“AI can help overburdened teams automate API security detection and remediation efforts, including identifying abnormal behavior, suspicious API traffic, or usage patterns that may indicate insider threats or fraudulent activities.”
Hi Karl, welcome to our Interview Series. Please tell us a little bit about your role and responsibilities at Noname Security. How did you arrive here?
In July 2021, I joined Noname as CISO, where I’ve helped establish a rigorous standard for operational and security excellence and advocate for ongoing platform advancements based on our customers’ needs.
When I had the opportunity to meet with the Noname Security team early in its platform design, I recognized that they were on the verge of solving several challenges in securing APIs. I wanted to be a part of their exciting adventure.
I have over 25 years of leadership in technology and security across financial services, retail, and federal government.
I’ve advised CEOs, CTOs, and investors on strategies for product, market, and customer success. Before joining Noname Security, I held the CISO role at PennyMac Loan Services and City National Bank and served as Senior Vice President of IT Risk Management at PNC.
CIO Influence Interview with Anand Oswal, SVP and GM of Network Security at Palo Alto Networks
Beyond my professional roles, I’ve held roles as the President of the LA Cyber Lab, Financial Services Co-Chair for Los Angeles Infragard, and Adjunct Faculty at the University of Minnesota’s Technological Leadership Institute. I also served eight years of active duty service in the U.S. Army.
Could you tell us more about the role of a modern Field CISO? What are the biggest challenges you tackle in your current role?
The role of Field CISO prompts me to wear different hats each day to bring value to everyone who shares in the mission of securing APIs. For the security community at large, I share our research and our solutions in the big picture – how are companies utilizing APIs in new ways and what risks or challenges we face in protecting APIs.
For current and future customers, I help them put together complete strategies to solve API challenges, not only with our technology but with our alliance partners, process designs, maturity models, training and staffing plans, etc. to achieve short-term and lasting success.
Lastly, I advocate with our Product team on areas of development and improvement that we can make that our customers need on their API security journey.
At the center of my role is the necessity of building trust with stakeholders. A Field CISO needs to be an asset to customers, vendors, and partners all in equal weight.
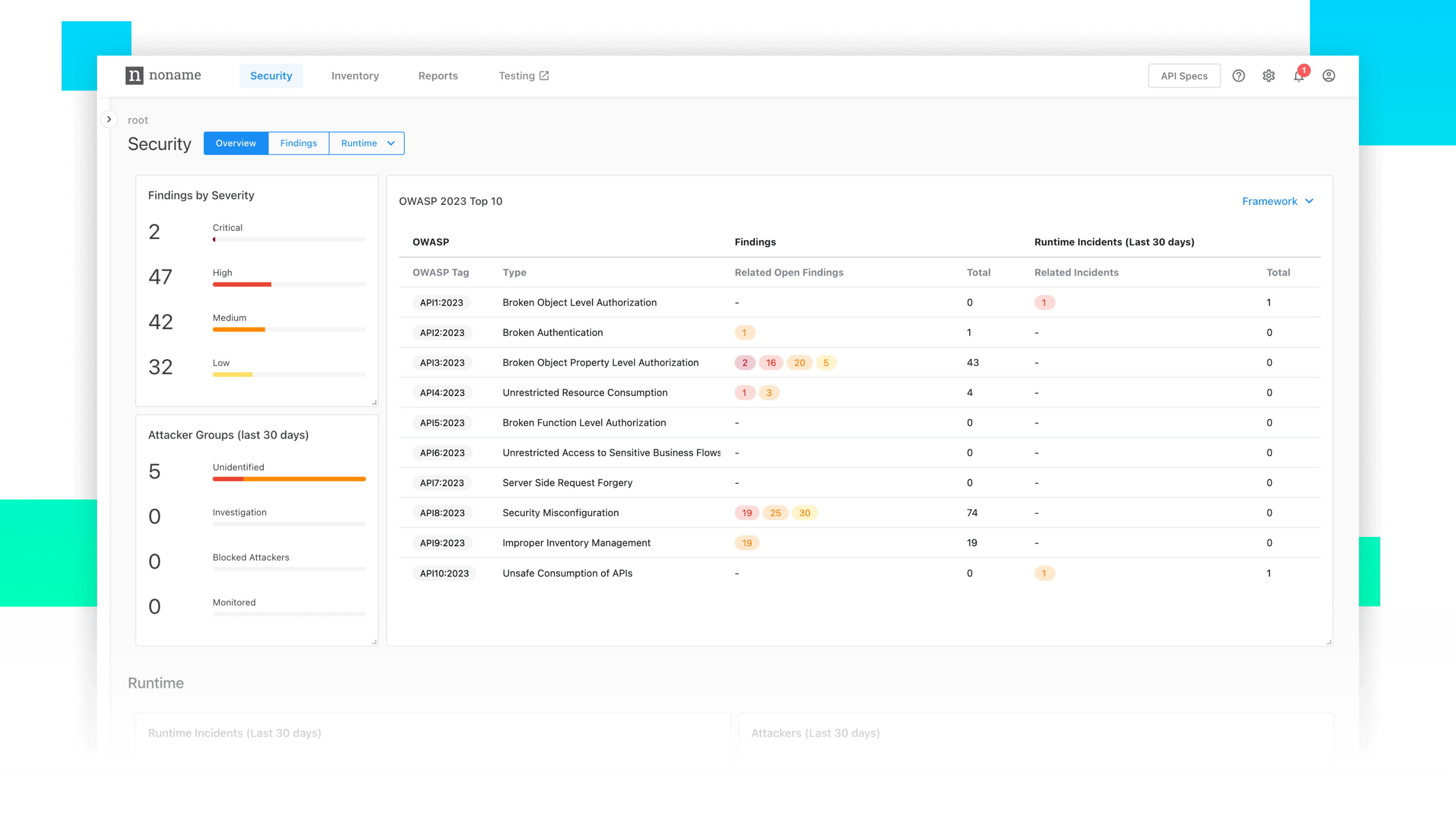
API security has become an absolute necessity for every organization. What are the core capabilities included in an API security framework that every CIO/ CISO should be aware of?
As the security of APIs has emerged over the last few years as a key priority, there is also an emerging body of best practices and frameworks organizations can utilize to assess their own practices, maturities, and capabilities. At Noname Security, we’ve established an API Top 20 Security Controls reference model to guide the planning and strategy towards a mature state of API security controls. Pivotal to this framework is the primary emphasis on people and process design, followed by selecting technologies that enable the capabilities within this framework.
