The modern cybersecurity landscape presents enterprises with increasingly sophisticated threats, among which Advanced Persistent Threats (APTs) stand out as particularly dangerous. APTs are complex, sustained cyberattacks often targeting sectors including healthcare, telecommunications, and finance. These threats are distinguished by their persistence and ability to infiltrate networks over extended periods, causing significant financial and data-related damages.
This article explores the key characteristics of APTs, the tactics used—such as spear phishing and malware—and their potential impact on business security. It will also provide actionable strategies for mitigating APTs, including enhancing network defenses, educating employees, and learning from real-world examples of previous attacks.
Also Read: CIO Influence Interview with Jimmy Xu, Field CTO at Cycode
What are Advanced Persistent Threats?
An Advanced Persistent Threat (APT) is a prolonged cyberattack wherein an attacker gains and maintains an undetected presence within a network to steal sensitive data over an extended period. Unlike traditional attacks, APTs are meticulously planned and tailored to bypass existing security measures and remain covert.
APTs involve a higher level of customization and sophistication, typically executed by well-funded and experienced cybercriminal teams. These adversaries invest considerable time and resources in researching and identifying vulnerabilities specific to high-value organizations.
The Three Stages of an APT Attack
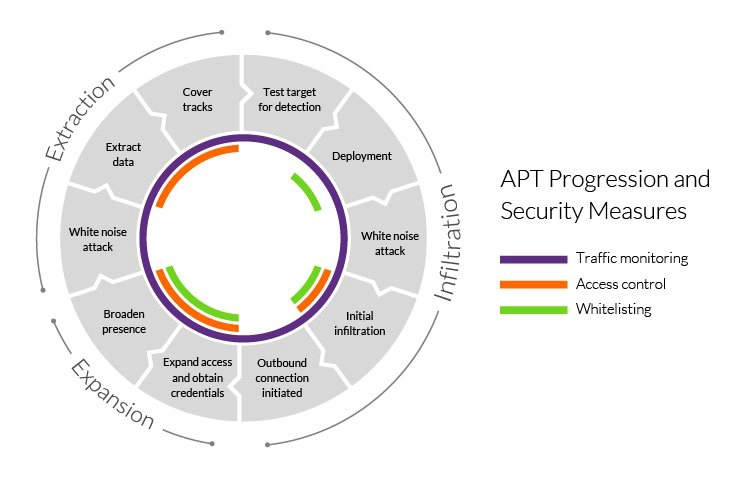
To effectively prevent, detect, and mitigate an Advanced Persistent Threat (APT), it is essential to understand its typical lifecycle. APTs generally follow a consistent pattern: infiltrating the network, expanding their access, and ultimately achieving their primary goal, which is often data theft.
Stage 1: Infiltration
The initial phase of an APT involves gaining access to the network, frequently through sophisticated social engineering tactics. A common method is spear-phishing, where attackers send targeted emails to high-level individuals, such as executives or IT leaders, often leveraging information from previously compromised team members. These emails may appear legitimate, referencing ongoing projects or familiar contacts. If multiple executives report falling victim to such spear-phishing attempts, it may indicate the presence of an APT.
Stage 2: Escalation and Lateral Movement
Once the attackers secure initial access, they proceed to the second phase, which involves expanding their foothold within the network. They deploy malware to move laterally, mapping out the network and gathering credentials like usernames and passwords to access critical business information. During this phase, attackers may also create a “backdoor” to facilitate future access, and establish multiple entry points to ensure persistence even if some are detected and closed.
Stage 3: Exfiltration
In the final phase, cybercriminals accumulate stolen data in a secure location within the network before extracting it. They may employ tactics such as a denial-of-service (DoS) attack to divert the attention of security personnel, allowing them to exfiltrate the data discreetly. The network remains compromised, potentially allowing attackers to return and exploit the system again.
Security Measures for Enterprises
Effective detection and protection against Advanced Persistent Threats (APTs) require a comprehensive approach involving network administrators, security providers, and individual users. Here are key measures to enhance APT defenses:
Traffic Analysis and Monitoring
Monitoring both ingress and egress traffic is crucial for preventing backdoor installations and blocking data exfiltration. Regular inspection of internal network traffic can alert security teams to unusual activities indicative of malicious behavior.
Deploying a Web Application Firewall (WAF) at the network edge can protect your web application servers by filtering traffic and mitigating application layer attacks such as Remote File Inclusion (RFI) and SQL injection, which are commonly used during the APT infiltration phase.
Internal network firewalls and traffic monitoring tools provide insights into user interactions within the network and can help identify abnormalities like irregular logins or large data transfers, which may signal an APT. Monitoring file share access and system honeypots can also aid in detecting potential threats.
Incoming traffic monitoring services are valuable for identifying and removing backdoor shells by intercepting remote requests from attackers.
Application and Domain Whitelisting
Whitelisting controls the domains accessible from your network and the applications users can install, reducing the attack surface available to APTs. Although effective, this measure is not foolproof, as trusted domains can be compromised and malicious files can masquerade as legitimate software.
To enhance whitelisting effectiveness, enforce strict update policies to ensure all applications are running their latest versions, mitigating the risk from outdated or vulnerable software.
Access Management
Employees often represent a significant vulnerability within your security perimeter, making effective access control essential. Potential risks include:
- Negligent Users: Employees who disregard security policies and inadvertently expose the network to threats.
- Malicious Insiders: Individuals who intentionally misuse their credentials to facilitate unauthorized access.
- Compromised Accounts: Users whose credentials have been stolen and exploited by attackers.
