Cybersecurity has become the most important concern to think about with the growing threat rates in the industry. Knowing more about Distributed Denial of Service (DDoS) attacks is crucial for maintaining a strong defense. Understanding current threats and their evolution is vital for assessing your organization’s security posture and making informed decisions about your security providers.
DDoS attacks have grown significantly in terms of frequency, peak bandwidth, and complexity. No organization is immune to these increasingly sophisticated threats. Monitoring the latest trends in DDoS attacks is essential for anticipating potential risks and adapting your defensive strategies accordingly.
A recent attack reported by Cloudflare peaked at 71 million requests per second—a 54% increase from the previous year’s record. Originating from a network of over 30,000 IP addresses, this attack displayed unprecedented scale and coordination. This escalation in HTTP DDoS attack intensity highlights a troubling trend in evolving cyber threats.
Also Read: A Comprehensive Guide to DDoS Protection Strategies for Modern Enterprises
Surge in DDoS Attacks: A Closer Look at the Numbers
The first half of 2024 has seen a remarkable increase in Distributed Denial of Service (DDoS) attacks. The number of incidents surged by 46% compared to the same period in 2023, with 445,000 attacks recorded in Q2 2024 alone. This represents a 34% rise from the previous six months (Q3–Q4 2023), highlighting a significant escalation in DDoS activity.
Escalating Attack Power: A Growing Concern
DDoS attack power has also seen notable growth. The most potent attack in the first half of 2024 reached 1.7 terabits per second (Tbps), a slight increase from the 1.6 Tbps recorded in 2023. Although a 0.1 Tbps increase may seem modest, it indicates a concerning upward trend in attack scale. For context, 1 Tbps is equivalent to over 212,000 high-definition video streams being transmitted simultaneously. As Andrey Slastenov, Head of Security Department at Gcore, explains, “A 300 Gbps attack can bring an unprotected server offline in seconds. Any rise in attack potency, no matter how small, can have serious repercussions.”
DDoS: A Persistent Threat
Distributed Denial-of-Service (DDoS) attacks have evolved from being minor irritations to becoming highly sophisticated threats that present significant challenges for businesses and organizations. The continuous advancement in DDoS detection systems and techniques has been essential in addressing these cyber threats. To understand the current landscape and anticipate future developments, let us review the progression of DDoS detection from its origins to the present day and look ahead to emerging trends in the field.
Why DDoS Attacks Remain a Persistent Threat
Distributed Denial-of-Service (DDoS) attacks present ongoing challenges for businesses due to their extensive and multifaceted impacts. The following are key reasons why DDoS attacks continue to be a significant threat:
- Revenue Loss: Downtime resulting from DDoS attacks can have severe financial implications. The cost of downtime varies significantly across different sectors. For instance, Veeam software estimates that an hour of downtime for a high-priority application costs around $67,651, while the cost for a normal application is slightly lower at $61,642. This underscores that every minute of downtime can be financially detrimental, regardless of the application’s priority level. For additional context, refer to Statistica’s 2019 report on the growing cost of enterprise server downtime.
- Lost Productivity: DDoS attacks that degrade or disrupt business applications and services can severely impact employee productivity. The shift towards remote work, accelerated by the COVID-19 pandemic, has heightened dependence on reliable connectivity. Consequently, downtime not only affects operational efficiency but also incurs significant costs related to lost productivity. CISOs should account for these costs when evaluating the overall impact of a DDoS attack.
- Remediation Costs: The aftermath of a DDoS attack often involves substantial remediation efforts, which can lead to increased labor costs, including overtime and external consultancy fees. Beyond IT staff, the broader impact includes potential damage to public relations and customer support teams overwhelmed by an influx of complaints and queries.
- Damage to Brand Reputation: Industries such as gaming, hosting, data centers, and financial services are heavily reliant on their reputation for reliability. A disruption in service availability can erode customer trust and damage the company’s reputation. In a competitive market, maintaining a positive reputation is critical for customer acquisition and retention.
- Loss of Market Share: Persistent DDoS attacks can lead to customer churn, as users may seek more reliable alternatives if they experience frequent service interruptions or latency issues. The inability to provide consistent service can directly impact a company’s market share and revenue.
- Ransom Costs: In recent years, DDoS attacks have increasingly been paired with ransom demands. Attackers may threaten to launch a DDoS attack alongside a ransomware attack unless a substantial ransom is paid. While paying a ransom is generally discouraged, some organizations have chosen to do so to regain control of their systems. Notable instances include the Colonial Pipeline attack, where the company paid $5 million in ransom, and the recent incident with Ireland’s Health Service Executive, where DDoS attacks were used as a precursor to ransomware deployment.