Our API security framework of 20 controls is divided into five categories – Governance, Development, Testing, Operations, and Detection/Response. We are thrilled to provide this control framework as part of the consultative relationship with our customers.
What is the best approach to manage and protect against API security-related incidents in 2023?
Comprehensive API security processes require an approach that considers all aspects of the API. From its development, deployment configuration, and run-time operations, the most mature organizations are looking at the API as an asset warranting this full lifecycle approach.
Best practices include:
- API security posture: Assess every API, including legacy and shadow APIs, and uncover the types of data they encounter. Based on that inventory, identify misconfigurations and vulnerabilities in the source code, network configuration, and policy. Focus security interventions on the highest-risk areas.
- Detection and response: Deploy behavioral AI models for real-time API threat detection. Integrate with existing IT workflows to automate incident response and block serious threats.
- Continuous testing: Continuously test API endpoints to identify API risks before they emerge. Supplement DevOps DAST, SAST, SCA, and other existing tools with API security testing that can be automated and integrated into CI/CD pipelines. Adequate testing will help you discover design flaws and prevent attacks like SQL injections.
As a Field CISO, how do you see the use of AI and Automation capabilities in mitigating AppSec vulnerabilities?
First and foremost, developer co-pilot technologies using AI can substantially improve source code quality and security during initial development. Of course, this itself requires training and tools, and we should not immediately throw AI at source code without training and proper integrations.
Nonetheless, this is where we see making the biggest impact using AI, which is the earliest stage of API development.
AI can help overburdened teams automate API security detection and remediation efforts, including identifying abnormal behavior, suspicious API traffic, or usage patterns that may indicate insider threats or fraudulent activities.
Finally, detecting the sophisticated attacker who uses AI is where we focus on in terms of our Noname Security platform. We can detect API abuse with automated machine learning-based detection, seeing the most subtle attacker activity or suspicious data movement that ordinary rules-based engines will overlook. As well, we leverage AI to analyze the configuration and context of an API to identify the broadest set of API vulnerabilities and misconfigurations.
Please tell us more about your API Protection for Azure and IBM DevOps ecosystems.
Through our partnership with Microsoft, joint customers can manage API security posture with native, automated log collection powered by Azure Diagnostic Logging and Noname Security machine learning algorithms and leverage API security policies to enhance runtime protection and prevent data leakage. Integrations with Azure Load Balancer, Azure API Management, Azure App Service, Azure Storage, and Azure Virtual Machines also enable a real-time view of all API traffic and security/configuration issues.
