Ransomware and Alpha Ransomware Discovery
Ransomware, a form of malware, restricts access to systems or files until a ransom is paid. Alpha ransomware, distinct from ALPHV ransomware, recently surfaced with its Dedicated/Data Leak Site (DLS) on the Dark Web, listing data from six victims. Discover the insights and observations of Rakesh Krishnan, Senior Threat Analyst at Netenrich, as we delve into the world of ransomware.
Typically, ransomware operators operate covertly before launching a DLS. Alpha ransomware first appeared in May 2023, observed through the threat actor’s TOX ID. Presently, it’s not widespread, with lower infection rates than competitors and no active samples for analysis.
Alpha ransomware encrypts files with random 8-character alphanumeric extensions, such as:
46140264-Readme.txt
79508AE9-Readme.txt
8C362A73-Readme.txt
E145AA52-Readme.txt
A75BE48B-Readme.txt
The sole listed sample, SHA1: c2b73063a4a032aede7dfd06391540b3b93f45d8, has yet to be recorded elsewhere.
Significance of Distinguishing Alpha Group from ALPHV Ransomware
- In May 2023, the ransom note lacked sophistication, not even featuring the name “Alpha”. It simply stated the data had been encrypted and provided instructions for contact.
- By June 2023, they adopted the name “Alpha Locker” in the ransom note, and by November 2023, they fully embraced the name “Alpha ransomware“.
- Initially, encrypted file extensions consisted of random numbers. However, in later iterations, they switched to an alphanumeric 8-character extension, indicative of evolving tactics.
- The group’s DLS on the Dark Web appears unstable and frequently offline, suggesting they are still in the process of establishing their operations.
- These observations collectively suggest that the Alpha group is relatively new to ransomware operations and is undergoing a learning curve in its approach.
Analysis of the Group’s Behavior
Evolution of the Alpha Ransomware Group’s Ransom Notes and File Extensions
This analysis looks closer at the Alpha ransomware group’s Ransom Notes (RNs) and file extensions, revealing their evolving tactics and possible inexperience.
Early Stages (May 2023)
- RN: Lacked a proper name, suggesting the group was still establishing itself.
- File Extension: Used random numbers, potentially indicating a basic approach.
June 2023 Revision
- RN: Introduced the name “Alpha Locker,” signifying a step towards branding.
- File Extension: Remained random numbers.
November 2023 Revision
- RN: Evolved into “Alpha ransomware,” displaying further name refinement.
- File Extension: Shifted to a more structured “Alphanumeric 8-Character” format, hinting at increased sophistication.
The Alpha ransomware group’s Ransom Notes and file extensions exhibit a clear pattern of development, suggesting they are a relatively new group. Their initial use of random numbers and lack of a proper name in their RNs could indicate inexperience. However, the later introductions of a name and a more structured file extension point to their efforts to become more established and sophisticated. The instability of their Data Leak Site further reinforces the notion of a group that is still under development.
Exploring the Data Leak Site (DLS)
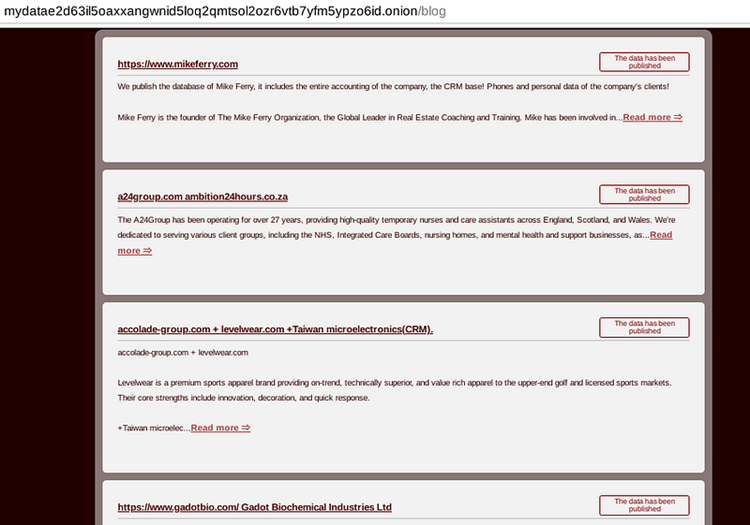
The Data Leak Site (DLS) associated with the Alpha Ransomware Group is labeled as “MYDATA.” However, it’s worth noting that this name may be subject to change due to its lack of memorability, as observed from the group’s behavior analysis.
To access the dark website, use the following URL:
mydatae2d63il5oaxxangwnid5loq2qmtsol2ozr6vtb7yfm5ypzo6id.onion
 Exploring the Features of the Alpha Panel:
Exploring the Features of the Alpha Panel:
The Alpha Group employs a traditional method to interact with victims through the Alpha Panel. This involves providing victims with a Personal Decryption Key, granting access to the panel, and facilitating direct communication for ransom negotiation purposes.
Upon accessing the panel, victims are welcomed and prompted to log in to initiate discussions with the Alpha Group.
