The rise of cloud computing has given rise to sophisticated cloud threats. When left unattended, these cloud threats could severely dent the cloud security posture of your organization, no matter how strong your Information Security (InfoSec) strategy is. According to a latest report on cloud threat management, a majority of cloud users are “repeatedly” making the same types of mistakes. These risky behaviors trigger 80% of the alerts, taking a toll on InfoSec teams while managing heavy cloud workloads.
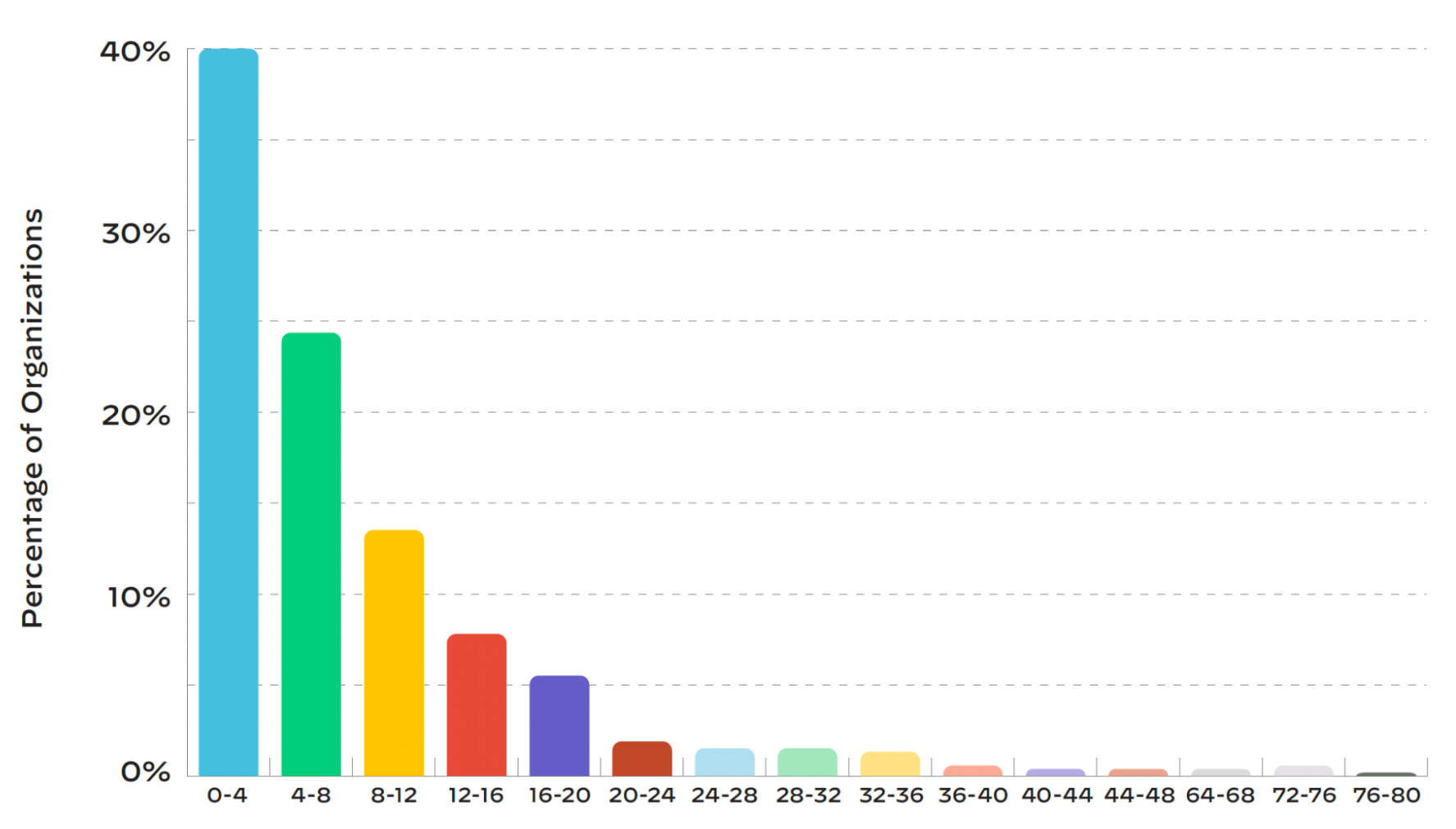
As cloud migration industry continues to grow at a rapid pace, InfoSec and DevSecOps teams could have a hard time creating and implementing cloud-native security policies pertaining to MFAs, firewalls, shadow IT frameworks, and database security exposures. Based on the data collected over the past 1 year, Palo Alto Networks’ analysts at Unit 42 published the latest Cloud Threat Report, Volume 7. The report identified the common gaps in cloud-native applications that led to data security incidents across multiple industries.
Top News: Palo Alto Networks Leads the Industry to AI-Powered SASE
If you are a CIO or a CISO, you must be dealing with different kinds of threats targeting your organization’s IT resources. Here’s a quick snapshot of all the cloud threats emerging in the wild.
58% of organizations do not enforce MFA for admins!
Shadow IT is a can of bad worms that could take down any organization in no time! How? 58% of organizations surveyed by Unit 42 found root admins do not use MFA to access IT resources. Worse, more than two-thirds (76%) of organization do not have an MFA protocol for their console users. When admin or console user is targeted in a brute force attack or SIM swap fraud, it could lead to a potential cloud data breach across multiple destinations, including organization-centric cloud identities.
