With the proliferation of cyberattacks, there is a growing demand for strong cybersecurity strategies. Core to any effective security plan is the need for detection and response, which will counter threats that have been able to bypass traditional security controls.
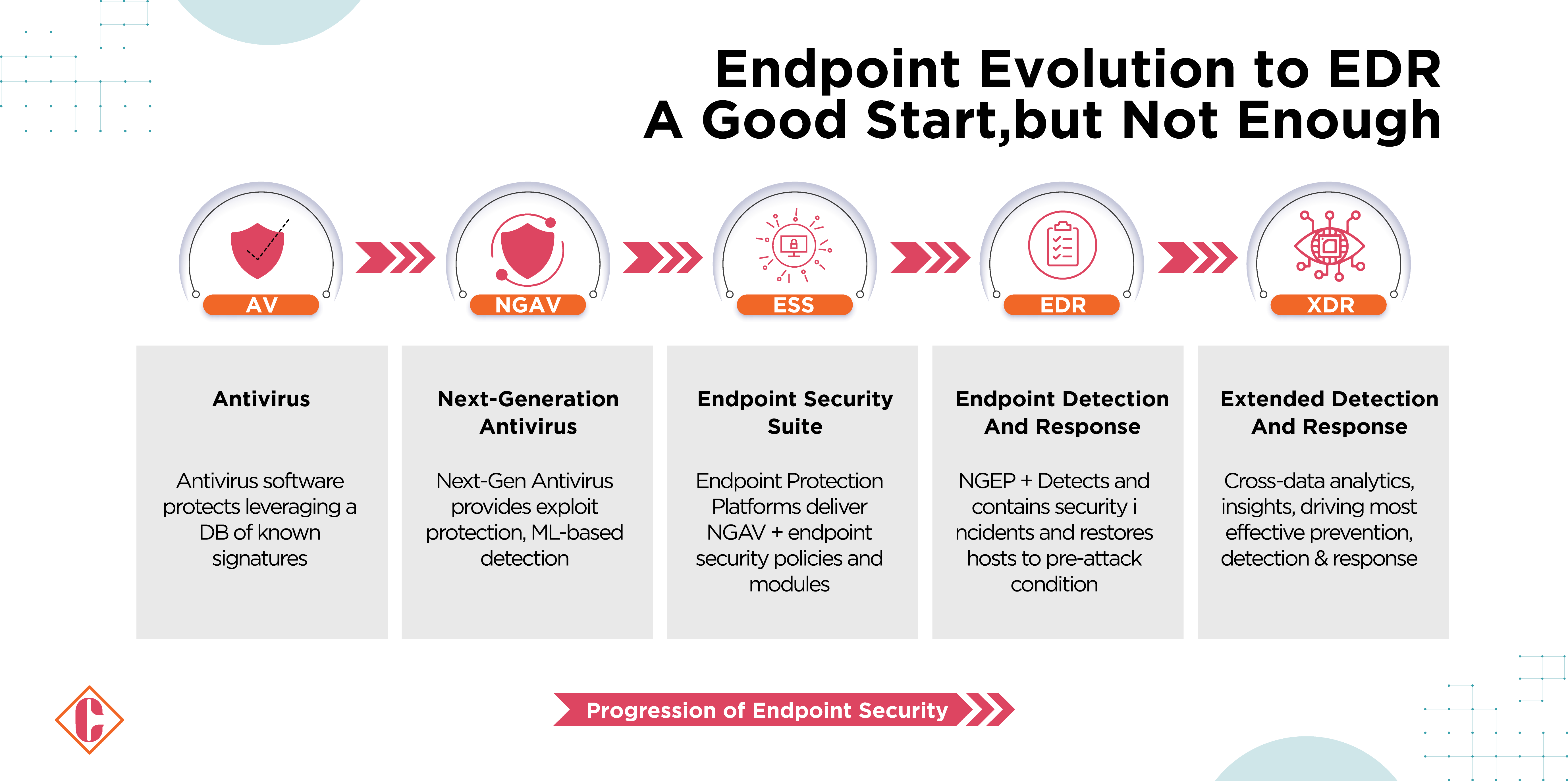
Traditional antivirus software, once used to be the frontline option, has been overcome by the complexity of today’s cyberattacks. This transition has given rise to Endpoint Detection and Response (EDR) and Extended Detection and Response solutions (XDR), representing a fundamental change in cybersecurity strategies. While EDR focuses on threat detection and neutralization at an endpoint level, XDR provides an integrated approach, ranging from endpoints to network and cloud environment, which furnishes defense against diversified cyber threats.
