Introduction
Identity and Access Management (IAM) is a structured framework comprising business processes, policies, and technologies dedicated to efficiently managing electronic or digital identities. IAM essentially empowers Information Technology (IT) managers to regulate user access to crucial information within organizational domains.

Various systems play pivotal roles within the IAM framework, including single sign-on systems, two-factor authentication, multifactor authentication, and privileged access management. These technologies collectively enable secure storage of identity and profile data, coupled with data governance functions, ensuring the sharing of only necessary and relevant data.
“Identity and Access Management (IAM) is a security and business discipline that includes multiple technologies and business processes to help the right people or machines to access the right assets at the right time for the right reasons, while keeping unauthorized access and fraud at bay.” – GARTNER
IAM deployment options encompass on-premises installations, third-party vendor services via a cloud-based subscription model, or hybrid models combining both approaches. CIOs analyze current weaknesses and strengths within the organization, strategically opting for IAM solutions. IAM emerges as a cybersecurity subject primarily focusing on overseeing user identities and access permissions within computer networks. Although IAM policies, processes, and technologies may vary across companies, the ultimate objective of any IAM initiative is to guarantee that the appropriate users and devices access the correct resources for valid reasons at specific times.
Importance of IAM for Enterprise Security: Here’s Why
The statistics underscore the critical need for IAM. A staggering 80% of cyberattacks employ identity-based attack methods, emphasizing the urgency for robust IAM implementation, according to Crowdstrike’s report. Additionally, 3 out of 4 Chief Information Security Officers (CISOs) acknowledge the vulnerability of collaboration tools, with 94% expressing dissatisfaction with the security tools inherent in Microsoft 365, as per the Mimecast report. In this context, IAM emerges as a proactive defense and an essential strategy to navigate the evolving threat landscape.
IAM’s significance in organizational cybersecurity cannot be overstated. It is crucial in helping IT departments strike a delicate balance—ensuring that essential data and resources remain inaccessible to the majority while remaining accessible to authorized personnel and devices. This balance is pivotal for maintaining security within the organizational framework. IAM becomes indispensable in managing and controlling who and what accesses an organization’s systems, offering a vital defense against data breaches and cyber-attacks.
IAM solutions address the dynamic nature of cybersecurity threats. This solution stands out as an effective tool for preventing and minimizing the impact of attacks. Unlike a broad lockdown that restricts everyone’s access after a breach, many IAM systems leverage artificial intelligence (AI) capabilities to detect and thwart attacks before they escalate into more significant issues.
Read about IAM in the CIO Influence Interview with John Engates, Field Chief Technology Officer at Cloudflare.
The Foundation of IAM
Core Components
-
Authentication:
Authentication verifies employees or users by soliciting unique identifiers and required credentials, such as usernames, emails, passwords, and biometric features. Access methods include swipe cards, smartcards, RFID, and certificates.
-
Authorization:
Authorization grants access to tools and resources based on the confirmed identity from authentication. It establishes the scope of a user’s operation, differentiating between User A and User B.
-
Administration:
IAM administration manages user accounts, groups, permissions, and password policies. It oversees creating and modifying user accounts, ensuring strong password usage, and prompting password changes for security.
-
Auditing and Reporting (A&R):
A&R focuses on users’ activities post-authentication and authorization, tracking and detecting unauthorized or suspicious actions. This component examines and records users’ access logs and security-related activities, ensuring compliance with industry regulations like CPRA, HIPAA, PCI DSS, GDPR, etc.
Challenges specific to B2B environments
-
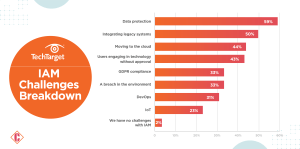
Data protection: The number one challenge listed in the bar graph is data protection, with 59% of respondents reporting that it is challenging for their organization. This suggests that many organizations struggle to keep their data safe from unauthorized access, loss, or corruption. This could be due to a number of factors, such as inadequate security measures, human error, or malware attacks. The consequences of a data breach can be severe, including financial losses, reputational damage, and legal liability.

-
Integrating legacy systems: Integrating legacy systems with new technologies can be complex and time-consuming. The TechTarget report shares that 50% of respondents reported integrating legacy solutions and organizational challenges. There are a number of reasons why integrating legacy systems can be difficult, such as incompatible data formats, different programming languages, and a lack of documentation. If not done properly, integration can lead to a number of problems, such as data errors, system outages, and security vulnerabilities.
-
Moving to the cloud: Many organizations are moving to the cloud to take advantage of its scalability, flexibility, and cost-effectiveness. However, as the bar graph shows, 44% of respondents reported that moving to the cloud is challenging for their organization. This could be due to a number of factors, such as concerns about data security, a lack of expertise, or the complexity of migrating applications and data to the cloud. If not done properly, cloud migration can lead to a number of problems, such as data loss, increased costs, and security vulnerabilities.
-
Users engaging in technology without approval: Forty-three percent of respondents reported engaging in technology without approval is challenging for their organization. This could include activities such as using unauthorized software, connecting personal devices to the corporate network, or accessing unauthorized data. These activities can pose a number of security risks, such as malware infections, data breaches, and identity theft.
-
GDPR compliance: The General Data Protection Regulation (GDPR) is a data privacy regulation in the European Union enacted in 2018. The data shows that 33% of respondents reported that GDPR compliance is challenging for their organization. This is likely due to the complexity of the regulation and the high penalties for non-compliance. Organizations not compliant with GDPR could face fines of up to €20 million or 4% of their annual global turnover.
