Data recovery management is a key component in the modern cyber readiness and defense program, particularly against ransomware attacks. The ability to recover data from encryption has only declined in recent years in manufacturing and production. According to an IBM report, 30 percent of all ransomware attacks in 2022 were focused on manufacturing — the highest among all industries. In another report, Dragos found 67% of attacks (143 confirmed incidents) targeted only manufacturing companies in the entire industrial sector.
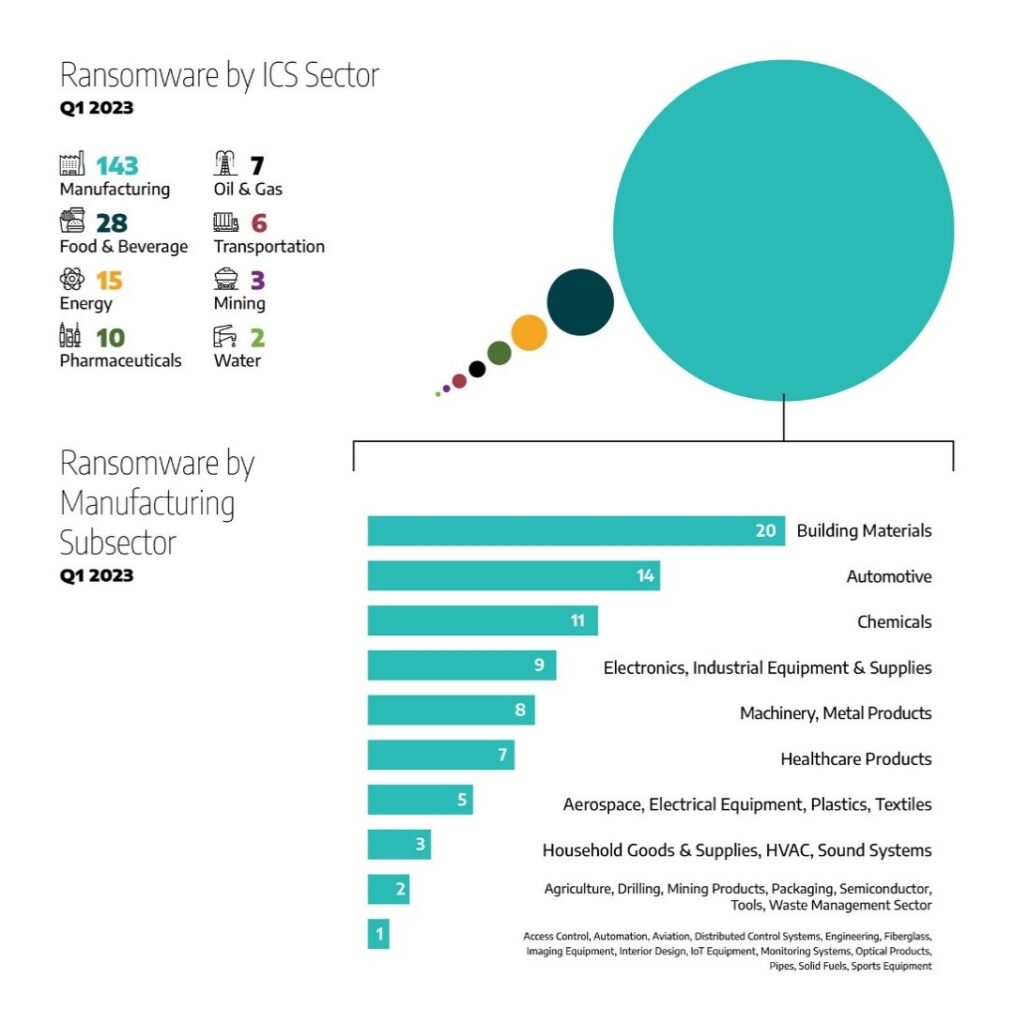
Despite having access to world-class threat intelligence tools for detecting attacks, victims are having a hard time recovering data from attackers. According to Sophos, despite known risks, the manufacturing companies are sluggish with their efforts against data encryption in 2023. Sophos released their new report titled, “The State of Ransomware in Manufacturing and Production 2023” to point out the cybersecurity readiness against ransomware attacks and the data recovery management in manufacturing.
