Application security or AppSec is a fundamental approach in the modern software development lifecycle (SDLC). AppSec testing is defined as the set of processes, practices, and tools used to prevent, identify, and repair vulnerabilities within an app. If left undetected or unrepaired, these software vulnerabilities can expose the software code to malware injections and code highjacking. According to the latest AppSec report, the software testing industry has shown a 14% decline in vulnerabilities detected in target applications over the past two years.
Synopsys, an AppSec leader, published its 2023 Software Vulnerability Snapshot Report. Synopsys Cybersecurity Research Center (CyRC) data underscores the effectiveness of different proactive measures in AppSec testing processes and methodologies. These processes involve the use of code reviews, automated testing, and continuous integration in detecting common programming errors. The decrease in software vulnerabilities found during AppSec testing shows improvement in code reviews and continuous integration. However, the researchers warn software development and testing teams against relying too much on a single security testing solution. A common approach like Static Application Security Testing (SAST) may no longer be viable in the current threat landscape, particularly when ransomware gangs are injecting malware and duplicate codes using advanced vulnerability detection tools for their crimes.
Importance of AI-based DevSecOps Security in Singaporean Businesses
Here are the key findings of the 2023 Software Vulnerability Snapshot Report related to AppSec tools and software testing trends.
Three-year Analysis of Top Vulnerabilities Known in the Application Security Testing Ecosystem
The Synopsys Security Testing Services team ran high-level AppSec tests for three years (2020-2022) to identify the top ten most common web and software application vulnerabilities. These tests focused on platforms made up of web applications, mobile apps, network systems, and source code.
- In 2020, 97% of tests showed software vulnerabilities
- In 2021, 95% of tests detected vulnerabilities
- In 2022, the numbers dropped to 83%
- During all these years, 92% of the tests showed vulnerabilities in the target applications
These tests were conducted in a simulated environment, probing target applications just like how a real-world cyber attacker would.
Here are the top 10 vulnerabilities mentioned in the report.
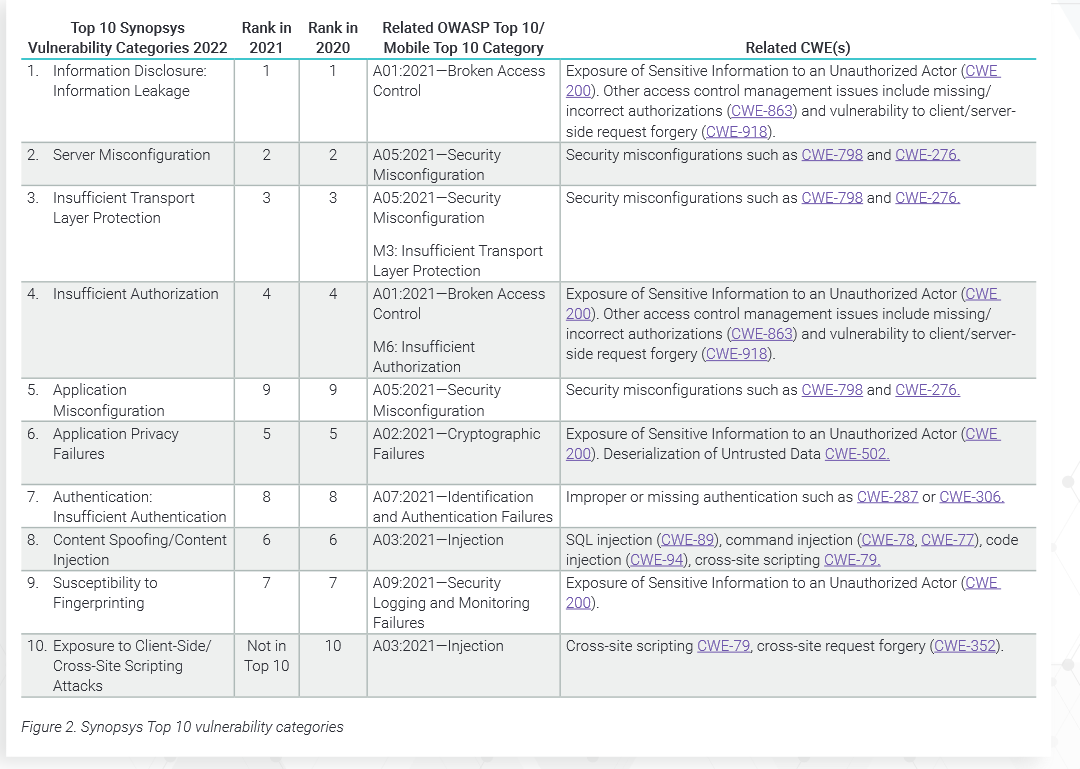
Vulnerability Categories 2022
Improvements in Software Coding and Testing Result in Fewer Vulnerabilities
Recent application security trends show that cloud-hosted applications are an ideal attack vendor for cyber attackers. While target groups penetrate software through vulnerabilities, a deeply embedded AppSec practice in SDLC can prevent damage to critical infrastructure and data breaches.
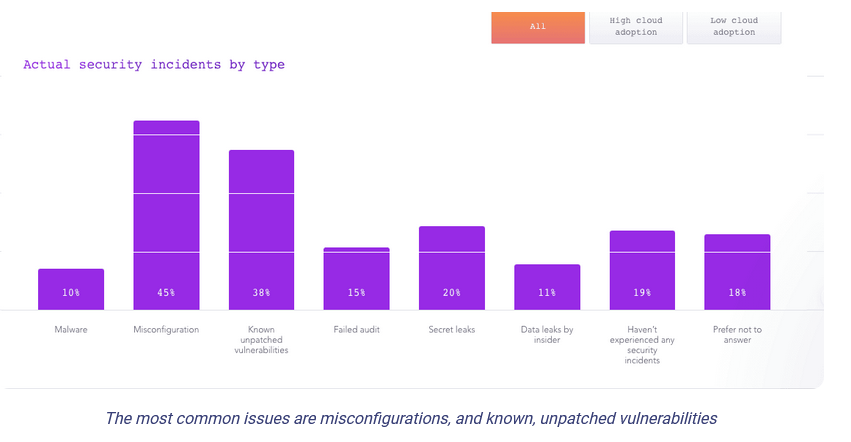
Cloud-native applications are most prone to vulnerabilities due to:
- misconfiguration
- malware
- known unpatched vulnerabilities
According to Snyk, 56 percent of organizations suffered a vulnerability incident due to a misconfiguration or known unpatched error in their cloud-native applications.
 The decrease in software vulnerabilities in the latest 2023 Software Vulnerability Snapshot Report highlights the improvements in software coding and testing practices. The use of AI ML capabilities, such as ChatGPT and Co-pilots for code reviews, automated testing, and continuous integration signify AppSec testing, audits, and corrections advancements.
The decrease in software vulnerabilities in the latest 2023 Software Vulnerability Snapshot Report highlights the improvements in software coding and testing practices. The use of AI ML capabilities, such as ChatGPT and Co-pilots for code reviews, automated testing, and continuous integration signify AppSec testing, audits, and corrections advancements.
Simulated software application testing in integrated development environments (IDEs) enables developers to identify vulnerabilities related to misconfiguration, code errors, and unpatched threats in real time, leading to higher software testing standards.
Cyber Attackers Take a Swipe at McLaren Health Care’s Database
New software modules are safe to a great extent. However, old projects, especially Open Source projects, across Java and JavaScript continue to be at risk.
Defining Software Vulnerabilities and Applications for AppSec Testing
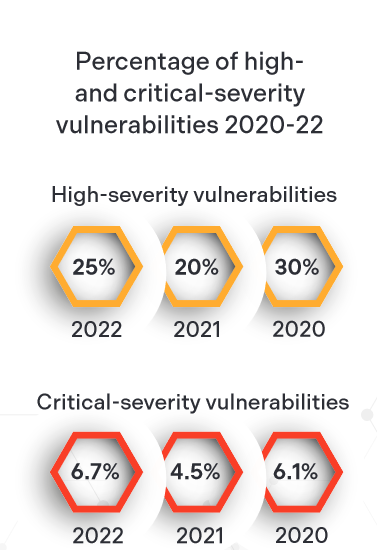
- High-severity vulnerabilities are less likely: On average over the past three years, 92% of the tests uncovered some form of vulnerability. However, only 27% of those tests contained high-severity vulnerabilities, and 6.2% contained critical-severity vulnerabilities.
- Leaked information continues to be a top risk: The top security issue that was uncovered has remained unchanged from 2020 to 2022 – information leakage, a major security issue occurring when sensitive information is exposed to unauthorized parties. An average of 19% of the total vulnerabilities were directly related to information leakage issues.
- Cross-site scripting is on the rise: Of all high-risk vulnerabilities found in 2022, 19% were found to be susceptible to cross-site scripting attacks.
- Third-party software poses increased risks: Among the top 10 security issues in 2022, 25% of the tests conducted found vulnerable third-party libraries to be a risk. Software is likely vulnerable if you do not know the versions of all components in use, including third-party and open-source components.
In the 2023 Software Vulnerability Snapshot Report, vulnerabilities were classified into three categories of severity:
- High
- Critical
- Medium
27% of the AppSec tests found high-severity vulnerabilities; 6.2% found critical-severity vulnerabilities.
Synopsys tests rate applications acting as a vector for cross-site scripting (XSS) among the top high-severity vulnerabilities. Similarly, SQL injection is the top critical severity vulnerability in AppSec testing reports between 2020 and 2022.
Now, coming to the AppSec testing designed to find vulnerabilities — software teams incorporate multiple processes and practices. The common techniques for vulnerability detection are:
- penetration (pen) testing
- dynamic application security testing (DAST)
- mobile application security testing (MAST) and
- network security testing
While many teams still use SAST for AppSec testing, multi-level testing is best recommended in 2024. For instance, server misconfigurations can go unchecked during internal testing if a combination of SAST (for coding errors), DAST (for live apps), SCA (for third-party inherited vulnerabilities), and pen testing are not done simultaneously.
Jason Schmitt, general manager of the Synopsys Software Integrity Group explains how organizations could benefit from taking security testing seriously and building a holistic approach to AppSec testing for a long-lasting impact in the marketplace. Jason says, “For the first time in years, we’re seeing a decrease in the number of known vulnerabilities in software, which provides new hope that organizations are taking security seriously and prioritizing a strategic and holistic approach to software security to make a lasting impact. As hackers have become more sophisticated, a multi-layered security approach is needed more than ever to identify where software risks live and protect businesses from being exploited.”
According to HCL’s recent Application Security testing trends report, there is a significant gap between the approach to and implementation of IAST (Interactive Application Security Testing) and SCA (Software Composition Analysis). These testing tools can have a huge impact on an organization’s ability to integrate real-time AppSec testing techniques into their existing cloud-native operations and CI/CD pipelines (Continuous Integration/Continuous Deployment). In 2024, we expect CISOs to take a more agile approach toward fixing vulnerabilities using multi-layered AppSec testing and remediation tools.


