When software development is integral to business operations, prioritizing software security is not just an option but a necessity for any organization. With myriad security products available, understanding the nuances of application security is the first step toward protecting your digital assets. This significance is underscored by the fact that application breaches account for 25% of all security incidents, highlighting the critical need for robust security measures.
This article aims to serve as a vital resource for Chief Security Officers (CSOs), security experts, and developers by providing an in-depth analysis of the top application security tools in the market. As advanced application security tools become indispensable in defending against vulnerabilities, our guide focuses on equipping you with the knowledge to select the right tools that align with your security requirements. By exploring the leading solutions, this article will assist you in fortifying your defenses, identifying vulnerabilities, enforcing security policies, and safeguarding sensitive data. Whether your goal is to enhance your application’s security posture or to stay abreast of the best practices in application security, this guide is designed to help you make informed decisions that cater to your specific needs.
Understanding the Application Security Types
Operating application security can be complex, particularly when commercial websites emphasize product benefits without clarifying the solution type. This ambiguity complicates comparisons between vendors or products. To demystify application security, it’s useful to categorize the tools into two primary groups that encompass the majority of offerings in the field:
- Application Security Testing (AST) Tools: These tools are essential for software development teams, including testing and operations personnel in a DevOps environment. AST tools focus on integrating security measures during development to prevent vulnerabilities before deployment.
- Runtime Protection Tools: Aimed at safeguarding applications in their operational phase, these tools defend against various threats once an application is live. Runtime protection is critical for ensuring ongoing security against emerging vulnerabilities.
A research paper, “Web Application Vulnerabilities and Threats,” highlights a concerning statistic: 90% of web applications are susceptible to hacker attacks. Furthermore, it is alarming that 39% of these sites could offer unauthorized access to their applications. Most of these vulnerabilities, accounting for 82%, are found directly within the application code.
Essential Features of Application Security Tools
In the early months of 2020, the frequency of attacks on web applications highlighted an alarming trend, with the average application facing 20,000 attacks. These incidents targeted vulnerabilities such as path traversal, SQL injection, and XSS. In response to this persistent threat landscape, application security professionals advocate for a comprehensive approach—test all applications thoroughly, periodically, and consistently. Utilizing the insights from these tests is crucial for strengthening an organization’s cybersecurity framework. To achieve this, the selection of appropriate application security tools is paramount. Here are the essential features these tools must offer:
- Compatibility with Your Environment: The market is saturated with various application security tools, each offering unique features. Some tools prioritize integration capabilities, others aim to minimize false positives, and some are tailored to specific operational environments. The choice of tool should be guided by its suitability for your environment and specific security needs, including user-friendly reporting and dashboard accessibility.
- Minimization of False Positives: The primary objective of application security tools is to identify and rectify vulnerabilities. However, the prevalence of blanket reporting and inadequate verification can lead to a high rate of false positives. Effective tools distinguish between genuine and potential vulnerabilities, requiring additional confirmation before classifying them as true positives. This precision is especially critical in large organizations, where efficiency in addressing security concerns is paramount.
- User-Friendliness and Efficient Vulnerability Detection: The vast number of vulnerabilities identified annually underscores the importance of efficient detection capabilities. In addition to identifying vulnerabilities, application security tools must be user-friendly. Features such as the ability to pause and resume scans, notification alerts for scan completion, and the tool’s stability during the scanning process enhance the user experience and operational efficiency.
- Compliance and Enterprise-Level Testing: The capability to conduct comprehensive compliance testing is vital to application security tools. These tools should offer advanced vulnerability management and generate trend reports, accommodating various organizational requirements, such as compliance with specific regulations. The quality of reporting is integral to an organization’s ability to meet compliance standards effectively. Additionally, reducing false positives is a critical concern for enterprises aiming to optimize the use of their resources in addressing genuine security threats.
Top Application Security Tools of 2024
#1 GitLab
GitLab Application Security integrates a comprehensive suite of security features into the GitLab platform, designed to detect and mitigate vulnerabilities across the software development and deployment lifecycle. Embedding various security testing tools and practices directly into the GitLab CI/CD pipeline facilitates automatic security assessments within the development process.
