In this context, CIOs and CISOs must take proactive steps to explore the readiness of their cryptographic systems and collaborate with solution providers to transition seamlessly into the post-quantum era. Understanding the urgency and long-term implications of this migration is critical to maintaining data security in the face of quantum advancements.
Also Read: Quantum Computing and IT Security: What Leaders Need to Know
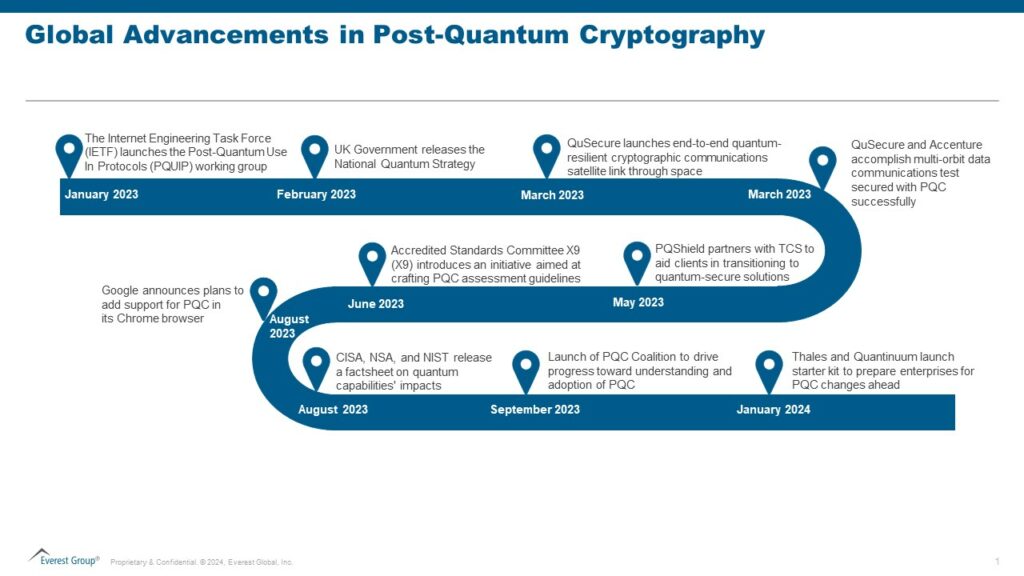
From Preparation to Action: Developing a Post-Quantum Cryptography Strategy
Transitioning to post-quantum cryptography (PQC) doesn’t have to be an all-at-once approach. Instead, it should be a carefully phased process, starting with board-level conversations involving the CISO, CIO, and CTO. These discussions should focus on building a long-term PQC strategy that integrates quantum-resistant algorithms into existing infrastructures while considering scalability, efficiency, cost, and risk management.
1. Implement a PQC Strategy:
The first step in developing a robust PQC strategy is acquiring the right expertise. With the rapid pace of developments in quantum computing, distinguishing between marketing hype and real advancements in quantum engineering is essential. Enterprises should follow industry best practices and stay informed through academic research and expert insights, such as Google’s Quantum Research, to make well-informed decisions. Keeping up with leading sources on PQC will provide valuable guidance on how to integrate new algorithms effectively.
2. Assess the Business Risk:
A comprehensive risk assessment should be conducted to identify critical data that is vulnerable to quantum attacks. Cryptographic systems are often embedded across multiple areas of an organization, safeguarding data at rest, in transit, and in use. It’s vital to create an inventory of these systems, classify sensitive data, and perform a thorough threat analysis to determine which parts of the infrastructure should be prioritized for PQC migration. Following examples like Google’s quantum threat analysis can help define the key areas that require immediate attention.
3. Analyze the Broader Risk:
Beyond cryptography, the adoption of PQC might necessitate significant changes across other systems. This could resemble the Y2K challenge, where the shift impacted everything from data formats to software architectures. Organizations should assess how PQC will affect interconnected systems and determine the potential need for broader modifications, such as adapting databases and applications to accommodate larger digital signatures or more complex algorithms.
4. Learn from the Past:
Looking back at how your organization handled previous cryptographic challenges can offer valuable insights. Consider organizing a tabletop exercise for leadership and board members to walk through the complexities of PQC migration. This proactive approach will help highlight past strategies that succeeded and identify gaps that need to be addressed. By learning from past cryptographic transitions and looking at industry leaders like Google, companies can better navigate the shift to quantum-resistant encryption.
Also Read: Navigating the Evolving Cyber Insurance Landscape: 7 Insights for CIOs
The Importance of Cryptographic Agility for CISOs and CIOs in the Quantum Era
As quantum computing continues to develop, the need for cryptographic agility becomes increasingly critical for organizations. With standards and technologies like quantum-safe virtual private networks (VPNs) already available, CISOs can begin migrating to post-quantum cryptography without waiting for updates to protocols such as TLS, which still face uncertain timelines.
The recent finalization of three quantum-resistant algorithms by NIST marks a significant milestone in preparing for the quantum era. These algorithms provide a foundation for securing sensitive information against the future capabilities of quantum computers, which could potentially break existing cryptographic protections. As a result, CISOs must take proactive steps to assess their current cryptographic methods and begin planning for a shift to quantum-resistant encryption.
A key element of preparation is the development of a cryptographic agility strategy. This involves identifying where critical data is stored, evaluating the current encryption in use, and ensuring that systems can transition smoothly to quantum-resistant algorithms when the time comes. The process of migrating to these new cryptographic standards will likely be complex and time-consuming, making early preparation essential for minimizing disruptions.
Furthermore, the NIST post-quantum standards extend beyond encryption, covering areas such as hashing and signatures, which are essential for verifying software integrity. This is especially important for long-lived hardware and software, which may continue to operate in environments where quantum computing poses a real threat to outdated cryptographic protections. As these systems may remain in use for years or even decades, implementing post-quantum cryptography early is crucial for ensuring long-term security.


