Security Orchestration and Automation (SOAR) refers to coordinating and automating security processes and tools. Incident response relates to an organization’s structured approach to managing and mitigating security incidents.
Leveraging security orchestration, automation technology, and incident response tools helps automate various tasks and processes within an organization’s incident response plan. Security teams can employ scripts, software, and workflows to orchestrate and simplify incident response steps. The end goal for businesses remains to respond quickly, accurately, and efficiently to security incidents.
Initially, incident response was done manually. It was time-consuming and led Security analysts to investigate alerts manually, correlate data from different sources, and execute response actions. The traditional approach became unsustainable with the increased volume and complexity of threats.
The global Security Orchestration, Automation and Response Market size was valued at USD 1.1 billion in 2022 and is expected to grow at a CAGR of 15.8% from 2022 to 2027. The revenue forecast for 2027 is projected to reach $2.3 billion. – MarketsandMarkets
Integrating security orchestration, automation, and response into your Security Operations Centrer (SOC) can increase efficiency and effectiveness. It is possible by correlating alerts from disparate security devices, automating tasks, and providing playbooks for incident handling.
SOAR implementation aims to make SOC processes efficient and improve incident response while having too many security alerts in a given environment. Effective incident response comprises people, processes, and technologies. However, SOAR needs various components to offer step-by-step response plans. The major three pieces that comprise SOAR are:
- Security orchestration organizes alerts from various security and network tools in a way so that they can be acted upon effectively, either manually or automatically.
- Security automation reduces the dependence on humans for repetitive tasks and alerts that can be handled automatically.
- Incident response means planning and executing the steps to answer an incident using particular processes and technologies.
What is SOAR?
Security Orchestration, Automation, and Response (SOAR) is a solution that helps security teams coordinate various security tools, automate mundane tasks, and simplify incident and threat response.
Large organizations usually have security operations centers (SOCs) using many different tools to manage cyber threats, often manually.
According to the 2023 Global Security Operations Center Study by IBM and Morning Consult, 81% of organizations found that manual threat investigation slowed their response times.
SOAR platforms offer SOCs a central dashboard to integrate these tools into streamlined threat response processes and automate routine tasks. This dashboard also helps SOCs manage all security alerts from these tools in one place.
How does SOAR work?
SOAR technology consolidates three former security tools into one. According to Gartner, which named the term “SOAR” in 2015, SOAR platforms combine security incident response, orchestration and automation, and threat intelligence into one system.
To understand how current SOAR solutions work, let’s examine their key components: security orchestration, security automation, and incident response.
Elements of SOAR
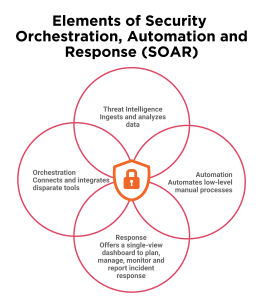
- Security orchestration: It ties together the combination of internal and external tools through integrations and APIs. This bundle of tools can include a vulnerability scanner, endpoint protection software, and firewalls. Information from these sources helps detect threats and improve collaboration, but it also means dealing with more alerts and data.
- Security Automation: This will analyze and automate processes leveraging the data provided by security orchestration. Automatic processes include vulnerability scanning and log analysis. Through AI and machine learning, automation will prioritize the threats and suggest the next action. Playbooks are predefined actions; they can be customized and connected to handle complex actions. For example, if a bad email is identified, a playbook can block the email, warn the employee, and block the sender’s IP address.
- Security Response: This is a single view for analysts to plan, manage, and monitor actions after threat detection. It is an attitude that collaborates and shares threat intelligence among teams. This will also include post-incident activities, including case management and reporting.
Benefits of SOAR in Incident Response
Constantly facing many threats daily drains your SOC and slows response. SOAR platforms help by handling less important tasks, letting SOC analysts focus on improving overall incident response.