-
A breach in the environment is a security incident resulting in unauthorized access to data or systems. The TechTarget report identifies that 33% of respondents reported that a breach in the environment is a challenge for their organization. This suggests that many organizations are concerned about the risk of cyberattacks. The consequences of a security breach can be severe, including financial losses, reputational damage, and legal liability.
Role of IAM in B2B Transactions
In contemporary B2B business, where secure exchanges are vital, Identity and Access Management (IAM) stands as a linchpin, ensuring the integrity and confidentiality of these interactions. IAM is crucial by fortifying authentication through robust mechanisms like multi-factor authentication and single sign-on (SSO), ensuring that only authorized individuals and businesses can access B2B platforms. This authentication strength is complemented by IAM’s granular authorization capabilities, allowing businesses to finely tailor access privileges for each B2B partner, thereby minimizing the risk of inadvertent or malicious data exposure. Additionally, IAM systems facilitate secure data sharing and collaboration by encrypting data in transit and at rest, enforcing role-based access controls, and automating user onboarding and offboarding processes. Moreover, IAM’s contribution extends to improving visibility through detailed logs and audit trails, enabling businesses to address potential security threats proactively and ensuring compliance with various data privacy and security regulations.
Business Benefits of IAM Implementation
-
Enhanced Security and Risk Management:
- Access privileges are granted based on policies, ensuring proper authentication, authorization, and auditing for all individuals and services.
- This systematic approach reduces the risk of internal and external data breaches.
-
Improved Regulatory Compliance:
- IAM frameworks make enforcing policies related to user authentication, validation, and privileges easier, addressing issues like privilege creep.
- Companies can better comply with government regulations, showcasing responsible corporate information usage and providing readily available data for audits.
-
Operational Efficiency and Reduced IT Costs:
- Automated IAM systems streamline operations, significantly reducing the time, effort, and costs associated with manual network access management.
- IAM implementation enhances overall operational efficiency, allowing businesses to allocate resources and reduce IT expenses strategically.
Case studies highlighting successful IAM implementations in the B2B sector
Case Study 1: 25% Improved Delivery with Automation-Infused IAM Platform
A prominent financial organization in America sought end-to-end identity and access management services to address challenges in its IAM architecture, resulting in increased efficiency and compliance. The key challenges included a lack of streamlined processes impacting business productivity, complex IDM configurations leading to defects, inadequate IAM product utilization, and non-compliance issues. The solution involved automating Oracle Identity Manager (OIM) processes, implementing scripts for user access provisioning, and centralizing governance processes. This automated approach significantly reduced tickets by 25%, improved qualitative delivery through automation services in the IDM platform, enhanced business productivity, decreased user access issues, and increased compliance by adhering to company standards and processes.
Case Study 2: Simplifying Secure Identity and Access for 27 Million Users
The IBM Office of the CIO faced the complex task of managing identity and access authentication services for over half a million IBM employees and 26 million global clients across two separate IAM platforms. To address this challenge, IBM transformed its authentication services using IBM Security Verify, a cloud IAM services platform. The solution enhanced scalability to over 27 million internal and external identities, offering passwordless QR or FIDO2 capabilities for over 800,000 authentications since migration. The implementation resulted in improved security, scalability, and user experience. IBM Security Verify’s APIs facilitated seamless application migration, enabling customization without draining development resources. The new solution allowed IBM to expand internal user choice for authentication, offering enhanced 2FA capabilities. The careful migration plan, leveraging Security Verify Bridge and Directory Sync, ensured minimal impact, tighter security control, and successful IAM modernization.
Leading IAM Software
Microsoft Entra ID
JumpCloud
Okta Workforce Identity
Salesforce Platform
IBM Security Verify
AWS Identity and Access Management (IAM)
IAM Best Practices for CIOs and C-Suite Executives
-
Adopt the Principle of Least Privilege:
- Limit user access to necessary resources, reducing internal and external threats vulnerability.
- Implement a robust IAM solution to enforce the principle while ensuring precise data access for authorized users.
-
Enforce Multifactor Authentication (MFA):
- Enhance security with MFA, providing unique verification codes for authorized users.
- Simplify user experience through password-less access using biometrics for authentication.
-
Periodically Rotate Access Keys:
- Mitigate security risks by regularly changing access keys and preventing unauthorized system access.
-
Use Temporary Security Credentials:
- Grant temporary access permissions to resources, minimizing the risk of long-term access key theft.
- Automatically expire temporary security keys at the designated term.
-
Regularly Audit Logs:
- Monitor user activity and detect suspicious actions through regular auditing of access logs.
- Strengthen IAM security by staying vigilant about potential threats.
-
Grant Permissions by Roles (RBAC):
- Implement role-based access control to provide permissions based on organizational roles.
- Prevent security vulnerabilities by ensuring users only have access necessary for their tasks.
-
Deprovision Unused User Accounts:
- Deactivate unused accounts regularly to ensure authorized access to organizational resources.
- Mitigate the risk associated with unused accounts to maintain a secure IAM infrastructure.
-
Leverage Separation of Duties:
- Separate system access between individuals to prevent fraud and restrict potential damage from malicious activity.
- Enhance overall security infrastructure by implementing a clear separation of duties.
-
Properly Manage Administrator Credentials:
- Exercise caution in managing administrator login credentials due to their significant access.
- Prevent malicious activities by administrators by implementing rigorous credential management practices.
-
Safeguard Root User Account:
- Protect the root user account, which controls all functions of the IAM infrastructure.
- Use MFA, audit logging, and access control policies to enhance the security of the root user account.