Features:
- The suite includes Static Application Security Testing (SAST) for vulnerability analysis in source code without execution, Dynamic Application Security Testing (DAST) for identifying vulnerabilities in live web applications, and Dependency Scanning to examine project dependencies for known vulnerabilities.
- It also features container scanning to detect vulnerabilities in container images, ensure license compliance, and verify that dependencies meet legal and security standards.
Advantages: Users appreciate GitLab’s user-friendly interface, especially its simplicity in importing projects from other repositories like GitHub and Bitbucket.
Challenges: However, some feedback suggests that the features offered in the premium edition may not justify the cost, and performance issues, such as slow task execution, have been noted.
#2 HCL AppScan
HCL AppScan delivers a robust security testing suite to protect businesses and customers from cyber threats. It includes products like AppScan on Cloud, AppScan 360, AppScan Standard, AppScan Source, and AppScan Enterprise, each tailored to meet specific security needs.
Capabilities: At its core, HCL AppScan offers dynamic application security testing (DAST), static application security testing (SAST), and interactive application security testing (IAST). It boasts compatibility with various development and deployment environments, supports compliance reporting, and offers customization through the AppScan Extension Framework.
Strengths: Users commend HCL AppScan for its responsiveness to feature requests, user-friendly design conducive to developers, and effective vulnerability detection and prioritization.
Limitations: User feedback points to areas needing enhancement, such as the dashboard interface’s user experience, limited integrations with certain container technologies, challenges in integrating with continuous integration/continuous deployment (CI/CD) processes, and scalability limitations tied to licensing.
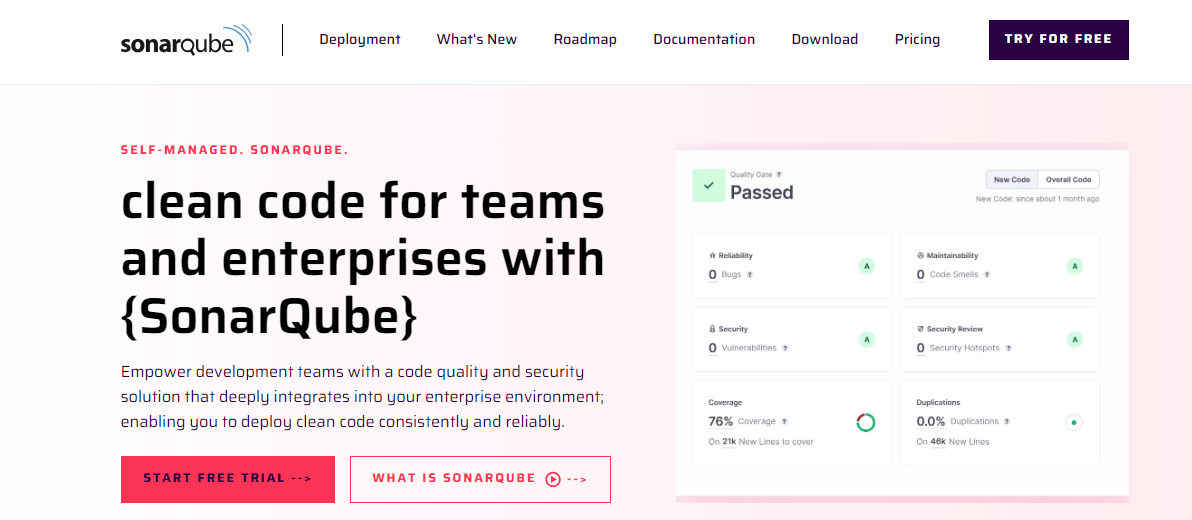
#3 SonarQube
SonarQube is designed to assist developers in producing cleaner, more secure code. It supports applications in 27 languages and provides comprehensive protection through numerous automated static code analysis rules. The tool provides continuous guidance to development teams, ensuring code quality and security best practices.
Key Features:
- SonarQube analyzes code in 27 programming languages, delivering early security feedback to developers.
- After each analysis, its quality gates assess whether the analyzed code meets market readiness standards.
- The platform aims to minimize coding issues and reduce the need for rewriting, thereby lowering maintenance costs.
Integration Capabilities: SonarQube integrates with popular development platforms and repositories, including GitHub, Azure DevOps, Bitbucket, and GitLab.