Implementing robust access controls involves assessing data access on a need-to-know basis, reducing the risk of credential misuse. Secure key network access points with Two-Factor Authentication (2FA), which requires users to provide a second form of verification, such as a passcode sent to their mobile device, to prevent unauthorized access and lateral movement within the network.
Also Read: Scanning with Caution: Understanding the Threat of QR Code Phishing
Advanced Persistent Threat Examples
GhostNet
GhostNet is an enduring APT known in the IT world. GhostNet was first identified in March 2009. Its control infrastructure was predominantly traced to China, with attacks targeting the Tibetan community, though the Chinese government has denied involvement.
The GhostNet attacks were executed through spear-phishing emails containing malicious attachments. These files deployed a Trojan horse, allowing remote command and control systems to execute commands and download further malware, thereby gaining full control over the compromised systems. The malware had capabilities to utilize audio and video recording devices to monitor the locations housing the affected computers. GhostNet successfully infiltrated political, economic, and media targets across approximately 103 countries, including the embassies of India, South Korea, Indonesia, and Romania.
Deep Panda
Deep Panda, also known as KungFu Kittens or APT12, is a Chinese state-sponsored cyber intrusion group targeting critical sectors such as government, defense, legal, financial, and telecommunications for espionage purposes. According to CrowdStrike, the group’s operations are highly sophisticated and representative of advanced cyber espionage activities.
The group’s primary aim is to maintain and monetize access to compromised environments. Deep Panda is among several hacking groups accused by Western cybersecurity organizations of breaching networks in the United States and other countries to steal sensitive government and defense documents.
Helix Kitten
Helix Kitten, believed to be an Iran-based adversary group, has been active since 2014. Its primary targets include organizations in aerospace, energy, financial, government, hospitality, and telecommunications sectors, predominantly in the Middle East. This group employs highly crafted spear-phishing messages, tailored specifically to the targeted users.
Technically, Helix Kitten is frequently associated with a custom PowerShell implant known as Helminth. This implant is typically delivered through macro-enabled Microsoft Excel files that require user interaction to execute an obfuscated Visual Basic Script. The group’s approach is notably multi-faceted: it involves frequent modifications, new malware downloads, and sophisticated memory manipulation techniques.
Advanced Threat Protection Tools
CrowdStrike
ESET
Palo Alto Networks
Trend Micro
SentinelOne
Sophos
WatchGuard
The Impact of APTs on Business Security
Advanced Persistent Threats (APTs) pose significant risks to business security, resulting in financial losses, intellectual property theft, and breaches of sensitive data, such as payment card information. These threats are often orchestrated by nation-states engaged in cyber and industrial espionage, targeting critical infrastructure and valuable business assets.
Financial Loss and Reputational Damage
APTs can lead to considerable financial losses for targeted organizations, with cybercriminal groups like APT8, a China-based threat actor known for its sophisticated cyber espionage activities, being a prominent example. The financial repercussions of an APT attack extend beyond immediate monetary damage to include reputational harm, regulatory fines, and the costs associated with forensic investigations. APT8, with its advanced tactics and state-sponsored backing, represents a serious threat to sectors such as finance, technology, and healthcare. Legal actions against these criminals can be complex due to their international operations, often requiring cross-border cooperation among law enforcement agencies. To mitigate financial risks, organizations must invest in robust cybersecurity measures, including regular security audits, comprehensive employee training, and well-prepared incident response strategies.
Data Breaches and Intellectual Property Theft
APT campaigns frequently lead to data breaches and theft of intellectual property. Threat actors like APT28, also known as FANCY BEAR, use tactics such as spear phishing to gain unauthorized access to valuable data. These breaches can have severe consequences for national assets and the confidentiality of sensitive business information. Cyber espionage groups like APT28 exploit network vulnerabilities to extract confidential information through meticulously crafted phishing emails. The theft of intellectual property not only threatens individual companies but also national security. To counter these risks, organizations should implement robust cybersecurity measures, including regular security assessments, employee training on phishing recognition, and multi-factor authentication protocols.
Strategies for Preventing and Mitigating APT Attacks
Addressing APT attacks requires a multi-faceted approach encompassing robust detection mechanisms, proactive prevention measures, strategic defenses, and the use of advanced tools and threat intelligence. Continuous monitoring, effective access control mechanisms, and two-factor authentication are critical components of an APT defense strategy.
Best Practices for Network and Data Security
Implementing best practices for network and data security is essential in protecting against APT threats. Utilizing solutions like APT security with Perception Point helps network administrators deploy effective security measures, identify vulnerabilities, and enhance overall cybersecurity resilience. Regular updates to security protocols, security assessments, and multi-factor authentication are vital to fortifying defenses. Advanced cybersecurity tools, such as intrusion detection systems and endpoint protection platforms, can further strengthen security posture and reduce the risk of data breaches.
Final Thoughts
Companies be they large or small are recognizing APT’s consequences, living in denial is not an option now. A successful APT attack can lead to loss of sensitive data which reflects in financial losses, reputational damage, and more violations.
In addition, recent trends show that attackers are leveraging AI and machine learning to automate tasks, improve evasion tactics, and identify attack vectors more effectively. The expansion of the Internet of Things (IoT) has also broadened the attack surface, complicating efforts to monitor and detect suspicious behavior. With the growing digital world, it is more important to understand to stay informed about the evolving threats and remain prepared well in advance with cybersecurity measures. This will help organizations aiming to protect their assets and maintain trust with their stakeholders.
[To share your insights with us as part of editorial or sponsored content, please write to psen@itechseries.com]