Accelerated Response Time
Security orchestration groups similar alerts from various systems into a single incident. Security automation allows the system to respond to alerts without human intervention, which makes it faster. Adding context to data and automating decisions makes handling alerts much faster.
Optimized Threat Intelligence
Threat intelligence provides great insight but tends to go unseen. SOC analysts are already overwhelmed with numerous tasks, and adding another source makes it even more challenging. The best SOAR platforms can ingest threat intelligence and associate it with events as they occur. This empowers the SOC analysts by immediately providing actionable information.
Reduced Manual Operations
Security automation helps the SOC analysts by removing the boredom and repetitive tasks of the job and guiding them through incident responses. A quality SOAR platform will include these tasks in the playbooks, detailing all of the steps necessary to deal with an incident from start to finish.
Smooth Operations
Each element of SOAR, in one way or another, helps in smoothing security operations. Security orchestration will aggregate data from multiple places; security automation will deal with less urgent alerts through automated playbooks. Incident response removes the need to make spur-of-the-moment decisions during attacks, reducing how long cyberattacks can affect business.
Lowered Cyberattack Impact
Mean time to detect and mean time to respond are two critical measures that allow organizations to know just how quickly they can detect and respond to a cyberattack. The longer the time spent finding and responding to an attack, the greater the damage to the organization.
SOAR reduces both MTTD and MTTR. With security orchestration, analysts are provided with a wealth of information for each incident, hence making threat detection easier, which cuts the time for collecting information and more for investigation. It facilitates faster response to alerts and incidents due to security automation, which acts out on them on an occurrence basis.
Simplified Integration of Tools and Technology
Security orchestration is advantageous because it can tie together alerts from the numerous security tools at hand. Your SOAR platform should integrate with a variety of security technologies:
- Cloud Security
- Data Enrichment
- Email Security
- Endpoint Security
- Forensics & Malware Analysis
- Identity and Access Management
- IT and Infrastructure
- Network Security
- SIEM & Log Management
- Threat Intelligence
- Vulnerability & Risk Management
These tools should be easily integrated into your SOAR platform. A self-service marketplace can quickly find the integration for a certain tool. Then, it becomes only a matter of clicking a button and adding it to a playbook.
Reduced Costs
Integrating a SOAR platform into a business model saves a typical enterprise a lot:
- 90% on reporting
- 80% on creating playbooks
- 70% on handling alerts
- 60% on training analysts
- 30% on managing shifts
Automated Reporting
Automatic reporting makes life easier and eliminates the need for manual metrics. The SOC staff can thus easily pull reports with a click or on a schedule whenever required, giving businesses reliable metrics on time. Most SOAR tools also provide reporting templates and allow users to create custom reports, simplifying the process.
Standardized Communication Plan for Incident
In many cases, handling and response during incidents involve persons outside the SOC, especially when incidents are huge. Therefore, response teams incorporate members from within and outside the SOC, which may be challenging to ensure that communication is done reliably and consistently.
Companies often establish a mission control hub to deal with high-priority incidents. A good SOAR platform will have a feature that represents a “virtual war room” to ensure cohesive communication. This ensures that no one involved, from PR to HR, legal, and the C-suite, misses a single detail in the incident response.
Challenges that Security Analysts Face?
Overload of Detection and Alert
Managing many security tools and systems can result in a high volume of alerts and notifications. Filtering through the noise and identifying genuine security incidents among the false positives and irrelevant alerts becomes overwhelming. The challenge lies in prioritizing and responding to critical incidents while avoiding alert fatigue.
Complexity of Security Operations
To protect against modern threats, security managers must manage multiple security solutions from multiple vendors, each with unique processes. Security teams need a solution that can integrate these processes for the common goal of incident response can significantly simplify the incident response process.
Manual and Time-Consuming Processes
Traditional incident response relies heavily on manual processes, which can be time-consuming and prone to human error. From incident identification and investigation to containment and eradication, the manual execution of these tasks can delay response times and hinder the ability to mitigate the impact of security incidents swiftly.
