on the dynamic relationship between cybersecurity and AI, emphasizing the need to ensure the security of AI systems as they get more prominence as threats arise. While the increasing dominance of machine learning and AI in the digital space becomes a matter of concern, it is nonetheless understandable that the integration of technology into cybersecurity strategies is a necessity for organizations, as it will grant a wide range of opportunities to combat cybersecurity problems and be productive.
During the webinar, attendees grasped the concept of the applied information technology and AI strategy by IBM including productivity driven by AI, secure AI, and exemplary cases of Watson applied for IBM Secure clients. Moreover, the guidelines and the best practices for securing the systems via AI against commonly known vulnerabilities were also shared, and IBM’s solution suite demonstrated in the forum the power of AI in threat lifecycle management and security operations automation.
That is why, the open architecture concept particularly for the establishment of security in hybrid cloud environments was mentioned along with the AI’s main use in cybersecurity by specifying its core principles. In addition, participants were informed about the various adversarial risks that exist when AI adoption takes place, for instance, how to deal with model evasion and data poisoning, amongst all.
FAQs
1. What was the focus of the IBM webinar on “Cybersecurity in the era of AI”?
The webinar explored the intersection of AI and cybersecurity, emphasizing AI’s role in both enhancing productivity and safeguarding against sophisticated cyber threats.
2. What are the key topics discussed during the webinar?
The webinar covered IBM’s Cybersecurity and AI Strategy, Open Best Practices to Secure AI, Leading Use Cases for Watson for IBM Security Clients, AI and Automation Threat Lifecycle Components, and Key Considerations When Maximizing the Impacts of AI in Cybersecurity.
3. How does AI contribute to cybersecurity productivity according to the webinar?
AI-driven productivity was highlighted, showcasing how AI automates repetitive tasks, such as alert summarization and log analysis, allowing human teams to focus on strategic aspects of cybersecurity.
4. What measures are recommended to secure AI systems against vulnerabilities?
The webinar suggested comprehensive guidelines, including the OWASP Top 10 for LLM Applications and ATLAS Matrix, along with seven best practices for securing AI systems against common vulnerabilities like prompt injection and data poisoning.
5. What are some notable outcomes demonstrated during the webinar?
Impressive client outcomes included a 55% quicker alert investigation and a 90% lower false positive rate through the implementation of IBM’s AI-infused capabilities, such as QRadar Threat Investigator.
6. How does the webinar address adversarial risks associated with AI adoption?
The webinar discusses adversarial risks, such as model evasion and data poisoning, and provides insights into managing these risks effectively to ensure the security of AI systems.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]