The ability to respond to data encryption is a major challenge for CIOs and CISOs in the manufacturing and production industry. Adversaries are taking full advantage of the technology to access and exploit vulnerabilities across 78,000 known surfaces. Most of these attacks penetrate the IT and networking systems through undetected and unpatched vulnerabilities, compromised credentials, and phishing vectors.
Looking to feature your content with us? Contact us for lead generation and content syndication services.
Knowing that manufacturing companies are an easy target for ransomware, attackers closely monitor the cybersecurity readiness of manufacturing companies before exploiting their IT vulnerabilities for extortion.
Here are the key highlights of the report that every CIO and CISO in the manufacturing industry should note.
Top root causes of ransomware attacks on manufacturing
Security managers and leaders are hardening their stance against ransomware attacks, but lacking in direction when it comes to preventing data loss. Going by the latest trends mentioning the root causes of ransomware attacks on organizations, compromised credentials (27%) and exploited vulnerabilities (24%) ranked on top of the list. Other root causes for ransomware attacks on manufacturing are:
- malicious emails (21%)
- phishing (20%)
- brute force attacks (5%),
- downloads (2%)
According to Checkpoint’s 2023 Cloud Security Report, misconfiguration of cloud platforms or improper setup (59%) ranks as the most significant security threat. Exfiltration of sensitive data (51%), unsecured APIs (51%), and unauthorized access (49%) also contribute to vulnerabilities.
“24% of respondents reported experiencing public cloud-related security incidents, with misconfigurations, account compromises, and exploited vulnerabilities being the most common incident types.”
(Source: CHECKPOINT’S 2023 Cloud Security Report)
Having an uneven cybersecurity readiness and awareness strategy leaves too much on the table for CIOs and CISOs to look into, especially when they are expected to provide answers to critical questions related to risks and the action plans. Identifying root causes is one thing, and acting on them (even with limited resources) is a totally different thing altogether. For CIOs and CISOs, managing risks associated with data recovery and ransomware attacks depends on robust models and protocols that take organizations to a stronger risk position against external threats.
68% of attacks led to data encryption
Data encryption is a “double dip” event for the manufacturing and production industry.
Attackers are using sophisticated means to target victims with a weak cybersecurity infrastructure. Nearly two out of three attacks on manufacturing businesses led to data encryption. Worse, manufacturing companies are seemingly unsure about the impact such attacks have on their IT and data management reputation. 32% of ransomware attacks that reported an incident of data encryption eventually resulted in data theft. This means the adversaries are firm about their target’s mismanaged data recovery plans even after data encryption.
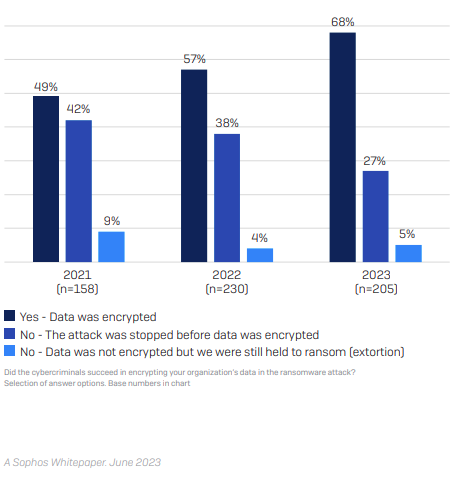
Despite the imminent risks to the infrastructure and existing IT resources, the security managers are unable to stop data encryption in time. While the number of attacks on companies continues to rise every year, their ability to detect incidents and stop data encryption in time has deteriorated. In 2023, only 27% of attacks were denied data encryption in comparison to 38% in 2022, and 42% in 2021.
Surprisingly, 5% of respondents mentioned that despite stopping data encryption in time, they were still held to ransom by the attackers. This could mean two things:
- The ability to stop and then audit data encryption was strongly compromised.