Evidence Gathering and Post-Incident Analysis
When responding to a security incident, it is essential to collect the right evidence to confirm the occurrence of a breach, identify the extent of the compromise, and support subsequent actions and investigations. However, many security professionals often struggle to determine what evidence needs to be collected and ensure its integrity.
How is SOAR the Solution for Automating Incident Response?
SOAR platforms or solutions help integrate security tools and processes to orchestrate and automate incident response tasks. This comprehensive solution provides a centralized command center to allow security teams to manage incidents effectively from the detection phase to the resolution phase. SOAR has advanced features that allow organizations to simplify their workflow, improve response time, and improve collaboration within security stakeholder teams.
Core capabilities that the SOAR platform offers to automate incident response effectively:
- Integrating security tools: SOAR platforms easily integrate with existing security tools, such as SIEM (Security Information and Event Management) systems, threat intelligence platforms, and vulnerability scanners. They enable real-time data aggregation, correlation, and analysis.
- Automating Workflows: allows for creating predefined workflows that automate routine tasks. Automating will allow incident response teams to focus on critical tasks and respond swiftly to evolving threats.
- Pre-defined Actions and Response: SOAR platforms allow the creation and execution of incident response playbooks, which comprise predefined response actions and procedures tailored to specific incident types.
- Case Management Systems and Collaboration Facilities: SOAR platforms have a centralized case management system that facilitates collaboration among response team members.
Top Security Orchestration, Automation and Response Solutions
#1 Splunk SOAR
Splunk is a leading software company founded in 2003; it has a powerful data platform that facilitates organizations in monitoring, analyzing, and searching data efficiently.
Splunk SOAR:
Splunk Phantom, previously known as Phantom, is a feature-rich solution that enhances engagement and collaboration in security orchestration and response workflows.
Key Features:
- Integrates with over 350 different tools and comes with 100 out-of-the-box playbooks.
- Includes a no-code visual editor and powerful case management for optimizing security workflows.
- Benefits from the intelligence delivered by Splunk’s in-house cybersecurity research team, SURGe.
#2 Chronicle SOAR
Chronicle SOAR, formerly known as Siemplify, is part of Google’s Cloud services. It offers businesses and managed service providers (MSPs) a unified platform for data accumulation and security alerts through automation, orchestration, incident response, and integrated threat intelligence.
Key Features:
- Integrates with Chronicle SIEM to ensure effective utilization of the most recent data.
- Equipped with a comprehensive suite of features for efficient case management, alert ingestion, grouping, prioritization, assignment, and investigation.
- Allows playbook creation without coding, promoting consistent response processes and task automation.
- Focuses on root cause investigation of threats rather than individual alerts.
- Provides integrated threat intelligence across the detection and response lifecycle for enhanced insights.
- Facilitates smooth collaboration and transparency between incident responses.
- Offers a raw log scan function for insights from unprocessed data.
Advantages:
- Simplicity in deployment and effectiveness in operation.
- Provides detailed insights about network status and security threats.
- Suitable for organizations of all sizes due to extensive features and easy implementation.
- Particularly effective for managing larger and more sophisticated organizations, especially for MSP clients.
#3 Cortex XSOAR
Cortex XSOAR by Palo Alto Networks is a California-based global leader in enterprise security solutions.
Cortex XSOAR Platform:
- The Cortex XSOAR platform is renowned for delivering threat prevention and comprehensive response and intelligence management capabilities.
- It boasts over 750 integrations and 680 content packs, functioning completely automated or under SOC supervision.
- It facilitates real-time human investigation by featuring a dedicated “war room” for data point correlation.
- The platform can ingest data from all major SIEM solutions and, through the Threat Intelligence Management (TIM) module, offers critical context to alerts.
- Integrations can be customized or directly downloaded from the Cortex XSOAR marketplace.
Optimized for Incident Response:
- Palo Alto Networks has optimized Cortex XSOAR for incident response, emphasizing the importance of automation.
