As Gartner had stated in 2018 — “GDPR is a wakeup call for all CISOs.” GDPR has ceased to be an all-European thing. It has now earned the global recognition of being one of the most widely accepted law for data privacy and information security. The recent fine on Meta (the owners of Facebook Messenger, WhatsApp, and Instagram) has stirred a rhetoric associated with the GDPR. The fact that this happened close to GDPR’s fifth anniversary only makes it more interesting and worth analyzing from a larger perspective. If big technology organizations are still unable to correct their GDPR compliance, it’s hard to understand how smaller organizations could be dealing with GDPR activities, that somehow overlaps with the role of a Chief Data Officer (CDO) and a Chief Information Security Officer (CISO). For most CISOs, GDPR could mean a set of regulating instructions on information privacy and data protection for the safety of users who trust organizations with their data.
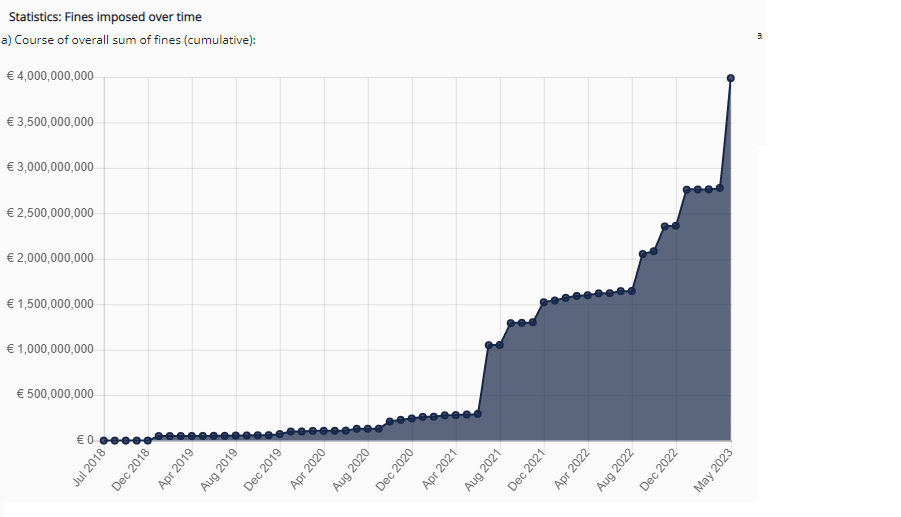
Astonishingly, the COVID-19 pandemic months saw a massive increase in the number of GDPR fines imposed on organizations that failed to comply with the regulations. The size of the total amount of penalties that were imposed on the organizations also increased significantly from April 2021, reaching its highest in May 2023.
 In our featured conversations, the leading IT and data security leaders from different regions spoke to us ahead of the GDPR anniversary. We discussed about the role of emerging technologies, attitude of CISOs and data officers, and the need to create more open platforms to discuss the gaps within GDPR and other related laws.
In our featured conversations, the leading IT and data security leaders from different regions spoke to us ahead of the GDPR anniversary. We discussed about the role of emerging technologies, attitude of CISOs and data officers, and the need to create more open platforms to discuss the gaps within GDPR and other related laws.
Our CIO Influence editorial team offered a common platform to these speakers to express their views and insights on GDPR and its role in shaping the data compliance frameworks for their respective organizations.
- George Gershow, IANS Faculty and CSO and SVP of IT at Sumo Logic
- Michael Jack, CRO and Co-Founder, Datadobi
- Larry Whiteside Jr., CISO of RegScale
- Paul Trulove, CEO of SecureAuth
- Alastair Parr, SVP of Global Products & Delivery, Prevalent Inc.
- Rick Hanson, President at Delinea
- Ashish Patel, GM EMEA of mobile security company Zimperium
- Chris Vaughan, VP Technical Account Management, EMEA, Tanium
- Jeff Reich, Executive Director at the Identity Defined Security Alliance (IDSA)
- Amit Shaked, CEO and co-founder, Laminar
Here’s what the leaders had to say about GDPR this week.