Benefits of Embracing Edge Computing for CIOs
Threat actors are quick to detect such incidents and immediately interrupt or destroy access to cloud workloads, extorting the organization or personnel for ransom.
Common leaks emerging from these cloud threats are linked with loss of credential, blocked access to cloud workloads, data in dark web, and exfiltration.
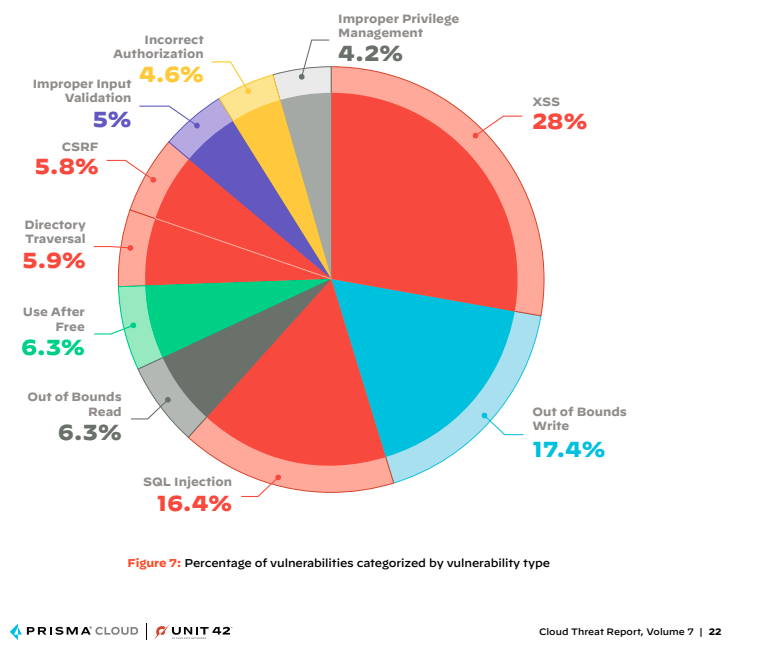
Common Types of Vulnerabilities in the Cloud Threats Landscape
The report on cloud threats found 905 of vulnerabilities on internet-linked cloud hosts comprise of web and API buckets. These applications could be poisoned with XSS, SQL injection, CSRF, and directory traversal vulnerabilities. According to Unit 42 analysts, there are 10 common exploited web and API vulnerabilities targeting cloud users. These are:
- XSS
- Out of Bounds Write
- SQL injection
- Out of Bounds Read
- User after Free
- Directory Traversal
- CSRF
- Improper Input Validation
- Incorrect Authorization
- Improper Privilege Management
Public Cloud Threats targeting VM instances can Cost you $12k Daily!
The new report found 75% of organizations have virtual machine (VM) instances with non-HTTP ports critically exposed to the public internet; 11% of hosts in public clouds have much higher risks and critical vulnerabilities that can be easily targeted until the organization loses its authority on the cloud workloads. In most cases, these attacks are led by misconfigured firewalls or cryptojacking bots that take over VMs for large-scale crypto-mining. Poor cloud operations management could lead to these attacks, but if not identified and reported sooner, the cryptojacking bots could deplete your financial resources very quickly, resulting in massive losses.
4 Days or More: That’s the time majority of organizations take to resolve a security alert!
According to Mimecast’s State of Ransomware Readiness 2022, 77% of cybersecurity professionals have mentioned the number of attacks on their organizations have either increased or remained same in the last 12 years. These attacks are getting more and more sophisticated, costing organizations upto $100k or more in total damage. If an organization loses $12k per day due to a cryptojacking bot attack, it would result in up to $48k by the time security teams actually identify and analyze the cloud threats on their systems. By that count, 60% of victims take 4 days to locate the critical attacks. On an average, it takes 145 hours to successfully resolve a security incident. While this could be a norm in the industry, it reflects inefficiencies in the handling of alerts and security triggers.
In terms of financial strains due to IT Security management, 94% of cybersecurity leaders estimated an increase of 28% in their yearly InfoSec budget to combat cloud threats arising from ransomware alone! We are not even considering the cost of training security professionals and console users against existing and emerging cloud threats in the cloud industry.
Could it be more than 50% rise in annual InfoSec preparedness and planning budgets? What do you think?
Rise in Number and Potency of Cloud Threats Likely to Increase in 2023 and 2024
Palo Alto Networks research shows an imminent rise in the cloud threats due to the kind of payouts these incidents bring to the attackers. Common types of attacks that could rise in 2023 include typo-sqatting, dependency confusion, account takeover, and self-sabotaged OSS. Due to an increase in OSS dependency in production environments, there could be additional number of attacks on cloud users proportional to the number of assets linked to the organization’s IT cloud workloads spanning multiple regions. These could all be managed with better security frameworks, but personal accountability is also important. In a Mimecast survey finding, it was revealed how cybersecurity personnel are getting disenchanted by successful attacks, lowering their personal accountabilities from 71% to 57% within a year! Cyber attacks not only affected the IT posture of the organization but also took a toll on the mental health of the cybersecurity personnel.
In the next six months, we could expect some major AI-related announcements in the cyber security threat intelligence domains that could strengthen security frameworks in the digital and open source ecosystems operating in public cloud and APIs. Unit 42 analysts are expecting stiffer OSS regulation and support for popular open-source projects, including OpenMLS, Bundler/RubyGems, Sequoia-PGP, curl,
WireGuard, and OpenSSH. All these could result in stronger collaboration between partners, participants and government in responding quickly to software and cloud-native security issues mentioned in the report.