- By incorporating automation into incident response workflows, organizations can efficiently reduce alert noise, eliminate repetitive tasks, and enhance analyst investigation and collaboration.
- Cortex XSOAR offers automation content packs for various usage scenarios, enabling quick deployment and identification of critical security aspects.
#4 FortiSOAR
Fortinet, headquartered in California, stands as a leading cybersecurity company renowned for its diverse range of solutions, including firewall, intrusion prevention, and endpoint solutions.
FortiSOAR Platform:
- FortiSOAR is designed to collect data from various sources and transform it into actionable intelligence.
- FortiSOAR, equipped with over 350 integrations and offering more than 3,000 automated workflow actions, ensures extensive coverage and versatility.
- It includes 160 customizable playbooks, ready to use straight out of the box for seamless automation.
- Advanced threat intelligence management is facilitated through integration with FortiGuard.
- The solution features a mobile application for alerts and executed actions, along with a role-based dashboard for metrics tracking, performance analysis, report generation, and incident management.
Key Capabilities:
- FortiSOAR is a central hub to streamline and accelerate workflows and responses, enabling teams to focus better on threat protection.
- Its capabilities encompass incident response, case and workforce management, threat intelligence management, asset and vulnerability management, compliance validation and reporting.
- Additionally, FortiSOAR offers a no/low-code playbook creation option, enhancing flexibility and customization.
- Designed for seamless functionality across different deployment options – SaaS, on-premises, multi-tenant, dedicated, and shared-tenant – FortiSOAR caters to the diverse needs of global enterprises and Managed Security Service Providers (MSSPs).
#5 IBM Security QRadar SOAR
A leading cybersecurity and technology company, IBM is a company that offers efficient product development across numerous sectors.
QRadar is a Security Orchestration, Automation, and Response (SOAR) solution developed by IBM. It aids organizations in assessing and mitigating emerging cybersecurity threats within their networks. This solution features several pre-packaged remediation playbooks that expedite the resolution of cybersecurity issues.
Key Features:
- Provides intuitive dashboards and metrics tracking to enhance administrative visibility.
- Offers drag-and-drop automation alongside in-app guidance to assist decision-making processes.
- The IBM Security App Exchange provides hundreds of free configurations for integration.
- Facilitates planning and preparation for swift response during cyber attacks.
- Includes comprehensive case management tools to ensure relevant users receive actionable notifications.
- Aids in comprehending and visualizing relationships across incidents.
Compliance and Efficiency:
- Operates in alignment with over 180 international privacy and data breach regulations.
- With its open platform, it ensures efficient incident response, consolidating alerts from various data sources into a single dashboard and streamlining investigation and remediation processes.
- Automates artifact correlation, case prioritization, and investigation, bridging skill gaps.
- Integrates reporting tasks into incident response playbooks, enabling cooperation between privacy, HR, and legal teams when responding to privacy breaches.
#6 ServiceNow Security Incident Response
Established in 2004, ServiceNow is a leading provider of digital workflows and IT business management solutions.
Security Incident Response (SIR) Solution: ServiceNow’s Security Incident Response (SIR) is a cloud-based component of the Security Operations (SecOps) platform. It offers comprehensive solutions for Security Operations Center (SOC) teams, facilitating incident management, team collaboration, and workflow streamlining.
Key Features:
- Automation of workflow and coordination of incident response.
- Rich library of playbooks and orchestrations tailored for various scenarios.
- AI tools for incident investigations.
- MITRE ATT&CK mapping to add context to investigations.
- Virtual “war room” for enhanced team collaboration.
- Real-time reporting capabilities with a granular approach.
#7 InsightConnect
Rapid7, headquartered in Boston, is a leading provider of cybersecurity services, offering innovative cloud-based solutions to help businesses manage their cybersecurity more effectively. InsightConnect is Rapid7’s cloud-based Security Orchestration, Automation, and Response (SOAR) solution. It enhances visibility and automates processes within the digital space, empowering organizations to streamline cybersecurity management.