Emerging Technologies Influence the Way GDPR Takes Shape in the Next Few Years
George Gerchow, IANS Faculty and CSO and SVP of IT at Sumo Logic
“The General Data Protection Regulation (GDPR) is an evolving regulation, and there are several developments expected in the coming years.
Emerging Technologies – As new technologies such as artificial intelligence and the Internet of Things become more prevalent, there will be a need to assess their impact on data protection and privacy. The European Data Protection Board (EDPB) is expected to provide guidance on the application of GDPR to these technologies.
Recommended: Top Five HPE GreenLake Cloud Services for Optimal Business Outcomes
About the ePrivacy Regulation, the European Union is also working on a new model which will complement GDPR by providing specific rules on the use of electronic communications data. The regulation is expected to be finalized and adopted in the near future.
Overall, GDPR is likely to continue to evolve and adapt to new challenges in the coming years, with a focus on protecting individuals’ privacy and personal data in an increasingly data-driven world.”
The Importance of Storing Certain Data Under WORM Control
Michael Jack, CRO and Co-Founder, Datadobi
“WORM data stands for Write Once, Read Many data, which refers to data storage that allows data to be written only once and then read many times, but cannot be modified. WORM data is required for a variety of reasons, particularly in industries where data integrity, authenticity, and long-term preservation are critical. Examples include financial services, healthcare, legal, telecommunications, and government sectors. In these industries, WORM data is used to store important records, such as financial transactions, medical records, legal contracts, and government archives. The data is stored in a format that cannot be altered or deleted, ensuring that the information is preserved in its original state and that it is available for audit or legal purposes if necessary. WORM data is also used to protect against data tampering and ensure compliance with various industry regulations, such as SEC Rule 17a-4(f), HIPAA, and GDPR.
CIO Insights: Closing the Protection Gap: Data Protection Must Be More Than a Box…
In response to these requirements, storage vendors have incorporated WORM capabilities into their systems. These capabilities allow for the creation of special storage areas where data can be stored for a specified period of time without being deleted or modified. The retention date of each file is stored individually as it may vary. For instance, some files may need to be retained for seven years while others may need to be kept for 10 years, and so on.”
EU-US Data Privacy Framework is the Most Awaited Event in Post-GDPR Era
Larry Whiteside Jr., CISO of RegScale
“Reflecting on another year of GDPR reminds me that the mere existence of this regulation has been a global game changer. From California Consumer Privacy Act of 2018 (CCPA) to the Personal Information Protection and Electronic Documents Act (PIPEDA), GDPR has been driving the notion of data privacy across the globe. To me, it’s a good example of what potential global policy could look like. Looking back at 2021, though the fines were not the highest we’ve seen, there were still some very hefty fines levied in 2022 with Meta and Clearview being the two organizations hit the hardest.
There are also two additional things being worked in the background to enable GDPR to keep up with the new threats to data privacy and reduce some of the current complexity that exist in its current state.
There is currently a Data Protection and Digital Information Bill, which had its first reading in May 2022, that seems to be stuck. This new bill seeks to simplify GDPR and make it more agile to adapt to the needs of organizations trying to create data privacy policies and architectures that enable them to meet the specific controls of GDPR.
Additionally, in an effort to combat the risks being introduced due to the AI phenomenon, there is work that is being looked at to identify the intersection between the Artificial Intelligence Act (AI Act) and GDPR. The outcome could be very interesting in how organizations meet GDPR as it relates to privacy data and artificial intelligence.
As we look forward, we should pay close attention to the EU-US Data Privacy Framework and the impact it will have on transmitting data into and out of the EU. This will make transferring data between countries a lot easier and potentially more clear as it relates to GDPR and the related controls.”
GDPR has Shaped the Way Companies Now Talk About Consumer Privacy
Paul Trulove, CEO of SecureAuth
“Consumer privacy has been a huge concern since the dawn of the internet. Aside from the obvious security concerns, people started to realize that their personal information was a commodity that was being monetized and exploited by large corporations (sometimes of dubious integrity). GDPR was the first truly wide-reaching attempt to codify and enforce consumers’ (and employees’) rights to privacy.
When it launched, most companies were scratching their heads about how to comply – or even if they needed to comply. GDPR was seen as a significant barrier to doing business in the European Union, the United Kingdom, and other geographies that had adopted GDPR-style legislation.
However, over the last few years, GDPR has become a standard – and has changed the way companies talk about privacy. Impacting everything from policy and legal considerations to product design to operational processes. Thanks to GDPR, consumer and employee privacy protections have been normalized throughout the global corporate world.
Two factor authentication is not required but preferred for accessing systems that process personal data, per the guideline issued by ENISA — the European Union Agency for Network and Information Security — which advises member states and private sector organizations in implementing EU legislation. However, given the current state of multi factor authentication which can be easily breached, we highly recommend that the organization should leapfrog and move toward a tighter authentication with invisible MFA and eliminate passwords.”
CISOs should Know About all the Regulations that are Similar to GDPR
Alastair Parr, SVP of Global Products & Delivery, Prevalent Inc.
“As it celebrates its fifth year driving positive change, GDPR continues to impact the practice of third-party management with its treatment of privacy as a core requirement. To this end, privacy teams are operating in lockstep with procurement and information security teams, ensuring that GDPR obligations are specified and tracked throughout the third-party lifecycle. Accordingly, we expect businesses to become better at tracking non-conformities within their extended enterprises.
As well, we see that organizations are beginning to see data privacy obligations as a global expectation, not just a requirement of their EU operations. For example, CCPA, the DPA 2018, and PIPEDA all bear a strong similarity to GDPR, reinforcing the perception that it set the precedent for what good data protection practice looks like for consumers and businesses alike.”
GDPR Makes a Huge Impact on the Cybersecurity Activities within an Organization
Rick Hanson, President at Delinea
“I’ve been in the cyber community since the mid-90s, and one consistency over the years is that personal data has always been paramount. However, even though the industry often understood what needed to be done to protect personal data, it was frequently deemed to be too costly or complex to implement.
Five years ago, I applauded the EU for taking a stand and providing guidelines and a framework to ensure that personal data and privacy were protected with GDPR. Yet even as this legislation passed and privacy advocates celebrated, many businesses were very concerned due to perceived burdensome and costly efforts that would be required of them to be compliant. Looking back on this anniversary, I am very encouraged that the technology community has innovated and evolved to solve many of these issues and challenges quickly. My belief is that it sets a solid foundation that the rest of the world can follow as we continuously work to protect our personal data and privacy.
We have come a long way since the early days of cyber and GDPR makes a significant impact, yet it does not solve the cybersecurity threat. It offers a framework that helps classify and protect yet these policies are public, giving any attacker a roadmap on how to circumvent the policy. As good as GDPR policy is, it does not mean our personal data is completely secure. We must continue to educate and innovate to solve these ongoing data privacy and security challenges.”
Mobile Commerce Owes its Success and Disruptive Nature to GDPR
Ashish Patel, GM EMEA of mobile security company Zimperium
“On its 4th anniversary, the General Data Protection Regulation (GDPR) continues to play a significant role in enhancing mobile security. GDPR, which came into effect on May 25, 2018, has introduced essential protections and regulations for the handling of personal data in the European Union (EU).
One of the key contributions of GDPR to mobile security is the increased emphasis on user consent and transparency. Mobile applications now need to obtain explicit consent from users before collecting and processing their personal data. This has led to improved transparency regarding data collection practices and has empowered individuals to make informed decisions about sharing their information.
GDPR has also encouraged organizations to implement stronger security measures to protect personal data on mobile devices. It has prompted the development of privacy-enhancing features and secure data storage practices within mobile applications. Organizations are now required to implement privacy by design and default, ensuring that privacy and security are integral components of mobile app development.
Furthermore, GDPR has facilitated the establishment of stricter data breach notification requirements. In the event of a data breach, organizations are obligated to notify both the supervisory authority and affected individuals within a specific time-frame. This prompt notification enables individuals to take necessary precautions to protect themselves, such as changing passwords or monitoring their accounts for suspicious activities.
Overall, GDPR’s value on its 4th anniversary in the context of mobile security lies in its promotion of user consent, transparency, improved security measures, and timely data breach notifications. These provisions have undoubtedly strengthened mobile security and heightened user awareness regarding the protection of their personal data.”
Shadow Data Would Remain a Target for Cyber Attackers; GDPR Fines Imminent if Not Taken Seriously
Amit Shaked, CEO and co-founder, Laminar
“The E.U. ‘s decision to fine Meta for illegal data transfers from Europe to the U.S. signifies the severity of the consequences for mishandling data. While in this circumstance, Meta was aware of the data being shared, many organizations are in the dark regarding where their sensitive data resides and unknowingly breaking compliance regulations. This unknown or ‘shadow’ data is a concern for 93% of data security and governance professionals, and one of the No.1 targets for cyber adversaries because it is not governed nor under the same security structure as other data stores.
To avoid the heavy fines from compliance laws such as GDPR, HIPAA, CCPA and more, it’s critical that data and governance professionals have automated guardrails in place to identify sensitive data and verify policy is being followed. In our cloud-age which is defined by ephemeral networks and data democratization, organizations need to have the ability to quickly detect and remediate regulatory compliance violations, and be able to quickly generate audit-ready reports. Doing so can not only help them avoid fines, but also protect them from the financial and reputational damages of a breach.”
Why Organizations should Build a Robust Cyber-risk Management Strategy with GDPR at the Center
Chris Vaughan, VP Technical Account Management, EMEA, Tanium
“With more and more organizations holding sensitive information in cloud services, legislation like GDPR is critical to protecting this data from unwanted exposure and breaches. However, it’s a challenge for businesses grappling with a multitude of endpoints to meet the strict regulatory requirements within the law. In the rush to comply with privacy regulations, organizations tend to overspend on point solutions. What these organizations don’t realize is that the plethora of disparate point tools is actually putting their business at risk.
Another major roadblock to successful data compliance in today’s organizations is a lack of endpoint visibility, which is leaving data exposed and enterprises highly susceptible to breaches. Building a robust compliance strategy in line with GDPR regulations requires a crystal-clear picture of all assets within your environment, including deep visibility into endpoint file operations and endpoint network operations.
Ultimately, effective compliance and data privacy requires effective cyber risk management – identifying assets, risks and vulnerabilities across their environment and fixing them both with speed and at scale. On the other hand, poor cyber hygiene can cause misplaces or lost data and a lack of compliance within regulatory frameworks.
Without having a way to identify, manage and prioritize mis-configurations and vulnerabilities, adhering to legislation like GDPR can be a daunting and messy task, if not altogether impossible. And as digital cyber-citizens, every user now has the legal right to request personal information to be either returned or deleted, putting them back in control of their data.”
Next Five Years would be Crucial for All Data-driven Businesses
Jeff Reich, Executive Director at the Identity Defined Security Alliance (IDSA)
“The rock in the pond that is the GDPR continues to cause ripples that affect everything in the vicinity. Seven years after the GDPR was adopted, five years after enforcement began, it is difficult to not see the results of the regulation, to date.
Starting in the EU by law, behavior is spreading to other countries and jurisdictions. In the United States, any state or territory creating privacy regulations models them after the GDPR. Merchants and vendors know what they need to do, even when they do not know how to do it yet. The best behavior change is with consumers.
Although we have yet to complete the journey, more and more consumers are seeing the value of their identity and the security that protects the privacy of their identity. That may be the biggest long-term benefit.
I look forward to the next five years to see what changes continue to ripple across the pond.”