Forrester defines XDRas: The evolution of EDR,which optimizes threatdetection, investigation, response, and hunting in real time. XDR unifies security-relevant endpoint detections with telemetry from security and business tools, such as NAV, email security, identity and access management (IAM), cloud security, and more. It is a cloud-native platform built on big data infrastructure to provide security teams with flexibility, scalability, and opportunities for automation.
What is EDR?
EDR stands for Endpoint Detection and Response. These solutions provide protection for corporate endpoints. They offer multi-layer, fully integrated endpoint protection. With this solution, the enterprise can get constant real-time monitoring with data analytics to detect threats and automated responses to mitigate detected threats.
Key features of EDR solution:
- Endpoint monitoring and event recording
- Data search, investigation and threat hunting
- Alert or suspicious activity validation
- Suspicious activity detection
- Data analysis
- Actionable intelligence to support response
- Remediation
What is XDR?
XDR stands for Extended Detection and Response, designed to simplify network security management. XDR solutions bring about seamless security visibility across an organization’s entire infrastructure, including endpoints, cloud systems, mobile devices, and more. This integrated view simplifies security management and guarantees that policies are applied uniformly across the organization.
According to Gartner, XDR is “a comprehensive, cloud-native, and analytics-driven security offering that combines multiple security products.”
Key features of XDR solution:
- Diverse, multi-domain security telemetry
- Threat-focused event analysis
- Threat detection and prioritization of data fidelity
- Data search, investigation and threat hunting across multi-domain telemetry
- Response to mitigate and remediate the threat
Step-by-step Breakdown of How EDR Works
- Continuous Visibility: EDR maintains continuous, real-time visibility into endpoint activity by employing predefined and observed baselines of normal behavior.
- Automatic Detection: Using predefined security logic, EDR automatically traces, identifies, and responds to suspicious activity on endpoints.
- Customizable Response: Users have the flexibility to determine how the EDR platform manages potential threats according to their preferences and security policies.
- Alert Generation: Upon detecting suspicious behavior, EDR platforms generate alerts and notify specific stakeholders about the potential threat.
- Automated Response: EDR platforms can initiate automated responses to potential threats, such as restricting activity, removing the threat, and repairing damages.
- Limited Scope: While EDR platforms can automatically respond to threats, their response scope is limited. Human intervention is often required to address gaps in the automated response process.
- Example Scenario: Upon detecting a threat, the EDR platform sends an alert and automatically isolates all affected endpoints. However, human intervention is necessary to determine the next steps in mitigating the threat and investigating the breach.
- Data Analysis: Data analysts utilize the information collected by the EDR platform to investigate the threat, understand the breach’s origin, and assess the extent of any additional damage.
- Network Protection: It’s essential to note that EDR platforms focus on endpoint security and do not provide comprehensive network protection. They complement traditional antivirus (AV) software by filling gaps in endpoint visibility and employing behavioral analysis to recognize emerging threats.
- Supplementary Role: EDR can be utilized as part of an overall security strategy to enhance endpoint security and strengthen defenses against cyber threats.
Step-by-Step Guide on How XDR Works
- Comprehensive Protection: XDR technology utilizes various methods to safeguard all network vectors, including cloud applications, endpoints, SaaS providers, and more.
- Integration of Security Tools: XDR integrates multiple types of detection across various security points into a single, all-encompassing platform. This platform provides centralized access to various security tools, such as EDR, CASB, IAM, secure web gateways, network IPS, network firewalls, and unified threat management.
- Diverse Protection Approach: XDR is not a singular tool with defined parameters; instead, it offers diverse protection by automatically collecting and correlating data from multiple components within the network.
- Detection and Response Capabilities: XDR technology can detect and respond to threats across multiple network components. While SIEM (Security Information and Event Management) centralizes information, XDR centralizes security tooling, enabling a more comprehensive approach to threat detection and response.
- Similar Functionality to EDR: XDR provides similar functionality to Endpoint Detection and Response (EDR), including generating alerts, providing data to support human investigations, and implementing automated threat responses.
Also Read: Akamai Set to Acquire Noname; Eyes Application and API Security Marketplace for All Environments
Similarities between EDR and XDR
While the scope and focus of EDR and XDR are different, they have security information and event management capabilities:
- Threat Detection: EDR and XDR solutions provide organizations with adaptive cyberthreat detection capabilities vital for detecting advanced cyber threats.
- Incident Response: Both EDR and XDR solutions are designed to respond in real-time to detected cyber threats, thus enabling teams to reduce dwell time and potential damages.
- Real-time Monitoring: As different as the reach of their protection might be, both EDR and XDR solutions monitor system activity and behaviors uninterruptedly. This enables them to identify cyber threats in real time.
- AI and Machine Learning: EDR and XDR solutions use generative AI to empower their real-time cyber threat detection and response capabilities. These cybersecurity systems leverage AI and machine learning models to analyze system behaviors and respond effectively to emerging threats.
EDR vs XDR
Scope of Detection: EDR systems monitor your business infrastructure devices and offer protection.
XDR solutions broaden the horizon for detecting cyber threats, adding more layers of your security stack, like applications and Internet of Things devices.
Data Collection: One major difference is the sources of compatible data. EDR relies solely on data sourced from endpoint devices,
while XDR can collect data from various components across the whole security infrastructure.
Automated Incident Response: EDR solutions provide incident response automation capabilities for your organization’s endpoints. This includes identifying suspicious behavior or isolating a device.
XDR solutions extend incident response automation capabilities across the whole of your security stack.
Scalability and Adaptability: XDR systems are more scalable and adaptable than EDR systems because they can interface with several layers of your security stack.
Such flexibility will allow XDR solutions to mix in with the complex security requirements of your organization.
The Significance of EDR and XDR in Cybersecurity
EDR and XDR in today’s cybersecurity environment are indispensable tools for hardening an organization’s defenses against mounting cyber threats and a successful defense against cyber attacks.
- Threat Detection and Response: EDR and XDR solutions play a very vital role in detecting and responding to security threats. EDR provides fine-grained visibility and control of endpoints; thus, threats can be identified at a fast pace and responded to with action. On the other hand, XDR provides holistic visibility across different security domains, thus providing broad threat detection and response capabilities.
- Improving Incident Response: EDR solutions provide deeper insight into security incidents, therefore allowing fast investigation and response. On the other hand, XDR solutions automate incident response workflows in order to speed up and be more effective in responding to security incidents.
- Risk Mitigation: Continuous monitoring and detection features in both EDR and XDR solutions ensure that threats are intercepted before they can bring about significant damage. This proactively helps minimize the consequences of a security incident and lowers the chances of successful cyberattacks.
- Increased Visibility: By aggregating and analyzing security data from different sources, these solutions enable security teams to have a better understanding of their organization’s security posture. This increased visibility allows them to identify areas for improvement and make informed investment decisions regarding security.
 Top EDR/XDR Tools
Top EDR/XDR Tools
#1 Darktrace
Darktrace offers lifecycle protection across the entire business. Its cyber AI tool integrates seamlessly with existing solutions to provide superior threat detection capabilities.
Key Offerings:
- Helps discover unpredictable cyber threats across corporate networks.
- Protect cloud applications and remote endpoints to enhance zero-trust policies.
- With its self-learning AI, it learns everything regardless of whether technology is old or complex, which makes it simplified in predicting threats.
Discover how Darktrace’s game-changing technology can protect your organization from developing cyber threats. Download the State of AI Cyber Security Report 2024 now to learn more about the growing role of AI in cybersecurity.