Also Read: Why Secure Collaboration is Critical for an Effective Cybersecurity Incident Response
DDoS Attack Trends to Know About
2024 Q2 DDoS Attack Statistics: A Detailed Breakdown
In the second quarter of 2024, a total of 4 million DDoS attacks were recorded, comprising 2.2 million network-layer attacks and 1.8 million HTTP DDoS attacks. However, this 1.8 million figure has been adjusted to account for the rise in sophisticated and randomized HTTP DDoS attacks. Our automated mitigation systems generate real-time fingerprints for these attacks. Due to the randomization in these sophisticated attacks, many fingerprints were produced for individual attacks, resulting in a total of approximately 19 million fingerprints—over ten times the normalized figure of 1.8 million.
The large discrepancy highlights the significant shift in the threat landscape. Tools and capabilities previously reserved for state-level or state-sponsored actors are now accessible to common cybercriminals. This shift has been accelerated by advancements in generative AI and autopilot systems, which enable faster and more effective code development, enhancing the sophistication and scale of attacks.
Ransom DDoS Attacks: Trends and Insights
In May 2024, the proportion of only Cloudflare customers reporting threats or actual ransom DDoS attacks surged to 16%, marking the highest level in the past year. The quarter began with a lower figure of 7%, but this increased sharply to 16% in May before slightly decreasing to 14% in June.
Overall, ransom DDoS attacks have been on the rise throughout the past year. In Q2 2024, 12.3% of customers reported being targeted or extorted, up from 10.2% in the previous quarter and consistent with the 12.0% reported a year earlier.
Regarding the origins of these attacks, 75% of respondents were unsure about the attackers’ identity or motives. Of those who did have insights, 59% identified competitors as the culprits, 21% pointed to disgruntled customers or users, and 17% attributed the attacks to state-level or state-sponsored actors. The remaining 3% suspected the attacks were self-inflicted.
Global DDoS Attack Analysis
In the second quarter of 2024, China emerged as the most targeted country for DDoS attacks globally. This ranking accounts for both HTTP and network-layer DDoS attacks, the overall attack volume, and the proportion of DDoS traffic relative to total traffic. The accompanying graphs illustrate this data, with longer bars indicating higher levels of attack activity.
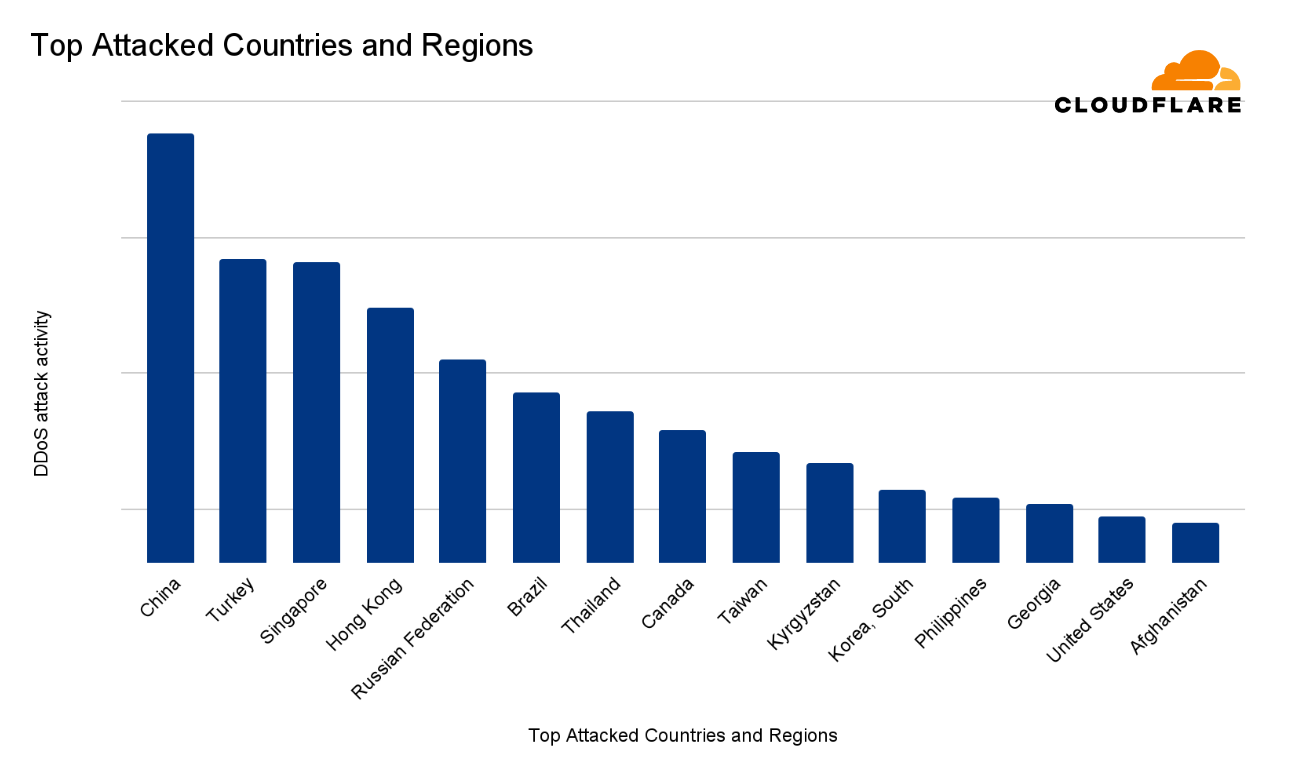
Following China, Turkey ranked second, with Singapore, Hong Kong, and Russia also experiencing significant DDoS activity. Brazil and Thailand rounded out the top seven. The chart below provides a detailed breakdown of the top 15 most attacked countries and regions, showcasing the distribution of attack intensity globally.
Industry Analysis
the Information Technology & Services sector was the most targeted industry for DDoS attacks. This ranking reflects both HTTP and network-layer DDoS attack volumes and the proportion of attack traffic relative to total traffic, following the same methodologies as previously described.
The Telecommunications, Service Providers, and Carrier sectors ranked second, while the Consumer Goods industry came in third.
Top Industries for HTTP DDoS Attacks
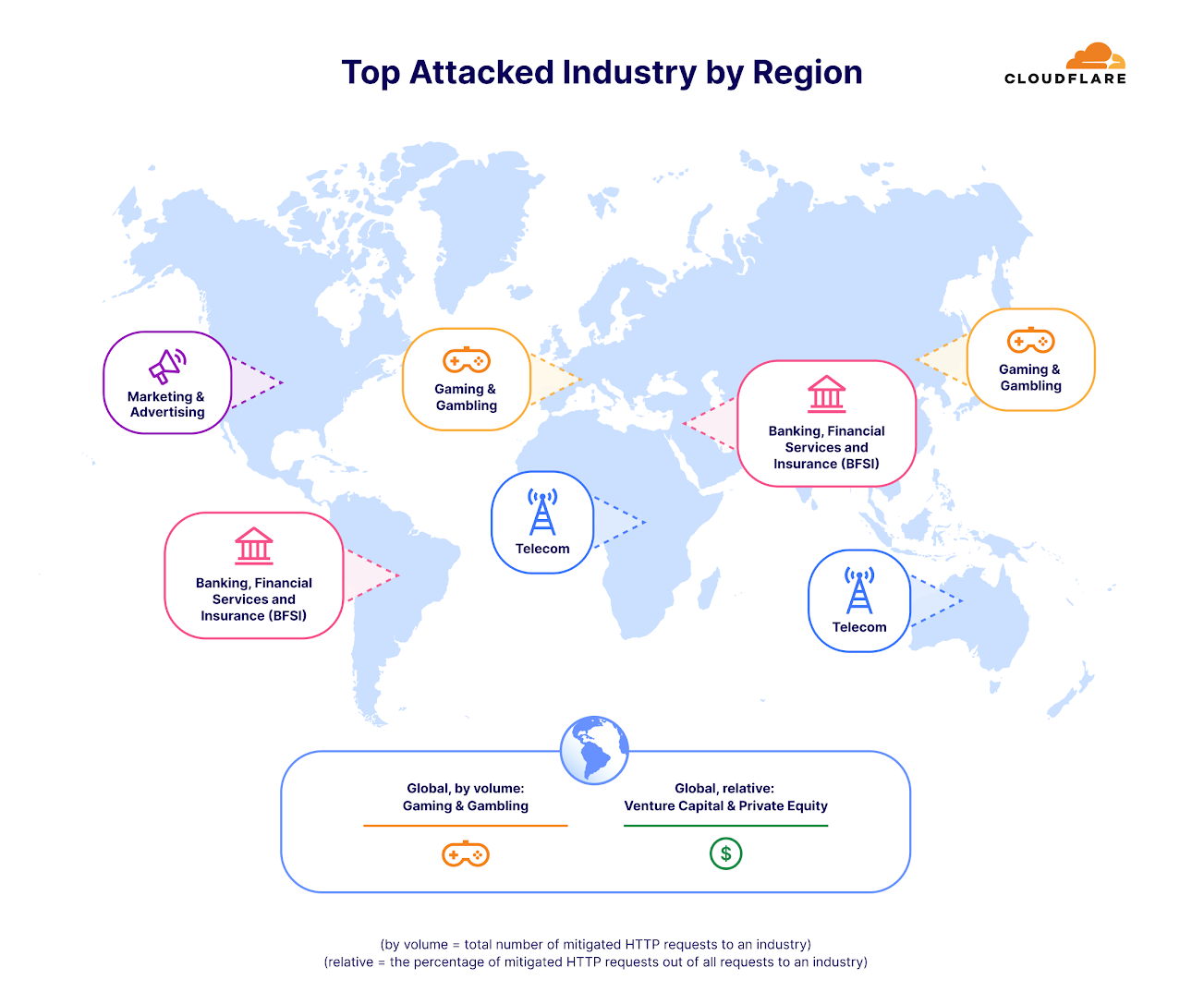
When focusing solely on HTTP DDoS attacks, the Gaming and Gambling sector emerged as the most affected, with the highest volume of attack requests. The regional breakdown of these attacks is detailed in the chart below.
Preparing for the Future
As we reflect on the DDoS attack trends of 2023 and anticipate the challenges of 2024, it is clear that vigilance and preparedness are essential. Organizations and individuals alike must adopt comprehensive and proactive strategies to mitigate the risks posed by these evolving threats.
Key Strategies for Enhancing DDoS Defenses
- Implement Multi-CDN Strategies – Multi-CDN (Content Delivery Network) strategies are increasingly crucial for safeguarding web-based services against DDoS attacks. By distributing web traffic across multiple CDNs, organizations can enhance both performance and security. This approach not only improves load times and global accessibility but also strengthens resilience against large-scale attacks. Spreading traffic across various CDNs reduces the risk of a single point of failure and enhances the overall capacity to absorb and mitigate DDoS threats.
- Utilize Enhanced Detection Systems – Advanced detection systems are vital for identifying and responding to DDoS threats with greater efficacy. These systems leverage sophisticated algorithms and, in some cases, artificial intelligence (AI) and machine learning to detect unusual traffic patterns and potential threats. Early detection enables swift responses to secure networks and protect assets. Incorporating enhanced detection systems into a layered cybersecurity strategy is crucial for minimizing the impact of DDoS attacks.