Key Features:
- Provides over 200 plugins and customizable workflows, seamlessly integrating with various applications such as Slack and Microsoft Teams.
- Offers Pro Automation for third-party products, automating responses to threats like phishing and ransomware.
- Facilitates vulnerability management through cohesive teamwork and strategic human decision-making when required.
Malware Threats Response:
- Offers prompt investigation and containment of malware threats such as ransomware and trojans, preventing severe damage to organizations.
- By automating and integrating existing systems and accelerating vulnerability management, InsightConnect provides a comprehensive solution to secure digital environments effectively.
Key Uses Cases of SOAR Solutions
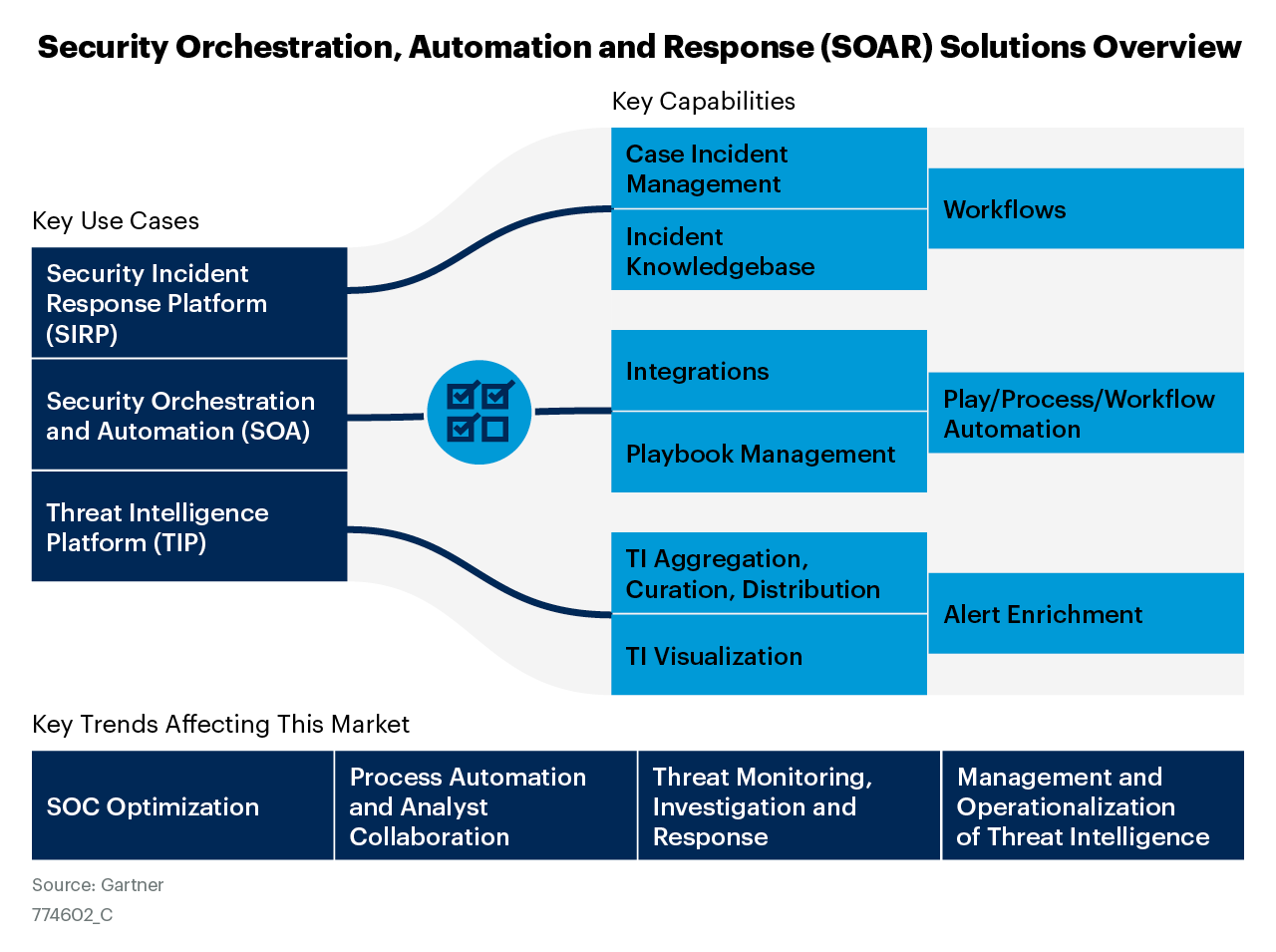
Automated Incident Response Processes
A SOAR platform automatically detects and investigates severe attacks. For example, it can identify suspicious emails, mark them as potentially phishing, look for similar emails in the network to delete or quarantine them, and block the source IP address or URL to stop other similar malicious emails from reaching workers.