 Victims and Industry Impact
Victims and Industry Impact
Upon logging in, victims will encounter a series of options:
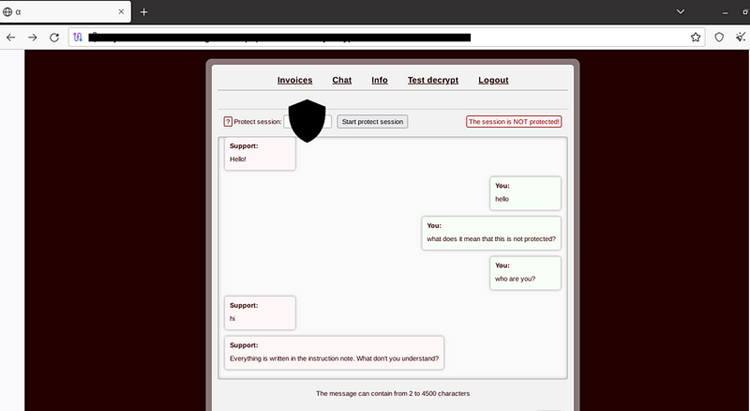
Victim Communication Interface: Upon observation of the provided snapshot, it becomes apparent that the small Greek letter “Alpha” (α) is visible on the tab, along with distinct section headings:
 INVOICE, CHAT, INFO, TEST DECRYPT, LOGOUT
INVOICE, CHAT, INFO, TEST DECRYPT, LOGOUT
This panel ensures secure chat sessions by generating a key between the victim and the threat actor.
The functionalities include:
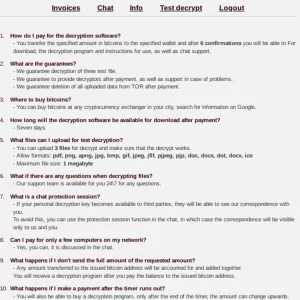
- Invoices: Provides victims with the ability to review their assigned ransom amounts.
- Chat: Facilitates negotiations with the Alpha group.
- Info: Contains instructional information on how to proceed.
- Test Decrypt: Allows victims to submit three sample files (each less than 1MB) for decryption testing.
- Logout: Terminates the session.
It is plausible that the Alpha Group utilized the CloudFlare Onion Service, which enhances security for hosted Onion Domains by adding layer of protection. Upon exploration of the data leaked/published by the group, it becomes evident that the group maintains an additional TOR Domain exclusively dedicated to hosting the leaked resources.
- TOX ID: 98D120C9033653042E290627914B890A3291013F7377A976A028051C52440C71487D5F14DDA2
- Bitcoin Address: bc1qff2u797mrekxtcnr68p2gqarnjxvy575jug430
- Ransom Demand: 0.2720 BTC
Insights from Rakesh Krishnan
- Mitigation Strategies for Alpha Ransomware Attacks:
As Alpha Ransomware hasn’t surged significantly yet, obtaining a sample is unavailable. However, a vital mitigation strategy is to avoid clicking on any external links received via email. - Impact on the IT Sector and Cybersecurity:
Analysis of the victim list revealed that the Alpha Group compromised a French firm named “Carri Systems,” indicating a focus on the IT Sector. - Role of Emerging Technologies in Defense Against Alpha Ransomware:
Cyber Awareness Programs play a crucial role as many attacks stem from SpearPhishing Campaigns, leading to Business Email Compromise (BEC) Attacks. Implementing Endpoint Security Solutions to detect anomalies and maintaining up-to-date systems and programs are also pivotal in thwarting Critical Bug Exploitation.
Final Note
Based on the panel and various indicators like the ransom demand, it appears that the group exhibits talent but also demonstrates a certain level of amateurism within this realm. It is anticipated that in the coming days, an increase in victims may occur, leading to heightened visibility for the group, potentially resulting in widespread attention as they gather additional digital footprints.
FAQs
1. What is ransomware, and how does it differ from other forms of malware?
Ransomware is a type of malicious software that encrypts files or restricts access to a system until a ransom is paid. Unlike other malware that may steal data or disrupt operations, ransomware explicitly demands payment in exchange for restoring access to the affected files or systems.
2. What distinguishes Alpha ransomware from other ransomware variants like ALPHV ransomware?
Alpha ransomware differs from other variants like ALPHV ransomware in its modus operandi and evolution. Initially lacking sophistication, Alpha ransomware gradually adopted a name and refined its tactics, such as shifting to alphanumeric file extensions. This suggests a group in the early stages of development within the ransomware landscape.
3. What insights do we gain about the behavior of the Alpha ransomware group through their Data Leak Site (DLS) and interaction with victims?
Analysis of the Alpha ransomware group’s DLS and victim interaction reveals a blend of amateurism and talent. The unstable DLS and evolving ransom notes suggest a group still establishing itself. However, the provision of a decryption key and communication platform for negotiation indicates a level of sophistication in their operation.
4. What mitigation strategies are recommended for defending against Alpha ransomware attacks, considering their evolving nature and potential impact on the IT sector and cybersecurity?
Given the evolving nature of Alpha ransomware and its potential impact on the IT sector, mitigation strategies include:
- Avoid clicking on external links in emails to mitigate the risk of infection.
- Implementing cybersecurity awareness programs to educate employees on phishing tactics.
- Deploying endpoint security solutions to detect and respond to anomalies.
- Ensuring systems and programs are regularly updated to mitigate the exploitation of critical vulnerabilities.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]



 Victims and Industry Impact
Victims and Industry Impact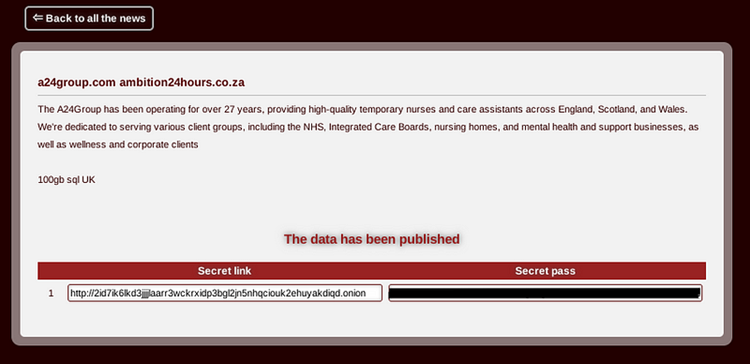 The victims list can be traced to the following domain:
The victims list can be traced to the following domain: