Introduction
Businesses reap immense benefits, yet face unprecedented risks from a surge in cyber threats in the evolving era. In this changing landscape, companies should prioritize improved cybersecurity. The alarming statistics highlight the need for action, emphasizing the importance of advanced security operations, like having a robust Security Operations Center (SOC).
- Cybercrime costs are escalating rapidly. According to Cybersecurity Ventures in a report by Cybersecurity Magazine, global cybercrime costs are projected to skyrocket to $10.5 trillion by 2035, a significant jump from $6 trillion in 2021.
- Ransomware attacks are increasing, with the FBI noting a 75% increase in 2021. The average ransom payment now exceeds a staggering $2 million.
- Data breaches have become commonplace, with over 1,800 reported by the Identity Theft Resource Center in 2022, exposing billions of records.
The imperative for advanced security operations becomes evident. Traditional security solutions prove insufficient against the constant innovation of hackers. To combat advanced threats, businesses must embrace proactive threat hunting, and incident response, and leverage threat intelligence. Data protection is paramount, necessitating secure handling throughout its lifecycle. Changing rules requires businesses to follow stricter regulations on data privacy and security.
Read more: AI’s Strategic Role in Shaping IT Security
Gartner Predicts that by 2027, 50% of large enterprise CISOs will have adopted human-centric security design practices to minimize cybersecurity-induced friction and maximize control adoption.
In the ever-changing field of cybersecurity, staying alert is crucial to protect networks and data from evolving threats. A vital component of a cybersecurity strategy is setting up a Security Operations Center (SOC). Especially important for large businesses and government organizations, a SOC is a fundamental part of their plan to reduce cybersecurity risks. This article explores what a SOC is, its parts, how it works, and why organizations need to enhance cybersecurity resilience.
Security Operations Center (SOC)
A Security Operations Center (SOC) is a centralized unit that monitors and manages an organization’s security posture. Staffed by proficient security professionals, the SOC is entrusted with the vital tasks of identifying, responding to, and mitigating security threats, ensuring continuous secure operations.
 Key Responsibilities of a SOC:
Key Responsibilities of a SOC:
Continuous Monitoring:
The SOC engages in vigilant monitoring to ensure the organization’s security remains intact.
Incident Handling Process:
SOCs are designed to streamline the security incident handling process, enhancing the efficiency and effectiveness of responses.
Collaborative Incident Resolution:
Facilitating collaboration among security personnel, SOCs assist analysts in triaging and resolving security incidents more efficiently.
Comprehensive Threat Landscape View:
The primary goal of a SOC is to attain a complete view of the business’ threat landscape. This encompasses various endpoints, servers, on-premises software, also third-party services, and the traffic between these assets.
Industry Analyst Recommendations
1. Invest in AI: Enhancing Threat Detection Efficiency
Industry leader Gartner recommends embracing AI-driven threat detection engines. The engines meticulously analyze behavioral indicators through extended security telemetry data, offering heightened visibility into potential security threats. Leveraging AI is focused on greatly enhancing the effectiveness of threat detection processes.
Source: Gartner Emerging Tech: Security — Improve Threat Detection and Response With AI-Based Behavioral Indications. 2023.
2. Drive Towards Automation: Addressing the Skills Gap
Acknowledging the persistent shortage of skilled security practitioners, Gartner underscores the necessity for increased automation within security operations. The drive towards automation becomes a strategic response to the shortage, enhancing efficiency and ensuring a swift and effective response to emerging security threats.
Source: Gartner Emerging Technology Horizon for Information Security, 2022. 2023.
3. Platform Consolidation: Streamlining Cybersecurity Strategies
Gartner’s survey analysis reveals a significant shift in cybersecurity strategies, with 75% of organizations actively pursuing security vendor consolidation. This marks a substantial increase from the 29% recorded in 2020. The trend toward platform consolidation is recognized as a strategic move to streamline and fortify cybersecurity measures across diverse organizational landscapes.
Source: Gartner Top Trends in Cybersecurity — Survey Analysis: Cybersecurity Platform Consolidation. 2023.
Functions of a SOC
A Security Operations Center (SOC) is critical in identifying and responding to cybersecurity incidents. The skilled SOC staff collaborates with various departments and teams to share incident information with the relevant stakeholders. SOC teams mitigate threats and manage log activity. Organizations opt for third-party providers to deliver SOC services.
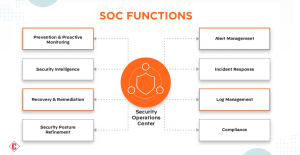
- Monitoring and Managing Security Posture: SOC oversees and manages the overall security stance of an organization.
- Developing and Implementing Security Policies: The creation and implementation of security policies and procedures are integral functions of a SOC.
- Security Awareness Training: SOC provides security awareness training to employees to enhance the organization’s security culture.
- Responding to Security Incidents: Rapid response to and resolution of security incidents is a key responsibility of the SOC.
- Analysis of Logs and Network Traffic: SOC analyzes logs, network traffic, and other data sources to identify potential threats and vulnerabilities.
- Vulnerability Assessments: Conduct vulnerability assessments to identify and address potential weaknesses in the security infrastructure.
- Providing Threat Intelligence Reports: Offering threat intelligence reports to keep the organization informed about evolving cybersecurity threats.
- Designing and Implementing Security Solutions: SOC takes charge of designing and implementing security solutions tailored to the organization’s needs.
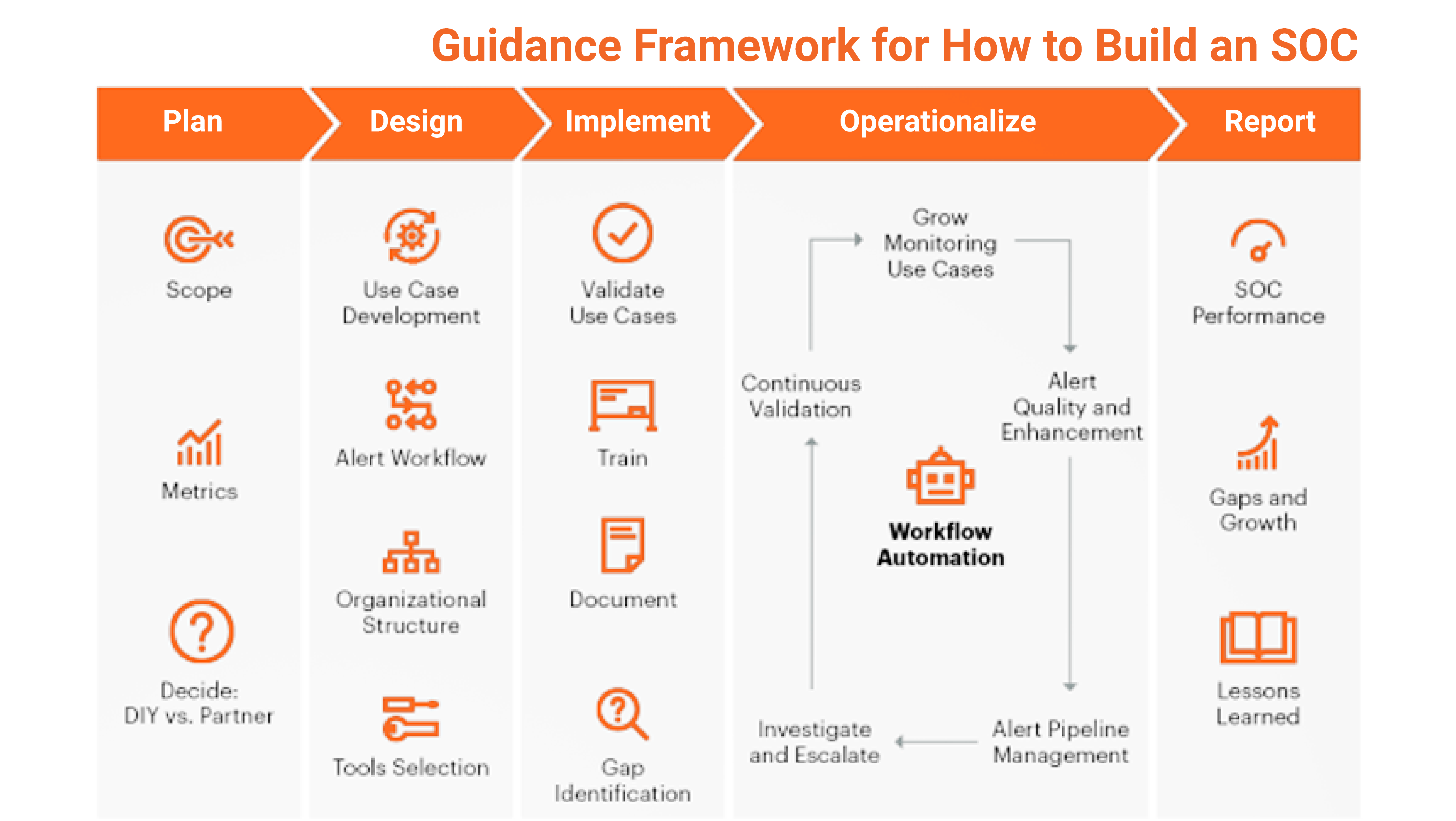
Steps to Build and Operate a Modern Security Operations Center
A Security Operations Center (SOC) is a facility where security professionals monitor and analyze events for security threats. A modern SOC is essential for any organization that wants to protect its data and systems from cyberattacks.