- Conduct Regular Security Audits and Updates – Regular security audits and updates are fundamental to maintaining a robust defense against DDoS attacks. Routine audits help identify system vulnerabilities before they can be exploited, allowing for timely improvements to security measures. Keeping software and systems updated with the latest security patches is essential for addressing emerging threats and minimizing the risk of breaches. This proactive approach is integral to sustaining strong defenses against evolving cyber threats.
- Engage in Community Collaboration and Intelligence Sharing – Participation in cybersecurity communities and intelligence-sharing networks is an effective way to enhance defenses against DDoS attacks. By exchanging information about threat patterns, attack methods, and effective countermeasures, organizations can collectively strengthen their security postures. Collaborative efforts and shared insights help build a comprehensive understanding of emerging threats and foster a unified response to cyber challenges. This community approach makes it more difficult for attackers to exploit known vulnerabilities and reinforces collective cybersecurity efforts.
Also Read: CIO Influence Interview with Jimmy Xu, Field CTO at Cycode
The surge in DDoS attacks was notable across various industries and regions, with a significant uptick in incidents linked to geopolitical events throughout the year. Sectors such as Banking, Software and Computer Services, and Telecommunications experienced particularly sharp increases in malicious activities compared to the previous year. On average, businesses now face approximately eleven DDoS attacks annually, equating to nearly one attack per month. The focus of attackers has shifted from merely maximizing bandwidth to employing smaller, more frequent micro and mini DDoS attacks. While large-scale volumetric attacks continue to be a straightforward method for causing disruption, these smaller attacks present a more complex challenge.
[To share your insights with us as part of editorial or sponsored content, please write to psen@itechseries.com]