#2 Vectra
Vectra an AI platform that offers hybrid attack surface visibility across identity, public, cloud, SaaS, data center networks and endpoint with XDR integration. Its innovative platform, fortified by patented Attack Signal Intelligence empowers security teams to swiftly prioritize, investigate, and counteract the most sophisticated cyber threats within their hybrid environments. With an impressive portfolio boasting 35 patents in AI-driven threat detection, Vectra AI stands as the most referenced vendor by MITRE D3FEND.
Vectra offers:
- Native hybrid cloud visibility
- Real-time attack signal intelligence
- Integrated managed response
#3 CrowdStrike
Crowdstrike Falcon is a cybersecurity solution provider and a leader in endpoint security. Falcon software provides comprehensive antivirus, threat intelligence, threat hunting, EDR and incident response. In addition, the platform includes:
- Establishment of third-party partnerships with CrowdStrike’s Technology Alliance partners.
- Introduction of an interactive graph illustrating cross-domain attack patterns.
- Implementation of behavioral analytics.
- Integration of pipeline for CI/CD.
Key offerings:
- Detect and defeat the adversary
- Accelerated Investigations with AI
- Automated Rapid Response
Advantages:
- MDR solutions significantly benefit smaller teams lacking a robust, dedicated security team.
- Consistent and robust platform performance across all areas.
#4 LogRhythm
LogRhythm offers the LogRhythm XDR Stack, a comprehensive suite of individual products designed to empower enterprises with unparalleled threat detection and response capabilities across their entire infrastructure:
- AnalytiX: AnalytiX solution facilitates flexible collection and centralization of diverse log and machine data. It delivers analytics-driven insights into IT, OT, and business operations, ensuring comprehensive visibility and understanding.
- DetectX: With DetectX, enterprises benefit from centralized analysis of all collected data. This data is contextually enriched with threat and risk intelligence, enabling proactive monitoring and detection of various security threats. DetectX leverages both out-of-the-box content and custom analytics to enhance threat detection capabilities.
- RespondX: RespondX equips teams with workflow orchestration and automation tools for swift investigation, mitigation, and response to any detected threat or incident. With RespondX, organizations can effectively address security threats and incidents across their expansive IT and OT landscapes, ensuring rapid and coordinated responses.
#5 Trend Micro
Trend Micro is a global cybersecurity company that offers a robust security platform. Trend Micro Vision One is a unified XDR platform that collects and correlates data across various security layers, including:
- Endpoints
- Servers
- Cloud Workloads
- Network
This comprehensive data collection allows for the following:
- Faster Threat Detection: By analyzing data from all these sources, Vision One can identify threats that siloed security solutions might miss.
- Improved Investigation and Response: Security analysts can investigate threats from a single platform, streamlining the process and enabling quicker response times.
- Reduced Silos: Vision One breaks down data silos, providing a holistic view of the security landscape.
Benefits of Trend Micro XDR/EDR Solutions:
- Centralized Management: Manage EDR and XDR functionalities from a single platform, simplifying security operations.
- Advanced Threat Detection: Leverage Trend Micro’s threat intelligence and machine learning to identify sophisticated threats.
- Improved Security Posture: Gain a comprehensive view of your security landscape and proactively address potential vulnerabilities.
- Scalability: Trend Micro solutions can scale to meet the needs of organizations of all sizes.
#6 Check Point Software
Check Point Software Technologies is a cyber security solution provider dedicated to protecting corporate enterprises and governments globally.
Check Point Infinity Platform provides innovative solutions to defend against sophisticated cyber attacks. It is AI-powered and cloud-delivered, providing enterprise-grade security across the data center, network, cloud, branch office and remote users with unified management. Its portfolio includes:
- Check Point Harmony
- Cloud Gaurd
- Quantum
- AI services
- Managed and Professional services
#7 Trellix
Trellix is redefining the future of cybersecurity with its open and native extended detection and response (XDR) platform. The company helps organizations mitigate or combat threats and gain confidence in the protection and resilience of their operations.
Trellix Helix Connect specializes in making visibility easier and analysis better through deep ingestion of data from native Trellix security controls across endpoint, network, data, and cloud security. Our next-generation XDR—Extended Detection and Response—solution scales efficiently with over 1 billion sensors to deliver multivector detection capability.
Product Features
- Seamlessly ingest data from a wide array of sources
- Identifies and understands the complete story of an attack rapidly
- Investigates and responds with confidence
#8 Palo Alto Networks (Prisma Cloud)
Prisma Cloud by Palo Alto Networks is the leader in cloud-native security, delivering the industry’s most complete security and compliance coverage across applications, data, and the full cloud-native technology stack. Our platform spans the entire development lifecycle, catering to multi-cloud and hybrid deployments with unrivaled efficiency.
 With Prisma Cloud’s integrated approach, security operations and DevOps teams collaborate seamlessly and become more agile while maintaining rigorous security measures. We empower organizations to accelerate cloud-native application development and deployment securely to navigate modern cloud complexities with confidence.
With Prisma Cloud’s integrated approach, security operations and DevOps teams collaborate seamlessly and become more agile while maintaining rigorous security measures. We empower organizations to accelerate cloud-native application development and deployment securely to navigate modern cloud complexities with confidence.
Secure it all with Prisma Cloud:
Prisma Cloud is the Code to Cloud platform that secures applications from design to runtime, offering unmatched security at every stage of the application lifecycle.
- Code: Ship secure code by design with Prisma Cloud’s developer-friendly approach to code security. We identify and fix risks before they reach runtime, ensuring your applications are hardened.
- Infrastructure: Prisma Cloud comprehensively protects your application infrastructure. We secure the full stack and harden your cloud estate to provide robust defense measures against emerging threats.
- Run: Prisma Cloud’s dynamic capabilities block the most advanced attacks in real-time. Our platform provides in-line protection and defense-in-depth strategies to stop active attacks and ensure the integrity and security of your cloud-native applications. Trust Prisma Cloud to take care of your digital assets from code to runtime with the highest efficacy and reliability.
Future Outlook
The convergence molds the future for EDR and XDR solutions, AI/ML integration, automation, cloud security integration, and the rise of managed services. Organizations are integrating EDR and XDR in a bid to unify security threat detection and response. AI and ML make detecting threats accurate and incident response more efficient. Automation and orchestration have increasingly become crucial in trying to counter threats’ heightened volume and complexity. Integration with cloud security tools provides visibility into the expanding cloud environment. Besides, a move to managed services reduces the management burden, providing the expertise and resources needed for the proper deployment and maintenance of such solutions.
FAQs
1. Is EDR replaceable by XDR?
XDR solutions replace EDR solutions as they provide a more comprehensive and integrated security approach. It might be costlier for the enterprises and require more resources and expertise to manage effectively.
2. What are the factors to consider while choosing between an EDR and XDR?
The factors include an organization’s security needs, budget allocations, availability of resources, complexity of the system, integration capabilities, false positive rates, and compliance obligations. Whereas XDR solutions are expected to cover a wide spectrum of security, they might be costly and complicated in management as opposed to EDR solutions.
3. What is the difference between EDR, MDR and XDR?
EDR concentrates on safeguarding endpoints, offering live monitoring and response against threats. XDR broadens this protection to cover networks, cloud setups, and emails, providing a more complete security solution. MDR, on the flip side, is a service that utilizes EDR (and sometimes XDR) tools to handle threat detection, response, and monitoring for organizations.
4. What are the steps for implementing EDR or XDR solutions?
Regardless of whether you determine EDR or XDR to be the better fit for your organization, there are several things you should do as you implement these cybersecurity systems, including:
- Involving key stakeholders and decision-makers: Confirm your cybersecurity strategy aligns with your organization’s overarching goals and objectives by incorporating feedback from business leaders throughout the implementation process.
- Conducting proof-of-concept (POC) testing: Identify vulnerabilities throughout your organization with POC testing and gain a detailed understanding of your specific security needs.
- Assess your existing security stack: Develop a plan for how your EDR or XDR solution should fit within your existing security stack to help streamline the implementation process.
- Training and educating your security team: Familiarize your security team with new EDR or XDR systems as early as possible to reduce potential errors and mistakes.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]