Advantages: The platform features a detailed dashboard that provides a comprehensive overview and deep insights into code metrics. Its user-friendly interface makes it suitable for development projects, facilitating an efficient and effective code quality and security management process.
#4 Veracode
Veracode offers a powerful mix of software-as-a-service (SaaS) technology and immediate expertise to facilitate DevSecOps. Through thorough analysis, developer support, and governance tools, it aims to diminish the risks of security breaches.
Key Features: Veracode delivers instant security feedback, identifying and assisting in the remediation of code vulnerabilities as they occur. It guides developers by indicating their code’s strengths and weaknesses, promoting a learning environment throughout the development process.
Advantages: Unique in its capacity to offer a holistic view of application security status across various testing methodologies—SAST, DAST, SCA, and manual penetration testing—Veracode stands out for its centralized management of security assessments. Its code-scanning process is notable for a low rate of false positives. Furthermore, Veracode is praised for its exceptional post-sales support and provides detailed reports on vulnerabilities, aiding developers in understanding and addressing security concerns effectively.
#5 VMware AppDefense
 VMware AppDefense is a cutting-edge platform designed for enterprise virtualization and security teams. It aims to secure virtual infrastructure effectively while offering tools for simplified micro-segmentation planning, application visibility, and reputation scoring.
VMware AppDefense is a cutting-edge platform designed for enterprise virtualization and security teams. It aims to secure virtual infrastructure effectively while offering tools for simplified micro-segmentation planning, application visibility, and reputation scoring.
Key Features: AppDefense enhances application visibility and provides advanced security measures. It simplifies the management and response to security incidents, facilitating a clearer understanding of threats.
Integration Capabilities: The platform supports integration with a variety of security and automation tools, including Splunk, IBM QRadar, Puppet, Cb Defense, Ansible, and Aqua Security, broadening its application and efficacy in enterprise environments.
Benefits: VMware AppDefense stands out for its comprehensive visibility into each workload directly from the hypervisor, ensuring a secure application environment. It offers detailed insights into network connections and interactions with servers or services. The user-friendly GUI allows for straightforward access to status reports and fine-grained control over guest-level operations, enhancing both security posture and operational efficiency.
#6 Checkmarx DAST
Checkmarx DAST is engineered to detect vulnerabilities and security gaps in web applications and APIs by simulating real-world cyber attacks in runtime. It is designed to seamlessly integrate with Continuous Integration/Continuous Deployment (CI/CD) frameworks, facilitating continuous security assessments.
Key Features:
- Identifies server and database misconfigurations, authentication and encryption issues, and other vulnerabilities.
- It offers real-time analysis for accurate vulnerability detection, supports a wide range of web applications and API frameworks,
- Integrates smoothly with existing workflows and provides comprehensive reports and analytics for enhanced insights.
Strengths: Users have highlighted the centralized reporting functionality as a crucial benefit, enabling efficient tracking and management of security issues.
Challenges: However, some users have reported difficulties integrating Checkmarx DAST into their CI/CD pipelines, indicating a need for compatibility and ease of use improvements.
#7 Qualys
Qualys identifies known and unknown IT assets across diverse environments, including endpoints, cloud services, containers, mobile devices, operational technology (OT), and the Internet of Things (IoT). It provides a detailed inventory that includes vendor lifecycle information and more, ensuring thorough asset management.
Features:
- Qualys delivers an integrated solution on a unified platform, offering immediate visibility and control over all IT assets.
- It stands out for its remarkable Six Sigma accuracy in eliminating false positives.
Integration Capabilities: The platform seamlessly integrates with tools such as CyberArk, BugCrowd, CyberSponse, AWS Security Hub, IntSights, and Jira, enhancing its functionality and application in security operations.
Advantages:
Qualys is a cloud-based solution that simplifies the coordination between various teams by offering an integrated, end-to-end security solution.
Its ease of use, continuous and comprehensive monitoring capabilities, outstanding vulnerability scanning, and PCI compliance readiness make it a preferred choice for managing IT security.
#8 Netsparker
Netsparker is designed to automate web security processes, offering fully integrated and scalable solutions with sophisticated reporting tools and native workflows. Leveraging proof-based scanning technology and automatic verification, Netsparker aims to eradicate false positives. Its cutting-edge scanning capabilities ensure robust protection against web vulnerabilities, including Cross-Site Scripting (XSS) and SQL Injection.
Beyond mere scanning, Netsparker automates routine security tasks, enhancing efficiency. A global dashboard provides complete oversight, displaying scanned vulnerabilities and their resolution status and offering comprehensive control over the security process.
It offers benefits:
- Fully integrated and scalable web security solutions
- User-friendly interface for ease of use
- Detects a wider range of vulnerabilities compared to other scanners
- Offers high-quality service and support
- Allows customization of scans for targeted assessments and time efficiency
#9 NowSecure
NowSecure DAST stands out as a specialized tool for testing mobile application security. It leverages static, dynamic, and interactive analysis methods to thoroughly evaluate mobile apps’ security posture. Designed to meet the unique requirements of modern mobile software development life cycles (SDLC), it offers comprehensive security and privacy testing solutions.
Strengths: Users appreciate the platform’s seamless integration capabilities and intuitive interface, facilitating an efficient testing process.
Limitations: However, some users have noted that the testing procedure can be complex and often requires direct involvement. Additionally, the cost of using NowSecure may be prohibitive for smaller organizations, presenting a challenge in accessing its full range of services.
#10 Metasploit
Metasploit is designed to enhance security teams’ capabilities, enabling them to conduct in-depth vulnerability verifications, manage security assessments, and bolster security awareness effectively. It provides a proactive stance against potential attackers.
Key Features:
- This tool boasts over 1,500 penetration testing exploits.
- Metasploit allows for the importation of network scan data, facilitating a comprehensive suite of features for data collection, automation, and penetration.
- Available in two editions, Metasploit Framework offers an open-source option, while Metasploit Pro delivers commercial support for advanced users.
Integration Capabilities: Metasploit integrates seamlessly with several analysis tools, including NeXpose, Nessus, Dradis, Tenable, and Nmap, enhancing its utility and efficiency in security assessments.
Advantages: Globally recognized as the leading penetration testing framework, Metasploit’s association with Rapid7 underscores its utility and effectiveness. Its ability to create reverse shells stands out as a significant benefit. Moreover, Metasploit is renowned for its intuitive interface and supports multiple platforms, making it a versatile tool for security professionals.
Conclusion
The foundation of application security lies in robust coding and design practices. No amount of training, auditing, or network security measures can compensate for fundamentally flawed programming. Ensuring application security is vital for any organization’s sustained success. This requires a commitment to secure development practices, complemented by ongoing testing and patching throughout the software lifecycle, to effectively maintain and enhance security postures.
FAQs on Application Security
1. What Does Application Security Entail?
Application Security is the collective measures taken to shield applications from threats and vulnerabilities at every stage of their lifecycle, encompassing the protection of software code, design, and deployment against malicious attacks to maintain data integrity.
2. Why Prioritize Application Security?
As software applications become increasingly integral to both business operations and personal activities, any vulnerabilities present can result in significant data breaches, financial losses, and reputational harm. Application Security is crucial for minimizing these risks by detecting and rectifying security flaws.
3. Which Threats Commonly Compromise Application Security?
Frequent threats to application security include SQL Injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), security misconfigurations, and vulnerabilities within unsecured APIs.
4. Steps to Secure an Application? Securing an application is a comprehensive process that involves:
- Regular security evaluations and penetration tests.
- Adherence to secure coding standards.
- Routine updates of software and its dependencies.
- Deployment of security measures such as Web Application Firewalls (WAF) and security scanners.
- Developer training in security awareness and practices.
5. What Is a Web Application Firewall (WAF)?
A Web Application Firewall (WAF) acts as a protective barrier that filters and scrutinizes HTTP traffic to and from a web application, safeguarding against malicious traffic and attacks.
6. What is the importance of Encryption in Application Security?
Encryption safeguards application security by transforming data into a secure code for transmission or storage, thereby preventing unauthorized access and ensuring the confidentiality and integrity of data.
7. How Do Authentication and Authorization Contribute to Application Security?
Authentication confirms a user’s identity upon accessing the application, whereas Authorization designates the extent of access and actions permitted to the user. Both functions ensure that only authorized users can access and interact with the application securely.
[To share your insights with us as part of editorial or sponsored content, please write to sghosh@martechseries.com]