- The security team did not pay attention to the aftermath of data encryption, resulting in ransomware demands.
88% (Only) got their Data Back after Encryption
Stats show that security teams within manufacturing and production organizations are lagging in their approach to data recovery. Only 88 percent of organizations in the manufacturing industry actually salvaged their data after encryption, almost 11 points below the global average (97%) for all organizations across industries hit by ransomware.
How they got their data back?
Security teams either paid the ransom for data recovery (34%) or used the data backup services (73%). In 2022, 33% of companies paid ransom for data recovery. While other industries prefer to pay ransom after data encryption, manufacturing organizations stick to backup services to recover data from ransomware attacks — a solid signal against a vicious challenge that is defining the state of ransomware preparedness in 2023 across all industries.
Cyber Insurance Policy Influences Response against Ransomware
One thing that manufacturing organizations understand better than others is the importance of having a cyber insurance policy ingrained within their corporate strategy.
A cyber insurance policy or cyber liability insurance covers a business’ liability arising due to a data breach or other security incidents. Currently, regulations dictate organizations to disclose the extent to which their IT systems and critical customer data were exposed to threat agents. Insurance policy safeguards the company against liabilities arising due to failure in data recovery of Social Security numbers, credit card numbers, account numbers, driver’s license numbers, health records, and so on.
94% of ransomware victims in the manufacturing industry with a cyber insurance policy recovered encrypted data. 52% of victims gained the confidence to pay the ransom to the attackers to take back control of the encrypted data. Without the backing of cyber insurance, only 53% of companies recovered encrypted data while merely 11% paid the ransom.
Clearly, cyber insurance is a savior for manufacturing and production industry against the highly aggressive data encryption-centric attacks.
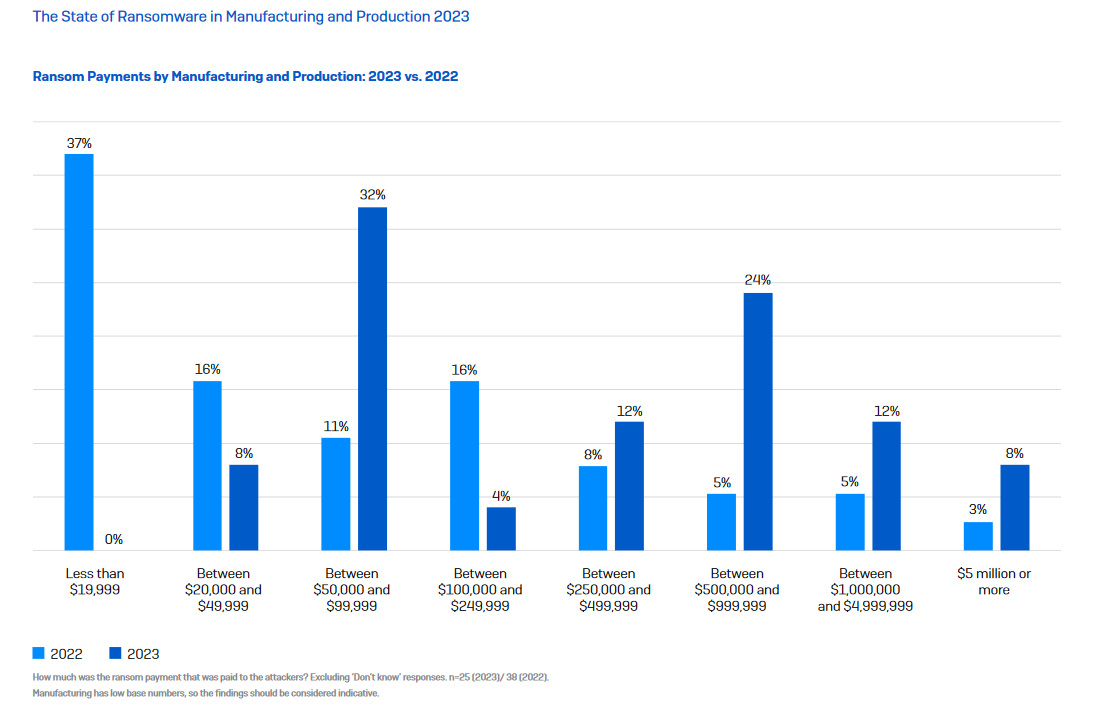
Paying 2X Higher Ransom in 2023 compared to 2022
8% of ransomware victims surveyed by Sophos mentioned they have paid a ransom of $5 million or more in 2023 compared to 3% in 2022. This is a massive uptick in the number of victims who agree to pay ransom to secure encrypted data.