This section will provide a step-by-step guide to building and operating a modern SOC. We will discuss the following topics:
Planning and Design: This phase involves defining the scope of your SOC, identifying your use cases, and developing a design that meets your needs.
Implementation: This phase involves selecting and implementing the tools and technologies you need to operate your SOC.
Operationalization: This phase involves developing the processes and procedures for operating your SOC on a day-to-day basis.
Reporting: This phase involves developing reports and metrics to track the performance of your SOC.
Growth: This phase involves continuously improving your SOC by identifying and addressing gaps, and adopting new technologies.
#1 Planning and Design
The first step in building a modern SOC is to plan and design it. This phase involves defining the scope of your SOC, identifying your use cases, and developing a design that meets your needs.
- Define the scope of your SOC: What are you trying to achieve with your SOC? What are your security goals?
- Identify your use cases: What types of security incidents are you most likely to encounter? What are the steps you need to take to respond to these incidents?
- Develop a design: Once you have defined the scope of your SOC and identified your use cases, you can develop a design that meets your needs. This design should include the following:
- The tools and technologies you need to operate your SOC
- The staffing requirements for your SOC
- The processes and procedures for operating your SOC
#2 Implementation
The next step is to implement your SOC design. This phase involves selecting and implementing the tools and technologies you need to operate your SOC.
- Select your tools and technologies: There are a wide variety of tools and technologies available for SOC operations. When selecting tools and technologies, consider your needs, budget, and security requirements.
- Implement your tools and technologies: Once you have selected your tools and technologies, you need to implement them. This may involve installing software, configuring hardware, and integrating different systems.
#3 Operationalization
Once your SOC is implemented, you need to operationalize it. This phase involves developing the processes and procedures for operating your SOC on a day-to-day basis.
- Develop your processes and procedures: Your processes and procedures should cover all aspects of SOC operations, including incident detection, investigation, and response.
- Train your staff: Your staff needs to be trained on your processes and procedures. They also need to be familiar with the tools and technologies you are using.
#4 Reporting
It is important to track the performance of your SOC. This phase involves developing reports and metrics to track the performance of your SOC.
- Develop reports and metrics: Your reports and metrics should track key performance indicators (KPIs) such as the number of security incidents detected, the time it takes to resolve incidents, and the number of false positives.
- Use your reports and metrics to improve your SOC: You can use your reports and metrics to identify areas where your SOC can be improved.
#5 Growth
A modern SOC is not static. It is important to continuously improve your SOC by identifying and addressing gaps and adopting new technologies.
- Identify gaps: Regularly assess your SOC to identify any gaps in your coverage.
- Address gaps: Once you have identified gaps, you need to take steps to address them. This may involve investing in new tools and technologies or training your staff.
- Adopt new technologies: New technologies are emerging all the time that can help you improve your SOC operations. Stay up-to-date on the latest technologies and consider adopting them when appropriate.
Security Operations Center (SOC) Best Practices
Security Operations Centers’ (SOCs) effective practices are pivotal for implementing and maintaining a robust security strategy. The SOC team’s primary responsibility lies in executing the established security strategy rather than crafting it. This involves deploying protective measures in response to incidents and conducting thorough post-incident analysis.
- Establish a SOC: Formulate a centralized unit tasked with monitoring and managing the organization’s security posture.
- Develop Security Policies and Procedures: Devise and implement security policies and procedures ensuring compliance with applicable laws and regulations.
- Implement Security Solutions: Deploy security solutions such as firewalls, intrusion detection systems, and antivirus software to safeguard the organization’s environment.
- Monitor and Analyze Logs: Vigilantly monitor and analyze logs, network traffic, and other data sources to identify potential threats and vulnerabilities.
- Provide Security Awareness Training: Conduct security awareness training for employees to ensure awareness and adherence to the organization’s security policies and procedures.
- Perform Vulnerability Assessments: Undertake vulnerability assessments to identify potential weaknesses in the organization’s environment.
- Respond to Security Incidents: Swiftly respond to security incidents, minimizing their impact through timely and effective actions.
Top Enterprises of Security Operations Center as a Service Market
IBM Corporation
Tata Consultancy Services
Atos
Check Point
eSentire Inc.
