Social engineering is creating a tumultuous situation for IT and SecOps teams with its malicious modus operandi. Attackers, themselves, are testing new waters to launch new types of warfare across various industries. For cloud customers, security is the number one challenge — because in 2022, 45% of the reported incidents occurred in the cloud.
According to another recent report, 94% of cloud tenants were targeted every month in 2022 by new forms of attack chains. This is seen as a tactical evolution adopted by financially-motivated cybercriminals who are injecting different kinds of social engineering malware. That’s the extent to which cyber attackers have grown in the post-pandemic months. These attackers target cloud tenants by gaining illegal access to corporate databases and devices. The rise in the number of reported cybercrime cases clearly indicates a change in the threat landscape.
In 2022, we saw a major uptick in the number of cyber attacks targeting cloud tenants.
The threat persists in 2023 too.
In fact, cybercriminals have emboldened their spirits to go after opportunities in the most unexpected of places. Despite wielding advanced technologies to secure cloud assets, CIOs are finding it extremely hard to safeguard their organization, people, and customers from modern forms of attack chains.
Globally, organizations running on cloud platforms could lose $10.5 trillion by 2025 due to cyber attacks. Hypothetically putting, if all the cybercrime attackers operated from the same country, they would be the third largest global economy in the world. US-based companies top the all-time list of targets, taking a lion’s share of the total number of records stolen from their databases in the last 3 years.
Recommended CIO Influence News:
Netskope Enables Secure Enterprise Use of ChatGPT and Generative…
Despite having access to some of the best-performing cloud security service providers and technologies, US companies suffer due to a constantly evolving strong attacking strategy adopted by the persistent threat actors and cyber terrorists. These attackers change their social engineering operatives very quickly with rapid iterations and wait patiently for their victims to make a mistake.
Understanding social engineering attacks can ultimately save your organization millions of dollars and tons of time and resources that go into recovering from financial loss and a tarnished brand image.
Let’s understand the social engineering equation and what the leading technology companies say about the technique.
What is Social Engineering?
Social engineering is very effective in trapping people. 84% of these attacks are financially-motivated, of which 50% are reported as pretexting incidents. (Source; Verizon)
Social engineering is also referred to as “human hacking” and “personality theft” perpetrated by cybercriminals.
People make the mistake of sharing all the information with a second person despite knowing that doing so (including their spouse, friends, or colleagues) could land them in trouble. It involves the use of manipulative techniques to gain the trust of their victims through personalized messaging and tempt them into divulging vital information such as passwords, personal data, or their company’s details.
In most cases, victims have no idea that they have been tricked by an attacker. These incidents mostly go unnoticed by individual victims — but, are severely investigated if an organization is at the receiving end.
CIO Influence Trends: Black Kite Announces First Ever Automated Cyber Risk Quantification Capabilities
How does Social Engineering Work?
To understand social engineering, you have to be absolutely clear about the online and physical identities of the persons you are dealing with. The whole ecosystem functions on the premise of “impersonation.”
What is Impersonation?
In the cybercrime context, impersonation is an illegal posture or identity adopted by an agent to commit fraud. Now, this fraud could lead to financial theft, data breach, stolen identity, ransomware, cyber-terrorism, or device hijacking. Pretexting is the start of most impersonation attacks.
This is what a pretexting format looks like.
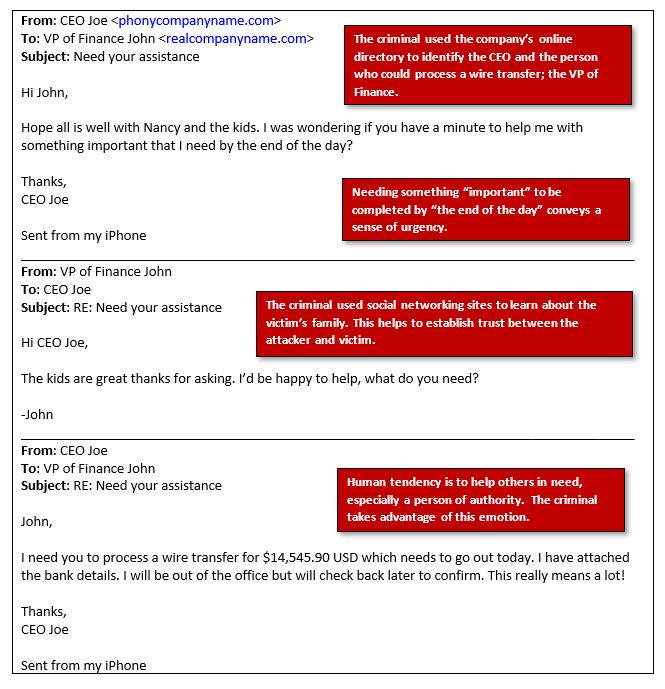
According to Microsoft, social engineering is a game of wait-watch-pounce-disappear.
Attackers build their strategy based on research which allows them to sink into the lives of their victims in the least suspecting way. From gathering background information about their victims to taking control of their confidential information, the entire tactic revolves around the art of persuasion using storytelling.
Here are the most common types of social engineering techniques that are identified by cybersecurity analysts.
Phishing
Phishing-related losses tripled between 2015 and 2021. Data hackers prefer to inject phishing vectors before moving ahead with their social engineering tactics.
84% of organizations have experienced at least one successful email-based phishing attack in 2022.
There are many layers of phishing that target victims in a social engineering context.
For example, CEO Fraud is a rampant one where a business leader from the employer’s side would pose as legitimate personnel and ask for credentials to log into a device or a cloud-hosted software application.
In some cases, a CEO Fraud could also become a financial fraud if a transfer of funds or sharing of financial information is involved.
From scanning a QR code to clicking on an email from a familiar (but not the same) ID, phishing can be carried out in numerous ways.
Whaling
Financial institutions, payment services, and e-commerce organizations face the maximum risks from whaling social engineering attacks in 2023.
Did you know Microsoft is the most abused brand in the world?
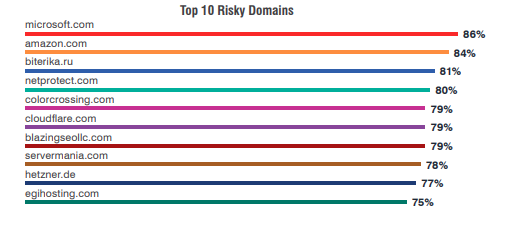
Users often fall prey to bogus emails carrying the name of reputed brands and organizations such as Cloudflare, Google, Facebook, Apple, and Amazon.
Apart from enterprise technology users, patients, e-commerce consumers, and job-seekers also fall prey to impersonation-led social engineering attacks. Whaling targets executives who hold the key to critical infrastructure, databases, and employee communication.
When attackers target a senior-level executive or a celebrity with social engineering tools, it’s called whaling (derived from the word – whale). Whaling is an extension of an advanced phishing attack, called spear phishing, where attackers instill a sense of fear and urgency in their victims. For instance, sending a legal notice and asking for a bank wire or crypto fund transfer to drop the lawsuit.
MFA Bypass
Cybercriminals are using phishing-as-a-service tools to launch reverse proxy attacks against MFA frameworks.
MFA Bypass is a new development in the social engineering attack ecosystem.
Cybercriminals opt for a combination of attack tactics — token compromise, prompt bombing, consent phishing, brute force, session hijacking, and SIM hijacking, to gain access to cloud applications such as email, team meetings, employee collaboration, file sharing, employee payrolls, health trackers, and biometrics.
According to the latest Proofpoint’s annual Human Factor report, EviProxy, Evilginx2, and NakedPages are prominent frameworks that support MFA bypass.
Telephone-Oriented Attack Delivery (TOAD)
Call centers are the new social engineering tool kits. Millions of TOAD messages are detected every month that are orchestrated with ‘vishing’.
At its peak, 13 million monthly TOAD messages were generated in 2022!
TOAD phishing campaigns have grown exponentially since the onset of the COVID-19 pandemic. According to NJCCIC, TOAD social engineering campaigns originate from call centers that are illegally misrepresenting the companies offering firewall services, digital banking and payment services, or currency exchange platforms.
TOAD agents generate a fake invoice or subscription link to lure victims, requesting them to leave their personal information on a “contact” form or click on a helpline number to reach the customer service department. Once the victim calls the call center, a trained agent steers the conversation toward service-based actions, which could include asking the victim to install an app on their device or scanning a QR code.
Water-holing, voice phishing, quid pro quo, and pharming– are other techniques that are catching cloud tenants on the wrong foot with social engineering campaigns.
According to Proofpoint’s EVP of cybersecurity strategy, Ryan Kalember, threat actors have evolved at a much greater speed compared to the enterprise security controls that typically protect an organization from threats. Attackers have found new ways to bypass existing frameworks by using innovative techniques such as MFA bypass and telephone-oriented attack delivery. Ryan says, “While many threat actors are still experimenting, what remains the same is that attackers exploit people, and they are the most critical variable in today’s attack chain.”
ChatGPT: Is it With Us or Against Us?
If let loose, it won’t take much time to turn ChatGPT into a PhishGPT or HackGPT tool, used conveniently to carry out social engineering campaigns against cloud users. The recent innovations in the field of generative AI have created opportunities for everyone, including cybercriminals. Criminals are using ChatGPT and other similar generative AI bots to craft branded emails and messages to trap their victims. Some groups are using copilot tools to auto-generate malicious codes for hacking purposes.
To secure IT assets and employees from falling into the phishing trap, CIOs could propose an AI model that can simulate cloud security threats and build LLMs to identify possible attack surfaces in their organization.
Securelist used ChatGPT to understand how LLMs could be used to assist security professionals against phishing attacks.
Cloud security is an organizational responsibility, yet having AI in your team to guard the vulnerable points is a strategic decision that CIOs and CISOs should explore in 2023. IT and SecOps teams could use AI and analytics to avoid the costs and risks associated with security incidents through continuous improvement, predictive threat monitoring, and real-time remediation.
With a solid cloud security strategy hinged on AI and human intelligence, it is possible to build an impenetrable anti-social engineering framework for your organization that learns and scales with time, experience, and data.