Smart move — cyber attackers too have changed their strategy and are identifying “princely” victims who can pay higher ransom to recover their data. Compared to 2022, the average ransom payments have nearly doubled this year. Sophos found 40% manufacturing organizations paid higher ransom ranging between $100k and $999k in 2023. Only 29% paid ransom in this range in 2022. The average ransom payment in 2023 hovered at $1,542,533 against a modest average of $812,830 in 2022! This shows the propensity to pay a higher ransom amount among the manufacturing organizations this year.
Interestingly, none of the victims paid a ransom below $20k.
The financial pains do not stop at merely paying out the ransom to the attacking groups. It drags on for the victims as an after-effect of ransomware events. In addition to the hefty ransom payments, manufacturing organizations had to spend more on recovery costs. For companies with a cyber insurance and backup services, the recovery costs may have been slightly lower. Sophos found manufacturing and production organizations spent the least to recover from an attack with a recovery cost of $1.08 million, way lower than the global average of $1.82 million across all industries.
This is what each industry pays as recovery costs after a ransomware attack:
| Industry | Recovery costs (in USD Million) |
| Business and professional services | $1.72 |
| Central / federal government | $1.32 |
| Construction and property | $1.63 |
| Distribution and transport | $3.54 |
| Energy, oil and gas | $3.17 |
| Financial services | $2.23 |
| Healthcare | $2.2 |
| Higher education | $1.06 |
| IT, technology and telecom | $1.21 |
| Local / state government | $1.21 |
| Lower education | $1.59 |
| Manufacturing | $1.08 |
| Media, leisure, and entertainment | $3.15 |
| Retail | $1.85 |
| Others | $0.9 |
Investments in Backups can significantly lower your recovery costs?
How?
Sophos tells us.
Organizations with a robust backups and data recovery infrastructure saved $1 million in recovery costs compared to others who paid the ransom instead. For manufacturing, “the mean recovery cost with backups was $50K less than by paying the ransom,” as per Sophos. 84% of private organizations hit by ransomware attacks mentioned loss of business and revenue in the survey. Despite the extent of vulnerabilities and the damage inflicted by ransomware attacks, the manufacturing and production companies are least likely (77%) to suffer from loss of business or revenue in 2023.
Companies are taking more time to recover
Sophos reported a drastic increase in the number of companies failing to salvage and recover their data quickly. In 2023, 28% of victims took up to a month to recover from a ransomware attack, which is slightly higher than last year’s record (23%). Only 9% of victims had enough resources and support to help them recover within a day after an attack. In 2022, this number stood at 22% of all attacked organizations in the manufacturing industry.
Sophos also found these about organizations who used backups for data recovery and paid ransom.
- 48% of organizations who have a backups solution had complete recovery from the attack within a week;
- Only 34% of organizations who paid ransom recovered within a week;
- 52% of backups users recovered their entire data after a month’s hassle, 66% of organizations who paid the ransom instead took more or less the same time for recovery.
It is evident that having backup-as-a-service can accelerate the data recovery process and save recovery costs after a ransomware attack.
Conclusion
Without adequate risk management resources and backups infrastructure, CIOs and CISOs could face a daunting challenge in 2023. With ransomware attacks finding new avenues to target and victimize businesses, security leaders should device a dynamic technology-driven strategy to stay ahead of the attackers all the time. This is only possible when organizations invest in adaptive technologies that respond automatically to attacks, killing the confidence of adversaries and buying the victims time to respond with a solid data recovery plan.
So, what does your data recovery plan looks like?