Since November 2021, Noname Security has actively engaged with Microsoft for Startups and the Pegasus program, allowing the company to expand its reach to hundreds of potential customers.
Our partnership with IBM, a leader in API management and application gateways, enables us to deliver advanced API security capabilities. This joint solution will help you reach new levels of security confidence. Together, we help IBM customers find API security issues faster, prioritize remediation based on impact to cut costs, ensure ongoing compliance with regulations and internal policies, and conduct real-time traffic analysis using automated AI and machine learning detection to stop attacks in real-time.
Working with IBM, Noname plans to develop even more innovative products that meet customers’ needs more efficiently and effectively. This will enhance our product offerings, help us better serve Noname and IBM customers, and strengthen our respective leadership positions in the marketplace.
We are witnessing a shift in regulatory forces for API security. Could you shed some light on the recent developments in this area that could impact CIO/CISO strategies in 2024?
In 2024, I predict we will see a notable shift in the regulatory landscape as regulatory agencies focus on API security in the wake of many high-profile API-related security breaches.
CIO Influence Interview with Anneka Gupta, Chief Product Officer at Rubrik
While asset management, especially in the banking sector, has traditionally been under scrutiny by regulators, APIs are emerging as a distinct category of assets that require management and oversight. Consequently, API inventory discovery and lifecycle management are emerging as focal points for banking regulators, reflecting the evolving technological landscape and the critical role of APIs in modern financial systems.
CISOs will need to elevate their API security capabilities to be more transparent and precise. And, CISOs will need to partner closely with API development teams and business line technology owners to achieve new levels of maturity and sophistication.
What would be your advice to CIOs against ransomware cyberattacks?
Do you have a SecOps framework at Noname Security against these attackers?
Could you share some information about your framework?
Ransomware defense remains at the very top of the priority list for most organizations. We recently wrote about this extensively, as securing APIs certainly does have an important role to play in protecting against ransomware.
In short, One of the key reasons why ransomware attacks are so successful is that they take advantage of APIs in the delivery of ransomware and exfiltration data. Strictly speaking, APIs are not susceptible to malware as are traditional hosts. However, ransom groups use APIs extensively, and our protection of APIs is central to an overall ransomware protection strategy.
Cloud Optimization Strategies for Navigating Cloud Evolution in 2024
Your take on the future of active AppSec platforms in building a strong IT infrastructure:
We are in an era of consolidation of tools/vendors right now. I would only be speculating as to whether that trend accelerates or falls away. But I think the constant in thinking about the future of AppSec is that technologies are always best utilized and risk reduction is most effective when designed with a developer-first mindset. “Shift Left” is not just a marketing term. It’s a reality we’ve observed in practice for years now, which is that an empowered developer is the biggest security asset a company can have. Technologies that hit the mark for developers will own the future of AppSec.
Lighter notes:
Burn the midnight candle or soak in the sun?
Sun.
Coffee, or Tea?
Neither. Just Coca-Cola…
What is your favorite Noname Security product marketing initiative that you want everyone to know about?
API Workshop
First memorable experience in your career as an IT and security ops leader?
Pulling security detail for a CEO’s wedding.
Most useful app that you currently use:
Canva
Read More: CIO Influence Interview with Charles Fan, Co-Founder at MemVerge
Thank you, Karl! That was fun and we hope to see you back on itechnologyseries.com soon.
[To participate in our interview series, please write to us at sghosh@martechseries.com]
This interview has been republished from 2023. Akamai has recently announced it has entered into a definitive agreement to acquire application programming interface (API) security company, Noname Security. Under terms of the agreement, Akamai has agreed to acquire all of the outstanding equity of Noname for approximately $450 million, after customary purchase price adjustments.
Karl is a cybersecurity leader and innovator who serves as the CISO for Noname Security. He has over 25 years experience leading innovative and diverse teams of technology and security professionals in financial services, retail and federal government. Previously, Karl served as the Chief Information Security Officer (CISO) for PennyMac Financial Services and City National Bank. He has a track record of providing CEOs, CTO and investors in cybersecurity on strategies for product, market and customer success.
Noname, headquartered in San Jose, California, is a privately funded company. Noname’s over 200 employees, including CEO and Co-founder, Oz Golan, are expected to join Akamai’s Security Technology Group.