SOAR platforms identify and contain threats so fast that they usually stop attackers from accessing sensitive data. Automated response reduces response times from hours to minutes.
Threat Hunting
Your security team may spend most of their day dealing with alerts, leaving little room to look, investigate, and handle threats. Automatic threat response frees up many incidents from being touched by a human analyst so that the security team can work on strategic long-term security plans and larger threats.
Priority for Penetration Tests
A SOAR platform automates most tasks, such as asset discovery, security scans, threat classification, and prioritization. This helps security teams focus more on areas needing extra care and can conduct penetration tests.
Vulnerability Management
A SOAR solution enhances the overall vulnerability management process, thereby ensuring that your security team can assess and handle risks effectively posed by newly found vulnerabilities. SOAR enables you to take a proactive security stance by automatically researching and gathering data on vulnerabilities.
Security Orchestration Automation and Response (SOAR) Trends
- Evolving threats and complexity: traditional SOAR solutions are now faced with rapidly increasing complexity due to evolving threats. The future of SOAR demands that such platforms evolve to address these challenges.
- Features of Next-Gen SOAR Platforms: Ideal SOAR platforms should be security capability deployed, not tool integration. They need to evolve from mere integration to the active management of security.
- Integration with Cyber Platforms: Security orchestration, automation, and response solutions need to be integrated with cyber platforms. This helps enhance the capability of managing cyber risks and Incident Detection and Response efforts across various verticals.
- Issues with bandwidth and latency: SOAR platforms effectively remediate bandwidth and latency challenges. This ensures smooth and effective function, especially for high data volumes and network demand environments.
Conclusion
Automating incident response with SOAR simplifies data sharing, reduces manual effort, and enhances communication and collaboration within the security team. With the automation of incident response, companies can utilize the complete potential of their security infrastructure for complex incident detection, response and mitigation. Automation in incident response by the SOAR platform has become a necessity. Integrating SOAR into security operations can boost incident resolution rates, improve accuracy and protect cyber defenses.
FAQs
1. What are the top features of an SOAR platform?
Orchestration
Automation
Case Management
Playbooks And Workflow Management
Threat Intelligence Management
Integrations With Security Tools
2. Which region in the market is leading in security orchestration automation and response?
North America is the leading region, with an anticipated CAGR of 10.7% through 2032.
3. SOAR vs SIEM: what are the key differences?
A Security Information and Event Management (SIEM) system gathers, analyzes, and stores security-related data, encompassing incidents and events. This data spans from firewalls and network devices to patterns signaling potential cyber-attacks.
SIEM tools usually require calibration and monitoring to assess data accuracy and prioritize significant information, which can be labor-intensive.
4. What are the benefits of SOAR platforms?
- Faster Response Times
- Reduced False Positives
- Centralized Management
5. How does the functionality of SOAR security tools operate?
The first step is data gathering using the functionality of SOAR security tools. Then comes data analysis. Using ML, the SOAR filters a vast quantity of data and carries out analysis. The third one is response. SOAR can help automatically enact the remediation process.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]