Tools Utilized in a Security Operations Center
Security Operations Centers (SOCs) employ various tools to enhance various aspects of their operations, covering prevention, event logging, automation, detection, investigation, orchestration, and response. Many SOCs utilize multiple sets of tools, often siloed to address different facets of their infrastructure. Research conducted by analyst firms like Ovum and ESG reveals that a majority of enterprises rely on more than 25 distinct tools within their SOCs. These tools encompass:
- SIEM (Security Information and Event Management): Aggregates and analyzes security data from various sources to identify potential threats.
- Network Intrusion Detection System (NIDS): Monitors and analyzes network traffic for signs of unauthorized access or suspicious activities.
- Network Intrusion Prevention System (NIPS): Works proactively to block or prevent identified network intrusions.
- Security Orchestration, Automation, and Response (SOAR): Integrates and automates security processes to enhance incident response efficiency.
- Security Analytics Platforms: Utilizes advanced analytics to identify and respond to security threats.
- Endpoint Detection and Response (EDR): Monitors and responds to threats at the endpoint, identifying and neutralizing malicious activities.
- Vulnerability Management Solutions: Identifies and addresses vulnerabilities in the organization’s systems and infrastructure.
- Data Loss Prevention (DLP): Implements measures to prevent unauthorized access and distribution of sensitive data.
- Identity and Access Management (IAM): Manages and controls user identities and access to systems and resources.
- Firewalls: Establishes barriers to control and monitor incoming and outgoing network traffic.
The advent of a new class of tools known as Extended Detection and Response (XDR) is transforming the landscape. XDR integrates and correlates data from endpoints, networks, and the cloud, replacing several key tools within security operations teams.
Read more: IT Leaders Share Their Insights on Data Privacy and Digital Transformation
Future Outlook: Transforming SOC Operations
Threat actors leverage advanced tools, while legacy technologies like SIEM struggle to keep pace. To counter this, scalable solutions aligned with cloud initiatives are vital. Manual analysis, alert fatigue, and slowed investigations plague SOC analysts dealing with complex and siloed data. Recognizing the human-centric core of SOCs, automation, incident distribution, and comprehensive training emerge as critical wishes. Automation, driven by security orchestration and response technologies, aids in scaling SOCs. Varied incident distribution fosters continuous learning, and comprehensive training ensures consistency and growth. Fulfilling these wishes is imperative for building efficient, effective, and modern SOCs capable of navigating the dynamic cybersecurity landscape.
FAQs on Security Operations Center (SOC)
1: Why is a SOC crucial for organizations?
A SOC is essential to prevent major cyber incidents, reduce threats, and adopt a centralized security approach. It provides a comprehensive strategy for detecting, preventing, and mitigating attacks, offering continuous protection through uninterrupted monitoring. The diverse SOC team, beyond the four analyst tiers, ensures broader and deeper coverage, including roles such as vulnerability managers, threat intelligence, malware, and forensic analysts.
2: What functions does a SOC perform in an organization’s security strategy?
A SOC serves as an organizational aspect of an enterprise’s security strategy, combining processes, technologies, and people. It manages and enhances the overall security posture, creating situational awareness, mitigating risks, and ensuring compliance with regulatory requirements. The SOC acts as a governance and compliance framework for tailored processes and technologies.
3: How can organizations enhance their SOC capabilities?
To improve a SOC, organizations should adopt modern tools like machine learning, automation, and artificial intelligence, mirroring strategies employed by well-funded threat actors. Challenges from legacy SOC environments, including lack of visibility, increased complexity of investigations, and alert fatigue, can be addressed by investing in solutions that consolidate tools, improve response times, and streamline threat intelligence data processing.
4: What are common challenges faced by SOCs and how can they be addressed?
Common challenges include lack of visibility, alert fatigue, and the complexity of investigations. Investing in solutions that consolidate tools, improve Mean Time to Respond (MTTR), and Mean Time to Identify (MTTI), and facilitate automation can address these challenges, staying ahead of evolving threats.
5: How is a SOC connected to SIEM (Security Information and Event Management)?
SOCs often face a high volume of low-fidelity alerts, overwhelming analysts. SIEM solutions alleviate this burden by handling data and providing context, making it easier for SOC analysts to manage alerts effectively. While an SIEM is not a prerequisite for having a SOC, the two work together to protect internal resources, improving overall security measures.
6. What advantages does a SOC provide?
SOCs deliver numerous benefits, including enhanced security posture, heightened visibility, more effective incident response, improved threat detection, and overall operational efficiency.
7. How does a SOC differ from a NOC?
SOCs and Network Operations Centers (NOCs) are frequently confused due to their shared focus on monitoring and managing network performance. However, their purposes diverge. SOCs concentrate on proactively detecting and responding to potential threats, whereas NOCs prioritize optimizing networks and ensuring uninterrupted uptime.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]



 Key Responsibilities of a SOC:
Key Responsibilities of a SOC: